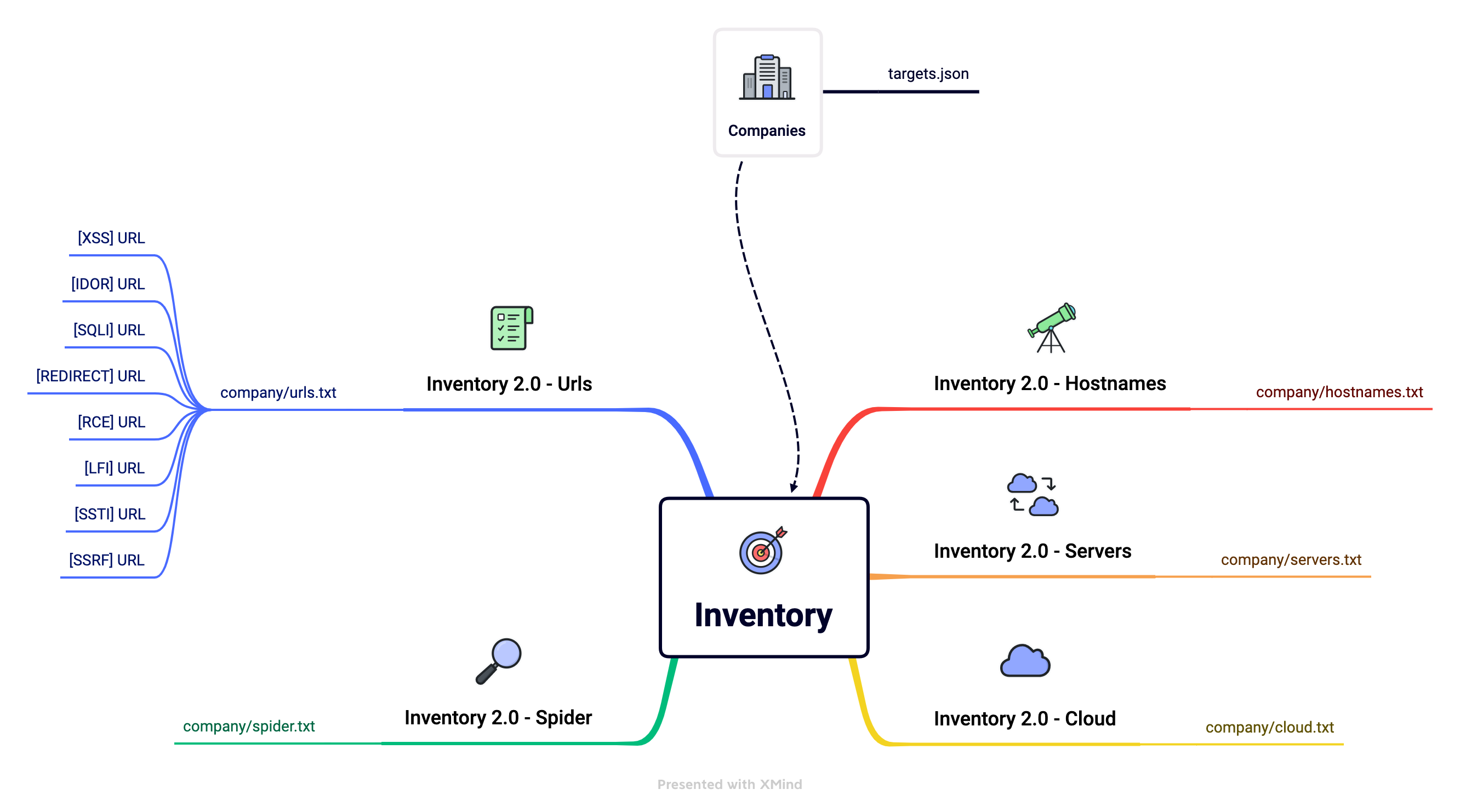
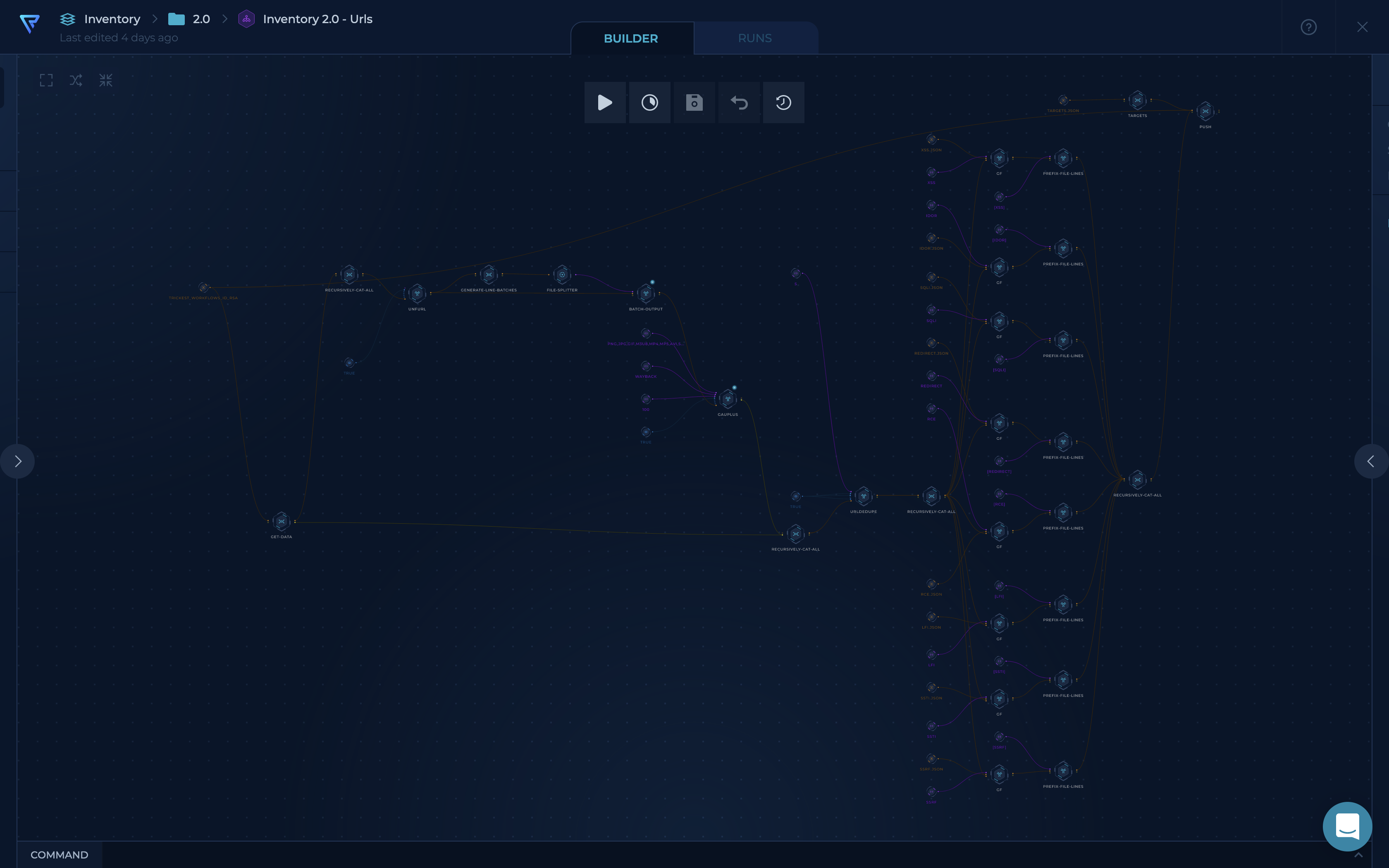
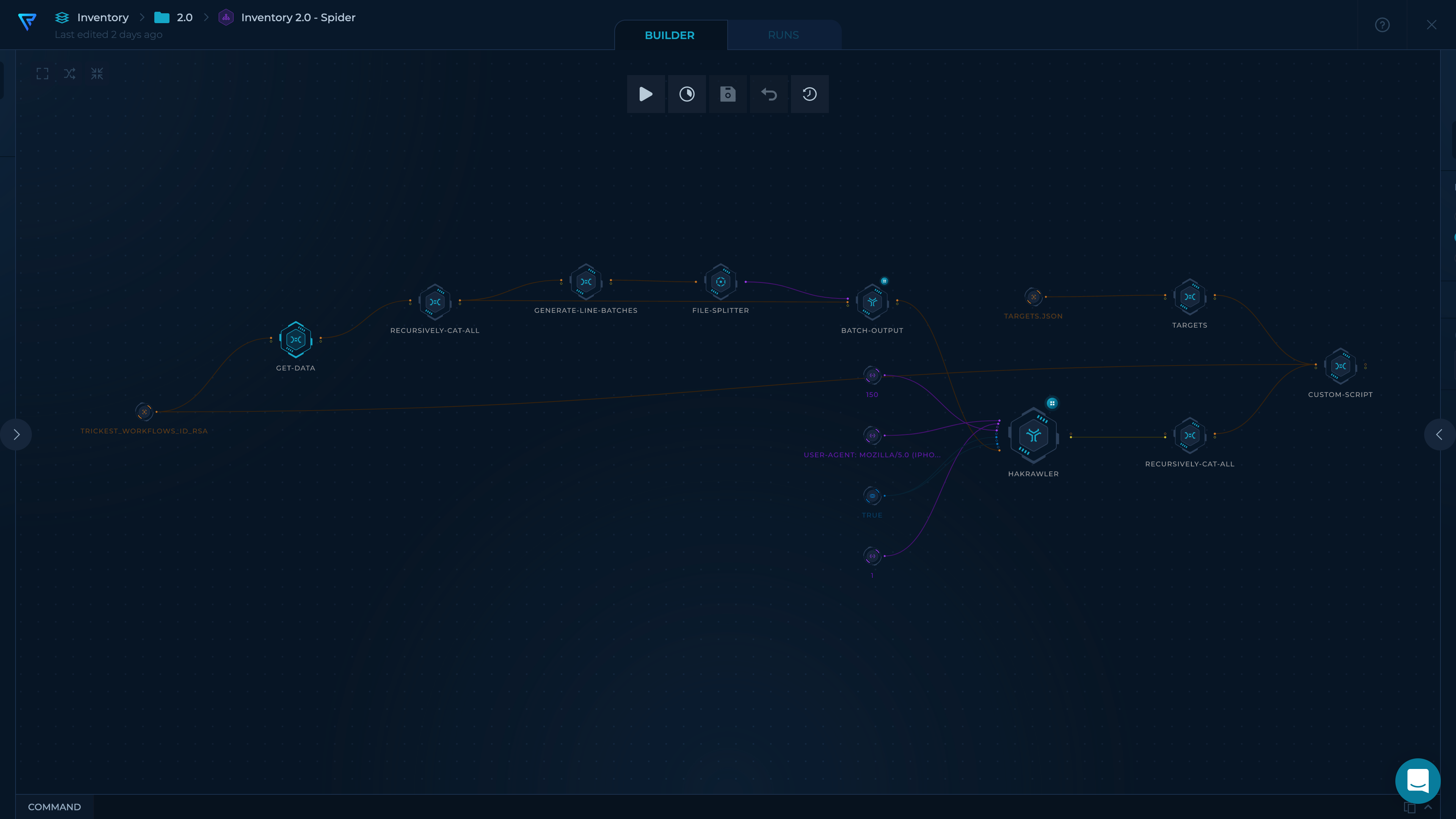
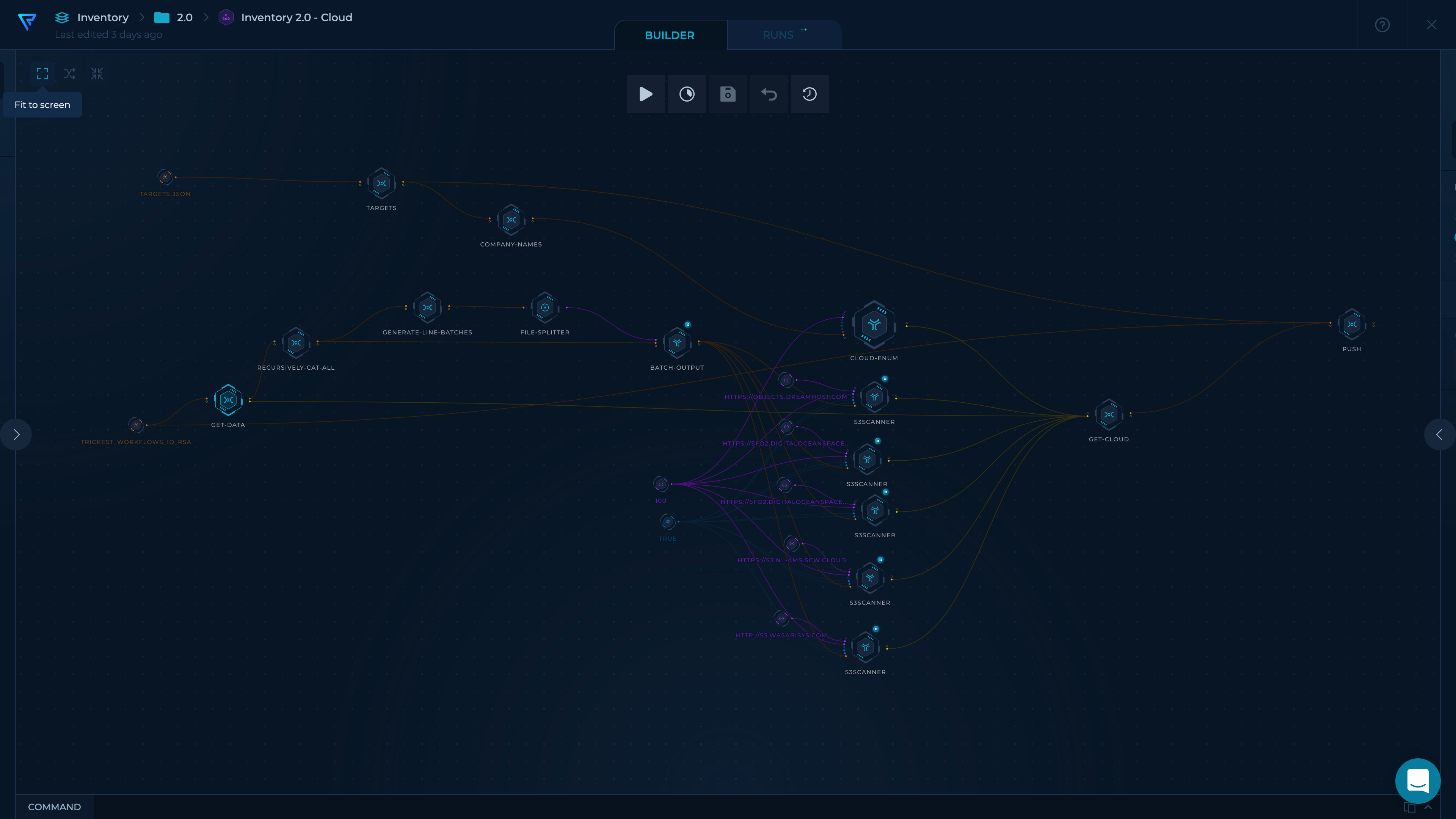
The data we collect here includes hostnames, URLs, web servers, cloud assets, and more.
Our aim with this project is to:
- help bug bounty hunters get up and running on new programs as quickly as possible.
- give security teams better visibility into their assets.
- reduce the load and noise that some programs face from automated tools (we run them on schedule, and give the results to everyone)
A few Trickest workflows pick up these targets, collect data on them, enrich it, clean it up, and push it to this repository.
- Get the list of domains from targets.json
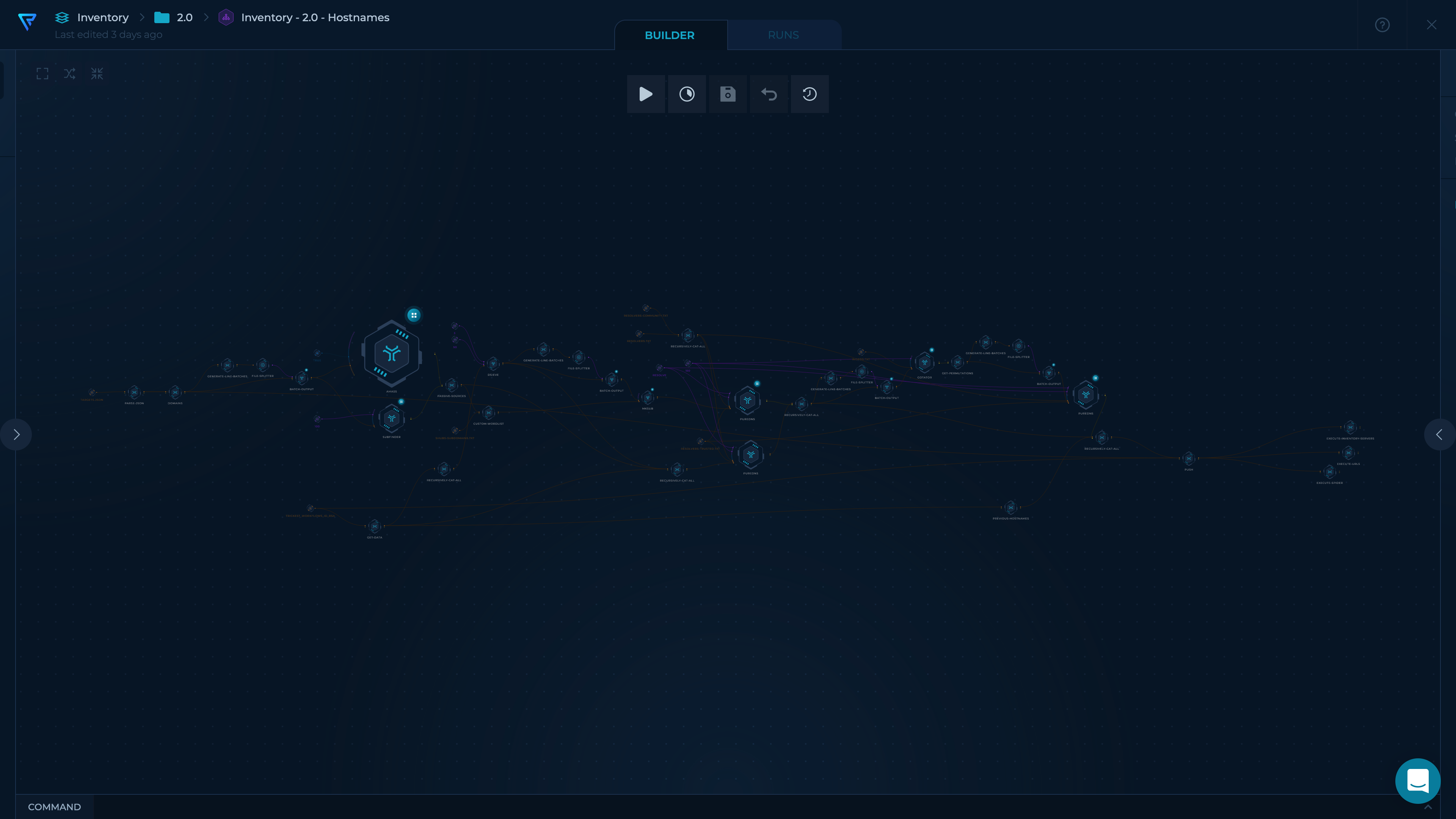
- Use subfinder and amass to collect subdomains from passive OSINT sources (Thanks ProjectDiscovery, hakluke, OWASP, and Jeff Foley!)
- Create words from passive results gathered in previous steps
- Find already resolved hostnames to dsieve to collect their
main environments(e.g. foo.admin.example.com -> admin.example.com) - Get a pre-defined
wordlist - Combine everything into one
wordlist. - Use mksub to merge the
wordlistand themain environmentsalong withroot-domainsand generate DNS names. - Resolve DNS names using puredns (Thanks d3mondev!).
- Generate permutations using gotator (Thanks Josue87!).
- Resolve permutated DNS names using puredns.
- Push hostnames update
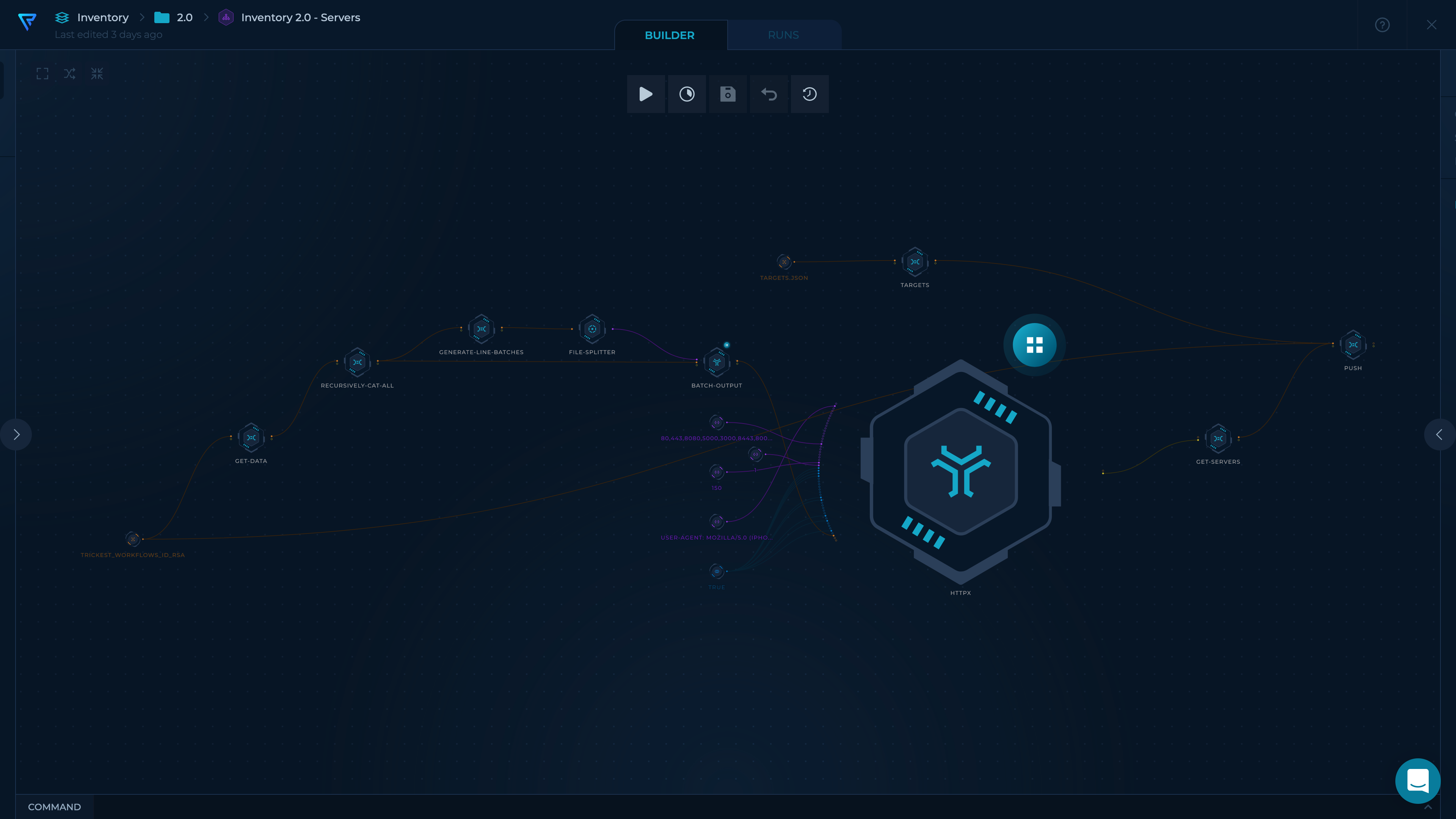
- Probe previously found hostnames using httpx to find live web servers on specific ports (
80,443,8080,5000,3000,8443,8000,4080,8888) and, for each one, collect its:- HTTP Title
- Status Code
- Content Length
- Content Security Policy
- Content Type
- Final Redirect Location
- Webserver
- Technology
- IP Addresses
- CNAME
- Parse httpx's output and organize it into files for easier navigation
- Push to the repository
- Collect URLs using newly found hostnames with gauplus (Thanks bp0lr!)
- Deduplicate with urldedupe (Thanks ameenmaali)
- Use gf and gf-patterns to categorize newly found URLs. (Thanks tomnomnom,1ndianl33t!)
- Use
prefix-file-linesto add a prefix for each of the vulnerability- IDOR
- XSS
- RCE
- SQLI
- SSTI
- SSRF
- REDIRECT
- LFI
- Push to the repository
- Collect cloud resources using cloud_enum (Thanks initstring!)
- Collected resources include
- AWS S3 Buckets
- AWS Apps
- Azure Websites
- Azure Databases
- Azure Containers
- Azure VMs
- GCP Firebase Databases
- GCP App Enginee Apps
- GCP Cloud Functions
- GCP Storage Buckets
- Use S3Scanner to bruteforce S3-compatible buckets (using the hostnames collected to seed the wordlist)
- Collected buckets include:
- AWS S3 buckets
- DigitalOcean Spaces
- DreamHost Buckets
- Linode Buckets
- Scaleway Buckets
- Wasabi Buckets
- Save each type of resource to its own file for easier navigation.
Note: As described, almost everything in this repository is generated automatically. We carefully designed the workflows (and continue to develop them) to ensure the results are as accurate as possible.
All contributions/ideas/suggestions are welcome! If you want to add/edit a target/workflow, feel free to create a new ticket via GitHub issues, tweet at us @trick3st, or join the conversation on Discord.
We believe in the value of tinkering. Sign up for a demo on trickest.com to customize this workflow to your use case, get access to many more workflows, or build your own from scratch!