This repository is a demo for building a Datacenter (network & Firewalls) with ansible. All this automation content is based on Arista AVD data model with some deviations to add support for Palo Alto Firewall configuration.
Disclaimer: It is a Proof of concept repository and it is not ready for production. use it at your own risk.
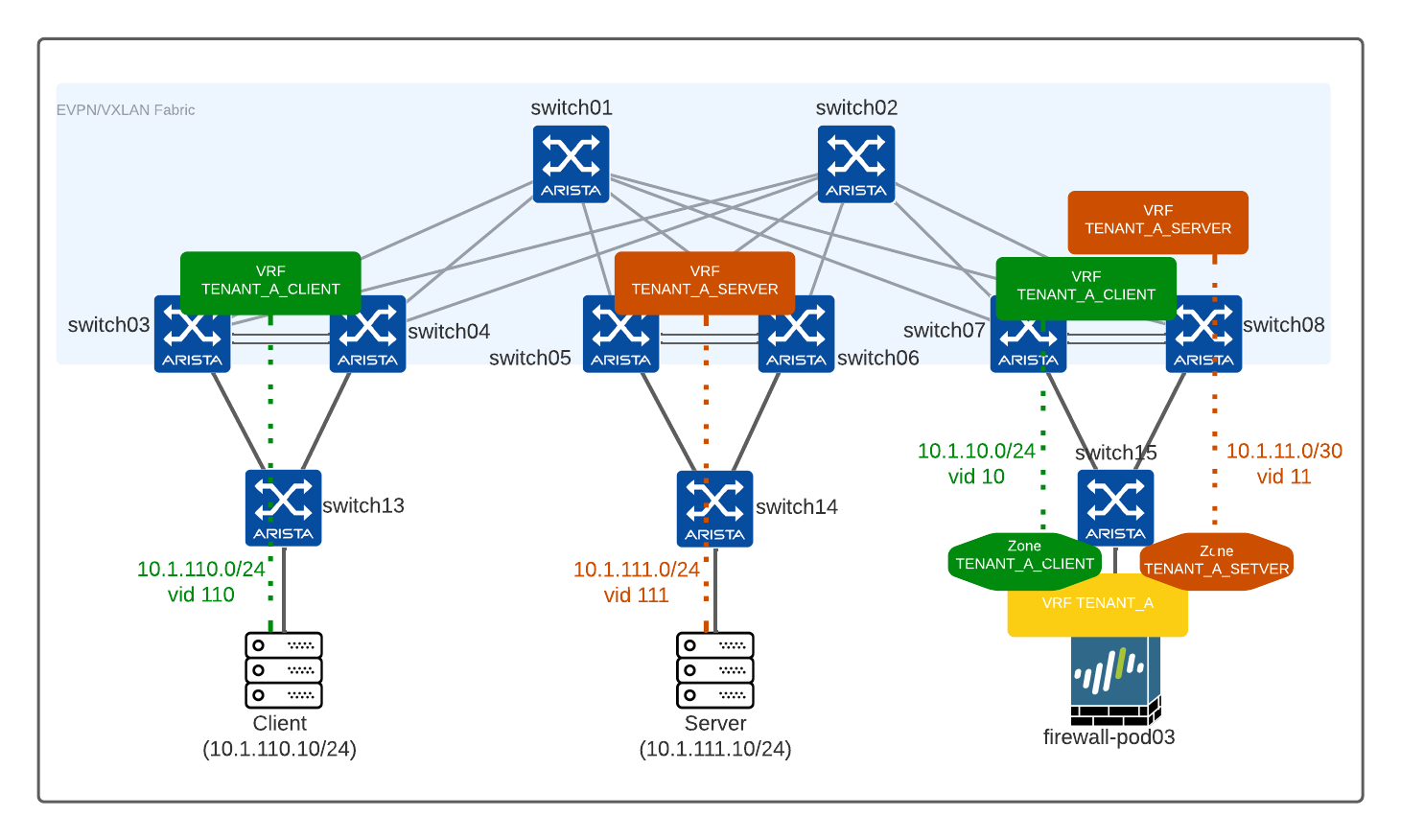
Repository is going to build the following topology with an IP Fabric running EVPN whith 1 tenant, 2 VRFs to connect 1 server, 1 client and 1 firewall each on a POD.
Note: this design does not implement redundancy.
Client:
- VRF:
TENANT_A_CLIENT - Network:
- Client: 10.1.110.0/24
- Firewall interconnection: 10.1.10.0/30
- Client VM:
10.1.110.10/24
Server:
- VRF:
TENANT_A_SERVER - Network:
- Server: 10.1.111.0/24
- Firewall interconnection: 10.1.11.0/30
- Server VM:
10.1.111.10/24
Client and server VMs must be provisioned manually
Firewall connect both VRFs with following settings:
- VRF:
Tenant_A(configured asvirtual_router) - Client security zone:
TENANT_A_CLIENT - Server security zone:
TENANT_A_SERVER
A full demo scrpit is available here
# Install reauirements
ansible-galaxy collection install requirements.yml
# Check devices connectivity
ansible-playbook playbooks/check-device-connectivity.yml --ask-vault-pass
# Manage EVPN Fabric
ansible-playbook playbooks/avd-build-and-deploy.yml --tags build,deploy --skip-tag debug --ask-vault-pass
# Manage Security zone
ansible-playbook-vault playbooks/panos-config-deploy.yml --tags build,deploy,policy --ask-vault-passAs the goal of this repository is to detail how to extend data model, we won't go through AVD data model in detaul and it would be better to read this repo example or AVD website.
All playbooks are saved under playbooks folder
- Collect facts as management connectivity checks
ansible-playbook playbooks/check-device-connectivity.yml --ask-vault-pass- AVD / Network side:
ansible-playbook playbooks/avd-build-and-deploy.yml --tags build --ask-vault-pass- Palo Alto / Security side:
ansible-playbook-vault playbooks/panos-config-deploy.yml --tags build --ask-vault-pass- AVD / Network side:
ansible-playbook playbooks/avd-build-and-deploy.yml --tags deploy --ask-vault-pass- Palo Alto / Security side:
ansible-playbook-vault playbooks/panos-config-deploy.yml --tags deploy --ask-vault-pass- Palo Alto / Security side:
ansible-playbook-vault playbooks/panos-config-remove.yml --ask-vault-passAll devices are configured with a management IP address only and the following credentials: ansible/ansible and connected to an Out Of band management.
| Hostname | Managment IP |
|---|---|
| switch01 | 10.73.254.1/24 |
| switch02 | 10.73.254.2/24 |
| switch03 | 10.73.254.3/24 |
| switch04 | 10.73.254.4/24 |
| switch05 | 10.73.254.5/24 |
| switch06 | 10.73.254.6/24 |
| switch07 | 10.73.254.7/24 |
| switch08 | 10.73.254.8/24 |
| switch013 | 10.73.254.13/24 |
| switch014 | 10.73.254.14/24 |
| switch015 | 10.73.254.15/24 |
In our example, we will build data to provision Palo Alto firewall from data coming from AVD data model. Of course, since this data model is not built for security devices, we will extend some sections.
All the transformation from AVD data model to those used by Palo Alto modules are part of this custom role avd_firewall_panos
Nothing special to do here as we won't configure an aggrgated interface. We just have to use Firewall hostname in firewalls keys.
firewalls:
FIREWALL-POD03:
rack: POD03
adapters:
- type: nic
server_ports: [ ethernet1/1 ]
switch_ports: [ Ethernet4 ]
switches: [ switch07 ]
profile: A-PR01-FIREWALLSo our role is going to generate something like:
interfaces:
- if_name: "ethernet1/1"
mode: "layer3"To generate sub-interfaces, we need to configure a bunch of things:
- Virtual Router (yes we want to isolate traffic) == Tenants in AVD
- Security Zones == VRFs in AVD
- Sub-interface information such as vlan tag and IP
To do that, we need to configure a firewalls knob under VRF / SVI
tenants:
# Tenant A Specific Information - VRFs / VLANs
Tenant_A:
mac_vrf_vni_base: 10000
enable_mlag_ibgp_peering_vrfs: true
vrfs:
TENANT_A_CLIENT:
vrf_vni: 10
svis:
110:
name: 'PR01-CLIENT'
tags: ['pod01']
enabled: true
ip_address_virtual: 10.1.110.254/24
10:
name: 'PR01-FW-INTERCO-CLIENT'
tags: ['pod03']
enabled: true
ip_address_virtual: 10.1.10.2/30
firewalls:
- name: firewall-pod03
is_aggregate_interface: true
firewall_interface: ethernet1/1
firewall_ip: 10.1.10.1/30So after building template, you can get data ready to configure your Palo Alto:
virtual_routers:
- Tenant_A
security_zones:
- TENANT_A_CLIENT
- TENANT_A_SERVER
l3_subinterfaces:
- name: "ethernet1/1.10"
tag: 10
enable_dhcp: false
ip: ["10.1.10.1/30"]
zone_name: "TENANT_A_CLIENT"
management_profile: "standard-interface-management"
virtual_router: "Tenant_A"
- name: "ethernet1/1.11"
tag: 11
enable_dhcp: false
ip: ["10.1.11.1/30"]
zone_name: "TENANT_A_SERVER"
management_profile: "standard-interface-management"
virtual_router: "Tenant_A"Also same process is used to generate a list of security objects based on SVIs address and being able to use them in the policy manager
Here we just use model provided by paloaltonetworks.panos.panos_security_rule module. It is configured under pannos group_vars but can be configured per device.
security_policies:
- rule_name: 'ICMP Permit'
rule_type: 'interzone'
description: 'Allow ICMP checks'
source_zone: ['TENANT_A_CLIENT']
source_ip: ['PR01-CLIENT']
destination_zone: ['TENANT_A_SERVER']
destination_ip: ['PR01-SERVER']
application: ['icmp', 'ping']
action: 'allow'Project published under APACHE2 license