Empowering Ethical Phishing for Security Assessment.
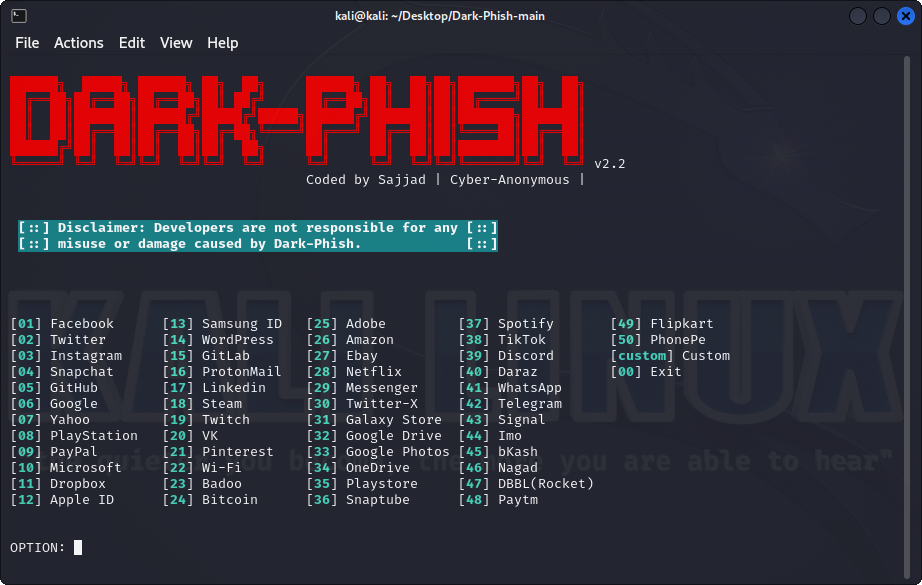
Dark-Phish is a specialized phishing tool created for educational and security testing purposes. It provides users with the capability to simulate phishing attacks, enabling the assessment of system vulnerabilities and user awareness.
Click here to view the demo on Replit
- Multiple Tunneling Options: Choose from various methods for flexible phishing simulation.
- Auto-saved Credentials: Victim credentials are stored automatically.
- Credential Management: Easily access and manage saved credentials.
- Custom Phishing Templates: Create customized and convincing phishing scenarios.
- OTP Capture: Efficiently collect one-time passwords for improved assessment capabilities.
- URL Obfuscation: Dark-Phish conceals phishing URLs, making them appear trustworthy and less suspicious.
Tested on
- Kali Linux
- Termux
Installation
apt install python3 curl php git openssh nodejs npm -ybash install.shpip3 install requests wget pyshortenersgit clone https://github.com/tucommenceapousser/Dark-Phish.git
cd Dark-PhishUsage
*Before using Dark-Phish, ensure you have the necessary packages installed as mentioned in the installation section.*
- Run Dark-Phish
python3 dark-phish.py- For help and usage information
python3 dark-phish.py -h- To access saved credentials
python3 dark-phish.py -rHelp
python3 dark-phish.py -h
Name:
Dark-Phish
Usage:
python3 dark-phish.py [-h] [-p PORT] [-u] [-v] [-r]
Version:
2.2
Options:
-h, --help Show this help message.
-p PORT, --port PORT Web server port [Default : 8080].
-u, --update Check for updates.
-v, --version Show version number and exit.
-r, --retrieve Retrieve saved credentials.Modes modded by trhacknon and custom
- custom
- customx (fun style customizable)
- facebookk
- telegram (otp)
OTP Capture Technique
- When a victim enters their credentials on the phishing page, the attacker immediately receives this information.
- The attacker, using the victim's credentials, logs into the legitimate website.
- The genuine website sends an actual OTP to the victim.
- Believing it's legitimate, the victim enters the OTP on the phishing page.
- The attacker intercepts the OTP, gaining access to the victim's credentials and logging in first.
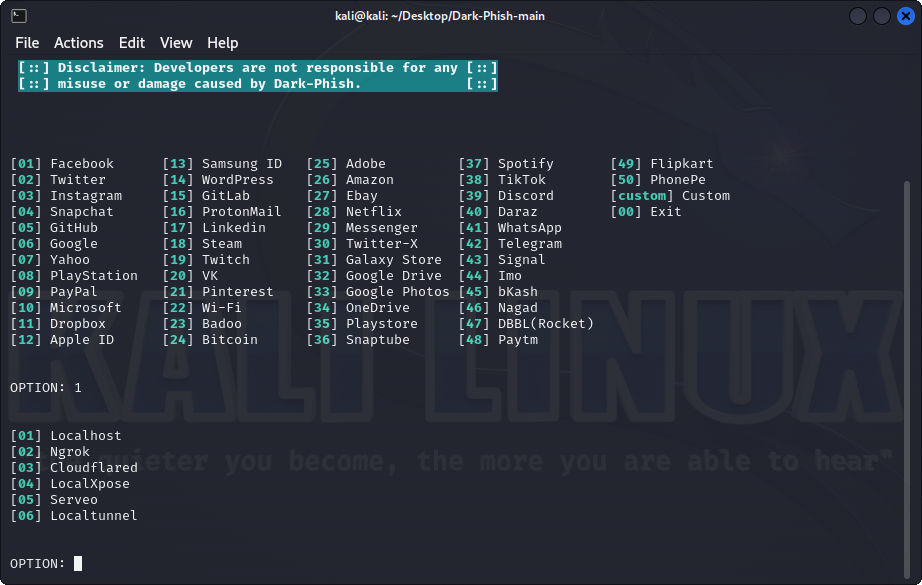
Available tunnels
- Localhost
- Ngrok
- Cloudflared
- LocalXpose
- Serveo
- Localtunnel
Dark-Phish is intended for educational and testing purposes only. Any use of this tool for illegal or unethical activities is strictly prohibited. The authors and contributors are not responsible for any misuse or damage caused by Dark-Phish. Use it responsibly and ensure compliance with all applicable laws and regulations in your jurisdiction.