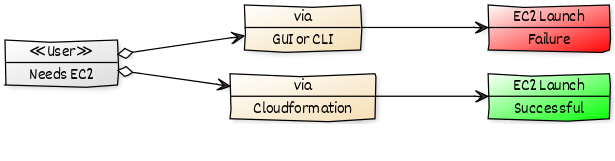
Let us say you want users the privilege to launch stack, but only through cloudformation. How do you achieve it. We can provide this type of authorization using the aws:CalledVia condition key.
-
This demo, instructions, scripts and cloudformation template is designed to be run in
us-east-1. With few modifications you can try it out in other regions as well(Not covered here).- AWS CLI pre-configured - Get help here
The following policy does the trick for us. The condition key in the statement checks, how the service is being called and only ALLOWs the request if it is made via cloudformation.
"Condition": {
"ForAnyValue:StringEquals": {
"aws:CalledVia": [
"cloudformation.amazonaws.com"
]
}
}-
- Create a new IAM User
- Create a permission with the policy provided here
least-privileged-permissions.json - Attach the policy IAM User
- Launch the clouformation template
- Should launch successfully
- Try to launch an instance with GUI/CLI it should fail
-
If you want to destroy all the resources created by the stack, Execute the below command to delete the stack, or you can delete the stack from console as well. This is not an exhaustive list, please carry out other necessary steps as maybe applicable to your needs.
Buy me a coffee ☕ through Paypal, or You can reach out to get more details through here.
Level: 200