This package provides a JDBC driver to Amazon Timestream for Java.
- Sign up for AWS — Before beginning, have an AWS account. For more information about creating an AWS account and retrieving your AWS credentials, see Sign Up for AWS and Create an IAM User in the AWS SDK for Java Developer Guide.
- Minimum requirements — To use the Amazon Timestream JDBC driver for Java, Java 1.8+ is required.
The Timestream JDBC driver is distributed as two JAR files.
JAR With All Dependencies Shaded Except SLF4J (amazon-timestream-jdbc-<version>-jar-with-all-dependencies.jar)
This is the shaded JAR which bundles up all the required dependencies and can be used directly in Java projects and external applications, without explicitly adding external dependencies. This JAR does not relocate the classpath of SLF4J, allowing logging to be enabled in external applications.
The JDBC driver is compatible with a number of BI tools. Instructions are outlined here for:
For other BI tools, please refer to that tool's product documentation
This is the lightweight JAR which does not include any dependencies. This JAR could be used if the application developer does not want duplicate dependencies and want full control over their dependency tree.
Some database connection tools require specifying the class name. The driver class for Timestream JDBC driver is:
software.amazon.timestream.jdbc.TimestreamDriverTo create a connection, construct a connection URL by appending optional connection properties to the default Timestream URL jdbc:timestream. The URL could be directly constructed, or a Properties object could be used in a Java application to do so.
The default URL for Timestream is jdbc:timestream.
Timestream supports optional connection properties that could be specified through the JDBC URL. To specify these optional properties use the following URL format: jdbc:timestream://PropertyName1=value1;PropertyName2=value2.... Note the property name is case sensitive.
An example of the JDBC URL with properties: jdbc:timestream://AccessKeyId=myAccessKeyId;SecretAccessKey=mySecretAccessKey;SessionToken=mySessionToken;Region=myRegion
A Properties object could be used to construct a connection URL in a Java application.
Properties prop = new Properties();
prop.put("AccessKeyId", "myAccessKeyId");
prop.put("SecretAccessKey", "mySecretAccessKey");
prop.put("SessionToken", "mySessionToken");
prop.put("Region", "myRegion");
DriverManager.getConnection(URL, prop);If the same connection properties are specified in both the URL and the Properties instance, the connection property in the URL will take precedence. For instance, in the following example "foo" will be used during authentication:
final String url = "jdbc:timestream://AccessKeyId=foo";
final Properties prop = new Properties();
prop.put("AccessKeyId", "userName");
DriverManager.getConnection(url, prop);NOTE: All property keys are case-sensitive.
All the connection properties are optional. If none of these properties are provided in the url jdbc:timestream, the Timestream JDBC driver will use the AWS default credentials chain to load the credentials.
| Option | Description | Default |
|---|---|---|
ApplicationName |
The name of the application currently utilizing the connection. This name is used for users' own debugging purposes and will not be communicated to the Timestream service. | The application name detected by the driver. |
| Option | Description | Default |
|---|---|---|
EnableMetaDataPreparedStatement |
Enables Timestream JDBC driver to return metadata for PreparedStatements, but this will incur an additional cost with Timestream when retrieving the metadata. | false |
| Option | Description | Default |
|---|---|---|
RequestTimeout |
The time in milliseconds the AWS SDK will wait for a query request before timing out. Non-positive value disables request timeout. | 0 |
SocketTimeout |
The time in milliseconds the AWS SDK will wait for data to be transferred over an open connection before timing out. Value must be non-negative. A value of 0 disables socket timeout. | 50000 |
MaxRetryCountClient |
The maximum number of retry attempts for retryable errors with 5XX error codes in the SDK. The value must be non-negative. | NONE |
MaxConnections |
The maximum number of allowed concurrently opened HTTP connections to the Timestream service. The value must be positive. | 50 |
| Option | Description | Default |
|---|---|---|
Endpoint |
The endpoint for the Timestream service. | NONE |
Region |
The signing region for the Timestream service endpoint. The signing region can be specified without an endpoint, but must be specified if a custom endpoint is given. | NONE |
| Option | Description | Default |
|---|---|---|
AccessKeyId |
The AWS user access key id. | NONE |
SecretAccessKey |
The AWS user secret access key. | NONE |
SessionToken |
The temporary session token required to access a database with multi-factor authentication (MFA) enabled. | NONE |
| Option | Description | Default |
|---|---|---|
AwsCredentialsProviderClass |
One of PropertiesFileCredentialsProvider or InstanceProfileCredentialsProvider to use for authentication. |
NONE |
CustomCredentialsFilePath |
The path to a properties file containing AWS security credentials accessKey andsecretKey. This is only required if AwsCredentialsProviderClass is specified as PropertiesFileCredentialsProvider. |
NONE |
| Option | Description | Default |
|---|---|---|
IdpName |
The Identity Provider (IdP) name to use for SAML-based authentication. One of Okta or AzureAD. |
NONE |
IdpHost |
The hostname of the specified IdP. | NONE |
IdpUserName |
The user name for the specified IdP account. | NONE |
IdpPassword |
The password for the specified IdP account. | NONE |
OktaApplicationID |
The unique Okta-provided ID associated with the Timestream application. A place to find the AppId is in the entityID field provided in the application metadata. An example entityID="http://www.okta.com//<IdpAppID>" |
NONE |
RoleARN |
The Amazon Resource Name (ARN) of the role that the caller is assuming. | NONE |
IdpARN |
The Amazon Resource Name (ARN) of the SAML provider in IAM that describes the IdP. | NONE |
| Option | Description | Default |
|---|---|---|
IdpName |
The Identity Provider (IdP) name to use for SAML-based authentication. One of Okta or AzureAD |
NONE |
IdpUserName |
The user name for the specified IdP account. | NONE |
IdpPassword |
The password for the specified IdP account. | NONE |
AADApplicationID |
The unique id of the registered application on Azure AD. | NONE |
AADClientSecret |
The client secret associated with the registered application on Azure AD used to authorize fetching tokens. | NONE |
AADTenant |
The Azure AD Tenant ID. | NONE |
IdpARN |
The Amazon Resource Name (ARN) of the SAML provider in IAM that describes the IdP. | NONE |
Timestream supports SAML-based authentication using both Okta and Azure Active Directory.
-
Admin permissions in AWS to create the identity provider and the roles.
-
An Okta account: https://www.okta.com/login/.
-
Access to Timestream.
-
Creating the AWS Account Federation application on Okta.
-
Set up SAML for Okta.
-
Configure Timestream JDBC driver to use Okta to access Timestream.
-
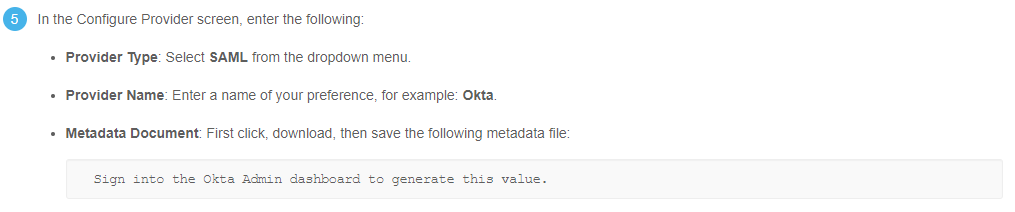
Sign in to the Okta Admin dashboard:
https://<company domain name>-admin.okta.com/admin/apps/active. -
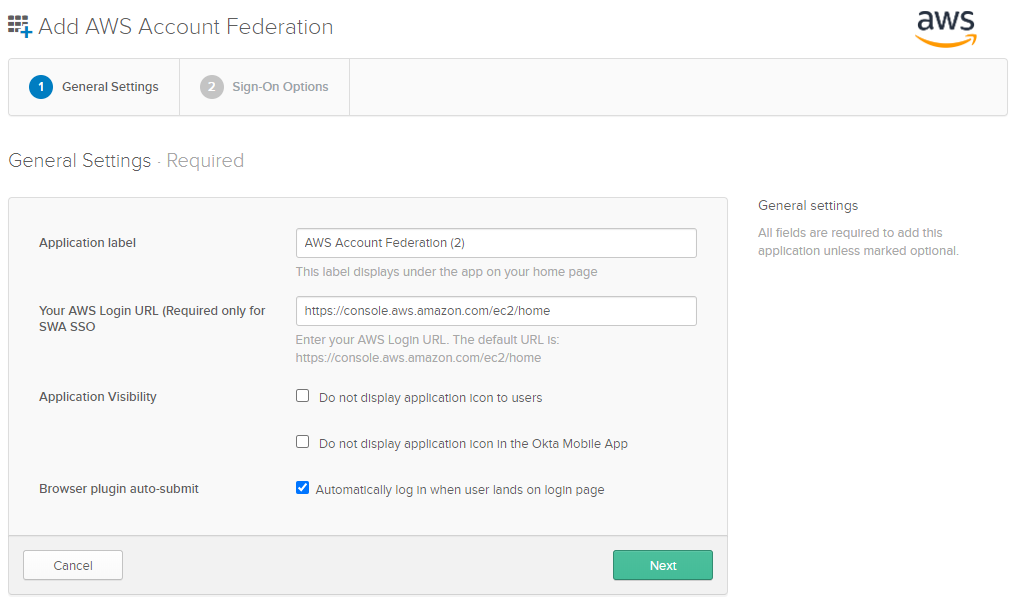
Select
Add Applicationand search forAWS Account Federation. -
Click
Add. -
Change the Login URL to the appropriate URL, e.g.
https://console.aws.amazon.com/console/home?region=us-east-1. -
Click
Next. -
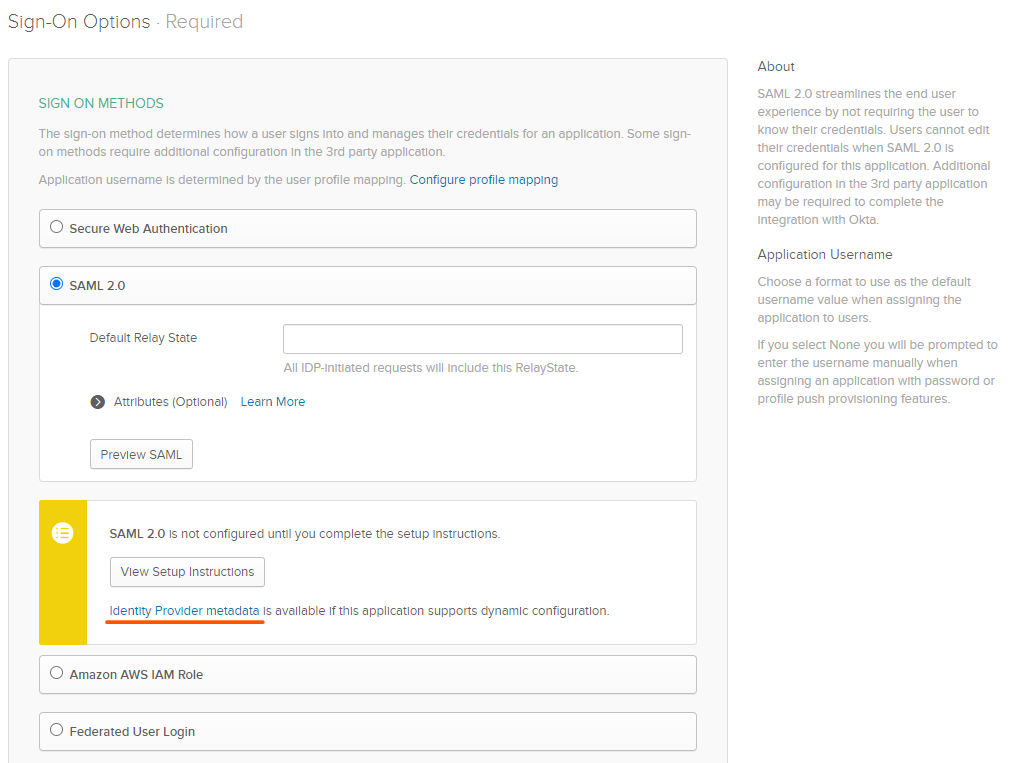
Select
SAML 2.0As the Sign-On method. -
Click
Identity Provider metadatato open the metadata XML file. Save the file locally, this is required later when creating the Okta identity provider. -
Leave the other configuration as blank for now.
-
Click
Done.
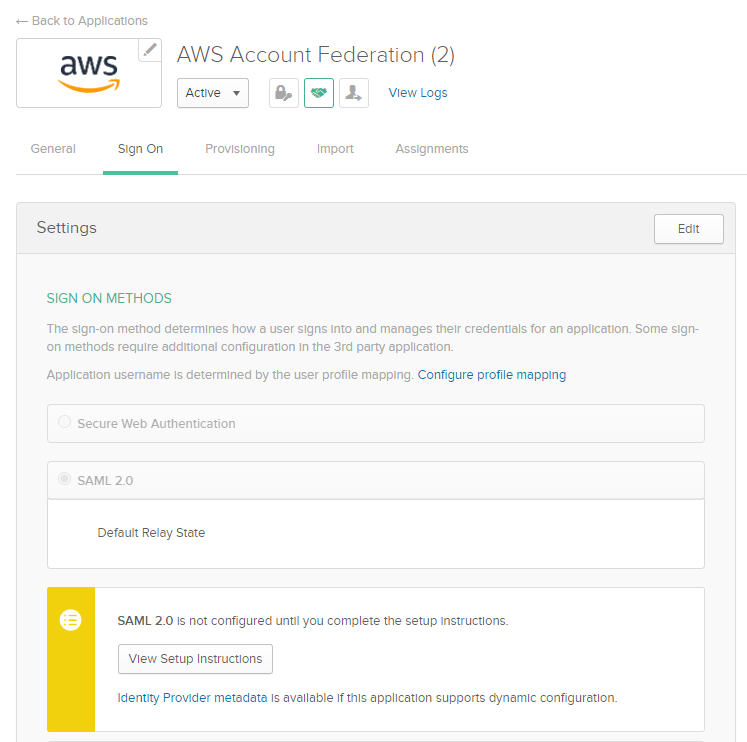
Select the Sign On tab. Click the View Setup Instructions button in the Settings section to set up SAML with Okta.
Alternatively use the following link to view the setup instruction:
https://saml-doc.okta.com/SAML_Docs/How-to-Configure-SAML-2.0-for-Amazon-Web-Service.html
The difference between these two links is that the latter link does not provide the link to the Metadata Document required when creating the Okta IdP.
This document could be found at:
-
https://<company domain name>-admin.okta.com/admin/apps/active. -
Select the AWS Account Federation application.
-
Select the Sign On tab.
-
Click on the
Identity Provider metadatahyperlink under theView Setup Instructionbutton to be redirected to the XML file.
-
Admin permissions in AWS to create the identity provider and the roles.
-
An Azure Active Directory account: https://azure.microsoft.com/en-ca/services/active-directory/
-
Access to Timestream.
-
Setting up the Azure enterprise non-gallery application using single sign-on (SSO) with SAML.
-
Setting up the IAM provider and roles:
-
Creating the SAML identity provider.
-
Creating an IAM role for access to Timestream.
-
Creating an IAM policy allowing the IAM role to generate an AWS STS token to connect to Timestream.
-
-
Start provisioning for Azure AD access to the newly created IAM IdP and Roles.
-
Configure Timestream JDBC driver to use Azure AD to access Timestream.
-
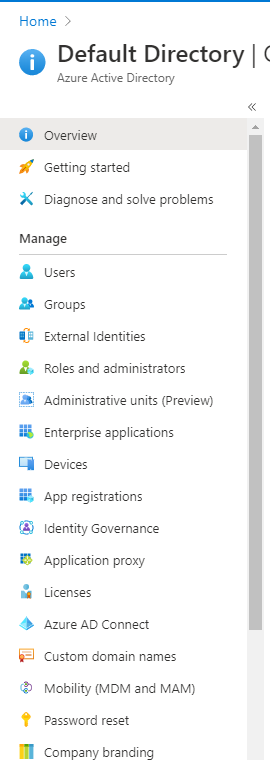
Sign in to Azure Portal.
-
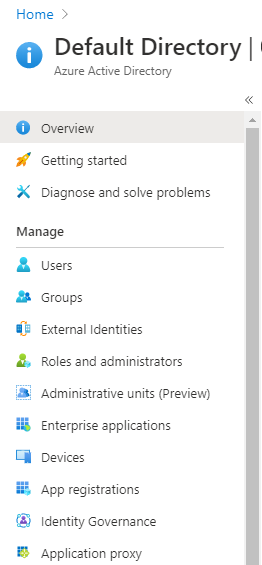
Select
Azure Active Directoryin the list of Azure services, this will redirect to theDefault Directorypage. -
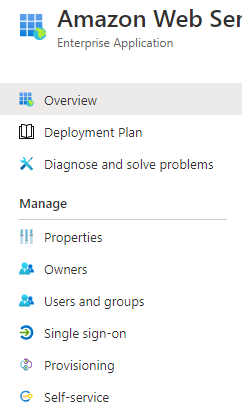
Select
Enterprise Applicationsunder theManagesection on the sidebar: -
Select
+ New application -
Find and select
Amazon Web Services -
Select
Single sign-onunderManagesection in the sidebar: -
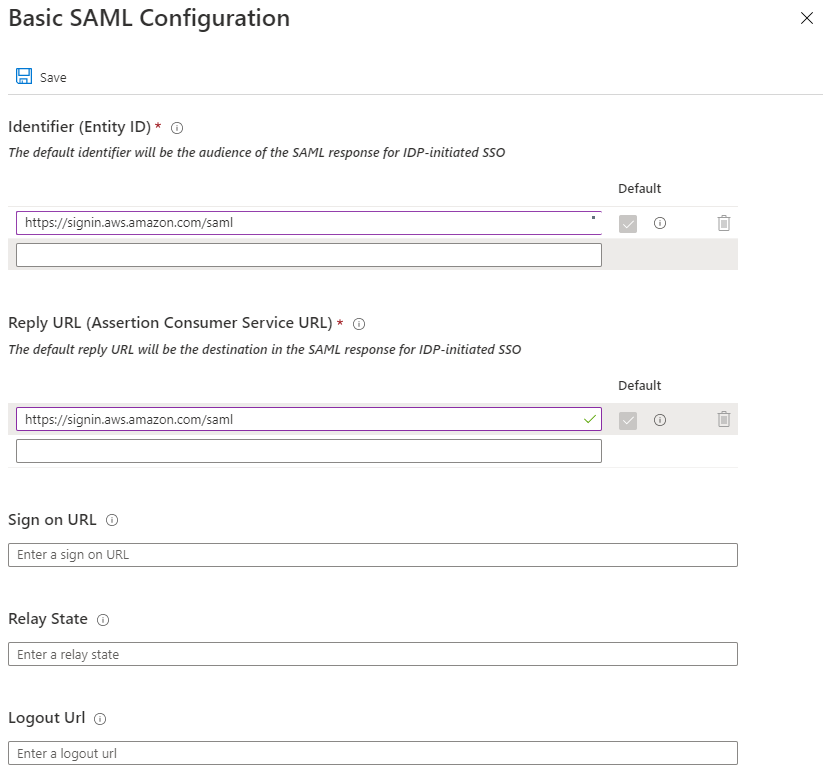
Choose SAML as the single sign-on method.
-
In the
Basic SAML Configuration, enterhttps://signin.aws.amazon.com/samlfor both theIdentifierand theReply URL: -
Click
Save. -
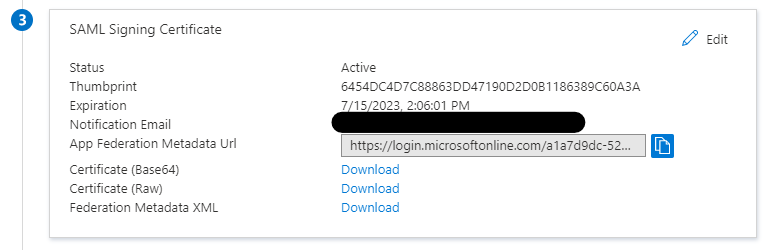
Download the
Federation Metadata XMLin theSAML Signing Certificatesection. This will be used when creating the IAM Identity Provider later. -
Go back to the
Default Directorypage, selectApp registrationsunderManage. -
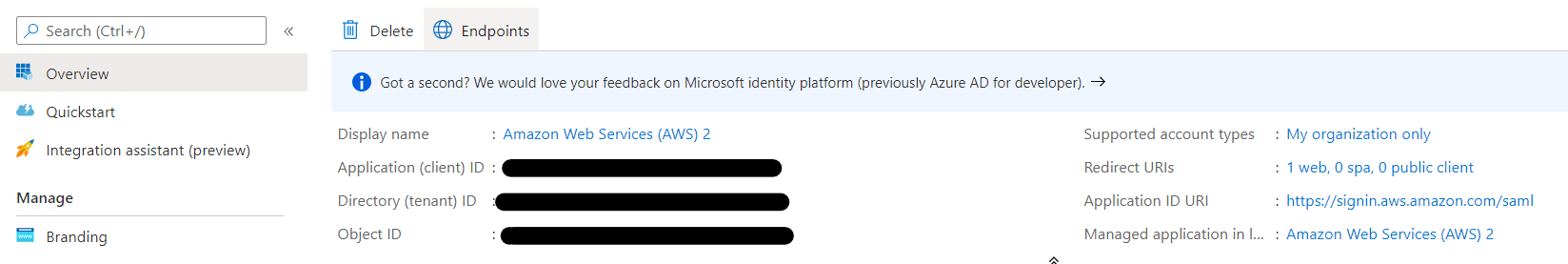
Select
Timestreamfrom theAll Applicationssection, the page will be redirected to the application’sOverviewpage. -
Take notes of the
Application (client) IDand theDirectory (tenant) ID, these values are required for when creating a connection: -
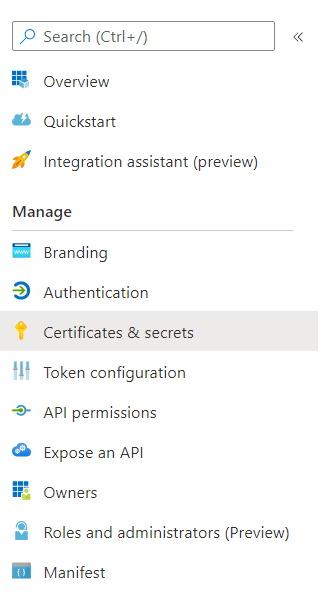
Select
Certificates & secrets -
Under
Client secrets, create a new client secret with+ New client secret. Take note of the generated value, this is required when creating a connection to Timestream. -
On the sidebar under
Manage, selectAPI permissions. -
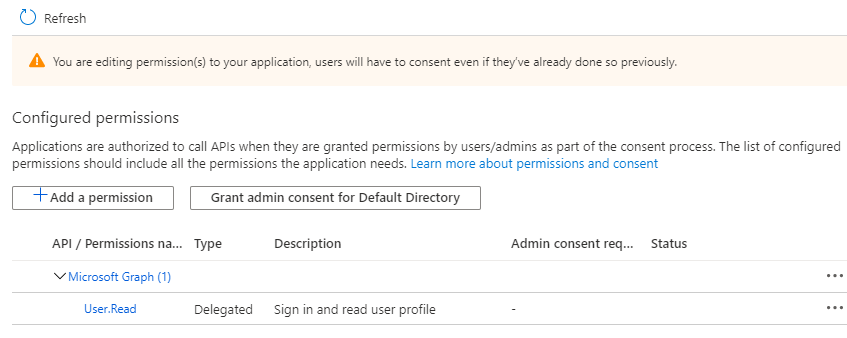
In the
Configured permissions, useAdd a permissionto grant Azure AD permission to sign in to Timestream. SelectMicrosoft Graphon theRequest API permissionspage. -
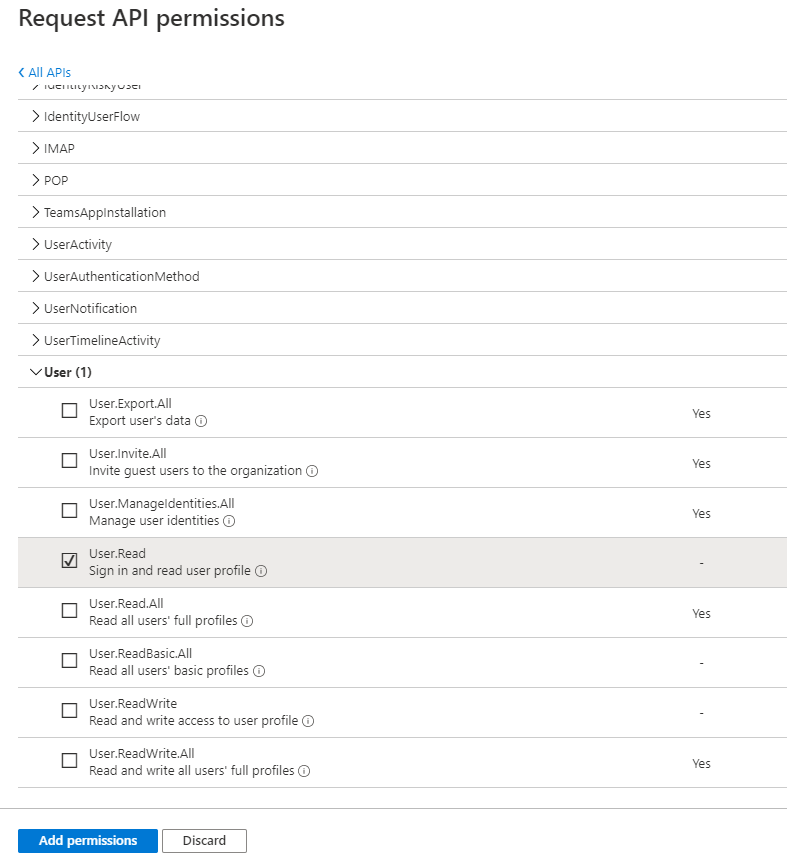
Select
Delegated permissions, select theUser.Readpermission.Click
Add permissions. -
Click
Grant admin consent for Default Directory.
Azure AD set up process is now complete.
This set up goes through the following:
-
Creating the SAML identity provider.
-
Creating an IAM role for access to Timestream.
-
Creating an IAM policy allowing the IAM role to generate an AWS STS token to connect to Timestream.
-
Sign in to the AWS Management Console.
-
Select
Servicesand selectIAMunderSecurity, Identity, & Compliance. -
Select
Identity providersunderAccess management. -
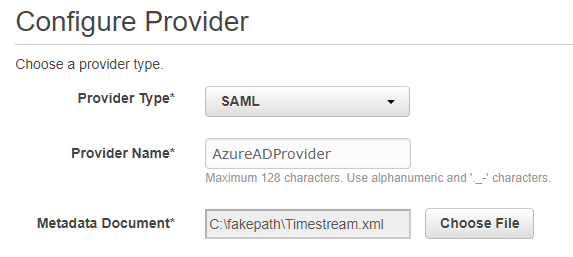
Select
Create Providerand chooseSAMLas the provider type. Enter the Provider Name, this example will use AzureADProvider. -
Upload the previously downloaded Federation Metadata XML file.
-
Select
NextthenCreate.
Upon completion, the page will be redirected back to the Identity providers page.
-
On the sidebar select
RolesunderAccess management. -
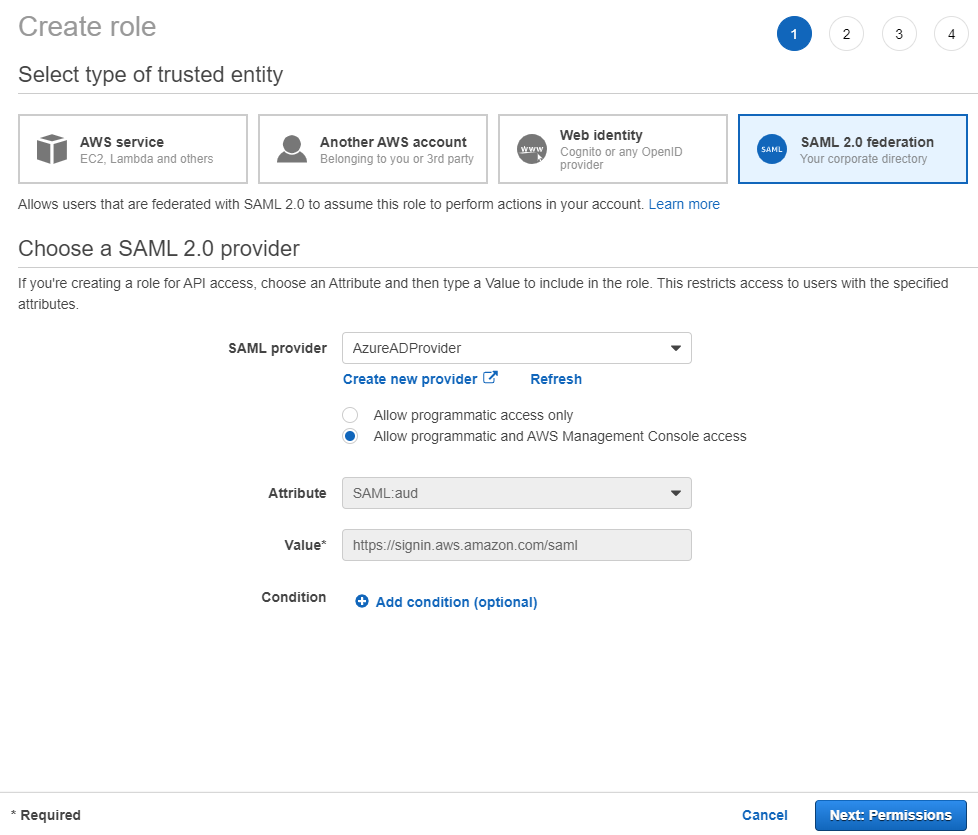
Select
Create role. -
Choose
SAML 2.0 federationas the trusted entity. -
Choose the Azure AD provider.
-
Select
Allow programmatic and AWS Management Console access. -
Click
Next: Permissions -
Attach permissions policies or continue to
Next:Tags. -
Add optional tags or continue to
Next:Review -
Enter a
Role name, this example will useAzureSAMLRole. -
Provide a role description.
-
Click
Create Roleto complete.
-
On the sidebar select
PoliciesunderAccess management. -
Select
Create policyand select theJSONtab. -
Add the following policy:
{ "Version": "2012-10-17", "Statement": [ { "Effect": "Allow", "Action": [ "iam:ListRoles", "iam:ListAccountAliases" ], "Resource": "*" } ] } -
Select
Create policy. -
Enter a policy name, this example will use
TimestreamAccessPolicy -
Select
Create Policy. -
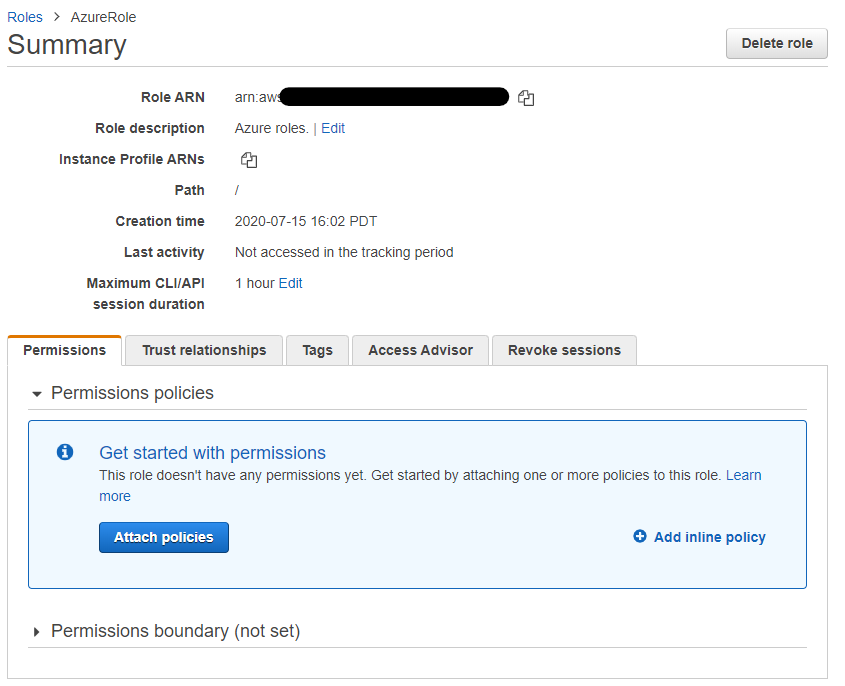
On the sidebar select
RolesunderAccess management. Select the previously created Azure AD role, selectAttach policiesunderPermissions. -
Select the previously created access policy.
-
Go back to Azure Portal.
-
Select
Azure Active Directoryin the list of Azure services, this will redirect to theDefault Directorypage. -
Select
Enterprise Applicationsunder theManagesection on the sidebar. -
Select
Provisioning -
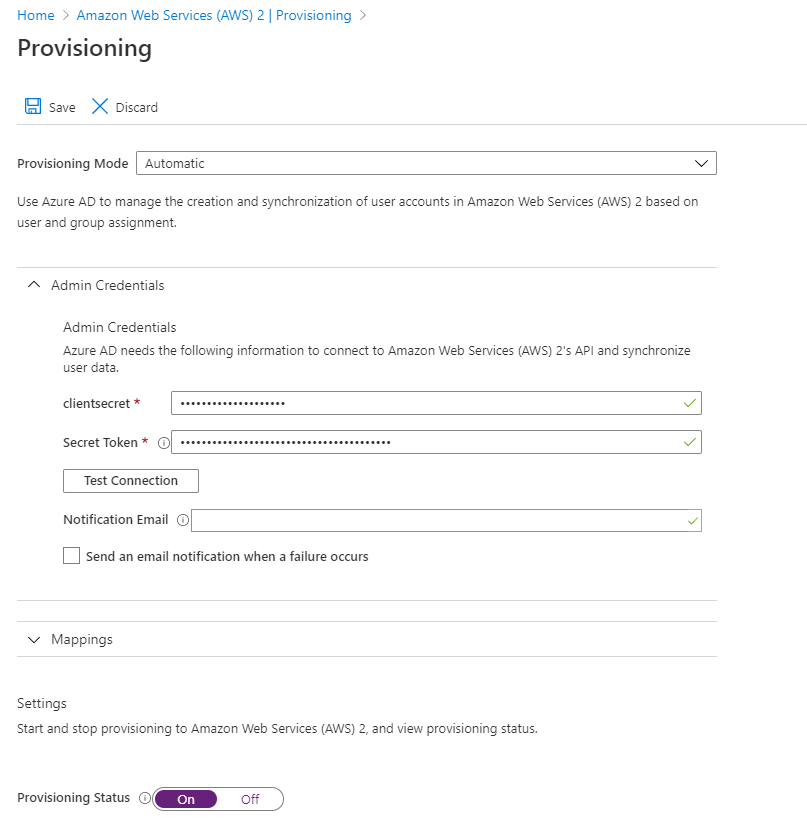
Select
Automatic modefor theProvisioning Method. -
Under Admin Credentials, enter
AwsAccessKeyIDforclientsecret, andSecretAccessKeyforSecret Token. -
Set the
Provisioning StatustoOn. -
Click save. This allows Azure AD to load the necessary IAM Roles.
-
Once the
Current cycle statusis completed, selectUsers and groupson the sidebar. -
Select
+ Add user. -
Select the Azure AD user to provide access to Timestream.
-
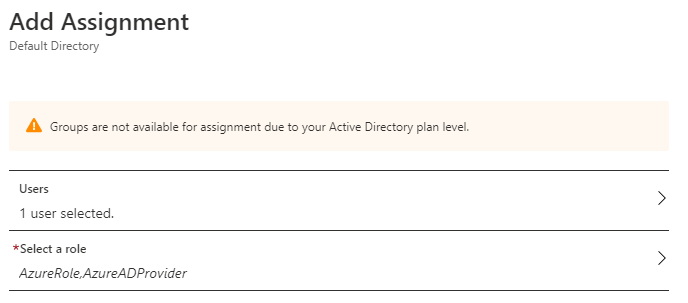
Select the IAM Azure AD role and the corresponding Azure Identity Provider created in AWS.
-
Select Assign.
Building the fully shaded JAR With All Dependencies Shaded Except SLF4J (amazon-timestream-jdbc-<version>-jar-with-all-dependencies.jar)
To build a fully shaded JAR, comment out the following two lines in the pom file in the /jdbc/pom.xml then run mvn install.
<scope>system</scope>
<systemPath>${project.basedir}/resources/aws-sdk-java-timestreamquery-1.11.805-SNAPSHOT.jar</systemPath>Since the Timestream Query SDK is not yet available on Maven Repository, these two lines are included to ensure that Github Actions can build the project.
To build the JAR with no dependencies, run mvn install.
To use the JAR with no dependencies in a Java application, the following required dependencies need to be added inside the pom file of your project.
<dependencies>
<dependency>
<groupId>com.amazonaws</groupId>
<artifactId>aws-java-sdk-core</artifactId>
<version>1.11.804</version>
</dependency>
<dependency>
<groupId>com.amazonaws</groupId>
<artifactId>aws-java-sdk-sts</artifactId>
<version>1.11.804</version>
</dependency>
<dependency>
<groupId>com.amazonaws</groupId>
<artifactId>timestreamquery</artifactId>
<version>1.11.805-SNAPSHOT</version>
</dependency>
<dependency>
<groupId>com.amazonaws</groupId>
<artifactId>timestreamwrite</artifactId>
<version>1.11.805-SNAPSHOT</version>
</dependency>
<dependency>
<groupId>com.google.guava</groupId>
<artifactId>guava</artifactId>
<version>28.0-jre</version>
</dependency>
<dependency>
<groupId>org.jsoup</groupId>
<artifactId>jsoup</artifactId>
<version>1.13.1</version>
</dependency>
<dependency>
<groupId>org.slf4j</groupId>
<artifactId>jul-to-slf4j</artifactId>
<version>1.7.24</version>
</dependency>
</dependencies>Building and using the Javadoc JAR to extract the Javadoc HTML files (amazon-timestream-jdbc-<version>-javadoc.jar)
Javadoc JAR builds with mvn install alongside the other JAR files. To extract the Javadoc HTML files, use the following command: jar -xvf amazon-timestream-jdbc-1.0.0-javadoc.jar
- Timestream does not support fully qualified table names.
- Timestream does not support the queries that contain ":" in the column aliases. Tools like Tableau may not work as expected.
- Timestream JDBC driver supports
getSchemasand does not supportgetCatalogs, so Tableau will show database as schemas instead of catalogs. - SQuirreL SQL Client does not support Rows and Arrays. Running a
SELECTquery that returns an Array or a Struct will result inUnknownType<2,003>/UnknownType<2,002>. - SQLWorkbench/J does not support using
Database Explorerto describe Timestream databases with anunderscorein the name, e.g.grafana_db. - SQLWorkbench/J does not display the array values within a
java.sql.Struct, instead SQLWorkbench/J displays the array's base type, e.g.com.tsshaded.amazonaws.services.timestreamquery.model.Row(DOUBLE, 2)instead of({1.3},2).
This library is licensed under the Apache 2.0 License.