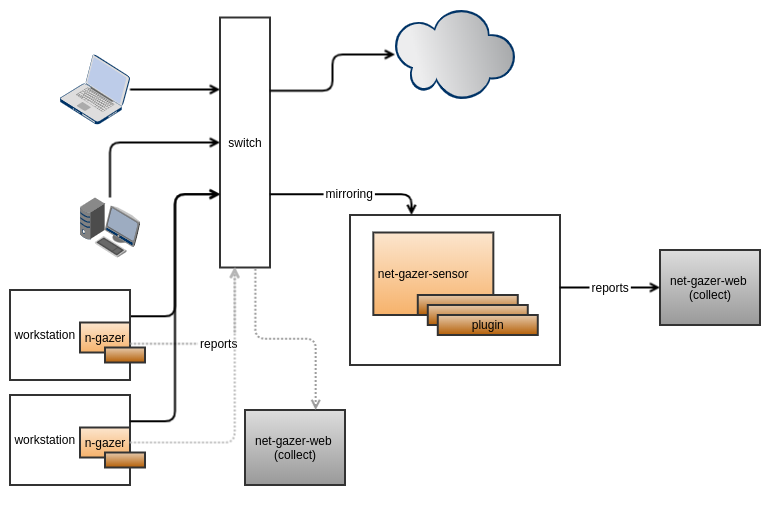
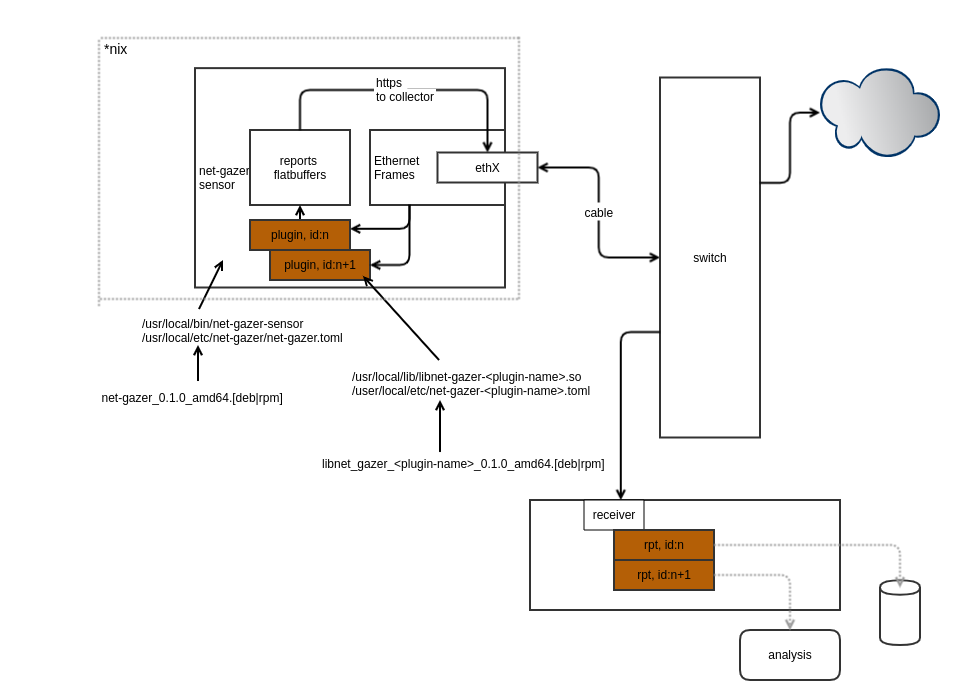
Design daemon, capable of intercepting traversing ethernet frames from network interface. Daemon should be able to load plugins for specialized packet processing. Plugins will be sending inspection reports via host daemon provided facilities. For deployment, daemon will be deployed to endponts, such as gateway, switch spanning ports and workstations
Plugins can use captured data for:
- network performace monitoring
- communication visualization
- statistical analysis
- host/network security
- many other things
data-collector part..
example pluging
- captures SYN+SYN/ACKs and traces tcp connection destination (just for fun) and profides graphed data, that can be visualised
- captures all ipv4 pakets
- geoiplocation - move to another process
- traceroute
- udp
- icmp
- tcp
- net-gaser-sensor
- net-gazer-plugins
- collector net-gazer-web
- redisgraph db docker-compose
- build net-gazer-sensor
$ cargo deb
install cargo-deb as
$ cargo install cargo-deb
- install net-gazer-sensor (plugins deb is configured for dependency on net-gazer)
# dpkg -i ./target/debian/net-gazer_0.1.0_amd64.deb
- stop daemon (b/c we will run it from cli)
# systemctl stop net-gazer
-
build plugin (from plugin repo build deb and install with dpkg)
-
build and run net-gazer-web
$ cargo run
- with docker-compose bring up redisgraph
$ docker-compose up
- run net-gazer-sensor (it will discover deployed plugin)
$ cargo run -- -vv
-
Create some network traffic
-
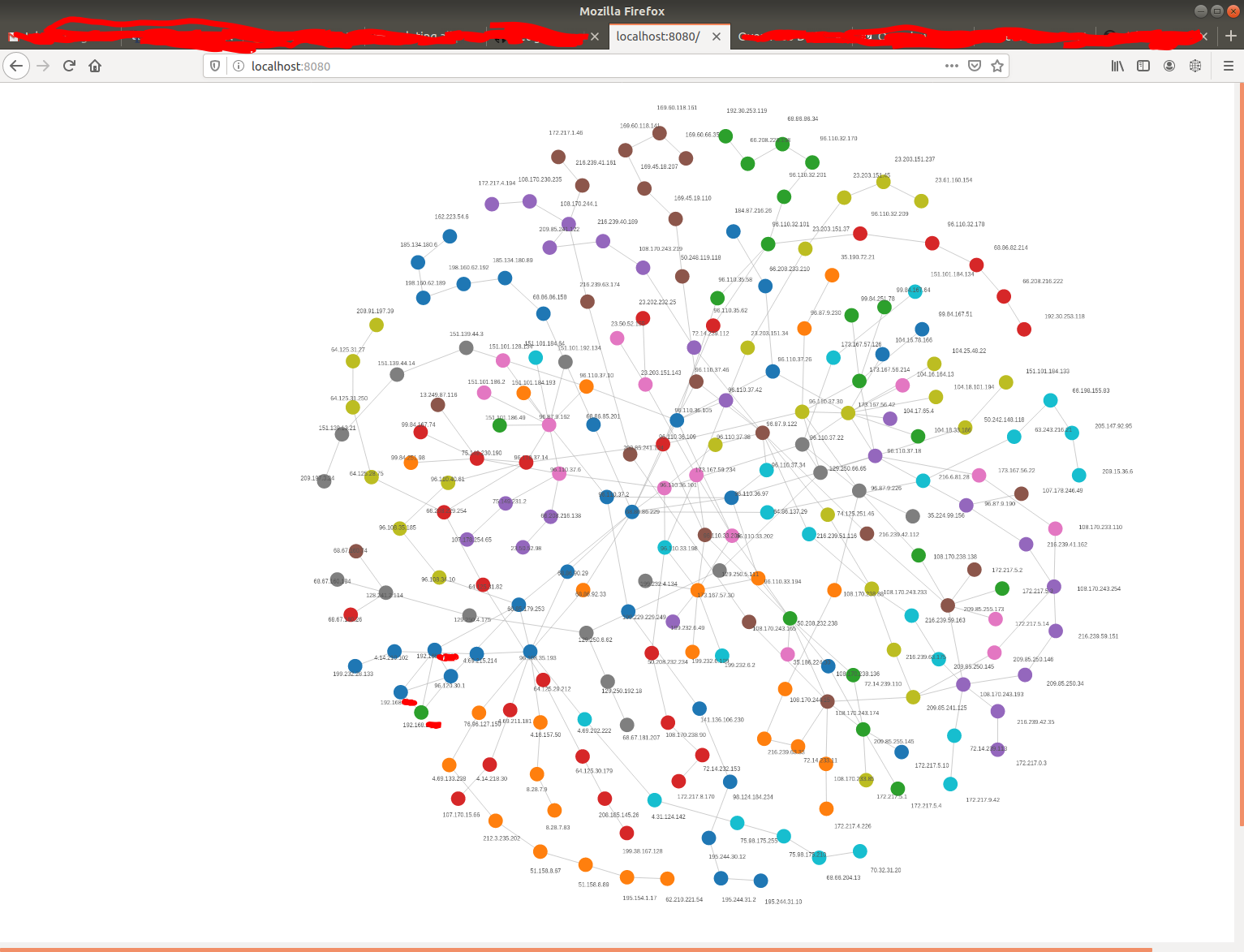
I use "redisinsight" to check graph (cypher query)
MATCH (n:hop) return n
to see 5 "neighbour" hopes
MATCH (a:hop{ip:'192.168.<your>.<ip>'})-[next*1..5]->(ancestors) RETURN a, ancestors
- to remove everything (ofter done)
# apt-get purge net-gazer
root is needed to run (./.cargo/config)
$ cargo run [-- --help]
$ cargo run -- -i eth0 -v
./etc/net-gazer/net-gazer.toml
/usr/local/etc/net-gazer/net-gazer.toml
/etc/net-gazer/net-gazer.toml
cargo run -- --help
Running `sudo -E target/debug/net-gazer --help`
net-gazer 0.1.0
network connection capture and analysis daemon
USAGE:
net-gazer [FLAGS] [OPTIONS]
FLAGS:
-h, --help Prints help information
-V, --version Prints version information
-v, --verbosity Verbose mode (-v(info), -vv(debug), -vvv(trace), etc.)
OPTIONS:
-c, --config <config-path> configuration file [env: NG_CONFIG=]
-i, --iface <iface> target network interface [env: NG_IFACE=]