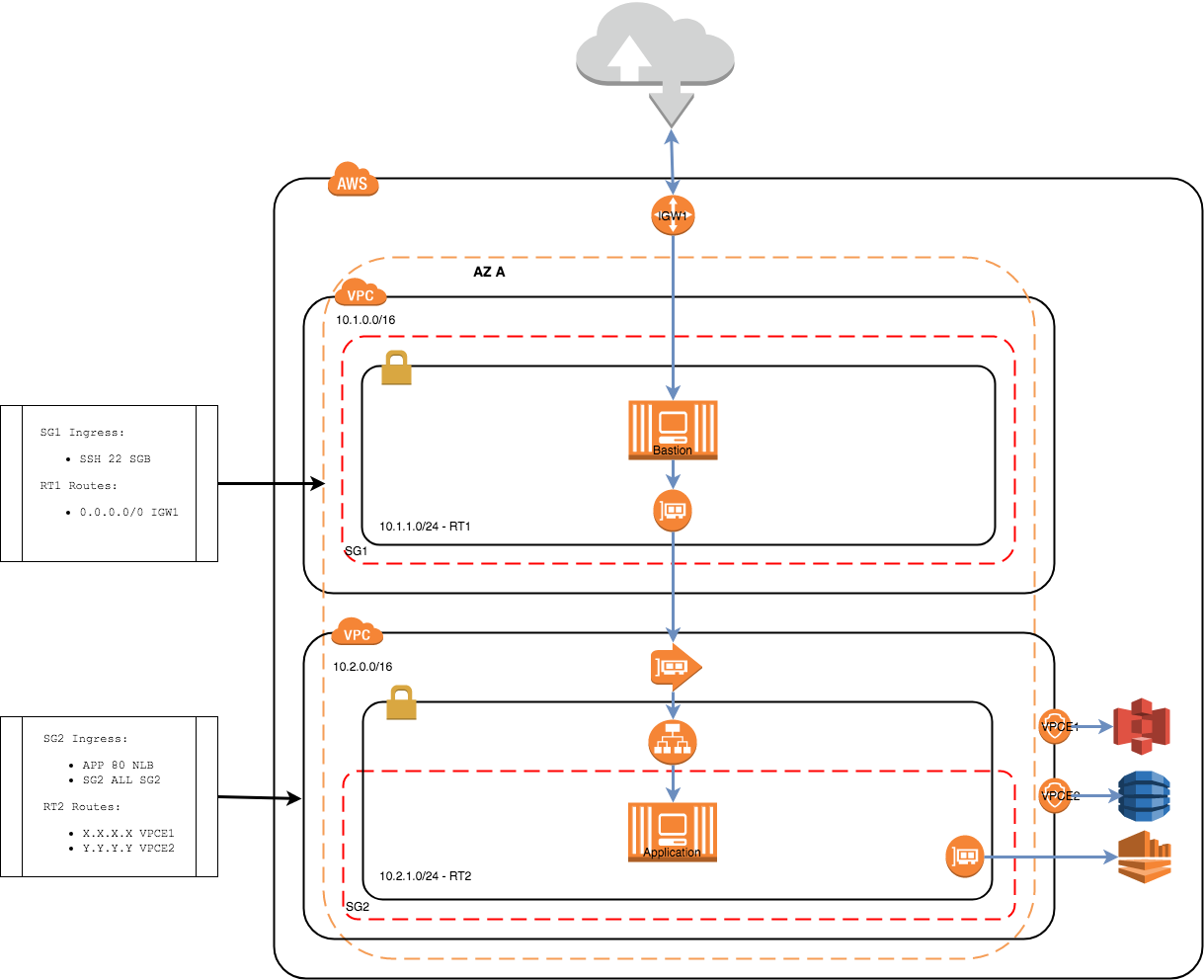
This project demonstrates how 2 non-peered fully segregated VPC's are able to communicate using
VPC Service Endpoints and a VPC Interface Endpoints
The bastion host in this diagram acts as the client for the application hosted in VPC 2 (10.2.0.0). The application has a very simple HTTPD running on port 80. An NLB is used to front a target group for the application on port 80. The VPC service endpoint is offering access to this application using a private DNS. Note that the security group 2 (SG2) has an ingress rule that allows TCP traffic from port 80 for all of the subnet. The reason for this is that the NLB is not attached to a security group and can take on any IP address in the assigned subnet.
In VPC 1 (10.1.0.0) a VPC endpoint interface has been created to connect to the application. The endpoint establishes an ENI that has been assigned to the same security group (SG1) as the bastion.
You will need the following tools and accounts to make it happen
You will need an AWS account, if you don't have one then just Sign-Up You will need a development user with admin access and security access keys in order to use the AWS CLI
Install the AWS CLI and set-up a profile using your access keys
You will need to set-up your desired AWS region with a secure key pair. This project is using London (eu-west-2) as the region I suggest you keep this the same as there are AMI's referenced that are region sensitive.
EC2 Key Pairs has instructions on how to set-up your key pair.
Once you have set-up key pair you will have access to the PEM file that needs to be stored safely. Terraform assumes that the PEM is available in your local key chain, you can add it it to your key-chain by running the following command
ssh-add -K your-key.pem
Install terraform command line tool. Depends on your OS, Install Terraform has some descent instructions.
If you are using OSX I suggest you use Homebrew to install the terraform package.
I suggest that you run a plan to determine that access to your AWS account is as expected. Run the following command in the root of the terraform source src/main/terraform Note that it is recommended that you override the default values for aws_profile and the bastion_network_cidr
terraform plan -var "aws_key_name=your-key-name" -var "aws_region=us-east-1"
The output of this command will detail all the resources that will be created once applied. Note that it is recommended that you override the default values for aws_region (eu-west-1), aws_profile (default) and the bastion_network_cidr (0.0.0.0/0) e.g.
terraform plan -var "aws_key_name=you-key" -var "aws_profile=bastion-lab" -var "bastion_network_cidr=199.250.200.0/24"
Once you are happy with the plan apply and decided on what variables to override you can apply your plan e.g.
terraform apply -var "aws_key_name=you-key" -var "aws_profile=bastion-lab" -var "bastion_network_cidr=199.250.200.0/24"
The best way to test the application is to SSH on to the test host and attempt accessing the internet.
- SSH to the bastion host - ssh ~/.ssh/<YOUR_KEY>.pem ec2-user@<BASTION_HOST_IP>
- cURL the application using the private DNS name - curl -I http://<VPC_ENDPOINT_PRIVATE_DNS>
Example Output:
curl -I http://vpce-058b2372d45e91f4e-9pa4nqob.vpce-svc-0841bfa5bc94b1b7b.eu-west-1.vpce.amazonaws.com
HTTP/1.1 200 OK
Content-Type: text/html
Server: WEBrick/1.3.1 (Ruby/2.0.0/2015-12-16)
Date: Wed, 28 Mar 2018 13:12:40 GMT
Content-Length: 2426
Connection: Keep-Alive
Clean up your environment by detroying, this will remove all traces:
terraform destroy -var 'aws_key_name=your-key.pem'