This project provides examples for widely practiced Service Mesh configurations.
To update git submodules to latest commit use:
git submodule update --init --recursive
git submodule foreach git pull origin master
Note: you need to manually approve the InstallPlans as the script describes.
./install-service-mesh-operators.shsource default-vars.txt && export $(cut -d= -f1 default-vars.txt)Or, Export Custom vars
export bookinfo_namespace=bookinfo
export control_plane_namespace=istio-system
export control_plane_name=basic-install
export control_plane_route_name=apiThis example demonstrates a basic confiuration using:
- A single Gateway deployed in the "<control_plane_namespace>".
- A VirtualService deployed in the member namespace referencing the Gateway in "<control_plane_namespace>/<gateway_name>".
./install-service-mesh-control-plane.sh./install-basic-gateway-configuration.shOpen the following url in a web browser.
echo "https://$(oc get route ${control_plane_route_name} -n ${control_plane_namespace} -o jsonpath={'.spec.host'})/productpage"./cleanup-basic-gateway-configuration.sh./cleanup-service-mesh-control-plane.shThis example is based on the blog post Consuming External MongoDB Services but takes it a step further to show how to deploy a MongoDB instance behind the same Service Mesh on Openshift and expose it via an External Load Balancer on the mongo ingress gateway for external communication. With this configuration we can present a certificate in the mongo-ingressgateway proxy and test TLS connections from outside the mesh to MongoDB.
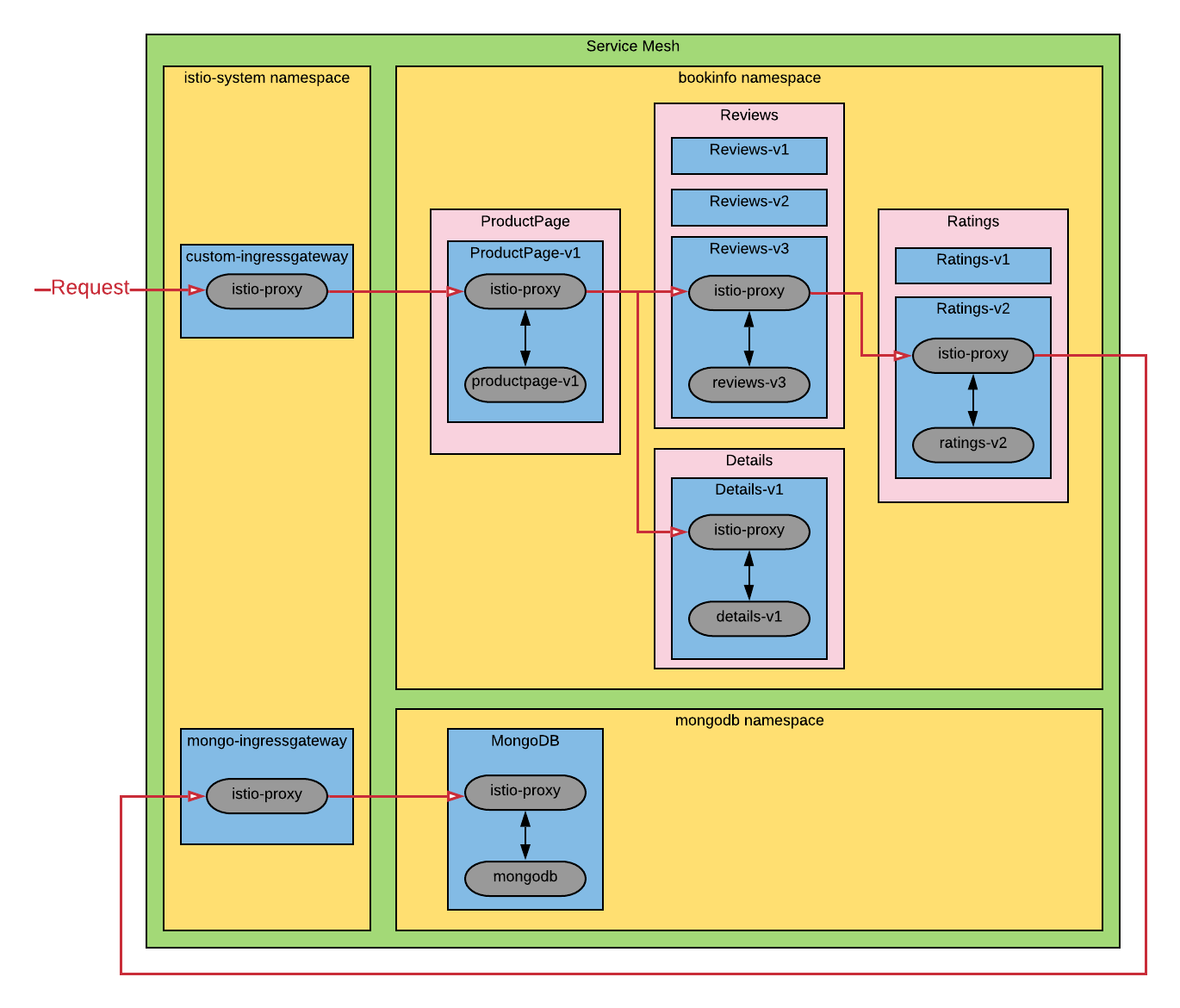
The bookinfo application is also deployed with an additional ratings-v2 service that connects to MongoDB via a ServiceEntry to the NodePort with TLS.
The updated architecture of the bookinfo app appears below:
./install-service-mesh-control-plane-mongodb.sh./install-mongo-gateway-configuration.shWait for the mongodb-v1 pod to run before running the setup script.
This will create the test database bookinfo rating-v2 service will connect to.
./ingress-mongodb-setup-tls.shOpen the following url in a web browser.
echo "https://$(oc get route ${control_plane_route_name} -n ${control_plane_namespace} -o jsonpath={'.spec.host'})/productpage"Refresh the product info page multiple times. If all was successful, you should see Reviewer 1 with a one star rating under Book Reviews.
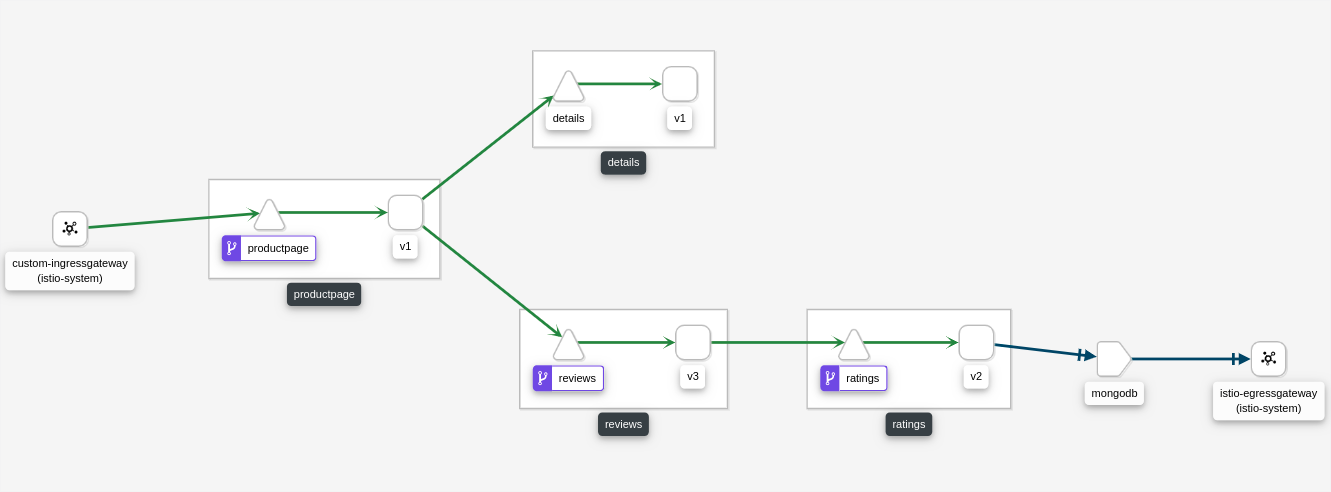
Within Kiali, all reviews requests should be directed to the rating-v2 service and then to the mongodb ServiceEntry.
You won't see traffic in kiali for mongodb requests since it is not using http or grcp, just tcp.
./cleanup-mongo-gateway-configuration.sh./cleanup-service-mesh-control-plane-mongodb.shThis example is also based on the blog post Consuming External MongoDB Services
The mongo service still exists in the same location as the previous example's architecture describes.
Direct mongo traffic through an egress gateway:
./install-service-mesh-control-plane-mongodb-egressgateway.sh./install-mongo-egressgateway-configuration.shWait for the mongodb-v1 pod to run before running the setup script.
This will create the test database bookinfo rating-v2 service will connect to.
./ingress-mongodb-setup-tls.shOpen the following url in a web browser.
echo "https://$(oc get route ${control_plane_route_name} -n ${control_plane_namespace} -o jsonpath={'.spec.host'})/productpage"Refresh the product info page multiple times. If all was successful, you should see Reviewer 1 with a one star rating under Book Reviews.
Note: the External Load Balancer host's IP can change to the mongo-ingressgateway kubernetes service on AWS. If that happens you will need to rerun install-mongo-egressgateway-configuration.sh to update the IP address of the direct-mongo-through-egress-gateway VirtualService and mongodb ServiceEntry.
The istio-proxy access logs within the istio-egrassgateway pod should show outbound traffic from it. This logging was enabled by the servicemeshcontrolplane's global.proxy.accessLogFile configuration.
[2020-07-22T00:38:16.510Z] "- - -" 0 - "-" "-" 1536 3960 24 - "-" "-" "-" "-" "13.58.124.191:27018" outbound|27018||my-mongo.tcp.svc 10.130.0.166:43250 10.130.0.166:15666 10.130.0.170:54548 - -./cleanup-mongo-egressgateway-configuration.sh./cleanup-service-mesh-control-plane-mongodb-egressgateway.shThis example demonstrates controlling outgoing traffic from the service mesh to external services. Priorities are applied based on the header that is provided with the request. In a real scenario this will most likely be injected based on some form of authentication and authorization. The example also provides samples to demonstrate the limits that are applied to the different service levels based on Istio destination rules using subsets for the external service.
This guide will walk through running the examples.