Kubernetes Fury Auth provides Authentication Management for Kubernetes Fury Distribution (KFD).
If you are new to KFD please refer to the official documentation on how to get started with the distribution.
Kubernetes Fury Auth uses CNCF recommended, Cloud Native projects, such as the Dex identity provider, and Pomerium as an identity-aware proxy to enable secure access to internal applications.
Kubernetes Fury Auth provides the following packages:
| Package | Version | Description |
|---|---|---|
| Pomerium | v0.25.0 |
Identity-aware proxy that enables secure access to internal applications. |
| Dex | v2.38.0 |
Dex is a Federated OpenID Connect Provider. |
| Gangplank | v1.0.0 |
Enable authentication flows via OIDC for a kubernetes cluster. |
| Kubernetes Version | Compatibility | Notes |
|---|---|---|
1.26.x |
✅ | No known issues. |
1.27.x |
✅ | No known issues. |
1.28.x |
✅ | No known issues. |
1.29.x |
✅ | No known issues. |
Check the compatibility matrix for additional information on previous releases of the modules.
| Tool | Version | Description |
|---|---|---|
| furyctl | >=0.6.0 |
The recommended tool to download and manage KFD modules and their packages. To learn more about furyctl read the official documentation. |
| kustomize | >=3.5.0 |
Packages are customized using kustomize. To learn how to create your customization layer with kustomize, please refer to the repository. |
- List the packages you want to deploy and their version in a
Furyfile.yml:
versions:
auth: "v0.2.0"
bases:
- name: auth/pomerium
- name: auth/dex
- name: auth/gangplankSee
furyctldocumentation for additional details aboutFuryfile.ymlformat.
-
Execute
furyctl vendor -Hto download the packages -
Inspect the download packages under
./vendor/katalog/auth/. -
Define a
kustomization.yamlthat includes the./vendor/katalog/authdirectory as a resource.
resources:
- ./vendor/katalog/auth/pomerium
- ./vendor/katalog/auth/dex
- ./vendor/katalog/auth/gangplank- Create the configuration file for Dex (here's an LDAP-based example) and add it as a secret to the
kustomization.yamlfile, like this:
secretGenerator:
- name: dex
namespace: kube-system
files:
- config.yml=./secrets/dex/config.ymlℹ️ read more on Dex's readme.
⛔️ Before proceeding, follow the instructions in Pomerium's package readme and Gangplank's readme to configure them.
- Finally, to deploy the module to your cluster, execute:
kustomize build . | kubectl apply -f -KFD Auth module integrates out-of-the-box with KFD's Monitoring module. Providing metrics and dashboards to visualize the status of its components.
In particular:
- Dex exposes standard Go adapter metrics, the metrics are automatically scrapped by Prometheus when using KFD Monitoring module but there are no Grafana dashboards nor alerts defined.
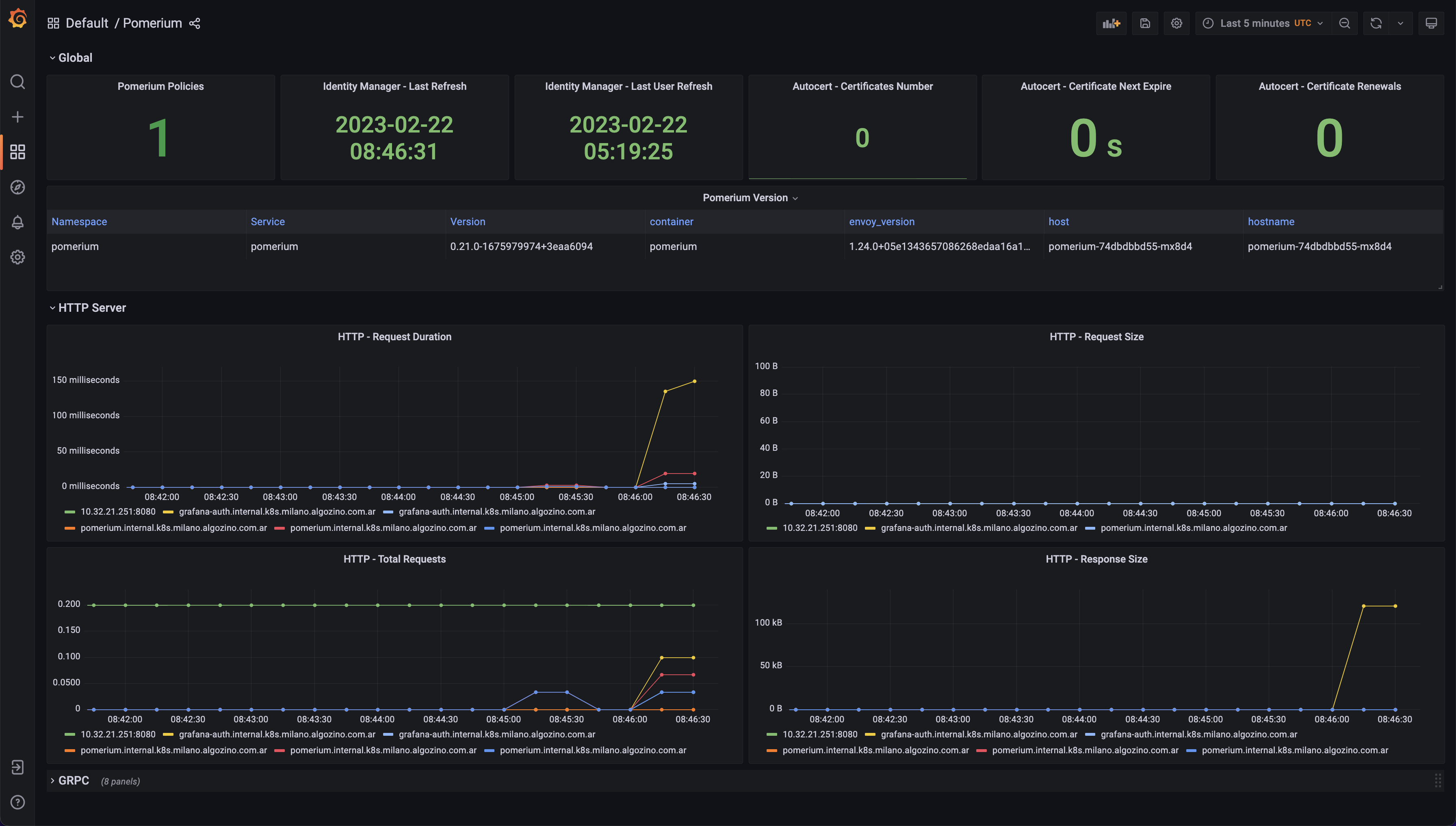
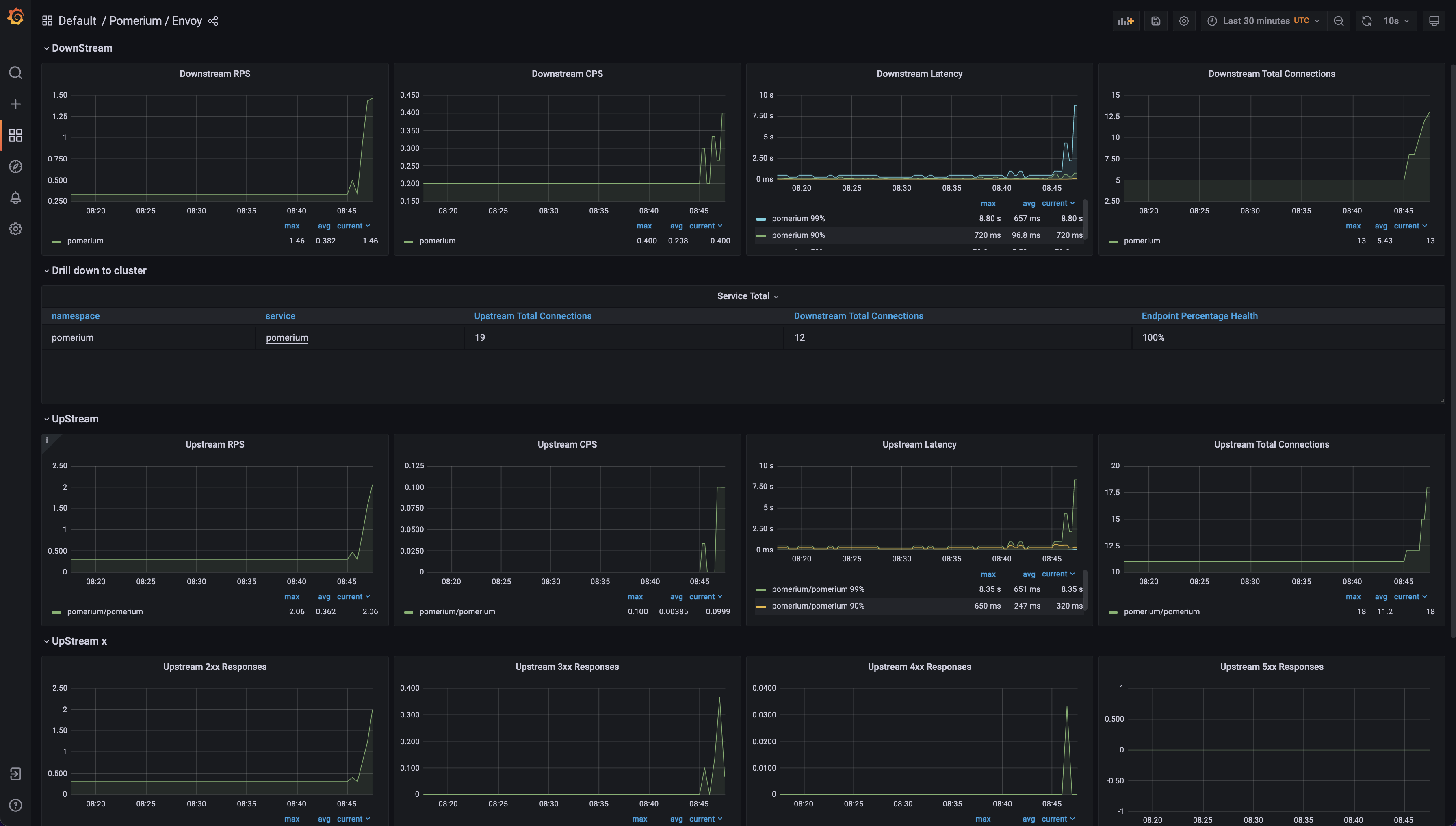
- Pomerium exposes several metrics about Pomerium itself and its underlying envoy proxy. Metrics are scrapped automatically by Prometheus and 2 Grafana dashboards are available with the
pomeriumtag when using KFD Monitoring module. Here are some screenshots:
- Dex Login:
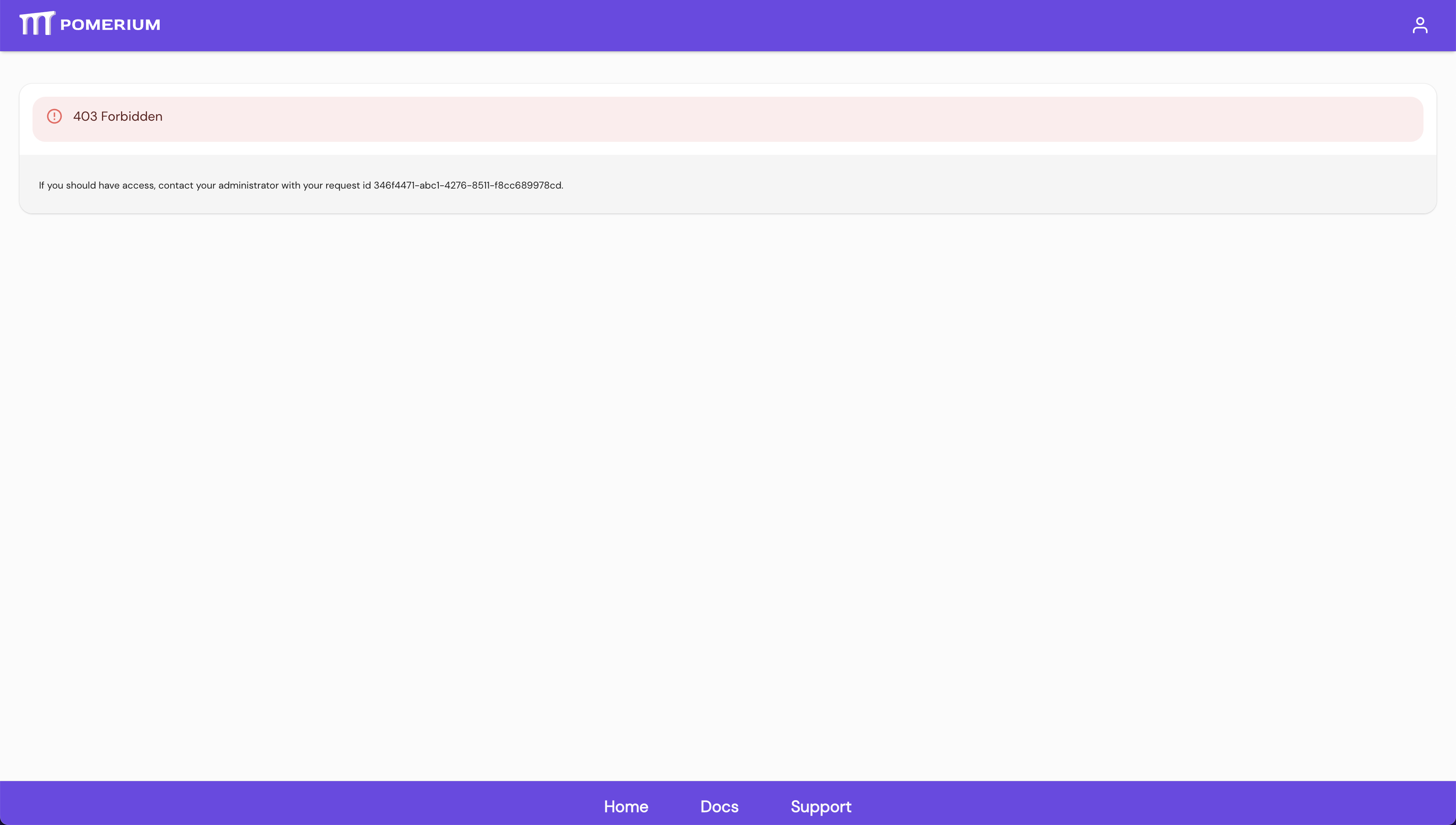
- Pomerium 403 not authorized error screen:
- Pomerium user profile screen:
Before contributing, please read first the Contributing Guidelines.
In case you experience any problems with the module, please open a new issue.
This module is open-source and it's released under the following LICENSE