中文 | EN
This script is used to detect Docker container escape methods, The following methods are currently supported:
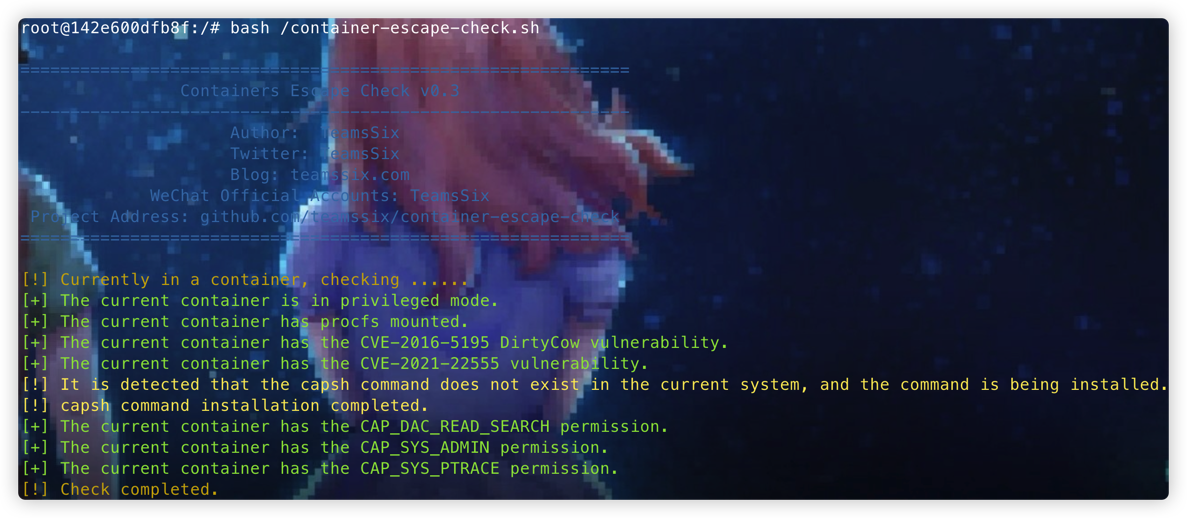
- Privileged Mode
- Mount docker Socket
- Mount host procfs
- Mount host root or etc directory
- Open Docker Remote API
- CVE-2016-5195 DirtyCow
- CVE-2020-14386
- CVE-2022-0847 DirtyPipe
- CVE-2017-1000112
- CVE-2021-22555
- Mount Host Var Log
- CAP_DAC_READ_SEARCH (Requires container to support capsh command)
- CAP_SYS_ADMIN (Requires container to support capsh command)
- CAP_SYS_PTRACE (Requires container to support capsh command)
- CVE-2022-0492
Run this script with one command in the container.
wget https://raw.githubusercontent.com/teamssix/container-escape-check/main/container-escape-check.sh -O- | bash
Or clone the project to run in the container.
git clone https://github.com/teamssix/container-escape-check.git
cd container-escape-check
chmod +x container-escape-check.sh
./container-escape-check.sh
If it feels good, remember to give the project a little star ✨
- This script needs to be run inside the docker container.
- Most of the detection methods here are based on my experience, and there may be false positives or omissions. If you find these problems, please submit an Issue.
- Some escape methods need to be judged according to the Docker version. I haven't thought of a way to get the Docker version from inside the container, so the script does not support the detection of this method yet.
- Add CVE-2022-0492
- If the capsh command does not exist, it will be installed automatically
- Enhanced privileged mode detection
- Enhanced /var/log detection
- Add CVE-2017-1000112
- Add CVE-2021-22555
- Add Mount Host Var Log
- Add CAP_DAC_READ_SEARCH
- Add CAP_SYS_ADMIN
- Add CAP_SYS_PTRACE
- Add Privileged Mode
- Add Mount docker Socket
- Add Mount host procfs
- Add Mount host root or etc directory
- Add Open Docker Remote API
- Add CVE-2016-5195 DirtyCow
- Add CVE-2020-14386
- Add CVE-2022-0847 DirtyPipe