[~] Version 2.0 IS OUT !! | 26/12/2019 06:57AM GMT+2 |
Lockdoor v2.0 is OUT!
Lockdoor is now available on Docker
Fixing Docker issue
Lockdoor is now optimized for quick execution
Lockdoor is now availabe on Redcould
Bugs Fixing for 7 tools
fixing (apt) package manager problems
| Support me 💰 : |
|---|
|
|
| ============= |
| Versions 🔐 : |
- Information Gathring Tools (21)
- Web Hacking Tools(15)
- Reverse Engineering Tools (15)
- Exploitation Tools (6)
- Pentesting & Security Assessment Findings Report Templates (6)
- Password Attack Tools (4)
- Shell Tools + Blackarch's Webshells Collection (4)
- Walk Throughs & Pentest Processing Helpers (3)
- Encryption/Decryption Tools (2)
- Social Engineering tools (1)
- All you need as Privilege Escalation scripts and exploits
- Working on Kali,Ubuntu,Arch,Fedora,Opensuse and Windows (Cygwin)
- Information Gathring tools (13)
- Web Hacking Tools (9)
- Working on Kali,Ubuntu,Arch,Fedora,Opensuse and Windows (Cygwin)
- Some bugs That I'm fixing with time so don't worry about that.
| Blogs & Articles 📰 : |
|---|
|
|
|
|
|
|
|
|
|
|
|
| ============= |
| Overview 📙 : |
| ============= |
| LockDoor is a Framework aimed at helping penetration testers, bug bounty hunters And cyber security engineers. |
| This tool is designed for Debian/Ubuntu/ArchLinux based distributions to create a similar and familiar distribution for Penetration Testing. But containing the favorite and the most used tools by Pentesters. |
| As pentesters, most of us has his personal ' /pentest/ ' directory so this Framework is helping you to build a perfect one. |
| With all of that ! It automates the Pentesting process to help you do the job more quickly and |
easily. |
| ============= |
| Features 📙 : |
| ============= |
Added value : (what makes it different from other frameworks). |
| Pentesting Tools Selection 📙 : |
| -------------------------- |
|
|
|
|
| Resources and cheatsheets 📙 : (Added value) |
| -------------------------- |
|
|
| ============= |
| Screenshots 💻 : |
| Kali Linux | Ubuntu | Arch Linux | Fedora | Opensuse | Windows (Cygwin) |
|---|---|---|---|---|---|
 |
 |
 |
 |
 |
 |
| Installation 🛠️ : |
|---|
| **The recommended way to use Lockdoor is by pulling the Docker Image so you will not have |
to worry about dependencies issues.** |
| **A Docker image is available on Docker Hub and automatically re-built at each update: |
https://hub.docker.com/r/sofianehamlaoui/lockdoor. It is initially based on the official debian docker image (debian).** |
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
| ============= |
| Lockdoor Tools contents 🛠️ : |
Information Gathering 🔎 : -------------------------- - Tools: - dirsearch : A Web path scanner - brut3k1t : security-oriented bruteforce framework - gobuster : DNS and VHost busting tool written in Go - Enyx : an SNMP IPv6 Enumeration Tool - Goohak : Launchs Google Hacking Queries Against A Target Domain - Nasnum : The NAS Enumerator - Sublist3r : Fast subdomains enumeration tool for penetration testers - wafw00f : identify and fingerprint Web Application Firewall - Photon : ncredibly fast crawler designed for OSINT. - Raccoon : offensive security tool for reconnaissance and vulnerability scanning - DnsRecon : DNS Enumeration Script - Nmap : The famous security Scanner, Port Scanner, & Network Exploration Tool - sherlock : Find usernames across social networks - snmpwn : An SNMPv3 User Enumerator and Attack tool - Striker : an offensive information and vulnerability scanner. - theHarvester : E-mails, subdomains and names Harvester - URLextractor : Information gathering & website reconnaissance - denumerator.py : Enumerates list of subdomains - other : other Information gathering,recon and Enumeration scripts I collected somewhere. - Frameworks: - ReconDog : Reconnaissance Swiss Army Knife - RED_HAWK : All in one tool for Information Gathering, Vulnerability Scanning and Crawling - Dracnmap : Info Gathering Framework
- Tools:
- Spaghetti : Spaghetti - Web Application Security Scanner
- CMSmap : CMS scanner
- BruteXSS : BruteXSS is a tool to find XSS vulnerabilities in web application
- J-dorker : Website List grabber from Bing
- droopescan : scanner , identify , CMSs , Drupal , Silverstripe.
- Optiva : Web Application Scanne
- V3n0M : Pentesting scanner in Python3.6 for SQLi/XSS/LFI/RFI and other Vulns
- AtScan : Advanced dork Search & Mass Exploit Scanner
- WPSeku : Wordpress Security Scanner
- Wpscan : A simple Wordpress scanner written in python
- XSStrike : Most advanced XSS scanner.
- Sqlmap : automatic SQL injection and database takeover tool
- WhatWeb : the Next generation web scanner
- joomscan : Joomla Vulnerability Scanner Project
- Frameworks:
- Dzjecter : Server checking Tool
Privilege Escalation : - windows-privesc-check.py - windows-privesc-check.exe - MySql : - raptor_udf.c - raptor_udf2.c
- Radare2 : unix-like reverse engineering framework
- VirtusTotal : VirusTotal tools
- Miasm : Reverse engineering framework
- Mirror : reverses the bytes of a file
- DnSpy : .NET debugger and assembly
- AngrIo : A python framework for analyzing binaries ( Suggested by @Hamz-a )
- DLLRunner : a smart DLL execution script for malware analysis in sandbox systems.
- Fuzzy Server : a Program That Uses Pre-Made Spike Scripts to Attack VulnServer.
- yara : a tool aimed at helping malware researchers toidentify and classify malware samples
- Spike : a protocol fuzzer creation kit + audits
- other : other scripts collected somewhere
- Findsploit : Find exploits in local and online databases instantly
- Pompem : Exploit and Vulnerability Finder
- rfix : Python tool that helps RFI exploitation.
- InUrlBr : Advanced search in search engines
- Burpsuite : Burp Suite for security testing & scanning.
- linux-exploit-suggester2 : Next-Generation Linux Kernel Exploit Suggester
- other : other scripts I collected somewhere.
- WebShells : BlackArch's Webshells Collection
- ShellSum : A defense tool - detect web shells in local directories
- Weevely : Weaponized web shell
- python-pty-shells : Python PTY backdoors
- crunch : a wordlist generator
- CeWL : a Custom Word List Generator
- patator : a multi-purpose brute-forcer, with a modular design and a flexible usage
Encryption - Decryption 🛡️: -------------------------- - Codetective : a tool to determine the crypto/encoding algorithm used - findmyhash : Python script to crack hashes using online services
- scythe : an accounts enumerator
| Lockdoor Resources contents 📚 : |
Information Gathering 🔎 : -------------------------- - Cheatsheet_SMBEnumeration - configuration_management - dns_enumeration - file_enumeration - http_enumeration - information_gathering_owasp_guide - miniserv_webmin_enumeration - ms_sql_server_enumeration - nfs_enumeration - osint_recon_ng - passive_information_gathering - pop3_enumeration - ports_emumeration - rpc_enumeration - scanning - smb_enumeration - smtp_enumeration - snmb_enumeration - vulnerability_scanning
Privilege Escalation
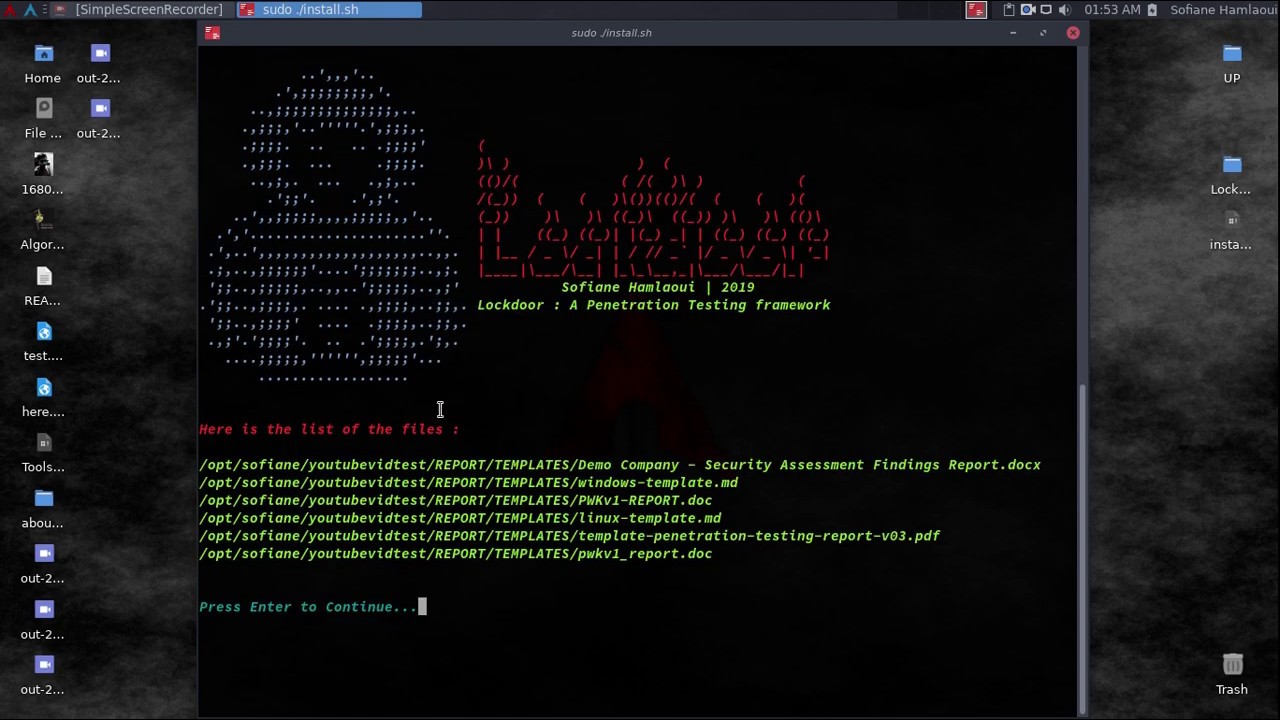
Pentesting & Security Assessment Findings Report Templates 📝 : -------------------------- - Demo Company - Security Assessment Findings Report.docx - linux-template.md - PWKv1-REPORT.doc - pwkv1_report.doc - template-penetration-testing-report-v03.pdf - windows-template.md - OSCP-OS-XXXXX-Lab-Report_Template3.2.docx - OSCP-OS-XXXXX-Exam-Report_Template3.2.docx - CherryTree_template.ctb Reverse Engineering ⚡ : -------------------------- - Buffer_Overflow_Exploit - buffer_overflows - gdb_cheat_sheet - r2_cheatsheet - win32_buffer_overflow_exploitation - 64_ia_32_jmp_instructions - course_notes - debuging - IntelCodeTable_x86 - Radare2 cheat sheet - x86_assembly_x86_architecture - x86_opcode_structure_and_instruction_overview
- auxiliary_info.md
- Cheatsheet_ApacheSSL
- Cheatsheet_AttackingMSSQL
- Cheatsheet_DomainAdminExploitation
- Cheatsheet_SQLInjection
- Cheatsheet_VulnVerify.txt
- code-execution-reverse-shell-commands
- file_upload.md
- html5_cheat_sheet
- jquery_cheat_sheet_1.3.2
- sqli
- sqli_cheatsheet
- sqli-quries
- sqli-tips
- web_app_security
- web_app_vulns_Arabic
- Xss_1
- Xss_2
- xss_actionscript
- xxe
- Fork it ( https://github.com/SofianeHamlaoui/Lockdoor-Framework/fork )
- Create your feature branch
- Commit your changes
- Push to the branch
- Create a new Pull Request