Azure Landing Zone Accelerators are an architectural approach and a reference implementation that enables effective construction and operationalization of landing zones on Azure, at scale. This approach aligns with the Azure roadmap and the Cloud Adoption Framework for Azure.
AKS Landing Zone Accelerator represents the strategic design path and target technical state for an Azure Kubernetes Service (AKS) deployment. This solution provides an architectural approach and reference implementation to prepare landing zone subscriptions for a scalable Azure Kubernetes Service (AKS) cluster. For the architectural guidance, check out AKS Landing Zone Accelerator in Microsoft Docs.
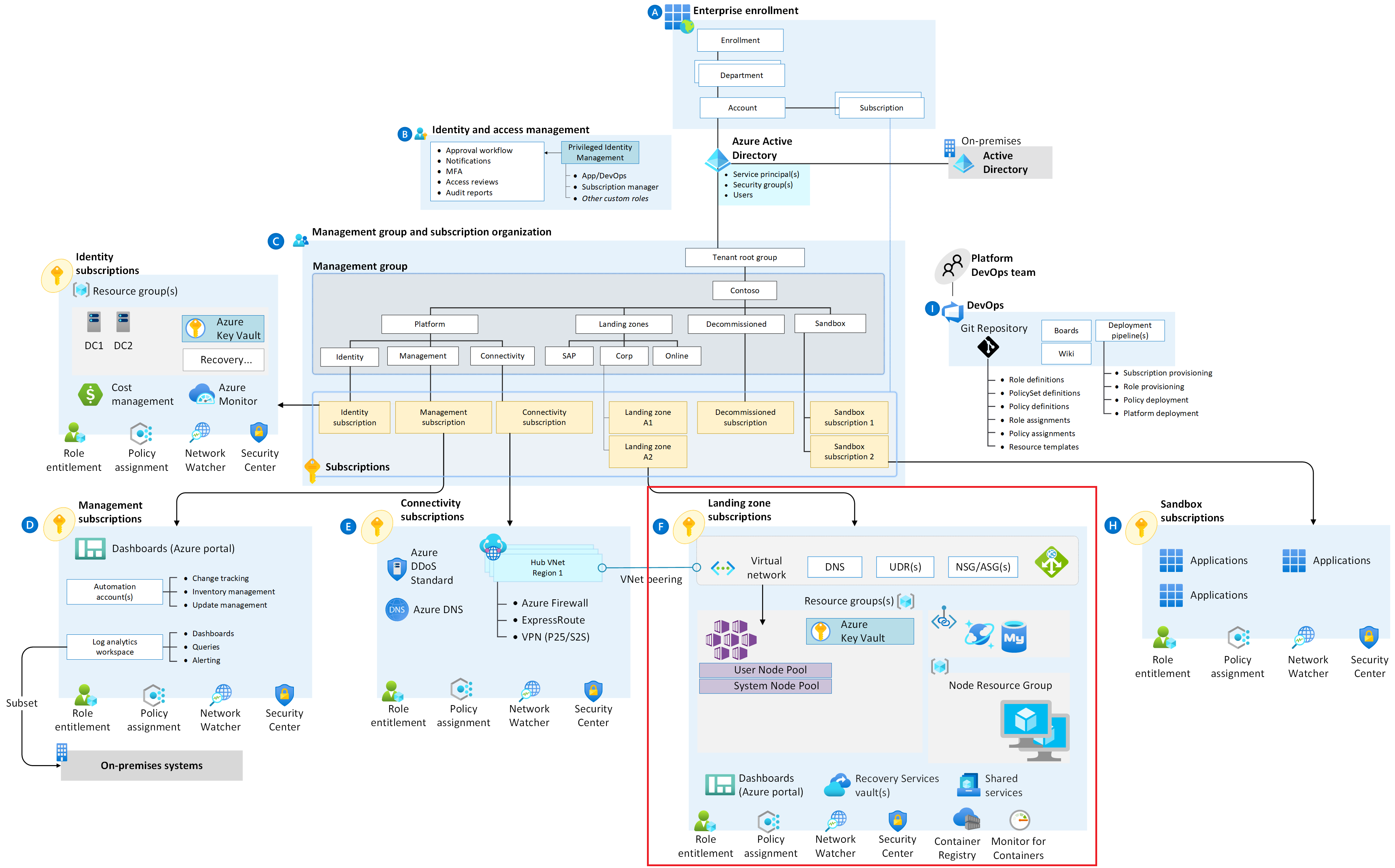
Below is a picture of what a golden state looks like and open source software like flux and traefik integrate well within the AKS ecosystem.
The AKS Landing Zone Accelerator is only concerned with what gets deployed in the landing zone subscription highlighted by the red box in the picture above. It is assumed that an appropriate platform foundation is already setup which may or may not be the official ESLZ platform foundation. This means that policies and governance should already be in place or should be setup after this implementation and are not a part of the scope this reference implementaion. The policies applied to management groups in the hierarchy above the subscription will trickle down to the AKS Landing Zone Accelerator landing zone subscription.
The reference implementations are spread across three repos that all build on top of the AKS Secure Baseline and Azure Landing Zones.
- This one
- The Bicep AKS Accelerator
- The Baseline Automation Module
In this repo, you get access to step by step guide covering various customer scenarios that can help accelerate the development and deployment of AKS clusters that conform with AKS Landing Zone Accelerator best practices and guidelines. This is a good starting point if you are new to AKS or IaC. Each scenario aims to represent common customer experiences with the goal of accelerating the process of developing and deploying conforming AKS clusters using Infrastructure-As-Code (IaC). They also provide a step by step learning experience for deploying AKS in an actual Enterprise environment. Most scenarios will eventually have a Terraform and Bicep version.
Use this repo if you would like step by step guidance on how to deploy secure and well architected AKS clusters using our scenario based model and/or you are new to AKS or IaC. This model promotes a separation of duties, modularized IaC so you can pick and choose components you want to build with your cluster and has implementations in ARM, Terraform and Bicep. It is the best starting point for people new to Azure or AKS.
A flexible templating approach using Bicep that enables multiple scenarios using a Web based tool. It provides tangible artifacts to quickly enable AKS deployments through CLI or in your CI/CD pipeline.
Driving the configuration experience is a wizard to guide your decision making, it provides presets for the main Azure Landing Zone deployment modes (Sandbox, Corp & Online). The output of this wizard experience are the parameters and CLI commands to immediately deploy using our maintained Bicep template to deploy your customized AKS environment in one step.
Use this repo if you would like to use a guided experience to rapidly create your environment with a maintained Bicep template based on the architecture of the AKS Secure Baseline.
This reference implementation demonstrates recommended ways to automate the deployment of the components composing a typical AKS solution. This repository includes information about separation of duties (different teams managing different parts of the deployment process), CI/CD and GitOps best practices.
Use this repo if you would like to learn how to quickly setup and get access to templates to help setup your own DevOps environments for AKS workloads.
Pick one of two options below
Pick one of the scenarios below to get started on a reference implementation. For the AKS secure baseline with non-private cluster, use the AKS baseline reference implementation.