08/22/2022
Reaper Farm is a yield aggregator on fantom. their V2 vaults were hacked on 8/2.
There were a number of implementations of the vaults with damages totalling $1.7mm, but the exploit was the same on all of them, so let's just focus on one — a DAI vault hacked for over $400k.
- vault: 0x77dc33dC0278d21398cb9b16CbFf99c1B712a87A
- fantom dai: 0x8D11eC38a3EB5E956B052f67Da8Bdc9bef8Abf3E
Review the code in this repo, find the exploit, and recover > $400k.
-
fork this repo and clone it locally.
-
update the .env file with an environment variable for FANTOM_RPC (already preset to the public RPC endpoint, which should work fine, in which case you can skip this).
-
review the code in the
src/folder, which contains all the code at the time of the hack. you can explore the state of the contract before the hack using block 44000000. ex:cast call --rpc-url ${FANTOM_RPC} --block 44000000 0x77dc33dC0278d21398cb9b16CbFf99c1B712a87A "totalAssets()" | cast 2d -
when you find an exploit, code it up in
ReaperHack.t.sol. the test will pass if you succeed. -
post on twitter for bragging rights and tag @unhackedctf. no cheating.
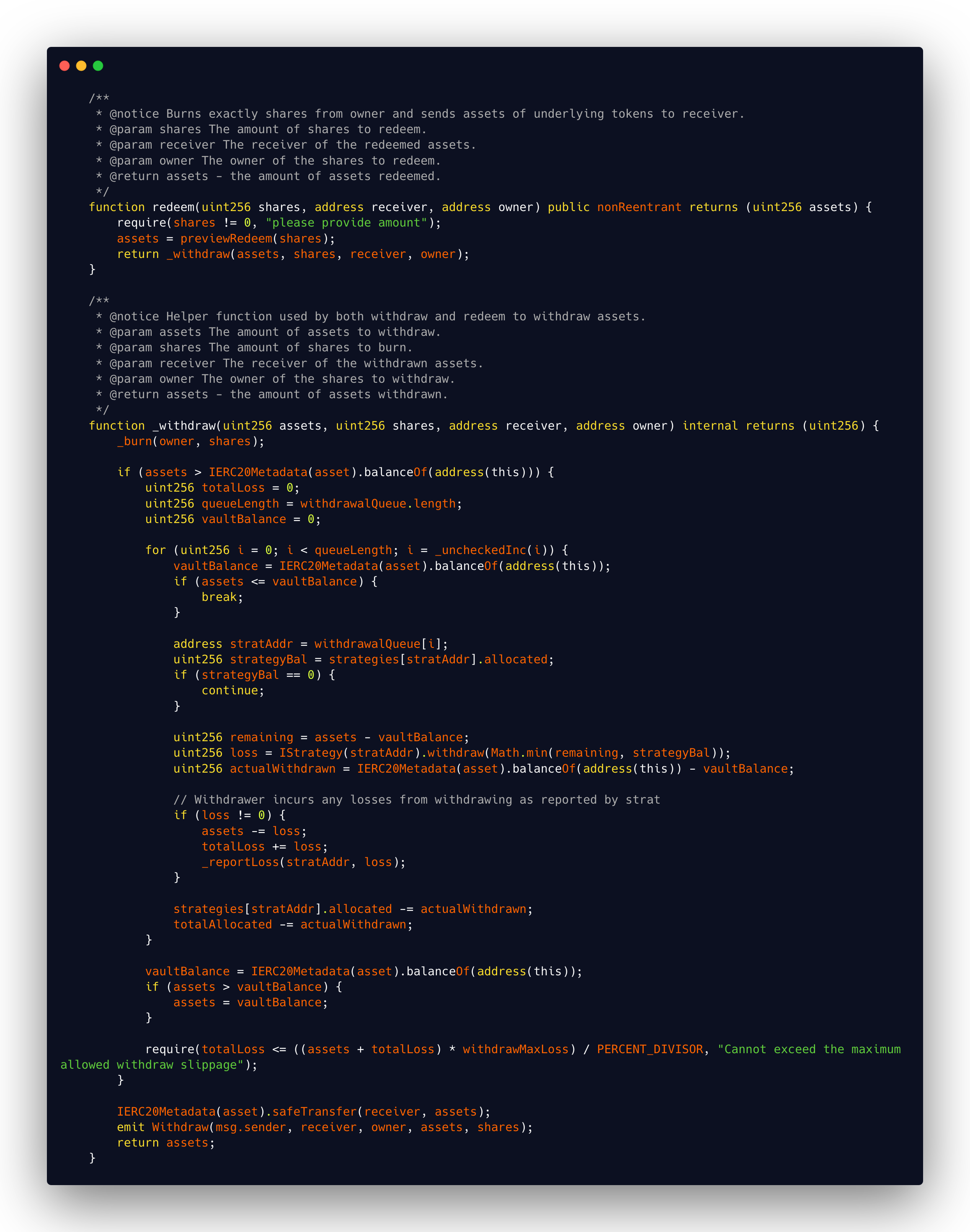
The crux of the exploit lies in the ReaperVaultV2 redeem() function. Neither in redeem nor the internal _withdraw function is there a check that the specified owner is equal to the msg.sender. This means anyone can redeem anyone else's vault shares for the underlying token and send the underlying token to an arbitrary recipient address!
Source:
src/ReaperVaultV2.sol. Created using carbon.now.sh
For new weekly challenges and solutions, subscribe to the unhacked newsletter.