This repository is under development ⛏ and maintained by Ziyao Wang, Mikel Dean, and Santiago Figueroa as part of the project: Adaptive Countermeasure based on Software-Defined Networking for Industrial Control Systems.
Check the meeting minutes ✏.
In this project, we practise SDN-based Attack & Defence on Modbus/TCP and HTTP protocols in an ICS network.
What is an ICS (Industrial Control System) network?
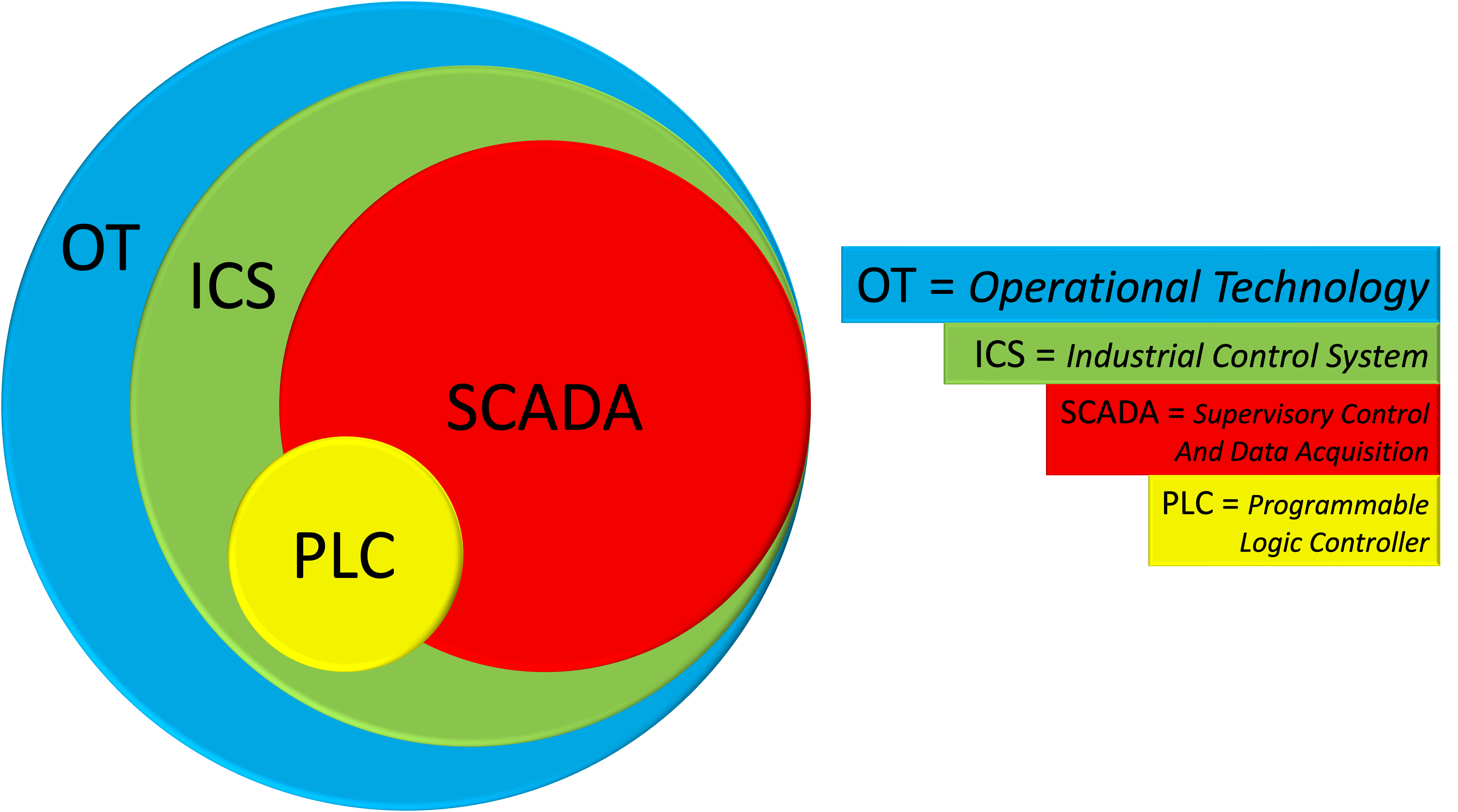
Figure 1 OT Components
Figure 1 shows the relationships among some ICS-related concepts.
- OT (Operational Technology) refers to any programmable system that can monitor and control devices, processes, and events.
- ICS (Industrial Control System) is an OT system used to control industrial processes such as manufacturing, production, and distribution.
- SCADA (Supervisory Control and Data Acquisition) is a type of ICS with HMI (Human Machine Interface) to monitor and control devices over long distances.
- PLC (Programmable Logic Controller) is another type of ICS with programmable memory that stores instructions to control industrial processes locally.
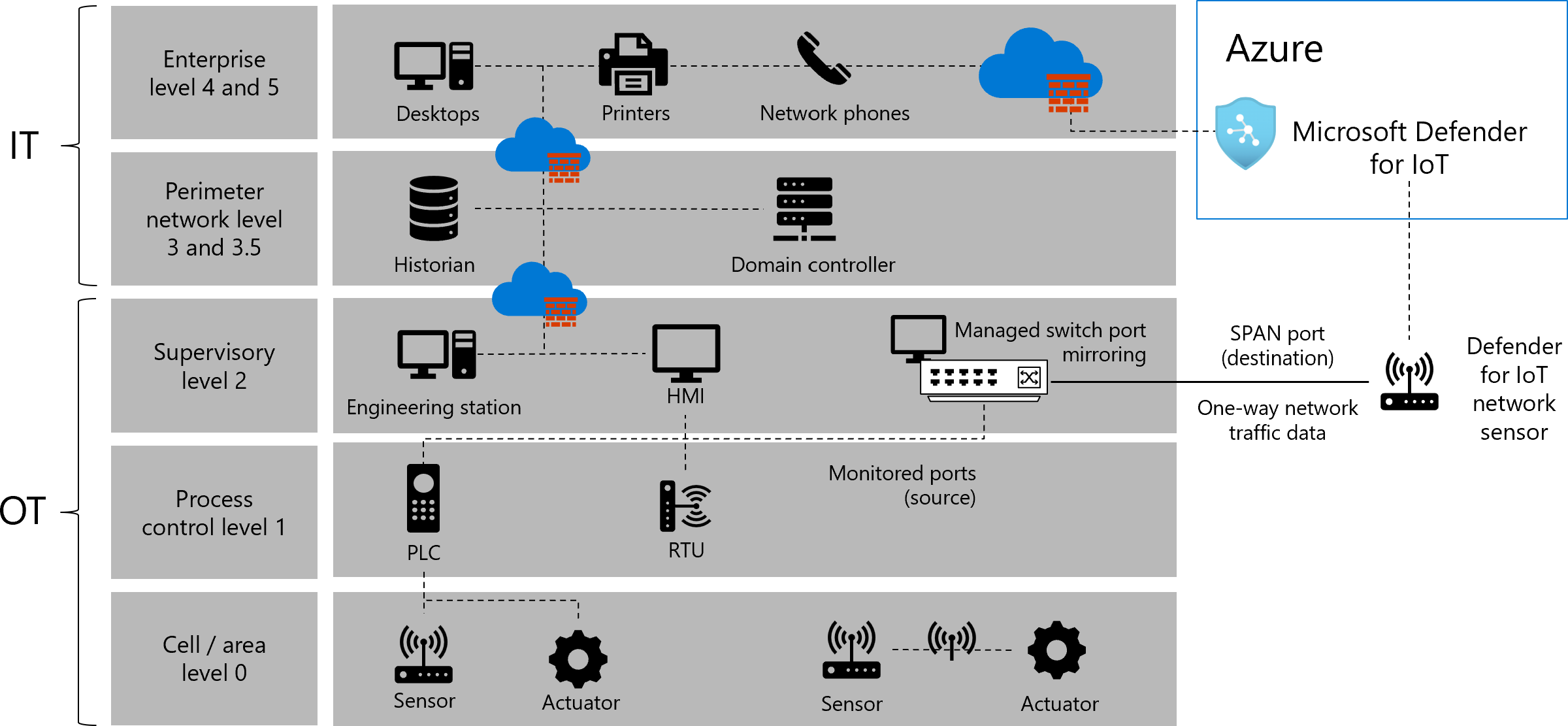
Figure 2 Purdue Model for ICS Security
Figure 2 shows a typical network topology of an industrial organisation. In the topology, the ICS network spreads across level 0, 1, and 2 of the Purdue model.
- PLC is often located in the factory. In the ICS network, the PLC in level 1 locally controls the sensors and actuators in level 0.
- SCADA is often located in the office. In the ICS network, the HMI (implements SCADA) in level 2 remotely monitors and controls the PLC in level 1.
In Figure 2, Microsoft presents its Azure solution to defend the ICS network using several managed switches in level 2 and a remote Microsoft defender. The remote Microsoft defender can interact with these managed switches to monitor and control flow of traffic in the ICS network, which resembles our SDN-based defence.
- Our SDN-based defence uses multiple Open vSwitches to replace the managed switches in level 2, and uses an ONOS SDN controller to replace the remote Microsoft defender. The ONOS SDN controller can interact with these Open vSwitches to monitor and control flow of traffic in the ICS network.
Our ICS network is deployed in GNS3 server, based on a generic base network.
How do we attack the Modbus/TCP and HTTP protocols in the ICS network?
Modbus/TCP is a type of Modbus protocol based on TCP (Transmission Control Protocol) that runs on Ethernet and uses TCP port 502.
- Modbus is a Client-Server protocol designed for communications between different ICSs. The Modbus server runs on TCP port
502. Modbus protocol has 3 implementations: Modbus/RTU, Modbus/ASCII, and Modbus/TCP. The first two of them run on serial, while the Modbus/TCP runs on Ethernet. As mentioned above, PLC and SCADA are 2 types of ICSs. Modbus/TCP protocol is mainly used for PLC and SCADA to communicate over Ethernet. In this case, PLC is Modbus server and SCADA is Modbus client.
HTTP protocol is widely known and its description can be easily found on the Internet.
- SCADA has a HMI in form of a web UI. Thereby, SCADA can be considered a HTTP server.
We use the endpoint DoS (Denial of Service) attack on Modbus/TCP and HTTP protocols.
- We use injection attack on Modbus/TCP to cause DoS on PLC (the Modbus server).
- We use Slowloris attack on HTTP to cause DoS on SCADA (the HTTP server).
Our attack tools are deployed in a Kali Linux, a Debian-based Linux distro with common attack tools bundled. In the case, the Kali Linux can be considered as the attacker.
How do we use SDN (Software-Defined Networking) to defend the ICS network against the attack?
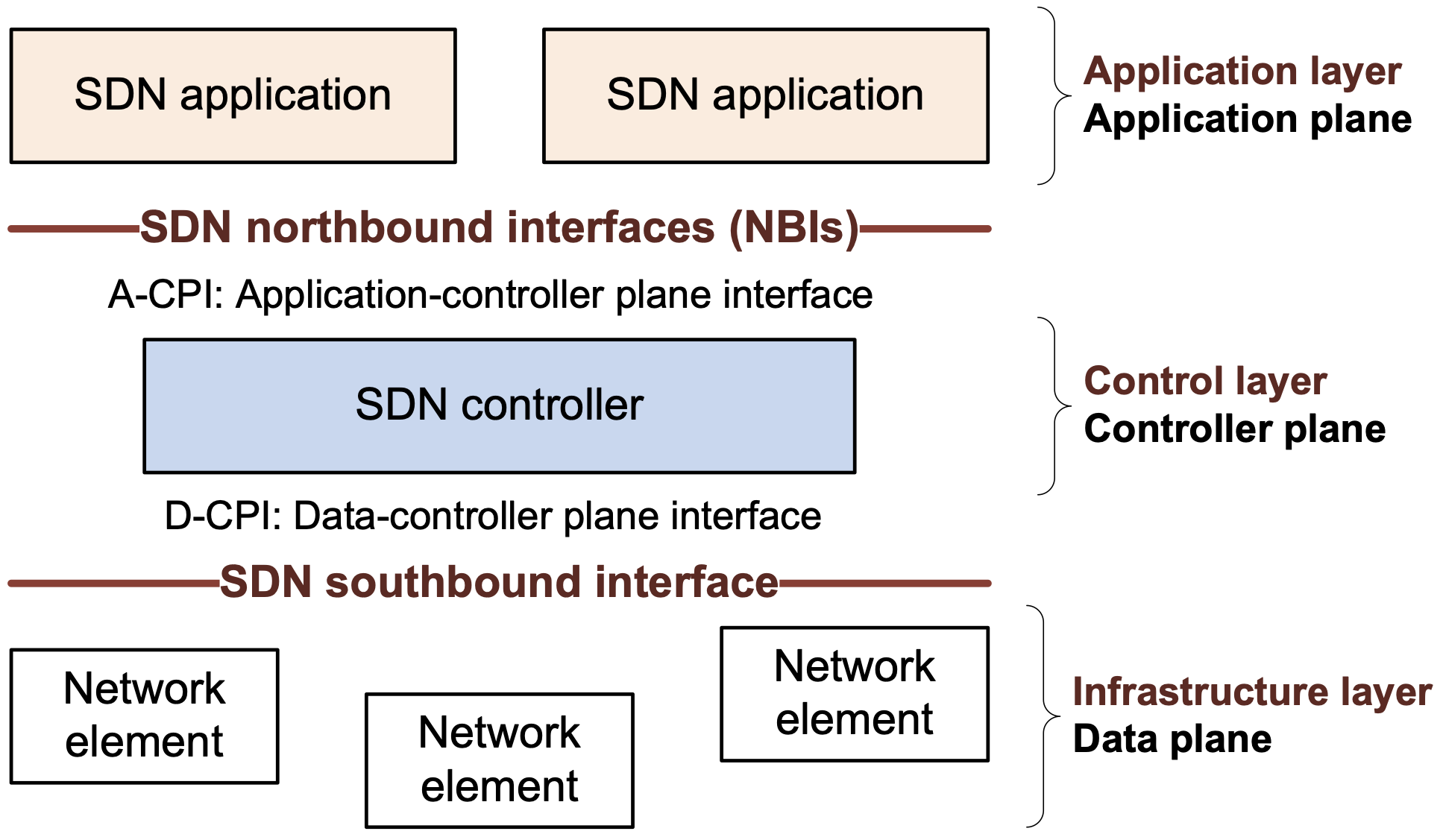
Figure 3 SDN Architecture
SDN (Software-Defined Networking) uses software to control the connectivity of network and the flow of traffic, along with inspection and modification of the traffic.
SDN has 3 layers (planes), as shown in Figure 3.
- The data plane contains network devices such as routers and switches. The ICS network is in the data plane.
- The controller plane sits the SDN controller that monitors and controls the data plane via the southbound interface. OpenFlow is a well-known southbound protocol.
- The application plane is for applications to monitor and control the SDN controller via the northbound interface.
Our SDN-based defence deploys multiple Open vSwitches in the data plane, and deploys an ONOS SDN controller in the controller plane to monitor and control the ICS network (the data plane) via these Open vSwitches.
- The ONOS SDN controller can interact with Open vSwitches via OpenFlow protocol. In the case, we can consider these Open vSwitches as "SDN clients" and the ONOS SDN controller as "SDN server".
- As mentioned above in Figure 2, our SDN-based defence resembles Microsoft's Azure solution to the ICS network security.
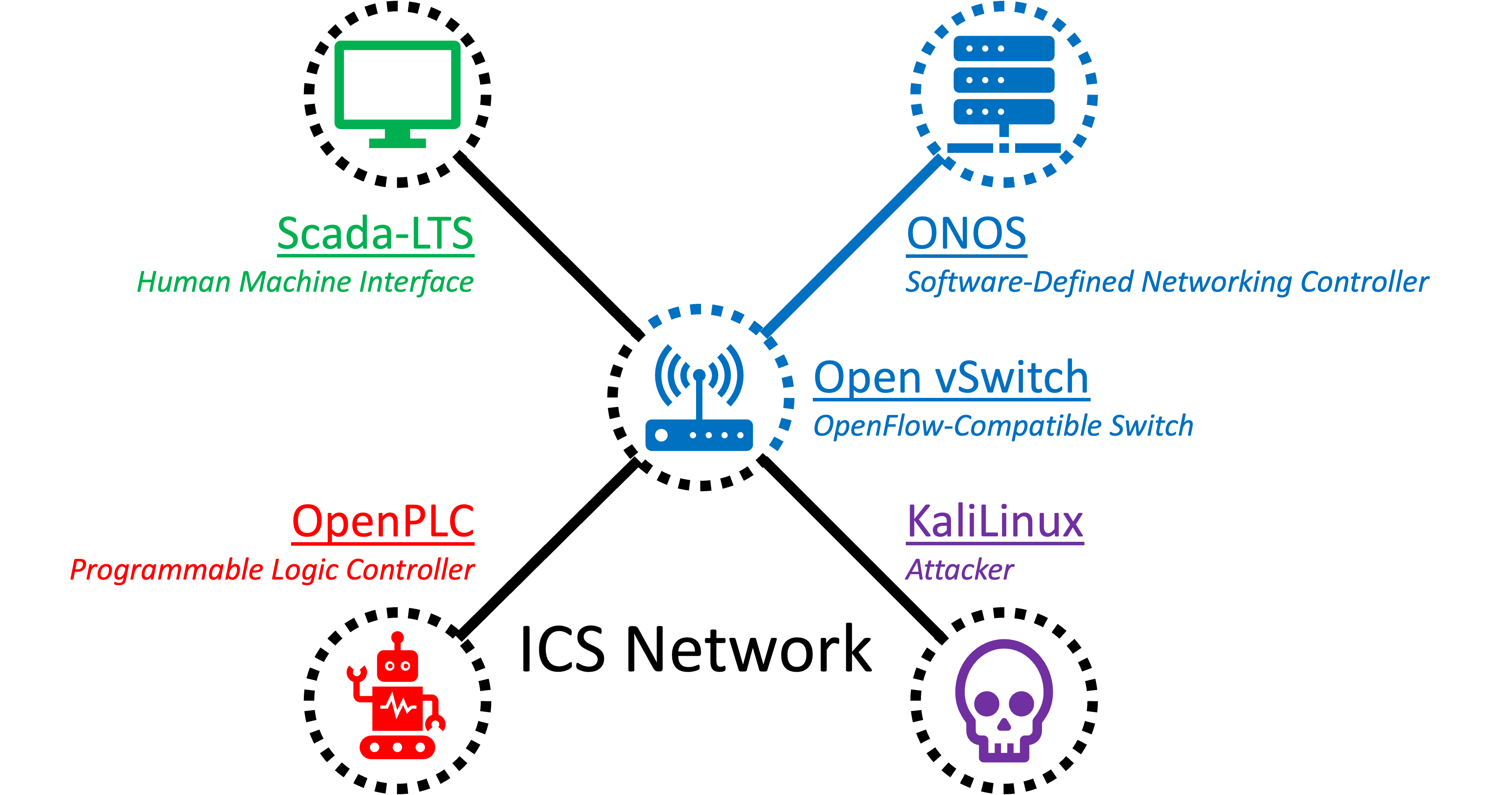
Figure 4 ICS Network Topology
Figure 4 is our ICS network topology where Attack & Defence takes place.
- OpenPLC (implements PLC) (the Modbus server)
- Scada-LTS (implements SCADA) (the Modbus client) (the HTTP server)
- KaliLinux (implements attacker)
- Open vSwitch (implements "SDN client")
- ONOS SDN controller (implements "SDN server")
- Install GNS3 client and server
- Deploy generic base network in GNS3 server
- Deploy ICS network in GNS3 server
- Conduct the injection attack on Modbus/TCP
- Deploy countermeasure in ONOS against Modbus/TCP DoS attack
- Change the ASAv firewall to pfsense/opnsense or find a licenced firewall
- Include the level-0 components of the Purdue model
- Attack and defence on OSPF
- Use other forms of attack different from the endpoint DoS