Shieldoo Mesh is a network administration tool leveraging the power of open-source technology, Nebula. Developed at Slack by Nate Brown and Ryan Huber, Nebula has been proven to securely manage networks for millions of users around the globe. Shieldoo Mesh encapsulates the intricate network security in a simple, user-friendly application, allowing devices to connect securely with a few clicks, no matter where they are located.
See home page of our project: https://shieldoo.io
-
Public IP Not Required: Forget about the challenges of configuring a public IP. Shieldoo simplifies the process, making your network less vulnerable and more secure.
-
Lighthouse Technology: Our unique "lighthouse" system guides each node to its destination. As a node connects to your network, it communicates with the lighthouse, which directs your device to the server node using the established connection.
-
Single Sign-On: You can log into your secure network using Google or Microsoft accounts, simplifying the login process and improving the user experience.
-
Zero Trust: We've built Shieldoo based on the Zero Trust principle, which requires identity verification for all endpoints on the network and checks service access eligibility.
-
Time-limited Access: Shieldoo supports temporary access rights, enabling admins to control and monitor access to the network over specified time periods.
-
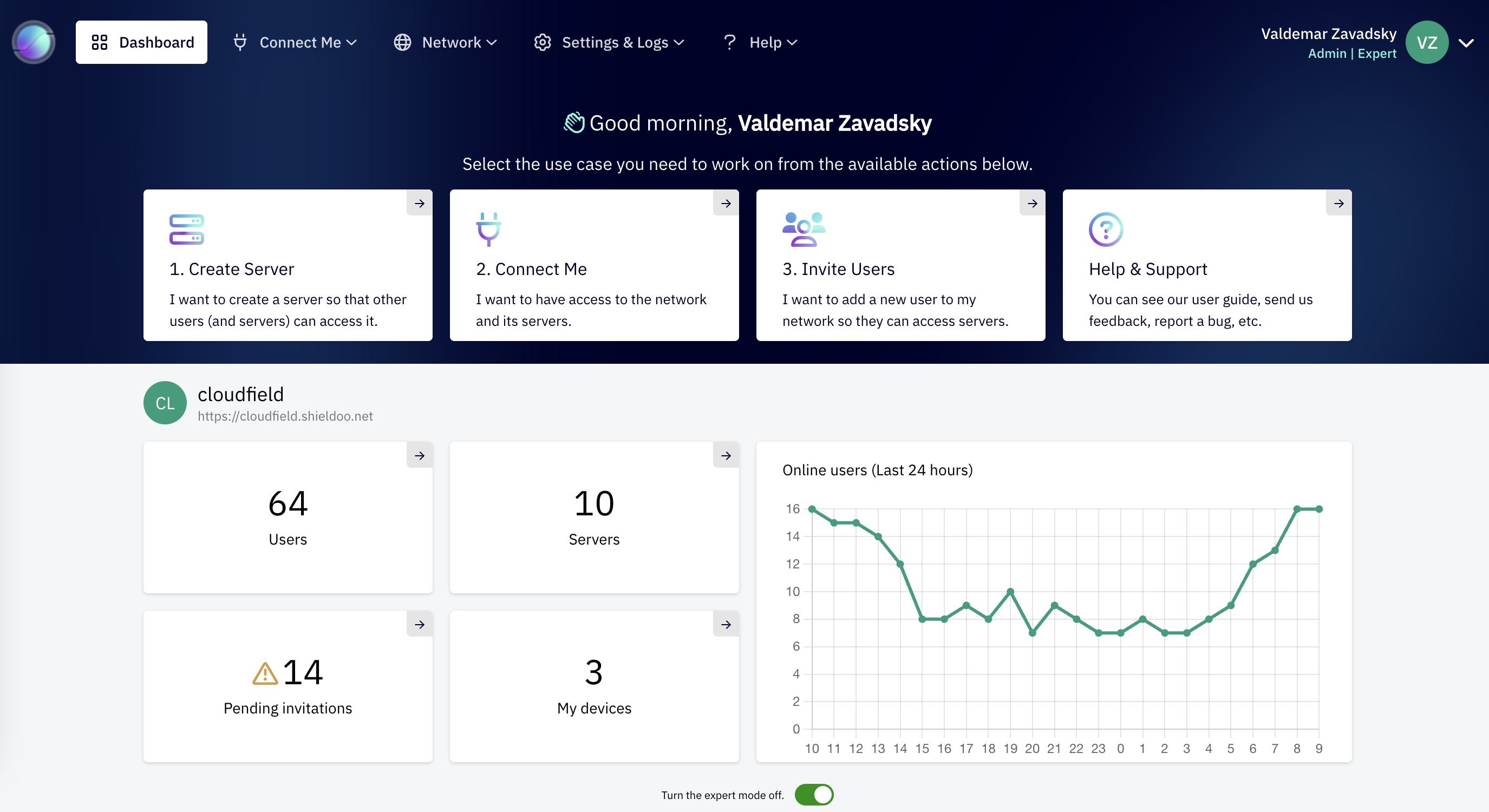
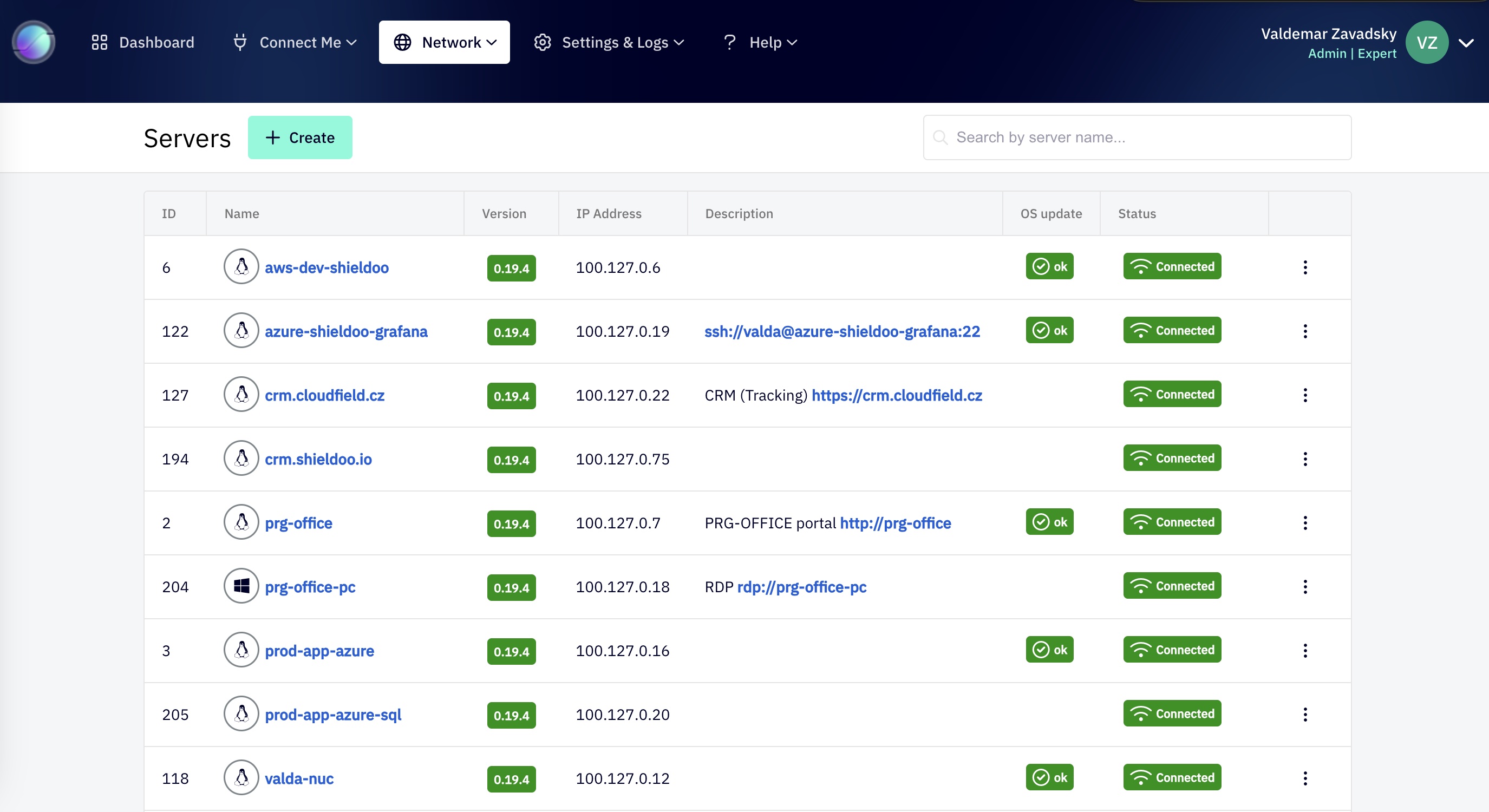
Traffic Monitoring: As an administrator, you can monitor which endpoint connects where and when, helping you track usage statistics and identify suspicious activity.
-
Easy Management: Shieldoo Mesh Admin makes network management a breeze, removing complexities like subnet and certificate hassles, and providing a user-friendly interface.
-
Lightweight Operation: Shieldoo Mesh Admin doesn't demand robust servers or extensive cloud capacity. Devices can communicate peer-to-peer, requiring minimal network backend interaction.
- Create a server in the public cloud or your chosen location.
- Install Docker on the server.
- Obtain the public IP address of the server.
- Enable ports 80/TCP, 443/TCP, 4242/UDP on your firewall.
- Clone this repository using git.
- Navigate into the cloned repository/server.
- Update the .env file with the following essential information:
ADMIN_EMAIL: The email of the admin user.SHIELDOO_DOMAIN: The domain name of Shieldoo Mesh (will be used foradmin.*,wss.*andlogin.*subdomains). It means valuemyshieldoo.example.comwill be used foradmin.myshieldoo.example.com,wss.myshieldoo.example.comandlogin.myshieldoo.example.com.- LIGHTHOUSE_IP: The public IP address of the server.
AAD_CLIENTID: Your Azure AD client ID.AAD_CLIENTSECRET: Your Azure AD client secret.AAD_TENANTID: Your Azure AD tenant ID.GOOGLE_CLIENTID: Your Google client ID.GOOGLE_CLIENTSECRET: Your Google client secret.
- Run
. .env;sed -i s/shieldoodev.cloudfield.dev/$SHIELDOO_DOMAIN/ docker-compose.yamlto update thedocker-compose.yamlwith your$SHIELDOO_DOMAIN. - Run
docker-compose up -dto start the Shieldoo Mesh server.
⚠️ Warning - For a production environment, generate the following secrets:
SERVER_JOBAPIKEY: The secret for communication with Shieldoo job API.OAUTHSERVER_SECRET: Shieldoo's internal OAuth server secret.LIGHTHOUSES_SECRET: The secret for lighthouse communication.- Generate JWKS keys for Shieldoo's OAuth server in folder shieldoo-mesh-oauth/jwks - see there
- generate new CA keys in folder shieldoo-mesh-admin/ca - see there
⚠️ Warning - You can enable also Basic Authentication for Shieldoo Mesh Admin portal. You can use the following ENV variables to enable and configure it, but than you have to solve security consideration implications by yourself (for example no MFA, no SSO, no password rotation, etc.):
BASICAUTH_ENABLED="true"BASICAUTH_USERS=''The
BASICAUTH_USERSvariable is a list of users in the htaccess format. You can use this online generator to generate the list of users. Or you can use command line toolhtpasswdto generate the list of users byhtpasswd -nm usernamethen copy the result into here separated by|character.
For local development, you can use configurations and docker-compose.override.yml file from the localhost folder.
Localhost configuration is shipped with enabled Basic Authentication for Shieldoo Mesh Admin portal. You can use the following credentials to log in:
- email:
user@example.com - password:
password
Basic Authentication is enabled and configured by these ENV variables:
BASICAUTH_ENABLED="true"BASICAUTH_USERS='user@example.com:$apr1$jI2jqzEg$MyNJQxhcZFNygXP79xT/p.|'
- Shieldoo Mesh Admin
- Shieldoo Mesh FrontEnd
- Shieldoo Mesh Lighthouse
- Shieldoo Mesh OAuth Server
- Shieldoo Mesh Client (for users and servers in mesh network)
- Go to Azure Active Directory -> App registrations -> New registration
- Fill in the name of the application and click Register
- Go to Certificates & secrets -> New client secret
- Fill in the name of the secret and click Add
- Copy the value of the secret and store it in a safe place
- Configure Login redirect URIs, use the following format:
https://login.<your.domain.name>/callback/microsoft - Go to Overview and copy the Application (client) ID
- Copy Tenant ID from Overview
See official documentation for more information: https://docs.microsoft.com/en-us/azure/active-directory/develop/quickstart-register-app
- Go to Google Cloud Console -> APIs & Services -> Credentials -> Create Credentials -> OAuth client ID
- Fill in the name of the application and click Create
- Configure Authorized redirect URIs, use the following format:
https://login.<your.domain.name>/callback/google - Copy the Client ID and Client Secret
See official documentation for more information: https://developers.google.com/identity/protocols/oauth2/openid-connect
You can generate an RSA keypair using either OpenSSL or ssh-keygen:
openssl genrsa -out keypair.pem 2048
openssl rsa -in keypair.pem -pubout -out app.rsa.pub
openssl pkcs8 -topk8 -inform PEM -outform PEM -nocrypt -in keypair.pem -out app.rsassh-keygen -t rsa -b 4096 -m PEM -f app.rsa
# Don't add passphrase
openssl rsa -in app.rsa -pubout -outform PEM -out app.rsa.pubTo set up a Nebula CA, you'll need:
1. The Nebula binaries or Distribution Packages for your specific platform. Specifically you'll need nebula-cert and the specific nebula binary for each platform you use.
./nebula-cert ca -duration 118760h -name "Myorganization, Inc"
This will create files named ca.key and ca.cert in the current directory. The ca.key file is the most sensitive file you'll create, because it is the key used to sign the certificates for individual nebula nodes/hosts. Move both files to the folder shieldoo-mesh-admin/ca.