| 黑白天实验室 |
HBT-SEC |
使用 Cobalt Strike 的 Beacon 对象文件自定义 DLL 注入 |
https://mp.weixin.qq.com/s?__biz=MzU4NTY4MDEzMw==&mid=2247491372&idx=1&sn=b3a3ddd688cdb8482de4afe4f0c31b23 |
| 潇湘信安 |
xxxasec |
任意文件上传之绕过云waf+本地防火墙双重防护 |
https://mp.weixin.qq.com/s?__biz=Mzg4NTUwMzM1Ng==&mid=2247491780&idx=1&sn=da7ec649bc7de8d7d9f8fe2405039e89 |
| LSCteam |
gh_d97c073d1479 |
使用含有已知漏洞的组件 |
https://mp.weixin.qq.com/s?__biz=MzUyMjAyODU1NA==&mid=2247488551&idx=1&sn=94554b33a1f4bd88af2fe0835d8e253f |
| Bypass |
Bypass-- |
内网渗透之域内信息收集 |
https://mp.weixin.qq.com/s?__biz=MzA3NzE2MjgwMg==&mid=2448907444&idx=1&sn=ec879432f580c5933ca651adcc6017ec |
| 酒仙桥六号部队 |
anfu-360 |
MYSQL另类利用方式 |
https://mp.weixin.qq.com/s?__biz=MzAwMzYxNzc1OA==&mid=2247493839&idx=1&sn=6e580a2e6194c80903adb1cacde39ae9 |
| 贝塔安全实验室 |
BetaSecLab |
漏洞分析 , CVE-2021-40444 |
https://mp.weixin.qq.com/s?__biz=Mzg4MzA4Nzg4Ng==&mid=2247494410&idx=1&sn=a212400507f9bb248be472f802b5b48e |
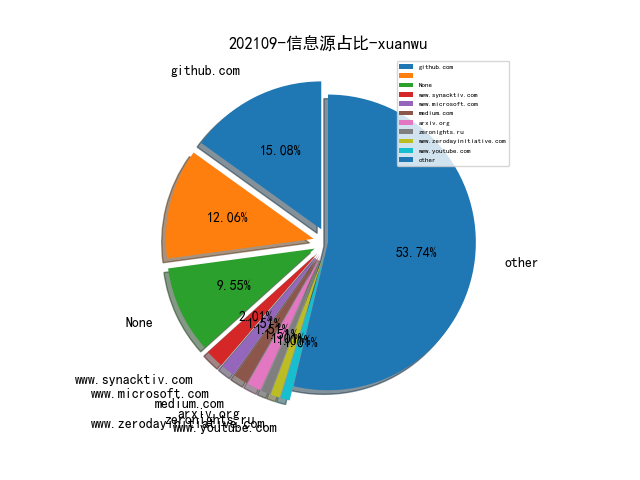
| 腾讯玄武实验室 |
XuanwuLab |
每日安全动态推送(09-29) |
https://mp.weixin.qq.com/s?__biz=MzA5NDYyNDI0MA==&mid=2651957890&idx=1&sn=584f313442a647f742e44511327fe678 |
| 维他命安全 |
VitaminSecurity |
微软发现旨在窃取AD FS管理员凭据的后门FoggyWeb;QNAP发布更新,修复QVR中3个严重的命令注入漏洞 |
https://mp.weixin.qq.com/s?__biz=MzUxMDQzNTMyNg==&mid=2247496793&idx=1&sn=267417ccc28682bc861b09bb155be909 |
| 看雪学院 |
ikanxue |
从两道0解题看Linux内核堆上msg_msg对象扩展利用 |
https://mp.weixin.qq.com/s?__biz=MjM5NTc2MDYxMw==&mid=2458394993&idx=2&sn=2083b054decba632e3a17f751e5541ee |
| 灼剑安全团队 |
Tsojan |
Linux下应急溯源常用命令 |
https://mp.weixin.qq.com/s?__biz=Mzg5OTY1ODMxMg==&mid=2247488152&idx=1&sn=89e1fa4d998b39596460e524b274d0cb |
| 火线Zone |
huoxian_zone |
PHP代码审计之漫画CMS |
https://mp.weixin.qq.com/s?__biz=MzI2NDQ5NTQzOQ==&mid=2247488859&idx=1&sn=8635058f3f0d038d3d86e1dc7117f1f5 |
| 渗透云笔记 |
shentouyun |
[翻译]盲SSRF利用链术语表 |
https://mp.weixin.qq.com/s?__biz=MzU2NzkxMDUyNg==&mid=2247491169&idx=1&sn=8dc73bc4fc943d42d8dd54db570febb3 |
| 深信服千里目安全实验室 |
Further_eye |
【漏洞通告】Openssh权限提升漏洞 CVE-2021-41617 |
https://mp.weixin.qq.com/s?__biz=MzI4NjE2NjgxMQ==&mid=2650256017&idx=1&sn=daea5afb6a1497825ccd24f7faf27e0a |
| 微步在线研究响应中心 |
gh_c108d4d389bf |
推陈出新,Donot组织窃密手法再升级 |
https://mp.weixin.qq.com/s?__biz=MzA5MDc1NDc1MQ==&mid=2247489841&idx=1&sn=3037ef80319c1ef79b39d41023b635db |
| 宽字节安全 |
gh_2de2b9f7d076 |
Windows委派 |
https://mp.weixin.qq.com/s?__biz=MzUzNTEyMTE0Mw==&mid=2247485421&idx=1&sn=fe9a3d2e891b9df1604fb9065645f465 |
| 天禧信安 |
txxa-385 |
【VulnStack】 ATT&CK RedTeam评估 |
https://mp.weixin.qq.com/s?__biz=MzUyMTE0MDQ0OA==&mid=2247486184&idx=1&sn=cde91af24257a2543ba3cdf42a55d200 |
| 大余安全 |
dayuST123 |
HackTheBox-Linux-Registry |
https://mp.weixin.qq.com/s?__biz=Mzg3MDMxMTg3OQ==&mid=2247496596&idx=1&sn=1f299bba0781781d4cefca08b7308f43 |
| 嘶吼专业版 |
Pro4hou |
【技术原创】ProxyOracle利用分析2——CVE-2021-31196 |
https://mp.weixin.qq.com/s?__biz=MzI0MDY1MDU4MQ==&mid=2247529637&idx=1&sn=2aeaf574df8400aa4414e9cadcb5657e |
| 合天网安实验室 |
hee_tian |
一款专门针对高质量女性的易语言钓鱼样本简单分析 |
https://mp.weixin.qq.com/s?__biz=MjM5MTYxNjQxOA==&mid=2652881368&idx=1&sn=2d2d7e3290ab00c2d655e80c5a16ec5d |
| thelostworld |
gh_3f2e5b9f028c |
一、小程序|App抓包(一)环境篇 |
https://mp.weixin.qq.com/s?__biz=MzIyNjk0ODYxMA==&mid=2247486232&idx=1&sn=927a38a8584a529494d8079810b2fe29 |
| i春秋 |
icqedu |
HTB靶场记录之OpenAdmin |
https://mp.weixin.qq.com/s?__biz=MzUzNTkyODI0OA==&mid=2247506053&idx=1&sn=54bc8a3ba648c71766ac528f28252e8e |
| SecIN技术平台 |
sec-in |
原创 , 内核缓冲区溢出3--开启kaslr |
https://mp.weixin.qq.com/s?__biz=MzI4Mzc0MTI0Mw==&mid=2247491320&idx=1&sn=ec22d97e39dfdc595a1b406e9634350d |
| HACK之道 |
hacklearn |
Fiddler对安卓模拟器里的APP抓包(步骤详细,各种抓包工具总结) |
https://mp.weixin.qq.com/s?__biz=MzIwMzIyMjYzNA==&mid=2247495402&idx=1&sn=d24822042735ec7f66be115d3408dd2d |
| 默安玄甲实验室 |
gh_fb6fe2418513 |
数据库利用 看这篇就好了 |
https://mp.weixin.qq.com/s?__biz=MzkzNjI2MzgzOA==&mid=2247484035&idx=1&sn=60ae9a2a6832ef9521df269ee57bce8e |
| 知道创宇 |
knownsec |
知道创宇云监测—ScanV MAX更新:Atlassian JIRA、DocCMS 、rConfig等12个漏洞可监测 |
https://mp.weixin.qq.com/s?__biz=MjM5NzA3Nzg2MA==&mid=2649855432&idx=4&sn=039b61624fc7d938de5f0d76dd1692e4 |
| 猪猪谈安全 |
zzt-anquan |
干货 , 逻辑漏洞出现场景、利用方式总结 |
https://mp.weixin.qq.com/s?__biz=MzIyMDAwMjkzNg==&mid=2247495677&idx=1&sn=4c07abcde1c0f8af41f502aced5fcaaa |
| 渗透Xiao白帽 |
SuPejkj |
【干货】记一次对某客户端的安全测试 |
https://mp.weixin.qq.com/s?__biz=MzI1NTM4ODIxMw==&mid=2247489945&idx=1&sn=a2c2104a377529e3cf7692d41fd58ea0 |
| 横戈安全团队 |
HengGeSec |
henggeFish-自动化批量发送钓鱼邮件 |
https://mp.weixin.qq.com/s?__biz=Mzk0NDIwMTgzMQ==&mid=2247484749&idx=1&sn=52ec2bdae3796687cfcad8e4996cfa15 |
| 楼兰学习网络安全 |
LLSecurity |
CodeQL检测SpringBoot应用敏感信息的返回 |
https://mp.weixin.qq.com/s?__biz=Mzg4ODU4ODYzOQ==&mid=2247484971&idx=1&sn=75ad25edfbfe3b29f361bd0d7f555cd0 |
| 情报分析师 |
qingbaofenxishi |
寻找网站真实IP手段大揭秘! |
https://mp.weixin.qq.com/s?__biz=MzA3Mjc1MTkwOA==&mid=2650485293&idx=1&sn=d3887f15110c828264cb86725300cbc2 |
| 奇安信 CERT |
gh_64040028303e |
【安全风险通告】CVE-2021-22017 VMware vCenter Server rhttpproxy 绕过漏洞 |
https://mp.weixin.qq.com/s?__biz=MzU5NDgxODU1MQ==&mid=2247494820&idx=1&sn=215195511954847a1d69b7e45337ed13 |
| 哈拉少安全小队 |
gh_b273ce95df95 |
【反序列化漏洞】__wakeup()魔术方法反序列化绕过 |
https://mp.weixin.qq.com/s?__biz=MzAxNzkyOTgxMw==&mid=2247487413&idx=1&sn=dd19034272c234f5f3df9880905b2722 |
| 利刃信安 |
LRXAEGZ |
【推荐】LSTAR - Aggressor CobaltStrike 综合后渗透插件 |
https://mp.weixin.qq.com/s?__biz=MzU1Mjk3MDY1OA==&mid=2247493214&idx=1&sn=cd65ca2f7f1484cb95574fe0f0a76fb6 |
| 不懂安全的校长 |
sectip |
Bypass_WAF - SQLi and XSS |
https://mp.weixin.qq.com/s?__biz=MzkyMzI3OTY4Mg==&mid=2247484330&idx=1&sn=60cea5a277ed98c6745c4a8dd8642601 |
| Khan安全攻防实验室 |
KhanCJSH |
红队笔记 - 横向移动 |
https://mp.weixin.qq.com/s?__biz=MzAwMjQ2NTQ4Mg==&mid=2247487708&idx=1&sn=78cc22c8176e5d6cfdf54c04f4fc46d7 |
| FreeBuf |
freebuf |
分享学习:模拟网站攻击到提权的全部过程 |
https://mp.weixin.qq.com/s?__biz=MjM5NjA0NjgyMA==&mid=2651138819&idx=1&sn=1af91e4611762f6d13aadc25d3146dcc |
| Docker中文社区 |
dockerchina |
Nginx 缓存机制详解 |
https://mp.weixin.qq.com/s?__biz=MzI1NzI5NDM4Mw==&mid=2247487698&idx=1&sn=9a896574aa14b0ba139d2c268354c996 |
| 3072 |
gh_02e64d74f88d |
样本中的CryptAPI |
https://mp.weixin.qq.com/s?__biz=MzU4OTk0NDMzOA==&mid=2247483998&idx=1&sn=48005303c79e264ac20146b4f3aed605 |
| 赛博英杰 |
GeniusCyberTech |
谭晓生:网络空间安全产业如何助力数字化转型 |
https://mp.weixin.qq.com/s/pFeEBd_kng7KSGMxSeMRcQ |
| 娜璋AI安全之家 |
gh_91f1fe28fc6e |
[当人工智能遇上安全] 5.基于机器学习算法的主机恶意代码识别研究 |
https://mp.weixin.qq.com/s/R3-5kzS2RfjyBsTxY8O0tA |
| 360威胁情报中心 |
CoreSec360 |
疑似APT-C-56透明部落攻击预警 |
https://mp.weixin.qq.com/s/hHBsy_B3jECr2FLk5g9gbA |
| 黑白之道 |
i77169 |
反弹shell的N种姿势 |
https://mp.weixin.qq.com/s?__biz=MzAxMjE3ODU3MQ==&mid=2650523397&idx=2&sn=513d86e5349504d198d3536a4109073d |
| 系统安全运维 |
Taurus-1314147 |
Linux应急响应实战 |
https://mp.weixin.qq.com/s?__biz=Mzk0NjE0NDc5OQ==&mid=2247492082&idx=1&sn=4bdc99a1c1e0d14ff1dfa37ec283be47 |
| 安全行者老霍 |
gh_c2b78e839fd7 |
欧盟网络安全局供应链攻击威胁全景图(下) |
https://mp.weixin.qq.com/s/LI_aErTZNl8zcOuextiSuw |
| 乌雲安全 |
hackctf |
php代码审计总结 |
https://mp.weixin.qq.com/s?__biz=MzAwMjA5OTY5Ng==&mid=2247498962&idx=3&sn=ba448121e4aa8469dea5420c0ec66b08 |
| 穿过丛林 |
gh_f90eac70537b |
漏洞知识图谱构建技术研究 |
https://mp.weixin.qq.com/s/Zfwxcs1oaCqwno6lcIOMLQ |
| FuzzWiki |
gh_fcf21e658324 |
浅谈固件Fuzz |
https://mp.weixin.qq.com/s/IL-wIM8wePZL07l9YJnX_Q |
| 雁行安全团队 |
YX_Security |
Dubbo 源码分析 |
https://mp.weixin.qq.com/s/o1QSOkTTFHft0EWpUh0pDg |
| 腾讯安全应急响应中心 |
tsrc_team |
Web应用组件自动化发现的探索 |
https://mp.weixin.qq.com/s/6xFYQ3D45VpTT3n_qgRing |
| Red0 |
gh_74f47275d982 |
RASP关键技术与相关产品调研 |
https://mp.weixin.qq.com/s/juEPju1Qx7Wdt0akDz9BsA |
| 赛博堡垒 |
gh_099f3e462773 |
VaultFuzzer: 针对Linux内核的状态导向模糊测试方案 |
https://mp.weixin.qq.com/s/ZevJBJjANmBLPCG0RyC3eg |
| 腾讯代码安全检查Xcheck |
gh_177b81103e8d |
Xcheck之PHP代码安全检查 |
https://mp.weixin.qq.com/s?__biz=Mzg2ODQ3ODE1NA==&mid=2247483818&idx=1&sn=f55330a128035ba29cc8f1eca2c56230&chksm=ceaafc0ff9dd7519397f4dc0f710c3901ad7b76436dbc7accbfc1a543c702f49dabefa0d7ea5&token=654851123&lang=zh_CN#rd |
| 网络安全应急技术国家工程实验室 |
NELCERT |
谈谈网络空间“行为测绘” |
https://mp.weixin.qq.com/s/THEdOpSu_bSPWo66sRDyPA |
| 绿盟科技研究通讯 |
nsfocus_research |
攻击推理-安全知识图谱应用的困境思考 |
https://mp.weixin.qq.com/s/DOfrD7SGpoXP--zZPzf5bg |
| 数世咨询 |
dwconcn |
网络空间资产安全管理实践与创新 |
https://mp.weixin.qq.com/s/3NWI-_qJZfTuqvFl3d2SAQ |
| 亿人安全 |
Yr-Sec |
内网渗透测试:DCSync 攻击技术的利用 |
https://mp.weixin.qq.com/s?__biz=Mzk0MTIzNTgzMQ==&mid=2247485912&idx=1&sn=2cbaf2d8eca710edb5e39a4031c1d9c6 |
| 互联网后端架构 |
fullstack888 |
如何高效迅速的进行CodeReview |
https://mp.weixin.qq.com/s/nlDSYvR2SyKhtl4fOPt2Hg |
| NGINX开源社区 |
gh_0d2551f1bdb6 |
NGINX速率限制原理及源码分析 |
https://mp.weixin.qq.com/s/hj7DPoFevmRPdgMY9orilg |
| 威胁棱镜 |
THREAT_PRISM |
IoT 恶意软件进化谱系研究 |
https://mp.weixin.qq.com/s/xXYFcVOXA6lZfhign0BJlg |
| ChaMd5安全团队 |
chamd5sec |
Miara的延续--gafgyt病毒分析 |
https://mp.weixin.qq.com/s/JYBdhxbt0mqU3wIqFFWdhQ |
| 黑哥说安全 |
gh_67cfd5e45750 |
谈谈网络空间“行为测绘” |
https://mp.weixin.qq.com/s/fQatA5iyewqRBMWtpVjsRA |
| 锦行信息安全 |
jeeseensec |
技术分享 , DLL注入之全局钩子注入 |
https://mp.weixin.qq.com/s/2CZA9aRr9nsawMkxHQrupg |
| 莫哥谈安全 |
gh_247dfbdf3d43 |
漫谈企业安全运营能力建设 |
https://mp.weixin.qq.com/s/dBAV_4iGw8rTU5Y3SI4ocA |
| 安全营销喵喵站 |
Z1-Businessweek |
Gartner:2021年SIEM(安全信息与事件管理)市场分析 |
https://mp.weixin.qq.com/s/2hiU8ko3N3duW0sI9JdNfA |
| 安全客 |
anquanbobao |
【技术分享】如何高效地捡漏反序列化利用链? |
https://mp.weixin.qq.com/s/th9hDuMK8LgrkesgPvEDHQ |
| 一个人的安全笔记 |
xjiek2015 |
[HTB] Haystack Writeup |
https://mp.weixin.qq.com/s/HFh8pMRtZ-fm_-0lMoUqvw |
| 安全学术圈 |
secquan |
小心你信任的人:跨域通信中的安全陷阱 |
https://mp.weixin.qq.com/s/ErjUg177-jGR9UQjyZaEoA |
| 网安思考 |
gh_e53abd003964 |
【专题研究第018期】DARPA近年网络空间安全领域主要项目梳理 |
https://mp.weixin.qq.com/s/CwXqkHDSFK6XMFtvOpnsjw |
| 机器学习研究组订阅 |
gh_7ce29bea153b |
自动检索、修复Python代码bug,微软推出DeepDebug |
https://mp.weixin.qq.com/s/jfgrIRQSb_gPwvYGs8b_Pw |
| 安全界 |
feei_cn |
GitHub Pull Request业务逻辑风险 |
https://mp.weixin.qq.com/s/Fo0OhNb-MP-GqKM-ASCXsg |
| 奇安信威胁情报中心 |
gh_166784eae33e |
Operation(Thủy Tinh)OceanStorm:隐匿在深海巨渊下的邪恶莲花 |
https://mp.weixin.qq.com/s/dGW0FrbZZ5UA6KuuZB8J_g |