Java漏洞平台,结合漏洞代码和安全编码,帮助研发同学理解和减少漏洞,代码仅供参考
- 默认账号:admin/admin
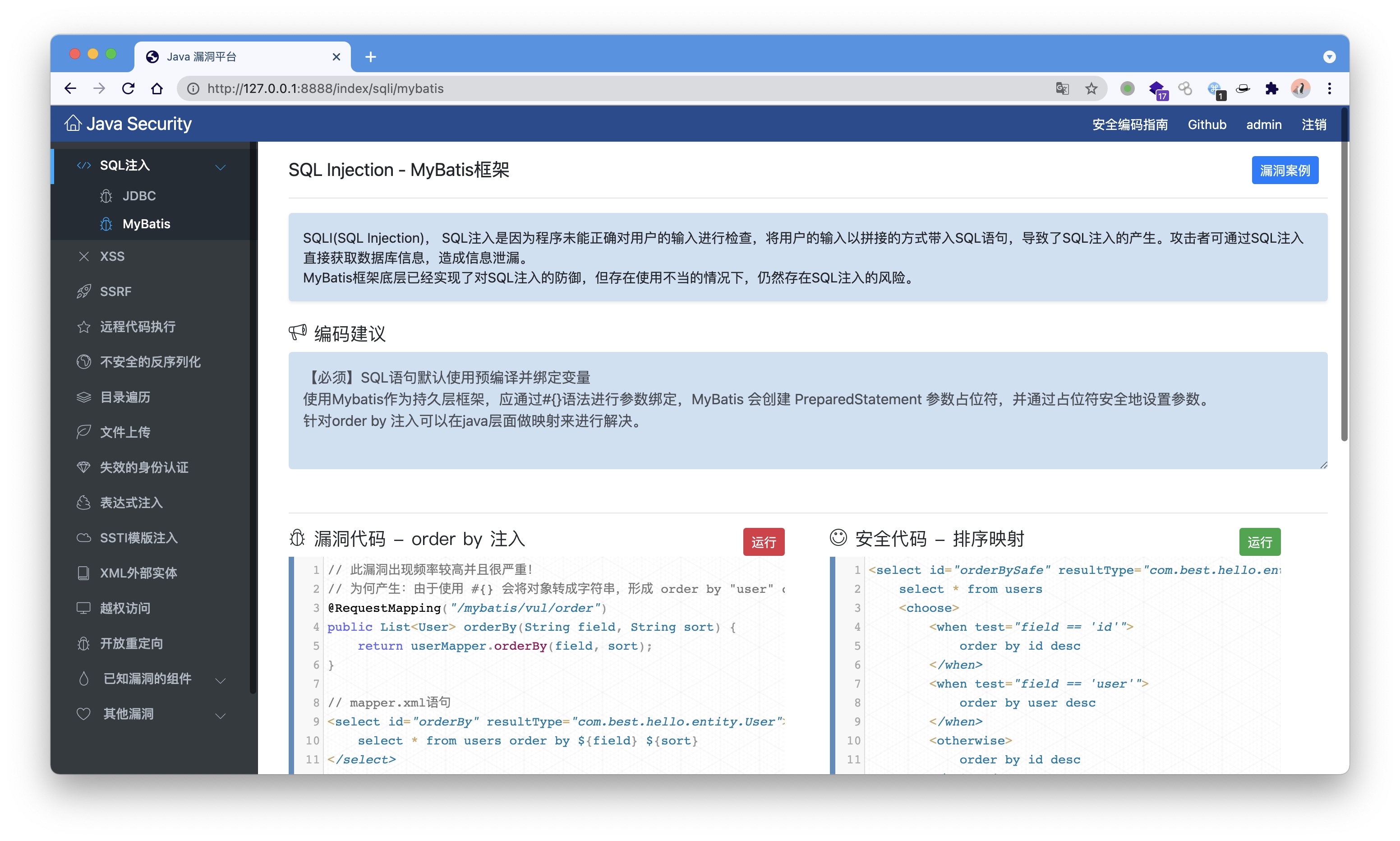
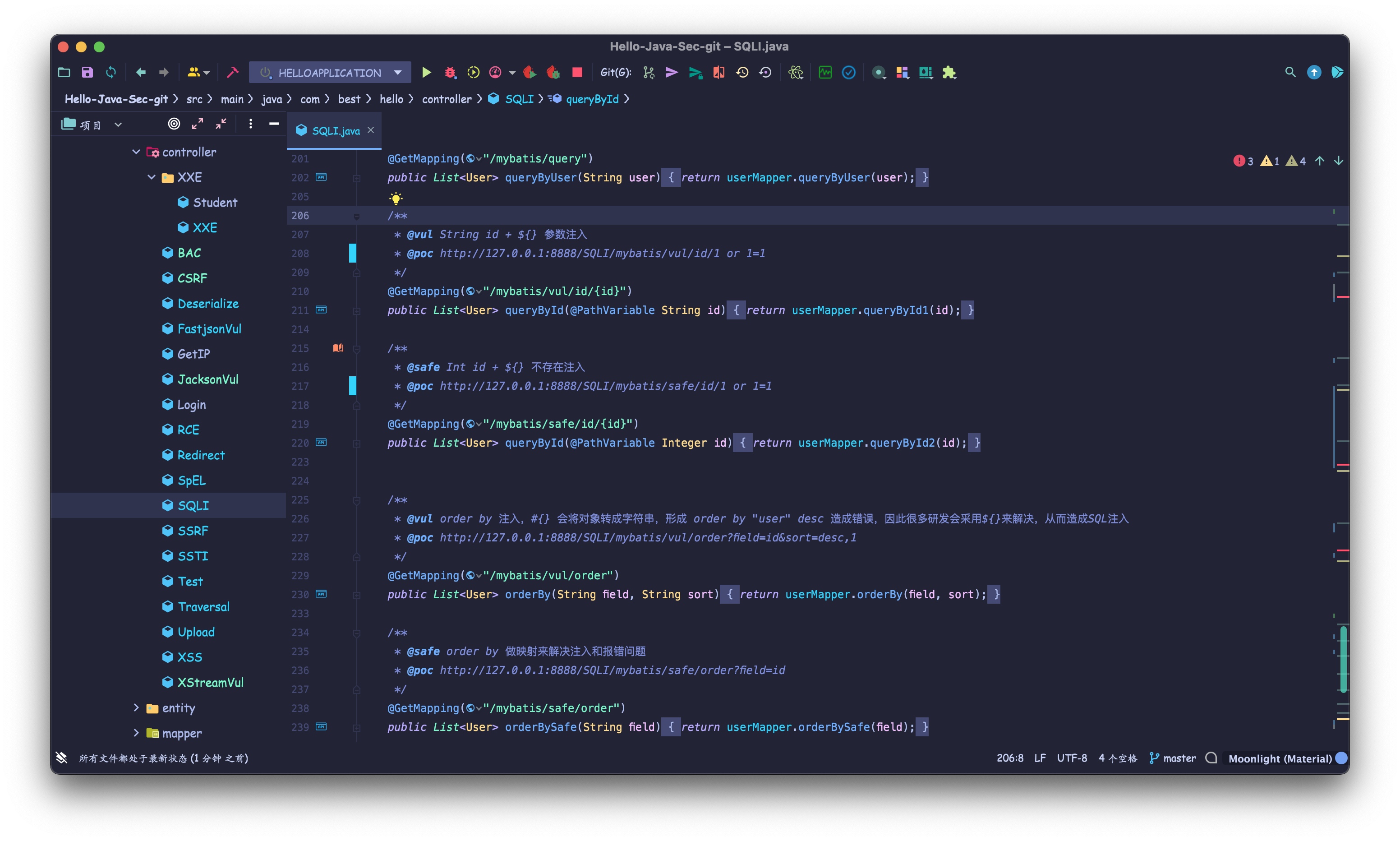
- SQLi
- XSS
- RCE
- Deserialize
- SSTI
- SpEL
- SSRF
- Directory Traversal
- Redirect
- CSRF
- File Upload
- XXE
- Actuator
- Fastjson
- Xstream
- Log4shell
- JNDI
- Dos
- Xpath
- Jwt
- more
配置数据库连接,数据库文件db.sql
spring.datasource.url=jdbc:mysql://127.0.0.1:3306/test
spring.datasource.username=root
spring.datasource.password=1234567
JDK 1.8环境
git clone https://github.com/j3ers3/Hello-Java-Sec
cd Hello-Java-Sec
mvn clean package -DskipTests
java -jar target/hello-1.0.0-SNAPSHOT.jar
mvn clean package
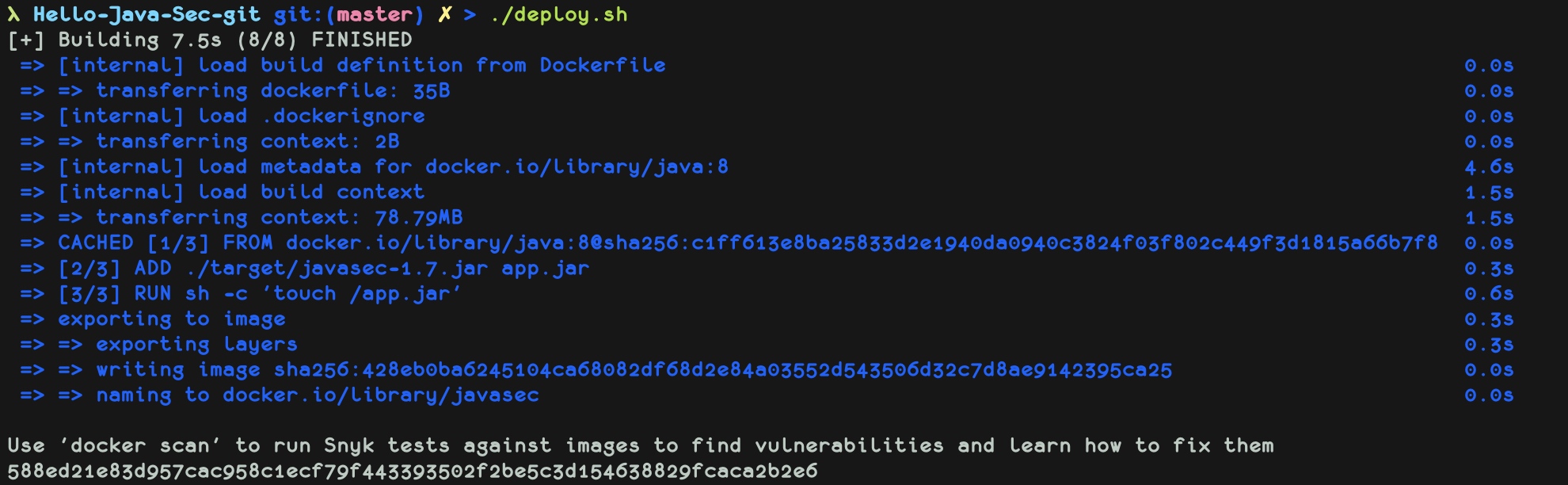
./deploy.sh
- Java 1.8
- SpringBoot 4.0
- Bootstrap 4.6.0
- Codemirror 5.62.0