this tool helps in solving android pattern lock bypass in CTFs
Really, the pattern lock is the SHA1 hash sequence of digits (0-8) with length from 3 (4 since Android 2.3.3) to 8.
Since Android does not allows the pattern to repeat "balls" and it does not use a salt when computing the SHA1 hash, it really takes a very short period of time to crack the hash and get the pattern.
The gesture board is a 3x3 matrix
and can be repressented as follows (each digit represents a "ball"):
-------------------
| 0 | | 1 | | 2 |
-------------------
| 3 | | 4 | | 5 |
-------------------
| 6 | | 7 | | 8 |
-------------------So if you set the pattern lock to 0 -> 1 -> 2 -> 5 -> 4
the SHA1 hash will be output of SHA1("\x00\x01\x02\x05\x04"),
and that is the hash to be cracked .
The hash is stored at /data/system/gesture.key, and (From a rooted device) can be downloaded as follows:
$ adb pull /data/system/gesture.key
0 KB/s (20 bytes in 0.071s)
$ ls -l gesture.key
-rw-r--r-- 1 simran simran 20 ago 21 17:45 gesture.key
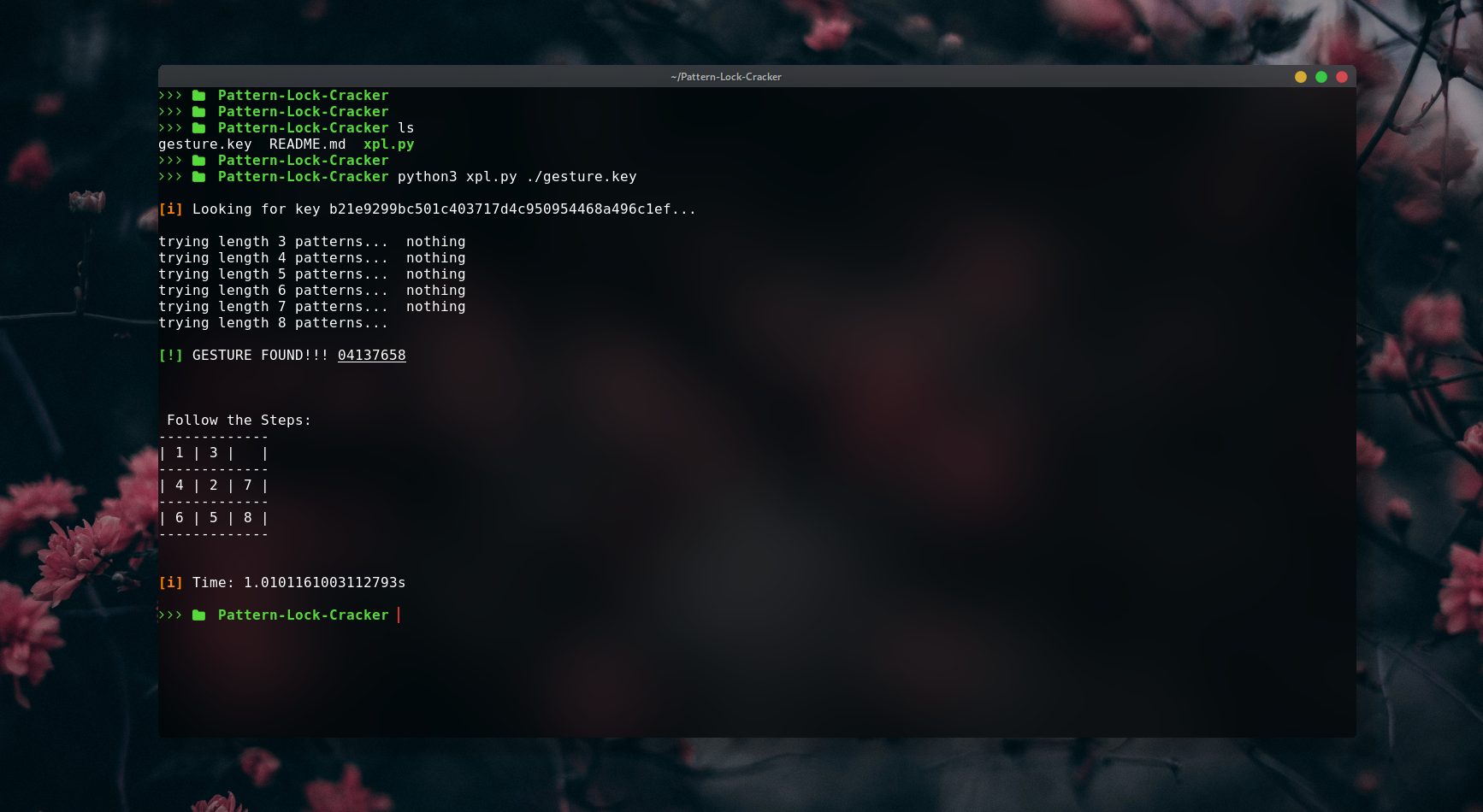
Step 1 :
$ git clone https://github.com/simran-sankhala/Pattern-Lock-Cracker.git
$ cd Pattern-Lock-CrackerStep 2 :
$ python3 xpl.py ./gesture.key