- Version
- Introduction
- Prerequisites
- Important Configuration Notes
- Template Parameters
- Configuration Example
This template is tested and worked in the following version Terraform v0.12.6
- provider.azurerm v1.36.1
- provider.local v1.4.0
- provider.null v2.1.2
- provider.template v2.1.2
This solution uses an Terraform template to launch a Four NICs deployment of a cloud-focused BIG-IP VE cluster (Active/Standby) in Microsoft Azure. Traffic flows from an ALB to the active member of a BIG-IP VE cluster, which then processes the traffic through a security inspection zone dynamically utilizing any number of F5 or third party security tools, before delivering traffic to application workload for final processing.
This is the standard secure cloud architecture design where the front-end BIG-IP VE instances are running with 5 interfaces:
- Management
- External
- Internal
- To-ServiceChain
- Fr-ServiceChain
The BIG-IP VEs have the Local Traffic Manager (LTM) module and SSL Orchestrator (SSLO) enabled to provide advanced traffic management functionality. This means you can also configure the BIG-IP VE to enable F5's L4/L7 security features, access control, and intelligent traffic management. The suggested SKU is F5-BIG-LTM-VE-1G-V18 base SKU, with the ADD-SSLO option SKU so we can also enable SSL inspection and Telemetry Streaming for future developments
The one big thing in this Terraform accounted for is composing resources a bit differently to account for dependencies into Immutable/Mutable elements. i.e. stuff you would typically frequently change/mutate, such as traditional config on the BIG-IP. Once the template is deployed, there are certain resources (like the network infrastructure) that are fixed while others (like BIG-IP VMs and configurations) can be changed
Ex.
-> Run once
- Deploy the entire infrastructure with all the neccessary resources, then we use Declarative Onboarding to configure the BIG-IP Cluster; AS3 to create a sample app proxy; then lastly use Service Discovery automatically add the DVWA container app to the LTM pool (Please note currently we also hardcode the node IP in the pool due to a bug in our AS3, which will be fixed in the next release)
-> Run many X
Networking Stack Type: This solution deploys into a new networking stack, which is created along with the solution.
- Important: When you configure the admin password for the BIG-IP VE in the template, you cannot use the character #. Additionally, there are a number of other special characters that you should avoid using for F5 product user accounts. See K2873 for details.
- This template requires a service principal. See the Service Principal Setup section for details, including required permissions.
- This deployment will be using the Terraform Azurerm provider to build out all the neccessary Azure objects. Therefore, Azure CLI is required. for installation, please follow this Microsoft link
- If this is the first time to deploy the F5 image, the subscription used in this deployment needs to be enabled to programatically deploy. For more information, please refer to Configure Programatic Deployment
- All variables are configured in variables.tf
- Azure Subscription and Service Principal are configured in provider.tf
- This template would require Declarative Onboarding and AS3 packages for the initial configuration. As part of the onboarding script, it will download the RPMs respectively. So please see the AS3 documentation and DO documentation for details on how to use AS3 and Declarative Onboarding on your BIG-IP VE(s).
- onboard.tpl is the onboarding script, which is run by commandToExecute, and it will be copy to /var/lib/waagent/CustomData upon bootup. This script is basically responsible for downloading the neccessary DO, AS3, and TS RPM files, and then installing them with REST calls.
- This template uses BYOL BIGIP image for the deployment (as default)
- The initial deployment will enable you to pass traffic from your clients to the DVWA app server. See Rerun AS3 if you would like to reconfigure the AS3 configuration.
- See the Configuration Example section for a configuration diagram and description for this solution.
| Parameter | Required | Description |
|---|---|---|
| prefix | Yes | This value is insert in the beginning of each Azure object, try keeps it alpha-numeric without any special character |
| rest_do_uri | Yes | URI of the Declarative Onboarding REST call. |
| rest_as3_uri | Yes | URI of the AS3 REST call. |
| rest_do_method | Yes | Available options are GET, POST, and DELETE. |
| rest_AS3_method | Yes | Available options are GET, POST, and DELETE. |
| rest_vm01_do_file | Yes | Terraform will generate the vm01 DO json file, where you can manually run it again for debugging. |
| rest_vm02_do_file | Yes | Terraform will generate the vm02 DO json file, where you can manually run it again for debugging. |
| rest_vm_as3_file | Yes | Terraform will generate the AS3 json file, where you can manually run it again for debugging. |
| SP | YES | This is the service principal of your Azure subscription. |
| uname | Yes | User name for the Virtual Machine. |
| upassword | Yes | Password for the Virtual Machine. |
| location | Yes | Location of the deployment. |
| region | Yes | Region of the deployment. |
| cidr | Yes | IP Address range of the DMZ Virtual Network, which contains 'subnet1' for mgmt network, 'subnet2' for external network, and 'subnet3' for internal network. |
| app-cidr | Yes | IP Address range of the App Network, which is sitting at another VNet and being peered to the DMZ Vnet. |
| f5vm01mgmt | Yes | IP address for 1st BIG-IP's management interface. |
| f5vm02mgmt | Yes | IP address for 2nd BIG-IP's management interface. |
| f5vm01ext | Yes | IP address for 1st BIG-IP's external interface. |
| f5vm02ext | Yes | IP address for 2nd BIG-IP's external interface. |
| instance_type | Yes | Azure instance to be used for the BIG-IP VE. |
| product | Yes | Azure BIG-IP VE Offer. |
| bigip_version | Yes | It is set to default to use the latest software. |
| image_name | Yes | F5 SKU (image) to you want to deploy. Note: The disk size of the VM will be determined based on the option you select. Important: If intending to provision multiple modules, ensure the appropriate value is selected, such as AllTwoBootLocations or AllOneBootLocation. |
| license1 | No | The license token for the F5 BIG-IP VE (BYOL). |
| license2 | No | The license token for the F5 BIG-IP VE (BYOL). |
| host1_name | Yes | Hostname for the 1st BIG-IP. |
| host2_name | Yes | Hostname for the 2nd BIG-IP. |
| ntp_server | Yes | Leave the default NTP server the BIG-IP uses, or replace the default NTP server with the one you want to use. |
| timezone | Yes | If you would like to change the time zone the BIG-IP uses, enter the time zone you want to use. This is based on the tz database found in /usr/share/zoneinfo (see the full list here). Example values: UTC, US/Pacific, US/Eastern, Europe/London or Asia/Singapore. |
| dns_server | Yes | Least the default DNS server the BIG-IP uses, or replace the default DNS server with the one you want to use. |
| DO_onboard_URL | Yes | This is the raw github URL for downloading the Declarative Onboarding RPM |
| AS3_URL | Yes | This is the raw github URL for downloading the AS3 RPM. |
| TS_URL | Yes | This is the raw github URL for downloading the Telemetry Streaming RPM. |
| CF_URL | Yes | This is the raw github URL for downloading the Cloud Failover RPM. |
| libs_dir | Yes | This is where all the temporary libs and RPM will be store in BIG-IP. |
| onboard_log | Yes | This is where the onboarding script logs all the events. |
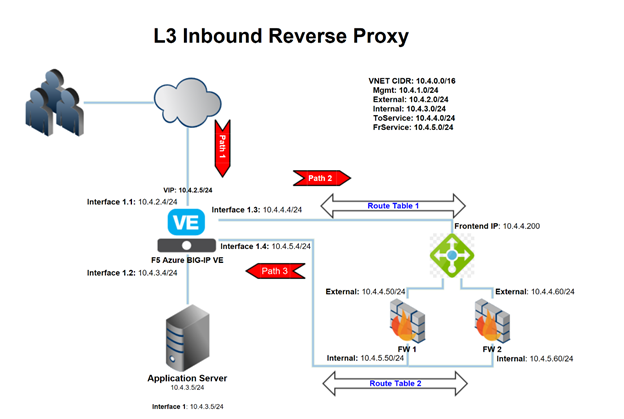
The following is an example configuration diagram for this solution deployment. In this scenario, all access to the BIG-IP VE cluster (Active/Standby) is through an ALB. The IP addresses in this example may be different in your implementation.
This deployment has created an Azure Log Analytic Workspace, and F5 BIG-IP would push the LTM and ASM logs via Telemetry Streaming to the Analytic Workspace. In other words, all the ASM and LTM logs are ready to be used for the Azure Sentinel Workbook. Please refer to the following screenshots.
For more information on F5 solutions for Azure, including manual configuration procedures for some deployment scenarios, see the Azure section of Public Cloud Docs.
For more information on F5 and Sentinel Integration, please refer to F5 Devcentral link
This example illustrates how to replace the BIG-IP VE
- Revoke the problematic BIG-IP VE's license
- Run command
terraform destroy -target azurerm_virtual_machine.f5vm02
- Run command
terraform apply
- You have 2 Active/Standby BIG-IP VEs behind the Azure LB. Repeate step 1 to step 3 on the other BIG-IP VE and HA Device Trust should be configured
This example illustrate how to upgrade the BIG-IP VEs (remember, when replace a VE, we replace both, can't be just single VE)
- Change the 'bigip_version' variable to the desired release
- Revoke the problematic BIG-IP VE's license
- Run command
terraform destroy -target azurerm_virtual_machine.f5vm02
- Run command
terraform apply
- You have 2 Active/Standby BIG-IP VEs behind the Azure LB. Repeate step 1 to step 3 on the other BIG-IP VE and HA Device Trust should be configured
- This example illustrate how to run your own custom AS3, you can have a catalog of AS3 and repeat this steps as many times as desired
terraform taint null_resource.f5vm_AS3
terraform apply -target null_resource.f5vm_AS3
- If you would like to re-run your DO json, just swap the above REST methods, and apply the new DO json file, then you can repeat the above steps as many time as you'd need.