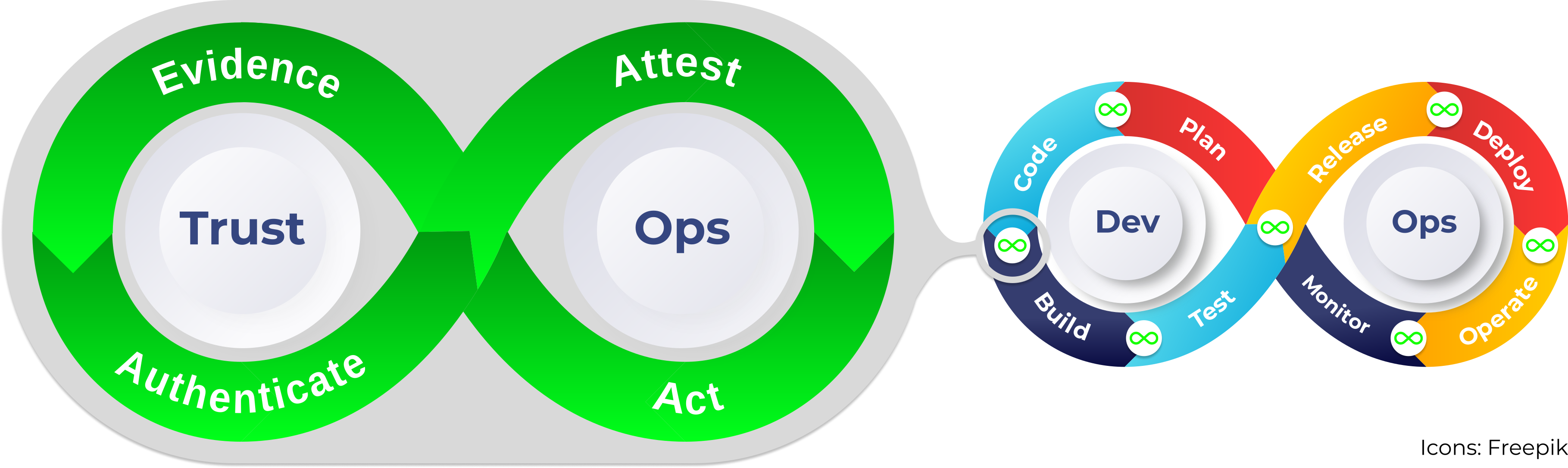
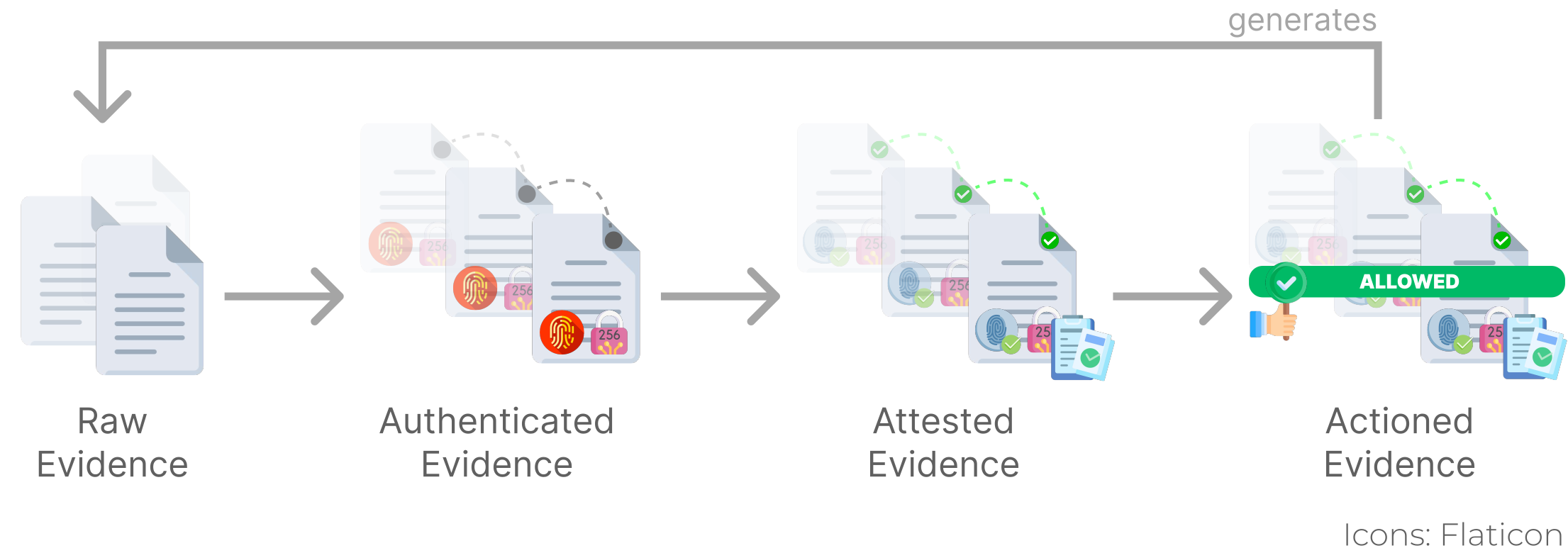
A list of tools and methods for building trustworthy software following TrustOps principles.
TrustOps is an emerging discipline focused on integrating trust and security practices across the software development lifecycle. TrustOps emphasizes automating evidence collection, authentication, attestation, and the continuous verifiability of the software supply chain to ensure that the software remains trustworthy throughout its lifecycle. The following tools and projects will help build secure, trusted software through various phases of TrustOps. Read more about TrustOps here.
- CNCF Cloud Native Security Whitepaper - Comprehensive guide to planning secure, cloud-native applications and understanding the risks at every stage.
- Chalk - A tool that captures and embeds metadata into build artifacts, enabling identification and traceability in production environments.
- SecretFlow - A framework for secure multi-party computation (MPC), helping you build secure, privacy-preserving data analytics and AI development with confidential computing mechanisms.
- GitHub Artifact Attestations - A feature to ensure that build artifacts are tamper-proof and verifiable.
- Nixpkgs Supply Chain Security Project - NixOs security initiative focused on securing the software supply chain for the Nixpkgs project.
- Reproducible Builds - A project advocating for reproducible build practices across the software supply chain.
- Chalk - A tool that captures and embeds metadata into build artifacts, enabling identification and traceability in production environments.
- in-toto - A framework to secure the integrity of software supply chains.
- OWASP SecureCodeBox - A security-testing toolchain that focuses on continuous security testing in CI/CD pipelines.
- Sigstore - Tools for signing, verifying, and protecting software supply chain components.
- Artifact Attestation for GitHub - Automates the release of artifacts with attestations to ensure that they are secure and unmodified.
- Notary - Signing and verifying artifacts. Safeguarding the software delivery security from development to deployment.
- The Update Framework - A framework for securing software update systems.
- Microsoft CCF (Confidential Consortium Framework) - Provides a secure environment for running distributed applications using confidential computing principles.
- Confidential Containers - Kubernetes-based data-in-use integrity, authenticity and confidentiality protection for sensitive workloads when released into production environments.
- Private Cloud Compute - Apple's vision for ensuring verifiable transparency, privacy and security when deploying sensitive applications.
- Nitro System Confidential Protections - Amazon's Nitro System ensuring that the infrastructure and applications remain secure during operations.
...
- Chalk - A tool that captures and embeds metadata into build artifacts, enabling identification and traceability in production environments.
- Syft - An open-source tool for generating Software Bill of Materials (SBOMs) for container images and filesystems.
- Trivy - An open-source security scanner for detecting vulnerabilities, misconfigurations, exposed secrets, and generating SBOMs in containers, filesystems, and repositories.
- GitHub Artifact Attestations - A feature to ensure that build artifacts are tamper-proof and verifiable.
- Sigstore - Tools for signing, verifying, and protecting software supply chain components.
- Notary - Signing and verifying artifacts. Safeguarding the software delivery security from development to deployment.
- Artifact Attestations - Verifies that all software artifacts have been attested to by their creators, ensuring their integrity.
- Attest.org - Ethereum Attestation Service (EAS) is an infrastructure designed to create attestations on-chain or off-chain about any subject or event, providing a public good for decentralized verification and trust.
- in-toto - A framework to secure the integrity of software supply chains.
- C-ATTS - Attest to a wide range of on-chain data, to create composite attestation.
- Kyverno - Kyverno policies can validate, mutate, generate, and cleanup Kubernetes resources, and verify image signatures and artifacts to help secure the software supply chain.
- Linus Torvalds on Security - Discussion on monitoring and maintaining trust in open-source software ecosystems.
- Private Cloud Compute - Apple's vision for ensuring verifiable transparency, privacy and security when deploying sensitive applications.
- Dependency Security - A deep dive into securing dependencies during software development and build processes.
Contributions welcome! Read the contribution guidelines first.