- Prerequisites
- Patterns
- Getting Started
- Default Landing Zone Configuration
- Customizing Your Environment
- Running the Scripts Locally
To ensure that Secure Landing Zone can be deployed, esure that the following steps have been completed before deployment.
An IBM Cloud account is required. An Enterprise account is recommended but Pay as you Go account suffices to deploy secure landing zone cloud resources.
If you do not already have an account, follow instructions to create the account and upgrade to Pay-as-you-Go
- Have access to an IBM Cloud account. An Enterprise account is recommended but a Pay as you Go account should also work with this automation.
-
Log into IBM Cloud console using the IBMid you used to setup the account. This IBMid user is the account owner and has all the IAM accesses.
-
Complete the company profile and contacts information for the account. This is required to stay in compliance with IBM Cloud Financial Service profile.
-
Enable the flag to designate your IBM Cloud account to be Financial Services Validated.
-
Enable VRF and Service Endpoints. This requires creating a support case. Follow instructions carefully.
-
Create an IBM Cloud API Key. User owning this key should be part of admins group. Necessary if manually provisioning
-
Setup Cloud IAM Access Groups. User access to cloud resources will be controlled using the Access Policies assigned to Access Groups. IBM Cloud Financial Services profile requires that all IAM users do not get assigned any accesses directly to any cloud resources. When assigning Access policies, Click "All Identity Access Enabled Services" from drop down menu.
For Key Management services, user can optionally use Hyper Protect Crypto Services. This instance will need to be created before creating the Secure Landing Zone.
To provision an instance of Hyper Protect Crypto Services IBM Cloud Console, complete the following steps:
- Log in to your IBM Cloud account.
- Click Catalog to view the list of services that are available on IBM Cloud.
- From the Catalog navigation pane, click Services. And then, under Category, select Security.
- From the list of services displayed, click the Hyper Protect Crypto Services tile.
- On the service page, select the pricing plan of choice.
- Fill in the form with the details that are required.
To initialize the provisioned Hyper Protect Crypto Service instance, we recommend to follow the product docs to perform the quick initialization.
Hyper Protect Cyrpto Service Documentation
For proof of technology environments we recommend using the auto-init feature. Auto Init Documentation
The toolchain requires authorization to access your repository. If it does not have access, the toolchain will request that you authorize access. Below shows you how you can create a personal access token for your repository
You can manage your authorizations via Manage Git Authorizations
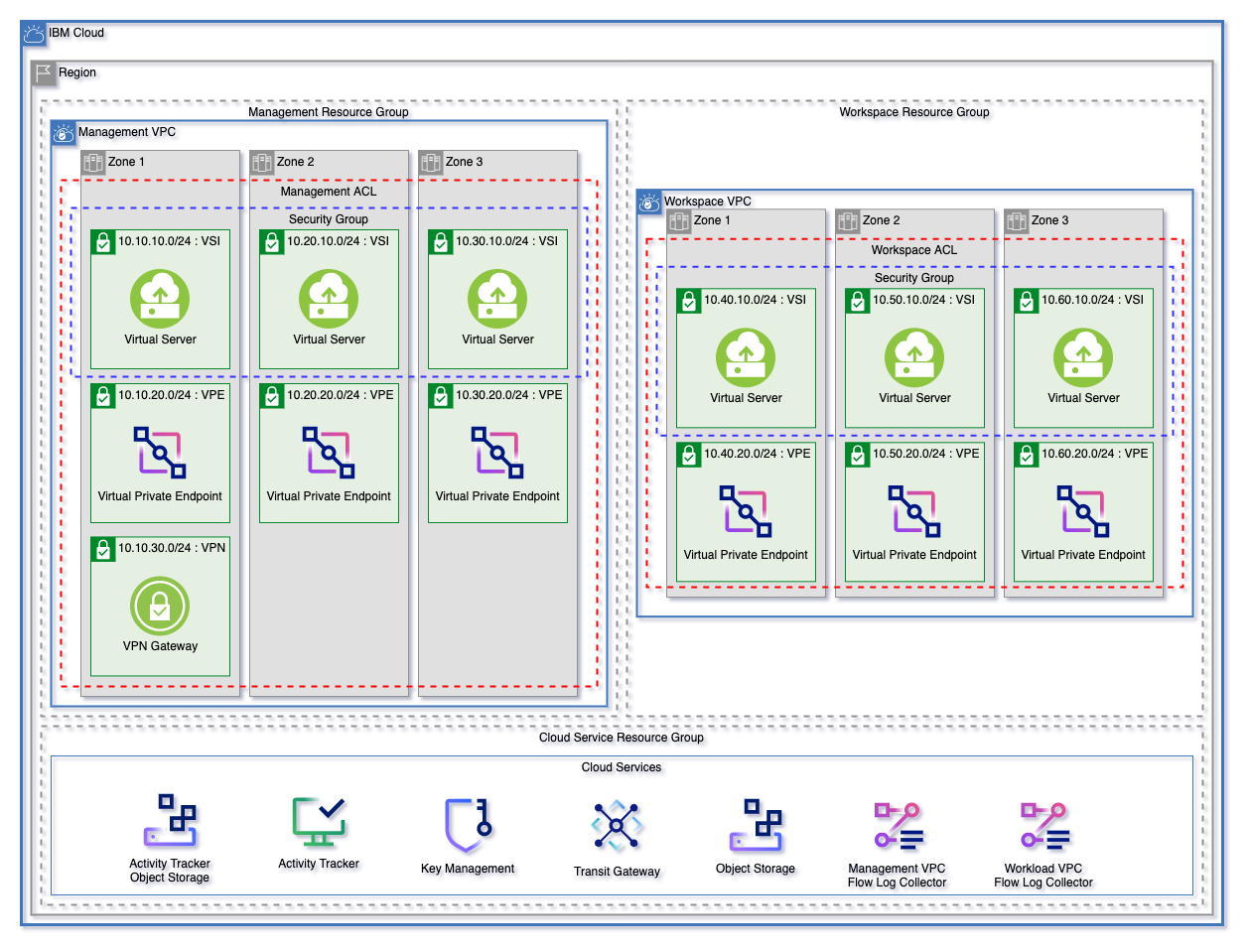
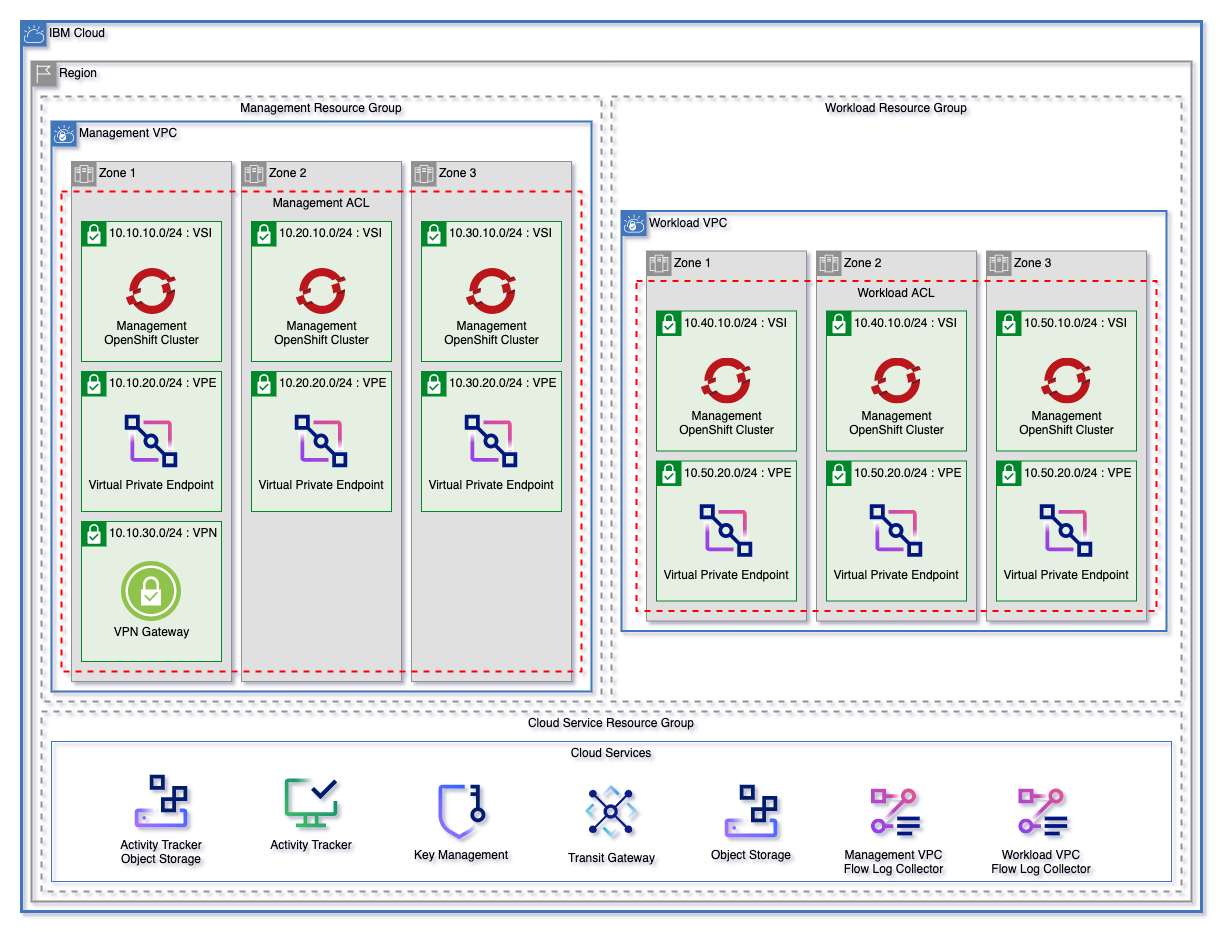
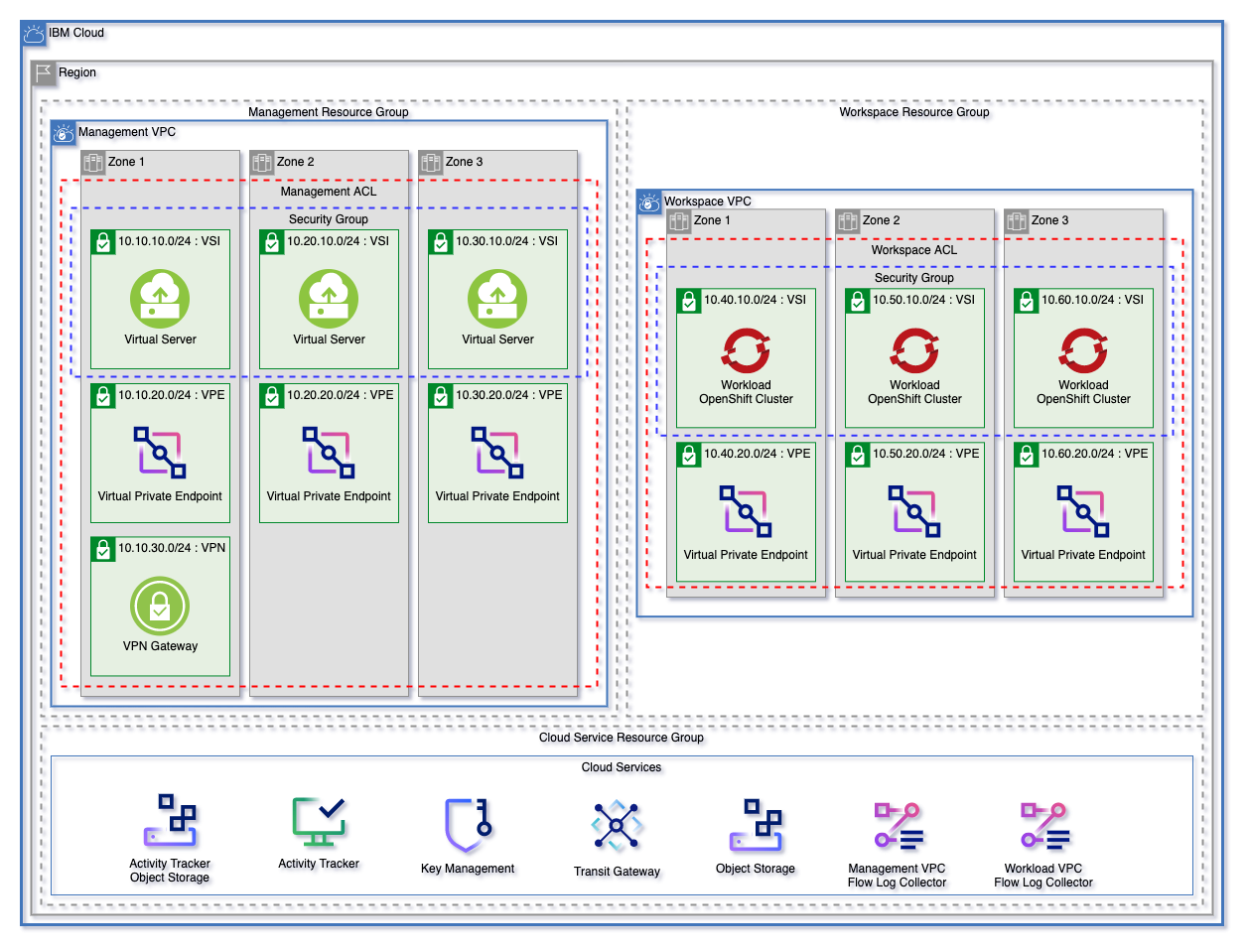
The landing zone module can be used to create a fully cusomizable VPC environment. The three patterns below are each starting templates that can be used to quickly get started with Landing Zone. These patterns can be found in the patterns directory.
Each of these patterns creates:
- A resource group for cloud services and for each VPC.
- Object storage instances for flow logs and activity tracker
- Encryption keys in either a Key Protect or Hyper Protect Crypto Services instance
- A management and workload VPC connected by a transit gateway
- A flow log collector for each VPC
- All nessecary networking rules to allow communication
- Virtual Private endpoints for Cloud Object storage in each VPC
- A VPN Gateway in the Management VPC
Each pattern will create an identical deployment on the VPC
- Virtual Server (VSI) Pattern will deploy identical virtual servers across the VSI subnet tier in each VPC
- Red Hat OpenShift Kubernetes (ROKS) Pattern will deploy identical clusters across the VSI subnet tier in each VPC
- The Mixed pattern will provision both of the above
To read more detailed documentation about the default configuration, read the pattern defaults here.
Whether provisioning with toolchain or running locally:
Both require editing terraform.tfvars with required variables noted by "< add user data here >"
You can provision an IBM Cloud Toolchain utilizing the template to create a CI/CD pipeline of executing Secure Landing zone. After reading the instructions on using the IBM Cloud Toolchain Template, click the "Deploy to IBM Cloud" button below to start the process. If you do not see the button, please log into IBM Cloud.
Once completed process:
- Click Repository tile
- Click Patterns directory
- Choose the appropriate pattern, edit
terraform.tfvarsfile and commit. - Please read the Working with IBM Cloud Toolchains for configuration and how to run the Toolchain
To run the scripts locally, follow these steps:
- Install Terraform CLI and IBM Cloud Provider plug-in with these steps. Install Python.
- Select the pattern that you want to provision (vsi/mixed/roks) within the patterns directory.
- Provide your
tfvarsfile with required variables, such as prefix, region, etc. - Provide your IBM Cloud API key through an environment variable (ex: export TF_VAR_ibmcloud_api_key=")
- Run
terraform initto initialize the working directory and configuration. - Run
terraform planto preview the changes that Terraform plans to make to your infrastructure. - Run
terraform applyto execute the plan to create or modify your infrastructure. - Once you no longer need the infrastructure, you can run
terraform destroyto delete the resources.
Additional VPC's can be added using the terraform.tfvars file by adding the name of the new VPC as a string.
vpcs = ["management", "workload", "<ADDITIONAL VPC>"]
Provisioned VPC components
To create a fully customized environment based on the starting template, users can use override.json by setting the template override variable to true.
By using the variable deifnitions found in our landing zone module any number and custom configuration of VPC components, VSI workoads, and clusters can be created. Currently override.json is set to contain the default environment configuration.
This module outputs config, a JSON encoded definition of your environment based on the defaults for Landing Zone and any variables changed using override.json. By using this output, it's easy to configure multiple additional workloads, VPCs, or subnets in existing VPCs to the default environment.
override.json does not need to contain all elements. As an example override.json could be:
{
"enable_transit_gateway": false
}As we develop the SLZ template, issues are bound to come up. When an issue comes up the following are required. Issues that do not have complete information will be closed immediately.
- A detailed title that is either the source of a bug, or a user story for the feature that needs to be added.
- example
As a user, I want to be able to provision encryption keys using either HPCS or Key Protect
- example
- Any additional information about the use case is helpful, so please be sure to include it.
- A detailed title that is either the source of a bug
- example
When provisioning ROKS, network ALBs cannot be provisioned.
- example
- If you are creating an issue related to a bug, a list of non-sensitive variables in code block format being used to create the architecture must be added to the issue description. This will enable us to recreate the issue locally and diagnose any problems that occur
- Additionally, if there are any logging errors, please include those as text or as part of a code block.