 SOC Workflow App helps Security Analysts and Threat Hunters explore suspicious events, look into raw events arriving at Elastic stack and view Saved Searches saved by teammates. Carry out investigations based on automatically generated alerts from SIEM, EDR, IDS arriving at Elastic stack, Elastic Machine Learning alerts and Threat Intelligence data enrichments from Anomali ThreatStream & MISP.
SOC Workflow App helps Security Analysts and Threat Hunters explore suspicious events, look into raw events arriving at Elastic stack and view Saved Searches saved by teammates. Carry out investigations based on automatically generated alerts from SIEM, EDR, IDS arriving at Elastic stack, Elastic Machine Learning alerts and Threat Intelligence data enrichments from Anomali ThreatStream & MISP.
To install SOC Workflow for your Kibana: Copy the file soc_workflow_ce-xxxxx.zip to Kibana server and run the command:
/usr/share/kibana/bin/./kibana-plugin install file:///PATH_TO_FILE/soc_workflow_app_ce/dist/soc_workflow_ce-xxxxx.zip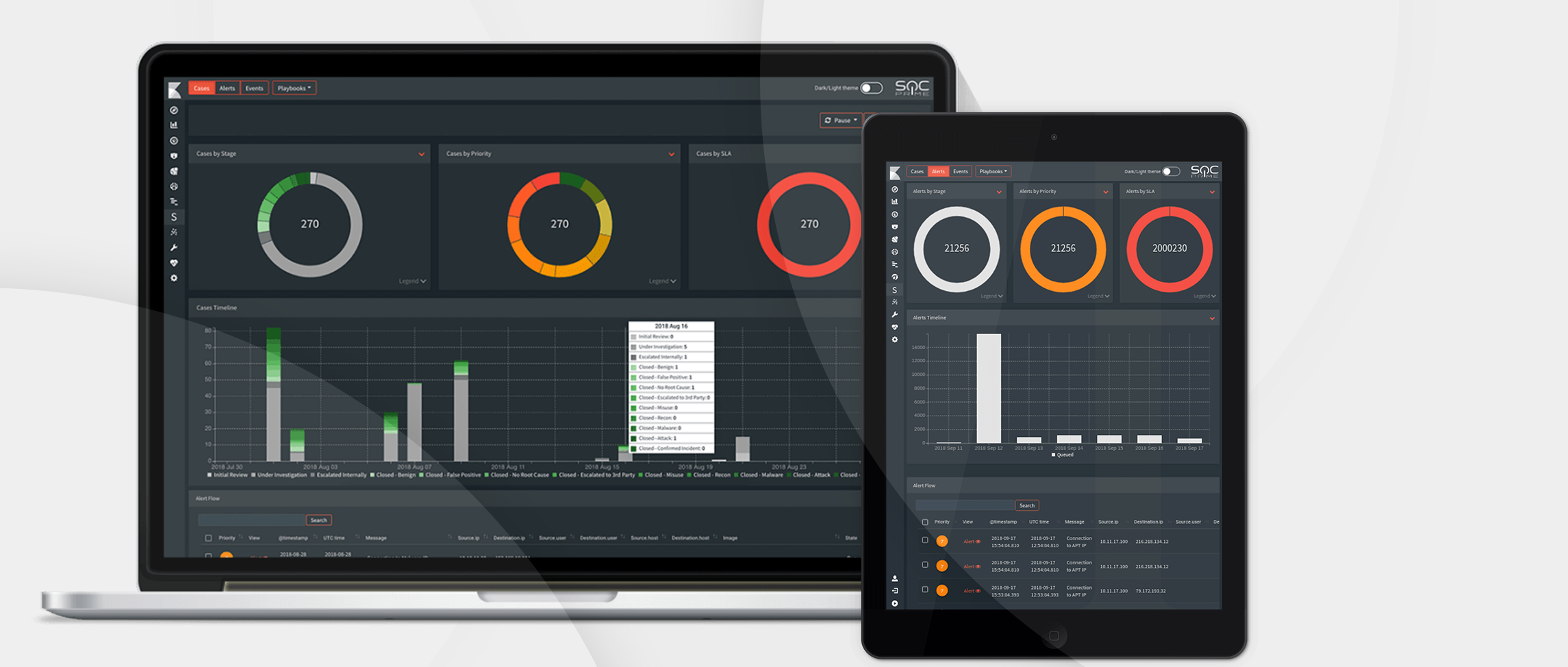 Wait until the installation finishes, it may take a few minutes to optimize and cache browser bundles.
Wait until the installation finishes, it may take a few minutes to optimize and cache browser bundles.
If you get the error: "Plugin installation was unsuccessful due to error "Incorrect Kibana version in plugin [soc_workflow_ce]. Expected [6.2.4]; found [6.2.2]", please open zip archive and modify file
"./kibana/soc_workflow_ce/package.json":put version of your Kibana to field "version".
Restart Kibana to apply the changes. In case after restart Kibana you don't see any changes, go to /usr/share/kibana/optimize. Delete all files in the folder "optimize" including subfolders. And restart Kibana. This will make Kibana refresh its cache.
SOC Workflow Application is using indices:
- "alerts_ecs*" - for events that need to be investigated by SOC. That could be correlation events generated by logstash or scripts;
- "alerts_logs*" - for workflow stages and comments history;
- "case_ecs*" - is used to store cases;
- "case_logs*" - for case stages and comments history;
- "sigma_doc" - is used for storing SIGMA documents for data enrichment
- "playbook" - for playbooks.
Create index templates for these indices from files:
- index_template_ecs_new.txt
- index_template_alerts_case_logs.txt
- index_template_playbook.txt
- index_template_sigma_doc.txt
Add playbooks to the index from the application or add your own ones in the same format. Run commands in Dev Tools Kibana console from the file playbooks_to_elastic.txt.
Playbook format:
"@timestamp": "1530687175111",
"playbook_name" : "Playbook",
"playbook_body" : "PUT HERE TEXT OF YOUR PLAYBOOK IN HTML CONVERTED TO BASE64"
Edit file
/usr/share/kibana/plugins/soc_workflow_ce/config/playbook_alert_links.jsonto add mapping of your own alerts to playbooks.
"Brute Force Detection Advanced": [
"User Brute Force",
"Server Brute Force Detection"
]Where "Brute Force Detection Advanced" is the name of the playbook. "User Brute Force", "Server Brute Force Detection" - are alert names in the index alert-ecs*. For these alerts playbook "Brute Force Detection Advanced" will be automatically assigned in the SOC App.
##Load SIGMA documents to index - "sigma_doc"; To fill sigma docs to index: Enter to folder resources/ELK_import_export
- Modify script es_config.py, put there Elasticsearch hostname, user and password.
- Run command
python /PATH_TO_FILE/ELK_import_export/import_es_index.pyIndices will be created and filled with sigma rules.
You should have the elasticsearch module, for python 2.7 install it using the command:
pip install elasticsearch
Configure external commands to run scripts/commands and make lookups to the 3d parties services.
Edit file /usr/share/kibana/plugins/soc_workflow_ce/config/data_actions.json
[{
"Menu": [{
"Submenu": [{
"name": "Command 1",
"command": "/bin/sh /opt/scripts/script1.sh \"[[value]]\""
}]
}]
},
{
"name": "Command 2",
"command": "/usr/bin/python2.7 /opt/scripts/scripts2.py -v \"[[value]]\""
},
{
"name": "Command 3",
"command": "/usr/bin/python2.7 /opt/scripts/script3.py -i [[value]]"
}]Where:
- "name" - display name of the lookup command
- "link" - link for drill-down.
- Put [[value]] to the appropriate place in the link to send field value from the alert/case.
Copy predefined scripts for data enrichment and response from folder "scripts_app" to Kibana /opt/scripts. And run commands:
chown -R kibana:kibana /opt/scripts
chmod +x /opt/scripts/*.shNow you can use the SOC Workflow plugin.
How to update
- Backup all config files in folder
/usr/share/kibana/plugins/soc_workflow_ce/config/. - Remove folder
/usr/share/kibana/plugins/soc_workflow_ce/. - Install application from new version archive.
- Remove Kibana cache - all files and subfolders in folder
/usr/share/kibana/optimize/. Do not delete folder "optimize". - In needed update or add new templates for data.
- Copy back upped configuration files to folder
/usr/share/kibana/plugins/soc_workflow_ce/config/ - Restart Kibana. Restart Kibana may take a while since rebuilding cache.