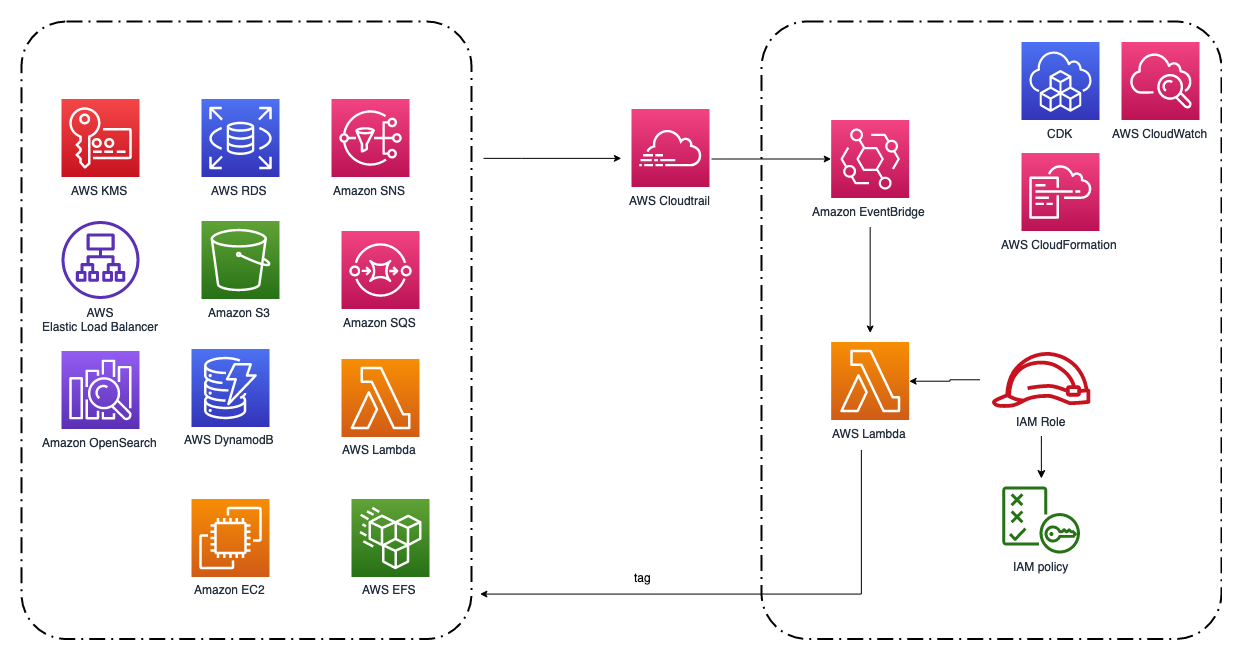
This is a Lambda function that can auto tagging newly created AWS resources. It is triggered by EventBridge events from CloudTrail logs. Currently it supports tagging EC2, S3, DynamoDB, RDS, Lambda, EFS, EBS, ELB, OpenSearch, SNS, SQS, ElastiCache and KMS.
The solution will Tag those supported resources with pre-defined tags and also (optionally) the identity used to deploy them for easier ownership and cost allocation.
Notice that the solution can only tag newly created resources, if you want to tag resources already created, please go to AWS Tag Editor Console, https://console.aws.amazon.com/resource-groups/tag-editor/find-resources.
If you want to deploy by CloudFormation, please refer https://github.com/aws-samples/resource-tagging-automation/tree/main/cloudformation.
-
A Linux machine to deploy CDK codes, with AWS IAM user's AK/SK configured.
-
Python3.8 and NodeJS are installed on the Linux machine.
- Ensure CDK is installed
$ npm install -g aws-cdk
- Create a Python virtual environment
$ python3 -m venv .venv
- Activate virtual environment
On MacOS or Linux
$ source .venv/bin/activate
On Windows
% .venv\Scripts\activate.bat
- Install the required dependencies.
$ pip install -r requirements.txt
- Bootstrapping cdk environment.
$ cdk bootstrap
- Synthesize (
cdk synth) or deploy (cdk deploy) the example, use --parameters to pass additional parameters, use --require-approval to run without being prompted for approval, Please replace your own tags to the tags parameter.
$ cdk deploy --require-approval never --parameters tags='{"TagName1": "TagValue1","TagName2": "TagValue2"}'
(Optional) You can also choose to disable the Identity Recording feature by definening the identityRecording parameter to false. This feature is enabled by default.
$ cdk deploy --require-approval never --parameters tags='{"TagName1": "TagValue1","TagName2": "TagValue2"}' --parameters identityRecording='false'
-
Configure AWS CLI, please refer https://docs.aws.amazon.com/cli/latest/userguide/cli-configure-quickstart.html#cli-configure-quickstart-config
-
Ensure the Lambda function is successfully created.
$ aws lambda list-functions | grep FunctionName | grep resource-tagging-automation-function
- Lambda function will be invoked when EventBridge rule triggered, such as EC2 Runinstances event, and the resource will be tagged by the Lambda function.
Notice this operation will destroy the Lambda function and all other resources created by CDK.
$ cdk destroy
- Go to AWS Console and navigate to Amazon EventBridge --> Rules, find and select rule 'resource-tagging-automation-awstaggingautomationruleXXXXXX', click 'Edit' button.
- Go to step 2 and find 'Event pattern' chapter, add new resource in eventSource, eventName and source.
- Keep clicking 'Next' button until click 'Update rule' in step 5.
- Go to AWS Console and navigate to Lambda --> Functions, find out function 'resource-tagging-automation-function'.
- Edit the function code, add a method to get newly created resources' ARN list from EventBridge rule event.
- The method example is as below.
def aws_elasticloadbalancing(event):
arnList = []
if event['detail']['eventName'] == 'CreateLoadBalancer':
print("tagging for new LoadBalancer...")
lbs = event['detail']['responseElements']
for lb in lbs['loadBalancers']:
arnList.append(lb['loadBalancerArn'])
return arnList
If your account permissions aren't set up correctly, or if you stop a deployment, you may have to manually clean up deployed resources. Navigate to the CloudFormation console, select the stack that needs to be cleaned up, and click the Delete button to destroy the stack manually and start over.
See CONTRIBUTING for more information.
This library is licensed under the MIT-0 License. See the LICENSE file.