DetectIQ is an AI-powered security rule management platform that helps create, analyze, and optimize detection rules across multiple security platforms. It can be used with the provided UI, or just with Python scripts using the self contained detectiq/core module. See examples in the examples directory for more information.


- Quickstart
- Current Features
- Road Map
- Screenshots
- Contributing
- License
- Support & Community
- Acknowledgments
⚠️ IMPORTANT DISCLAIMERThis project is currently a Proof of Concept and is under active development:
- Features are incomplete and actively being developed
- Bugs and breaking changes are expected
- Project structure and APIs may change significantly
- Documentation may be outdated or incomplete
- Not recommended for production use at this time
- Security features are still being implemented
We welcome all feedback and contributions, but please use at your own risk!
To get started, run the commands below. For more information, refer to the docs!
Step 1. Clone the repository.
git clone https://github.com/slincoln-aiq/DetectIQ.gitStep 2. Set your environment variables (using .env.example as a template).
cp .env.example .envStep 3. Run the provided start.sh script and pass install as an argument.
bash start.sh installStep 4. Run the provided start.sh script and pass run as an argument.
bash start.sh runStep 5. Use your favorite browser to navigate to http://localhost:3000.
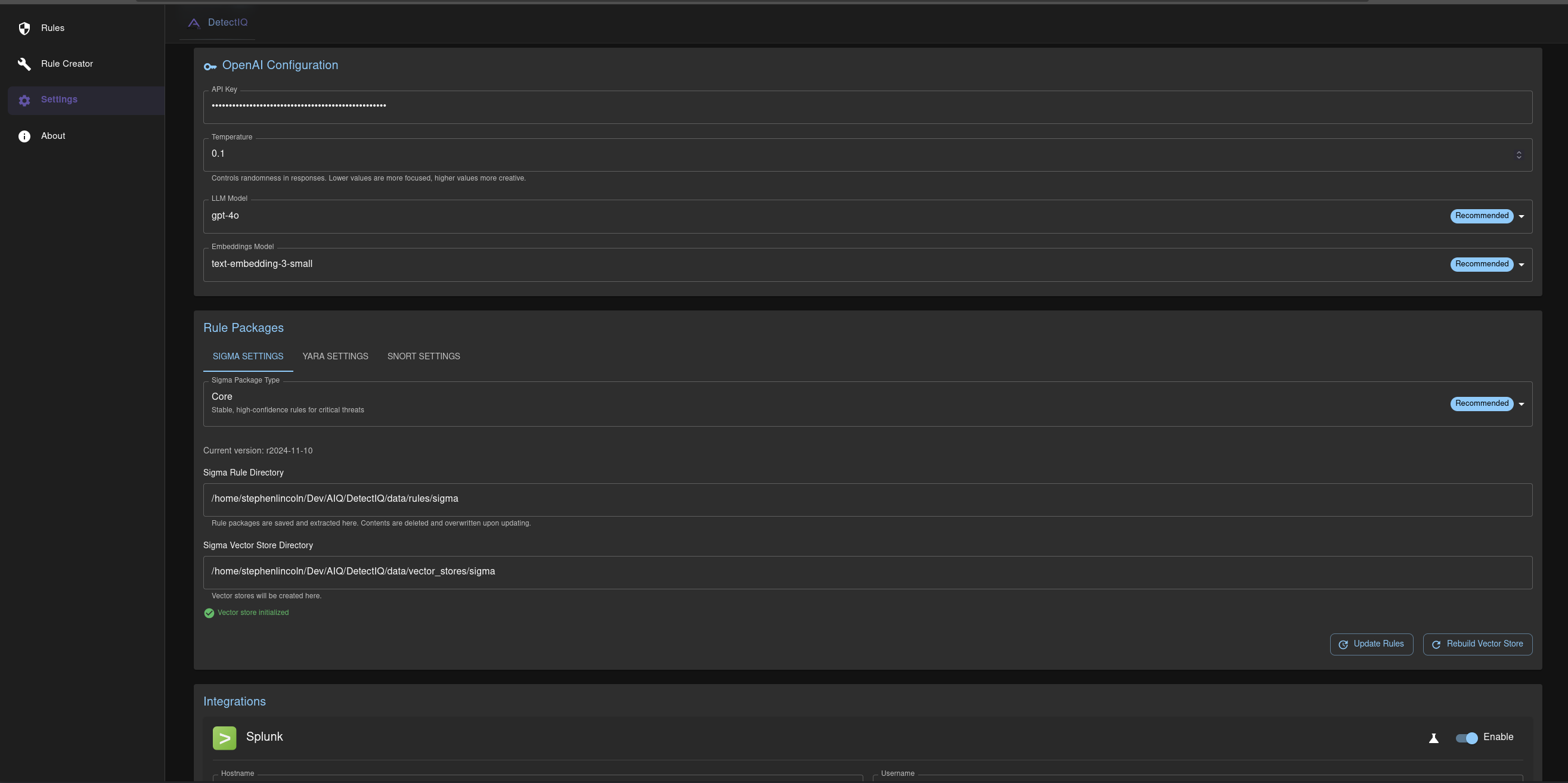
- Create and optimize detection rules using OpenAI's LLM models
- Intelligent rule suggestions based on context and best practices
- Automated rule validation and testing
- Upload malware samples and PCAP files for static analysis, automatically adding context for YARA and Snort rule creation
- LLM Rule creation analysis and detection logic returned in the rule creation response
- Enhanced by community-tested repositories:
- SigmaHQ Core Ruleset
- YARA-Forge Rules
- Snort3 Community Ruleset
- Automatically check and update repositories with rule changes
- Vectorize rules for efficient similarity comparison for more context-aware rule creation engine
- Automated file analysis for YARA rules
- PCAP analysis for Snort rule creation
- Implicit log analysis for Sigma rule optimization (Explicit Analysis Coming Soon)
- Automatic Sigma rule translation to various SIEM queries using
pySigmaandSigmAIQwrapper - Seamlessly create Splunk Enterprise Security correlation rules from Sigma rules
- Custom/local LLM models, embeddings, and vector stores
- More integrations with SIEMs such as Elastic and Microsoft XDR
- Explicit log analysis for Sigma rule optimization
- Rule testing and validation
- Rule searching, e.g. "Do I have a rule in place that can detect this?"
- Deployment tracking and workflow automation
- Rule management UI Enhancements
- Authentication and Authorization
- Project refactoring for production readiness
- Chatbot (langchain agents) UI with memory
- Docker containerization and deployment
- Rule management without OpenAI requirements
- More non-webapp examples
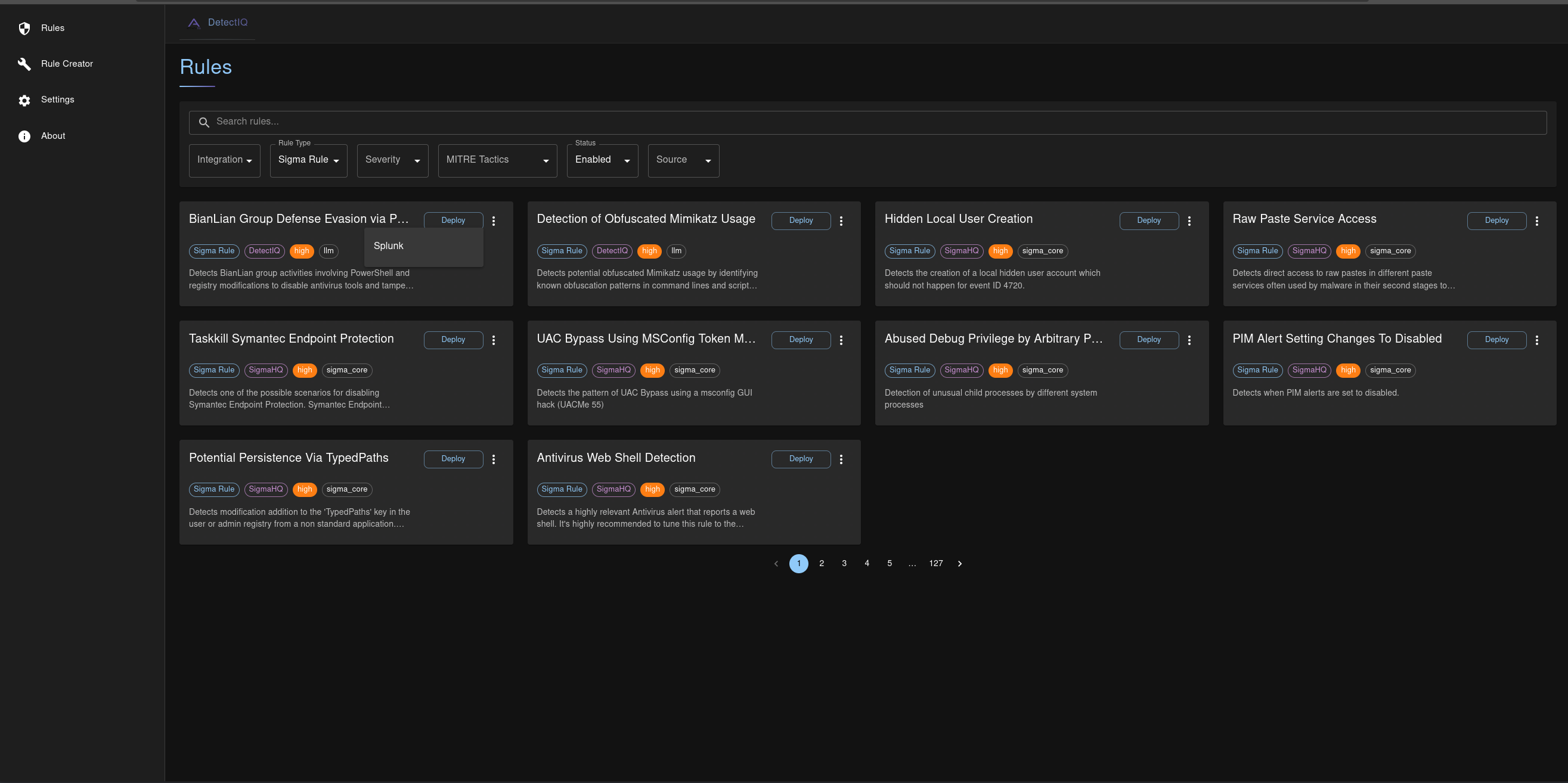
Rule Dashboard with Splunk Deployment Option
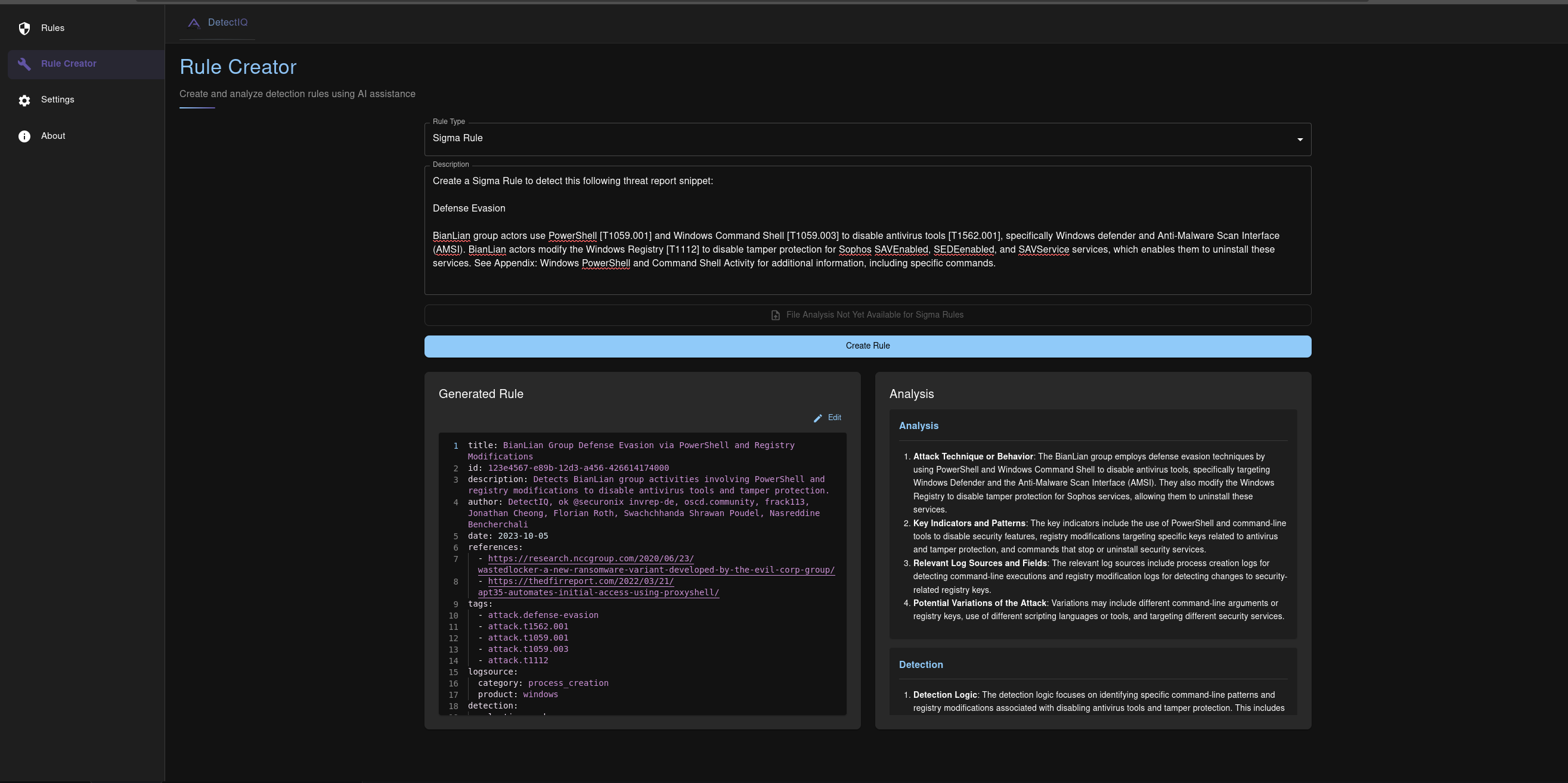
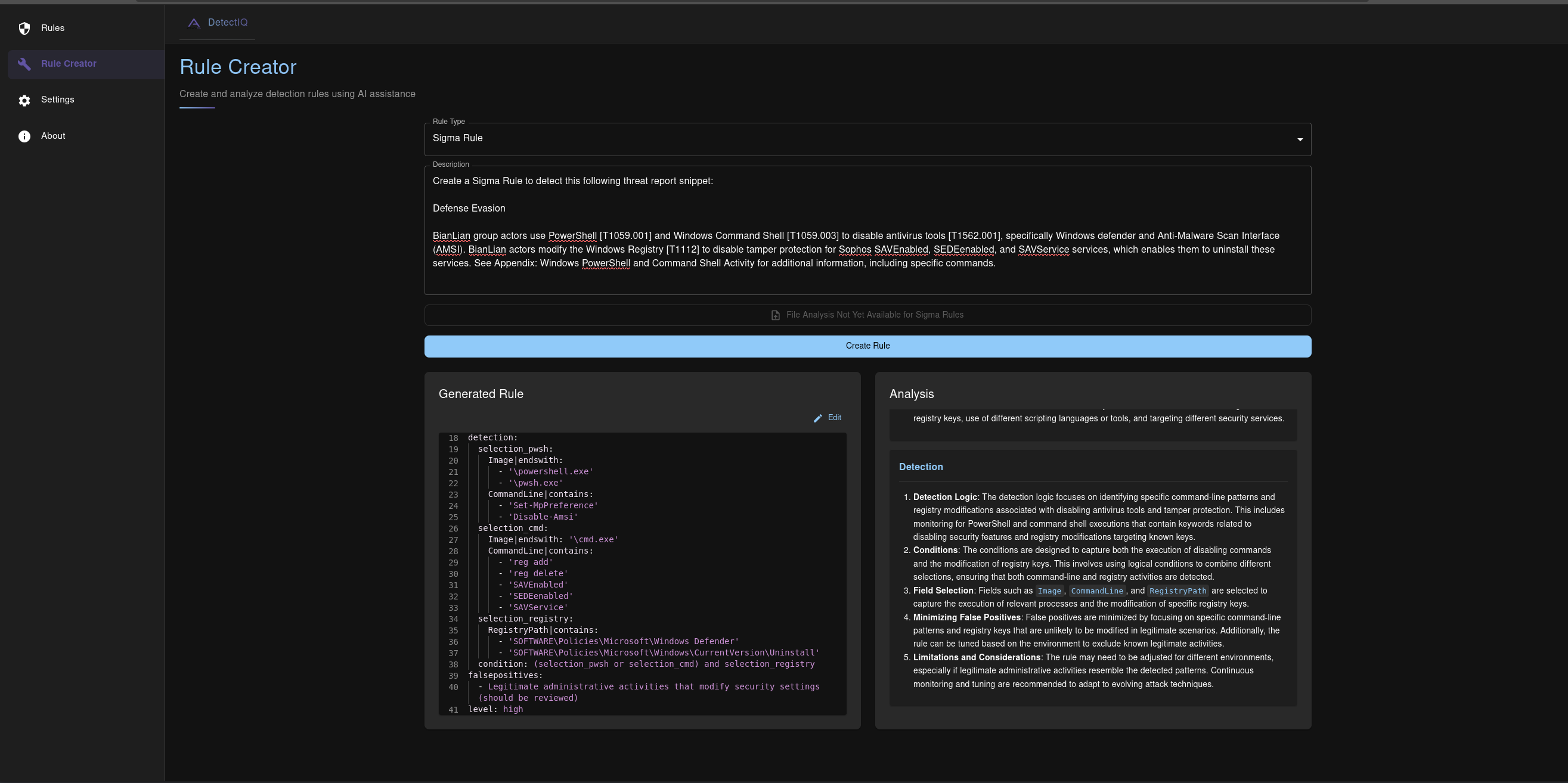
Sigma Rule Creation from threat report snippet
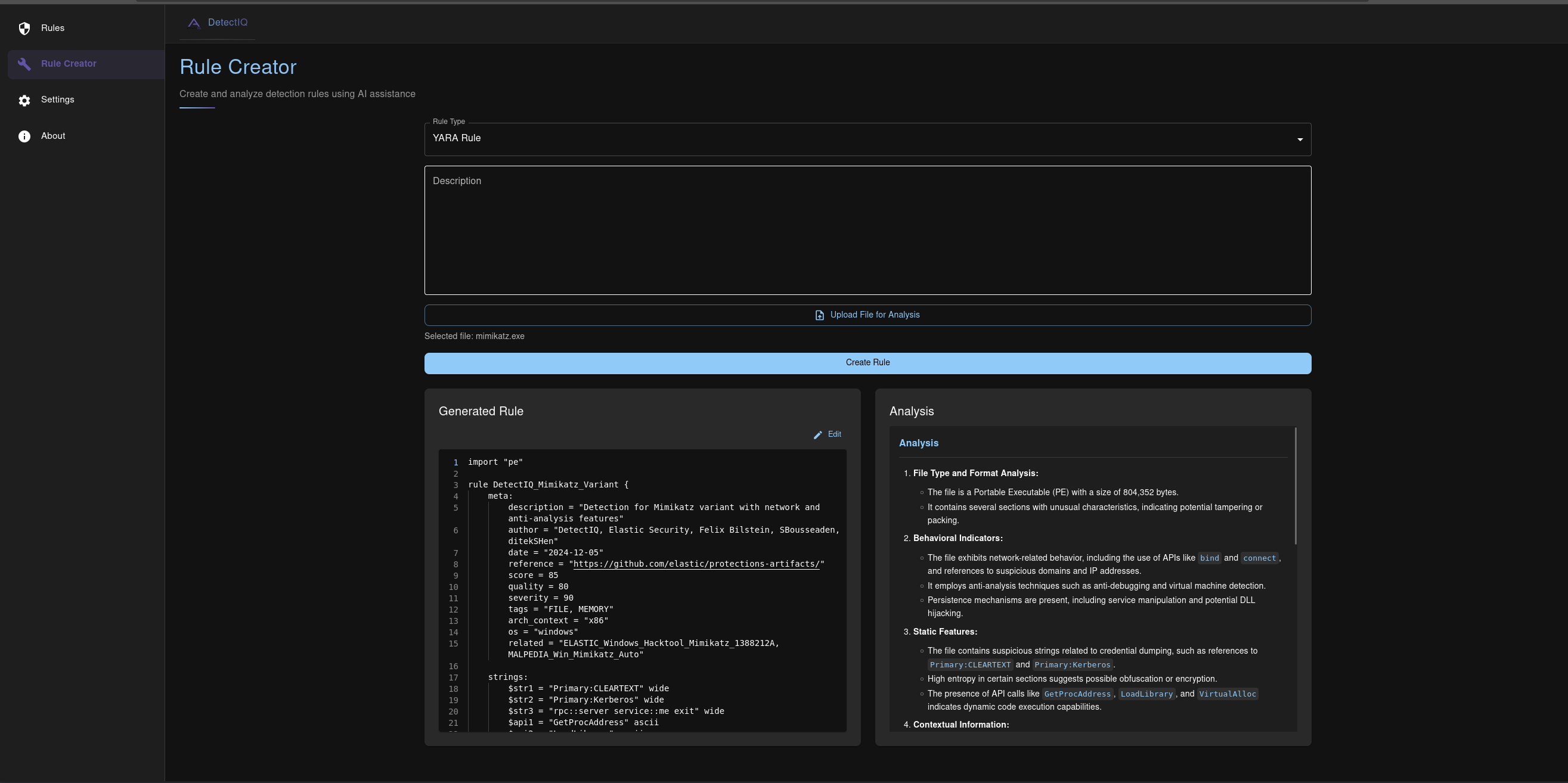
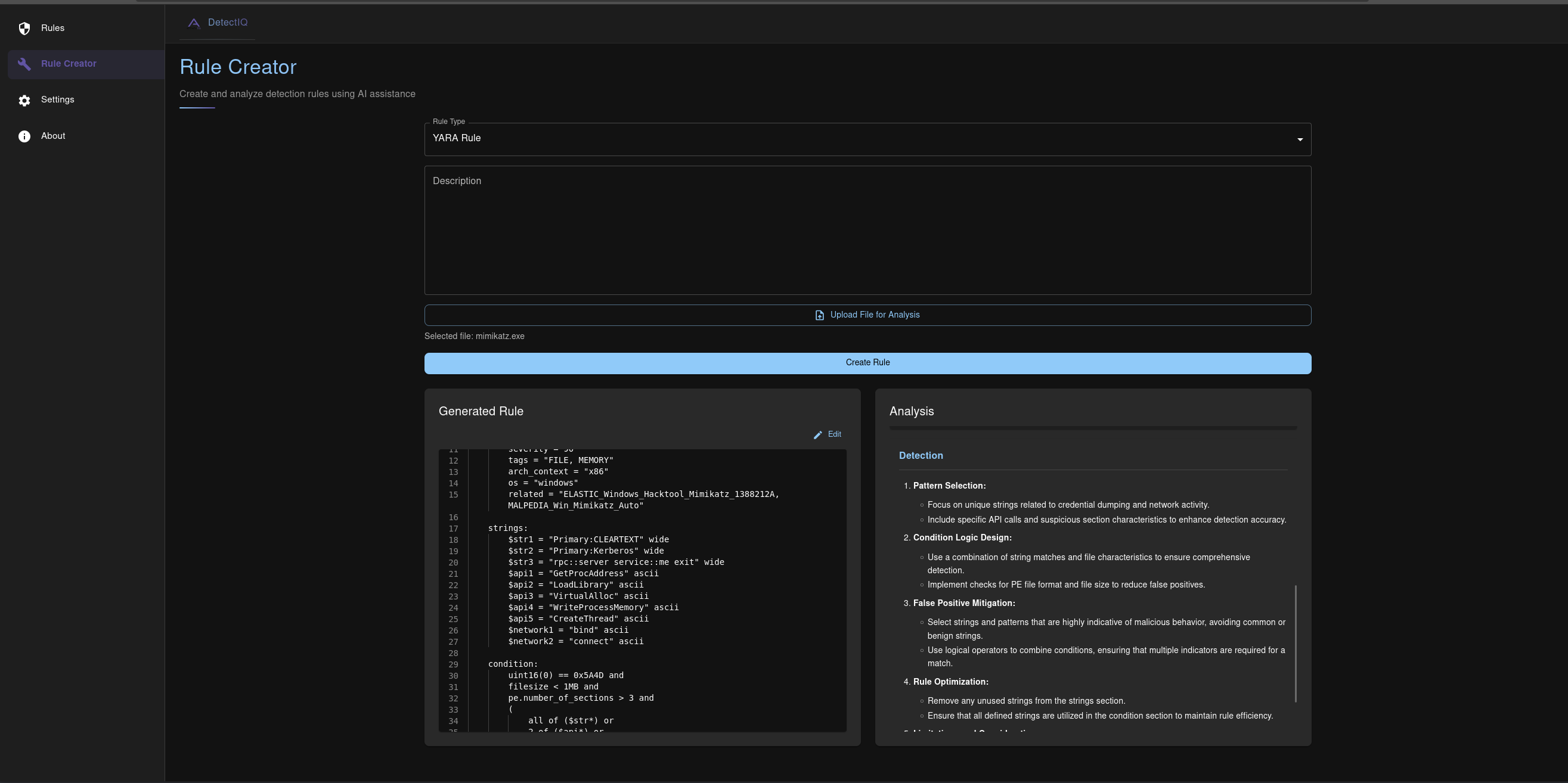
YARA Rule Creation using file analysis from uploaded mimikatz.exe sample
- Fork the repository
- Create a feature branch
- Commit your changes
- Push to the branch
- Create a Pull Request
This project uses multiple licenses:
- Core Project: LGPL v2.1
- Sigma Rules: Detection Rule License (DRL)
- YARA Rules: YARAForge License
- Snort Rules: GPL with VRT License
- Join our SigmaHQ Discord for discussions
- Report issues via GitHub Issues
- SigmaHQ Community
- YARA-Forge Contributors
- Snort Community
- OpenAI for GPT-4o Integration