- A set of exploitation and reversing aids for IDA
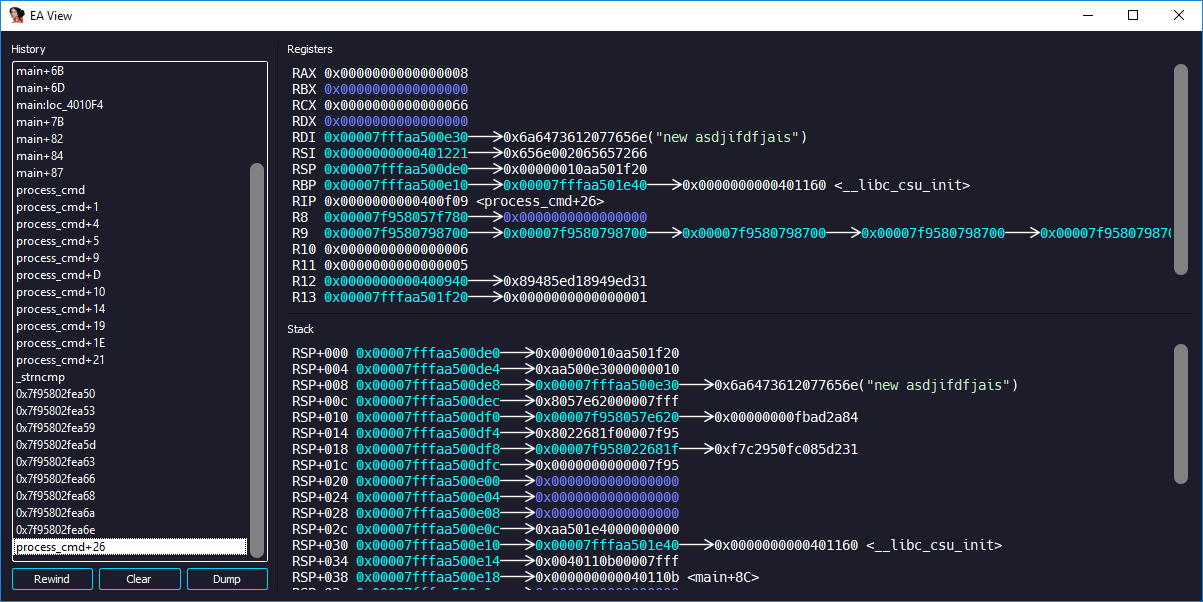
New context viewer for IDA, Features include:
-
Recursive pointer derfereneces
-
History browser
-
Color coded memory
-
Instruction rewind feature
-
A similar interface to that of popular
GDBplugings (eg.PEDA/GEF)
-
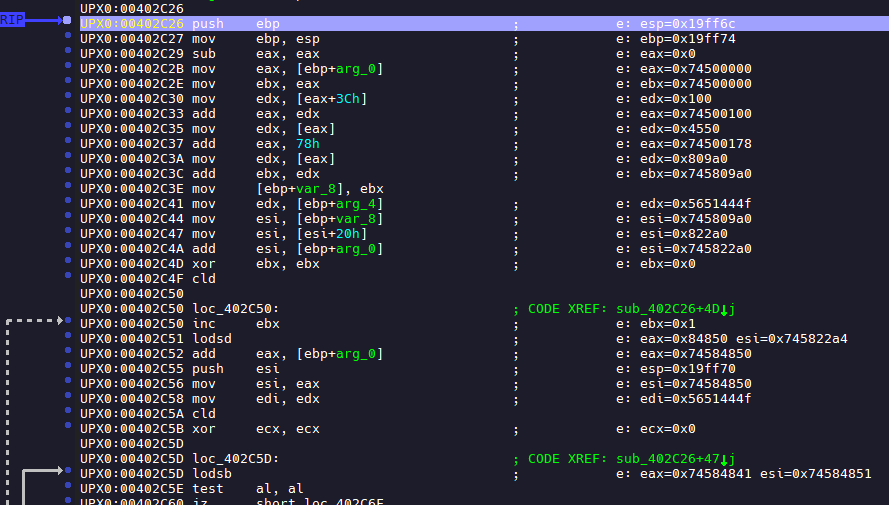
Live annotate the results if furture instructions in IDA using the
UnicornCPU emulator -
Can be hooked to breakpoints
-
Visualise instructions before execution
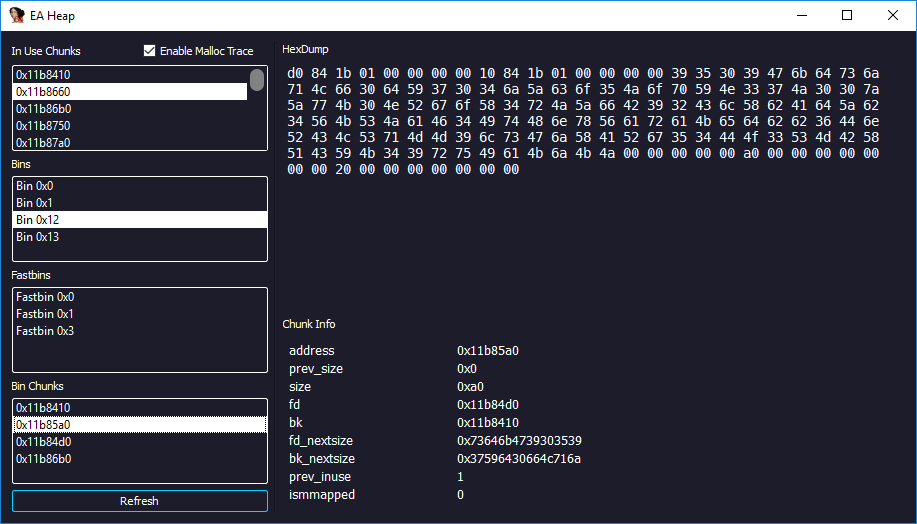
Explore current heap state of glibc binaries
-
Trace allocations
-
Enumerate bins
-
View all free and allocated chunks headers
-
Useful for heap exploitation / debugging.
-
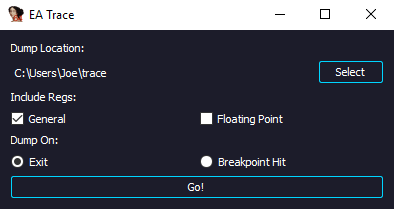
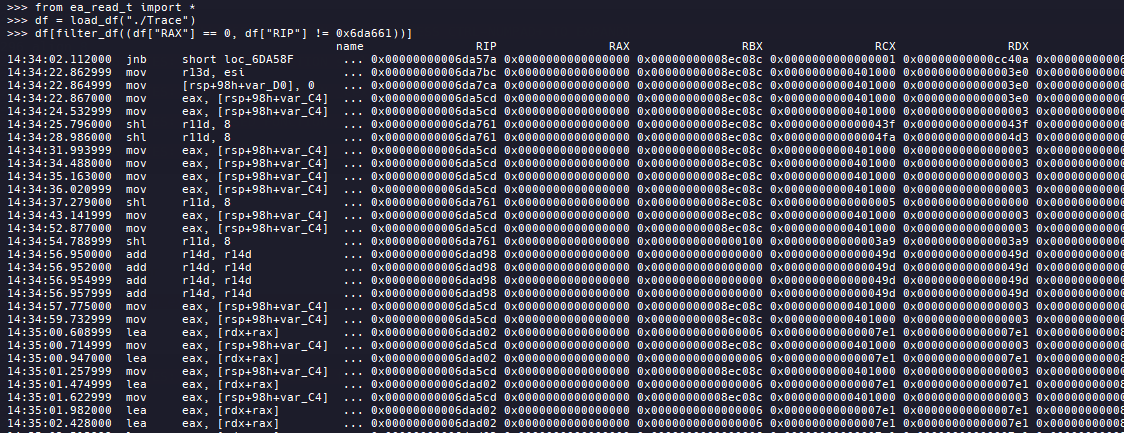
Dump the results of an IDA trace into a Pandas Dataframe
-
Analyze traces in Python using Pandas
-
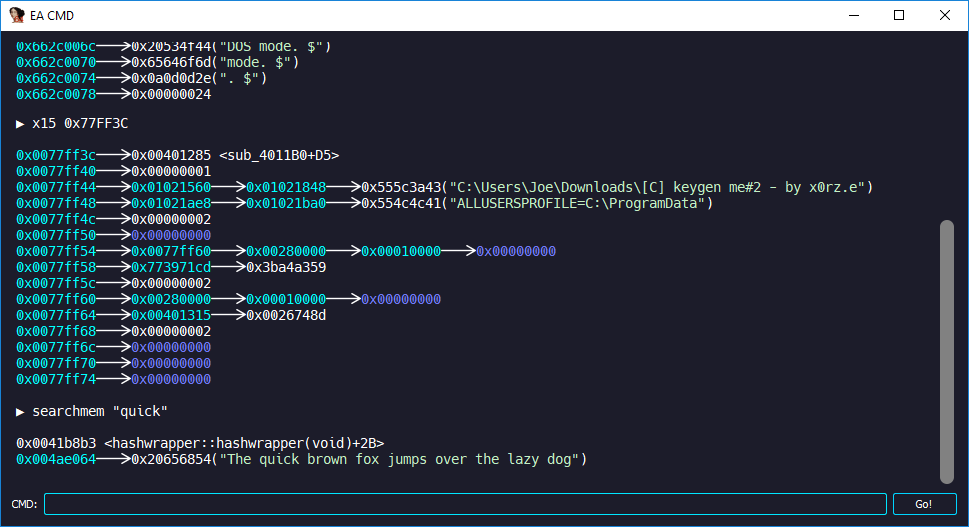
GDB bindings for IDA
-
GDB style mem queries + searches
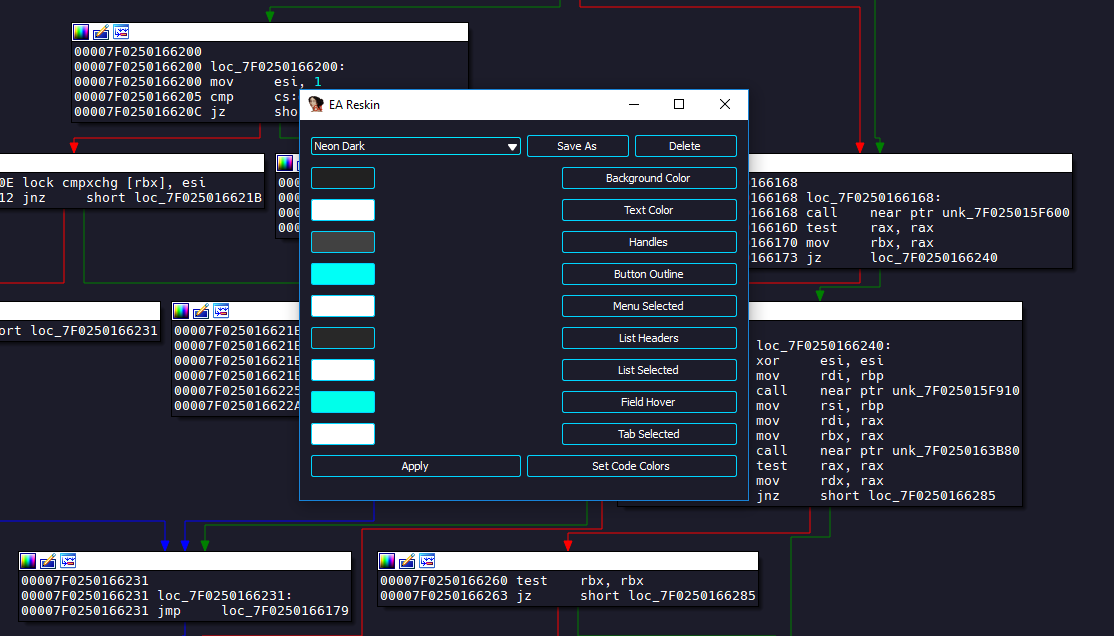
- Restyle IDA using GUI.
No core dependencies for the plugin. Nevertheless certain fetures will be disabled without these python libraries installed:
Pandas
Unicorn CPU emulatorCapstone Dissasembler
-
Place
ida_eafolder inIDA Prodirectory (C:\Users\{name}\AppData\Roaming\Hex-Rays\IDA Proon Windows) -
Add line
from ida_ea import ea_mainto youridapythonrcfile. -
Plugin is accessed via
IDA EAtab added to the menu bar
-
Only tested on Windows with
IDA 6.8 -
Only supports
x86/x86-64binaries -
Alpha release so expect many bugs!