ARM version of the two DSV parts (Injector and Syncer) for native K8s integration.
To make the DSV Injector and DSV Syncher work some work has to be performed.
The file that holds the DSV credentials (Client_Id, Client_Secure_Id, tenant name and possible Top Level Domain (TLD)) needs to be created. An example is shown below:
{
"default": {
"credentials": {
"clientId": "<CLIENT_ID>",
"clientSecret": "<CLIENT_SECRET_ID"
},
"tenant": "<TENANT>"
}
}{
"default": {
"credentials": {
"clientId": "<CLIENT_ID>",
"clientSecret": "<CLIENT_SECRET_ID"
},
"tenant": "<TENANT>",
"tld":"<TLD DOMAIN>"
}
}The below variables can be used to change the namespace, the json file that holds the credentials for DSV, what image to use and the version (IMAGE_TAG) of the image that needs to be pulled. The last variable is needed to start the two parts as the original container image is pointing to /app/ to start the parts.
NAMESPACE='testing'
CREDENTIALS_JSON_FILE='dsv_creds.json'
IMAGE_REPOSITORY='docker.io/wessenstam/dsv'
IMAGE_TAG='latest'
IMAGE_ENTRYPOINT='/usr/bin/'For the installation Helm is being used. This is a pre-requisite to install the DVS K8s components.
Run the following command to install and run the DSV Injector. It will use the variables set earlier.
helm install --namespace $NAMESPACE --create-namespace --set-file credentialsJson=${CREDENTIALS_JSON_FILE} --set image.repository=${IMAGE_REPOSITORY} --set image.tag=${IMAGE_TAG} --set image.entrypoint=${IMAGE_ENTRYPOINT}'dsv-injector' dsv-injector ./charts/dsv-injectorAfter the installation of the DSV Injector and a successful running of the Pod, run the next helm command to install the DSV Injector:
helm install --namespace $NAMESPACE --create-namespace --set image.repository=${IMAGE_REPOSITORY} --set image.tag=${IMAGE_TAG} --set image.entrypoint=${IMAGE_ENTRYPOINT}'dsv-syncer' dsv-syncer ./charts/dsv-syncerAfter the installation, the following will be available in k8s:
-
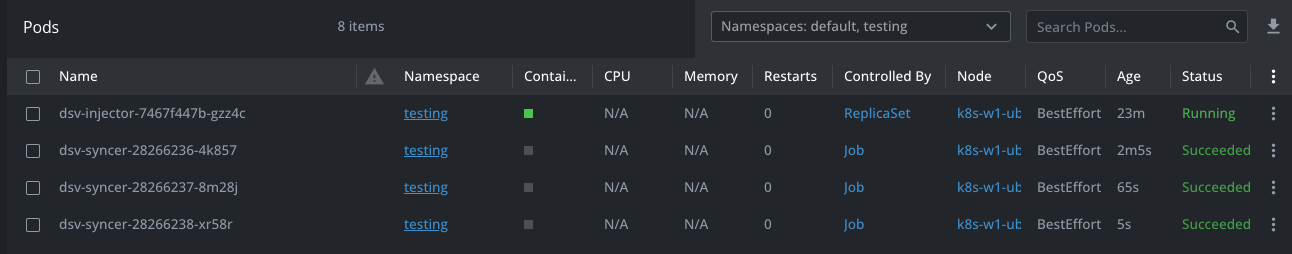
Pods
A pod named dsv-injector-xxxxxxxxx-xxxx will be seen and in a running state. Pods with the name dsv-syncer-xxxxxxxx-xxxxx with a state succeeded
-
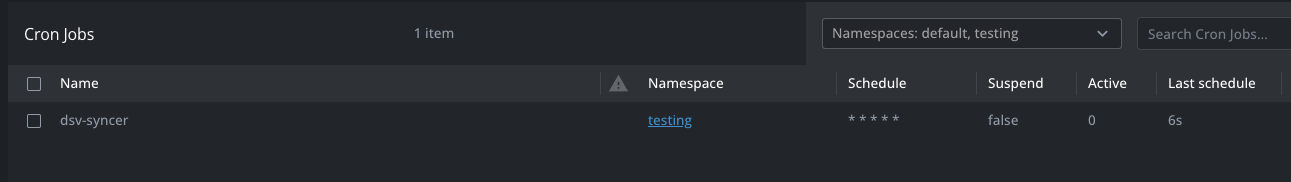
Cron Job
A Cron Job will be added to k8s that is used for the dsv-syncer. This job will run every minute and syncs the data from DSV into k8s for defined secrets.
-
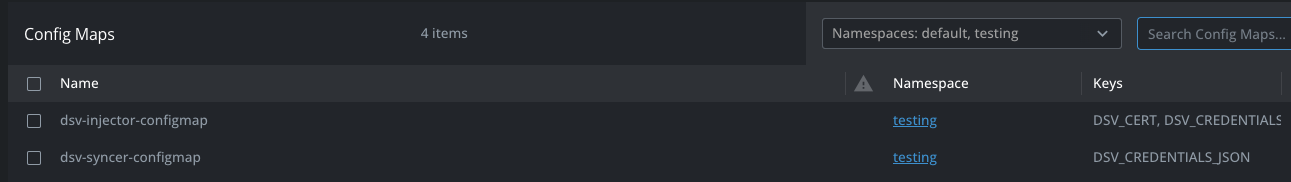
Config Maps
Two configmaps should be shown. They hold the information needed by the two components.
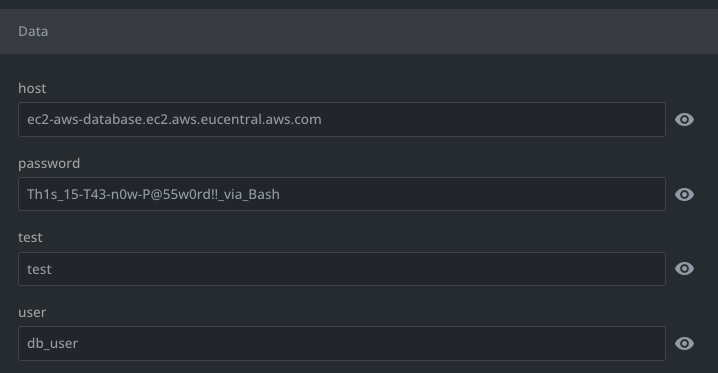
Now that the DSV integration is configured we need to create a kubernetes YAML file to start the synchronisation of the secret. The following YAML file can be used to pull/sync a secret called aws:ec2-database. The secret in k8s is named secret-aws-ec2-database:
---
apiVersion: v1
kind: Secret
metadata:
name: secret-aws-ec2-database
annotations:
dsv.delinea.com/credentials: default
dsv.delinea.com/set-secret: aws:ec2-database
type: Opaque
data:
host:
password:
user:This will pull/sync the secret with respect to the field
- host
- password
- user
If the field in the YAML file does not exist, it will be delete from the secret. This way it is possible to avoid empty fields. Any fields that are not mentioned in the YAML file, will be added to the secret.
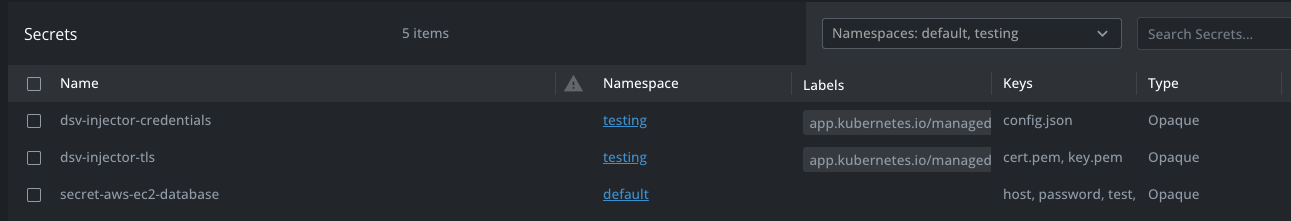
After the secret has been defined using the YAML file, there will be a k8s secret named after the YAML file, besides two other secrets which are defined during the installation with Helm.
The data of the secret must match the secret from as available in DSV.
For the screenshots Lens is used as the k8s management tool.
The information is put together using the files of Delinea DSV which can be found at https://github.com/DelineaXPM/dsv-k8s.
Information on Kubernetes can be found at https://kubernetes.io/docs/reference/generated/kubectl/kubectl-commands.