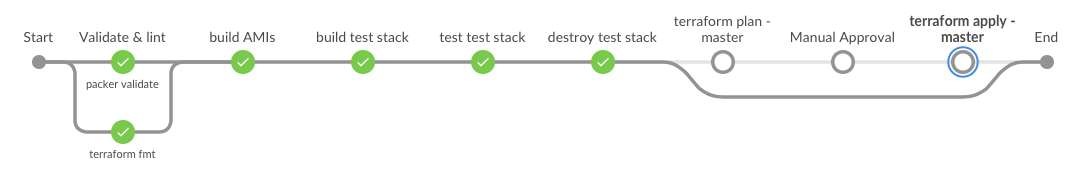
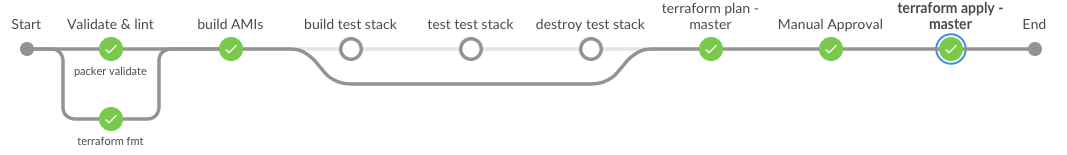
This is a working Jenkinsfile Multibranch Pipeline for building AWS AMI's images & deploying EC2 instances based on the AMI with terraform (in both a per-branch test stack, destroyed by the pipeline, and maintaining production from the master branch).
The pipeline uses 2 docker images to run jobs, most of the work is done in hashicorp-pipeline, which contains packer, terraform, aws cli & some other needed binaries (jq, perl), the other docker image used is chef/inspec, which is used to test the stack built during non-master pipeline executions.
terraform fmt -check=true -diff=trueused to check terraform config filespacker validateused to validate packer config filesbaseandapplicationAMI's built and tagged with SHA1 of thebase/base.jsonandapp/app.json, to help prevent unnecessary AMI builds- Automatically configures terraform remote state (S3 & DynamoDB)
- terraform workspaces used to store per-branch terraform state
- parameterized terraform build using per-branch tfvars
chef/inspecused to validate AWS resourcesterraform planwith stash of plan, human approval,terraform applyworkflow for master/production changes
- Add
demo-aws-credscredential set (uses AWS Credentials plugin) - Update terraform to actually deploy an EC2 instance (for demo purposes, this only builds a VPC, so zero cost & quick cycle time for pipeline experimentation, trivial to add an EC2 instance)
- Use AWS Auto Scaling group to replace running EC2 instances with EC2 instances built from the master branch
appAMI - Use AMI tags to ensure
appAMI matches the branch (Use the SHA1 ofapp/app.jsonto search for the AMI in terraform, requires some tfvars templating/injection) - Extend
chef/inspecstage to test AWS EC2 - Add a Selenium or other web test stage
If you want a simple dockerized Jenkins setup to host this, I used Jenkins 201, there's also example Job DSL here.
Some of the scripts in this pipeline (build.sh & common.sh) are based on an incomplete packer/AMI example from CircleCI.
aws ec2 deregister-image --image-id ami-4fa54026
HMM