Traefik plugin to proxy requests to owasp/modsecurity-crs:apache
Demo with WAF intercepting relative access in query param.
- docker-compose up
- Go to http://localhost:8000/website, the request is received without warnings
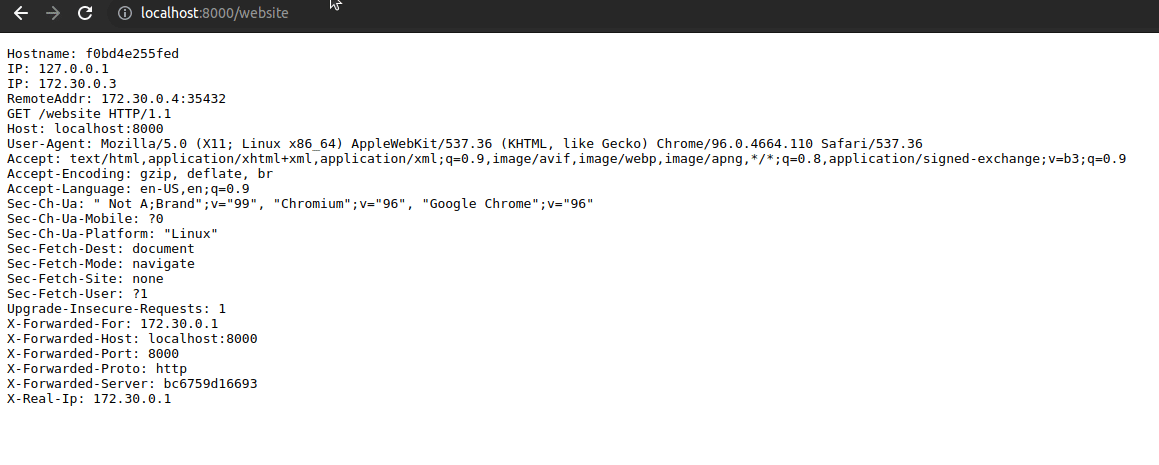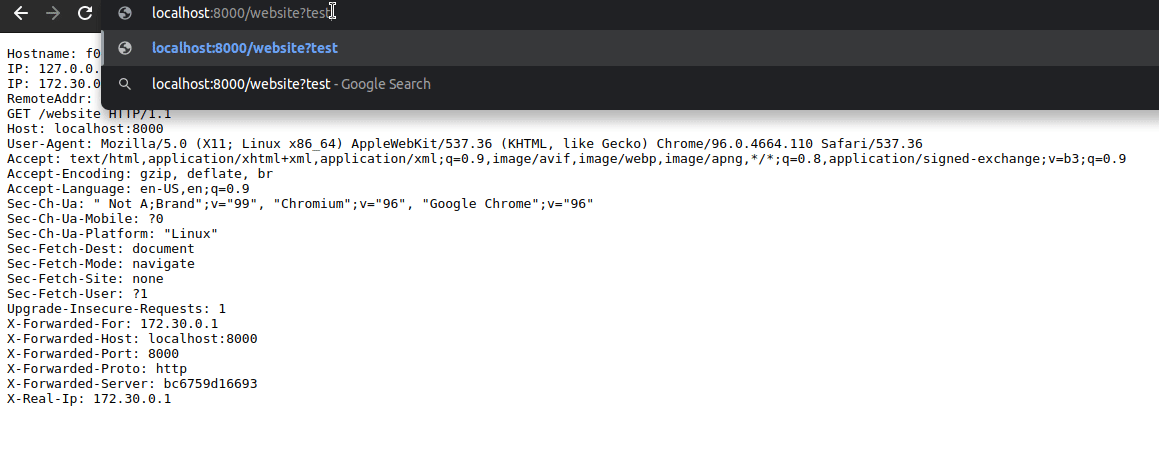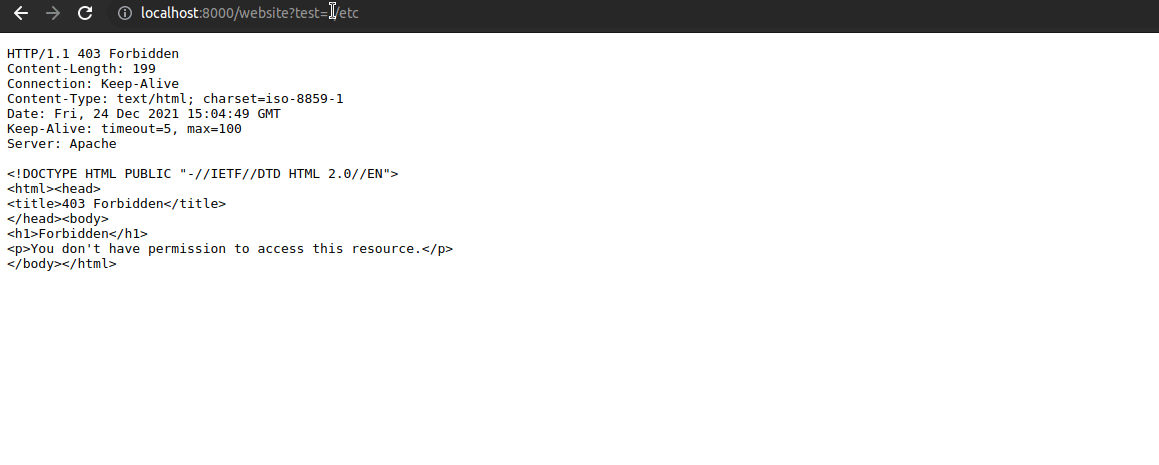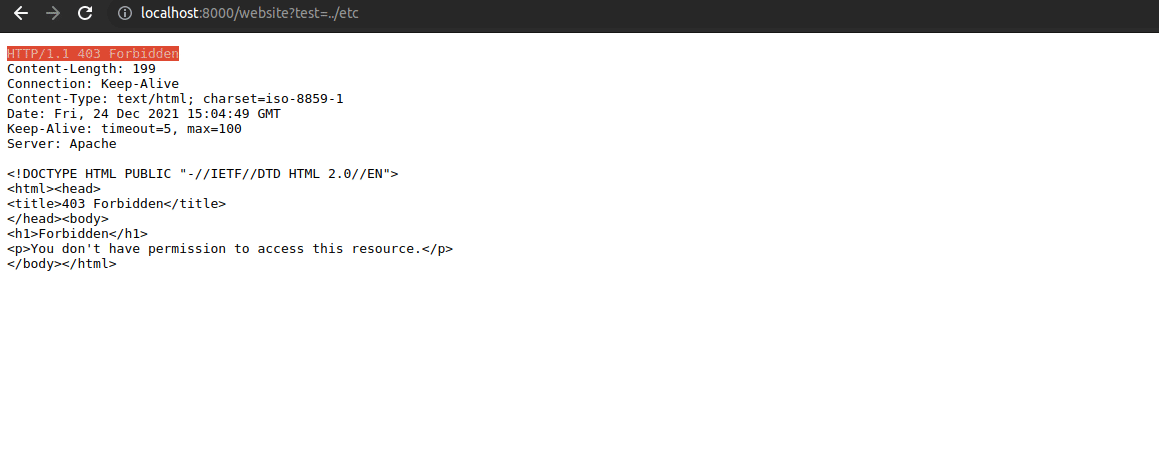
- Go to http://localhost:8000/website?test=../etc, the request is intercepted and returned with 403 Forbidden by owasp/modsecurity
This is a very simple plugin that proxies the query to the owasp/modsecurity apache container.
The plugin checks that the response from the waf container hasn't an http code > 400 before forwarding the request to the real service.
If it is > 400, then the error page is returned instead.
The dummy service is created so the waf container forward the request to a service and respond with 200 OK all the time.
This plugin supports these configuration:
modSecurityUrl: (mandatory) it's the URL for the owasp/modsecurity container.maxBodySize: (optional) it's the maximum limit for requests body size. Requests exceeding this value will be rejected usingHTTP 413 Request Entity Too Large. The default value for this parameter is 10MB. Zero means "use default value".
Note: body of every request will be buffered in memory while the request is in-flight (i.e.: during the security check and during the request processing by traefik and the backend), so you may want to tune maxBodySize depending on how much RAM you have.
docker-compose -f docker-compose.local.yml up to load the local plugin