English | 中文
TerraformGoat is HuoCorp research lab's "Vulnerable by Design" multi cloud deployment tool.
Currently supported cloud vendors include Alibaba Cloud, Tencent Cloud, Huawei Cloud, Amazon Web Services, Google Cloud Platform, Microsoft Azure.
| ID | Cloud Service Company | Types Of Cloud Services | Vulnerable Environment |
|---|---|---|---|
| 1 | Tencent Cloud | Object Storage | Bucket ACL Writable |
| 2 | Tencent Cloud | Object Storage | Unrestricted File Upload |
| 3 | Tencent Cloud | Object Storage | Bucket Object Traversal |
| 4 | Tencent Cloud | Elastic Computing Service | CVM SSRF |
| 5 | Alibaba Cloud | Object Storage | Bucket HTTP Enable |
| 6 | Alibaba Cloud | Object Storage | Object ACL Writable |
| 7 | Alibaba Cloud | Object Storage | Object ACL Readable |
| 8 | Alibaba Cloud | Object Storage | Special Bucket Policy |
| 9 | Alibaba Cloud | Object Storage | Bucket Public Access |
| 10 | Alibaba Cloud | Object Storage | Object Public Access |
| 11 | Alibaba Cloud | Object Storage | Bucket Logging Disable |
| 12 | Alibaba Cloud | Object Storage | Bucket Policy Readable |
| 13 | Alibaba Cloud | Object Storage | Bucket Object Traversal |
| 14 | Alibaba Cloud | Object Storage | Unrestricted File Upload |
| 15 | Alibaba Cloud | Elastic Computing Service | ECS SSRF |
| 16 | Huawei Cloud | Object Storage | Object ACL Writable |
| 17 | Huawei Cloud | Object Storage | Special Bucket Policy |
| 18 | Huawei Cloud | Object Storage | Unrestricted File Upload |
| 19 | Huawei Cloud | Object Storage | Bucket Object Traversal |
| 20 | Huawei Cloud | Elastic Computing Service | ECS SSRF |
| 21 | Amazon Web Services | Object Storage | Object ACL Writable |
| 22 | Amazon Web Services | Object Storage | Bucket ACL Writable |
| 23 | Amazon Web Services | Object Storage | Special Bucket Policy |
| 24 | Amazon Web Services | Object Storage | Bucket Object Traversal |
| 25 | Amazon Web Services | Object Storage | Unrestricted File Upload |
| 26 | Amazon Web Services | Elastic Computing Service | EC2 SSRF |
| 27 | Amazon Web Services | Elastic Computing Service | Console Takeover |
| 28 | Amazon Web Services | Identity and Access Management | IAM Privilege Escalation |
| 29 | Google Cloud Platform | Object Storage | Object ACL Writable |
| 30 | Google Cloud Platform | Object Storage | Bucket ACL Writable |
| 31 | Google Cloud Platform | Object Storage | Bucket Object Traversal |
| 32 | Google Cloud Platform | Object Storage | Unrestricted File Upload |
| 33 | Google Cloud Platform | Elastic Computing Service | VM Command Execution |
| 34 | Microsoft Azure | Object Storage | Blob Public Access |
| 35 | Microsoft Azure | Object Storage | Container Blob Traversal |
| 36 | Microsoft Azure | Elastic Computing Service | VM Command Execution |
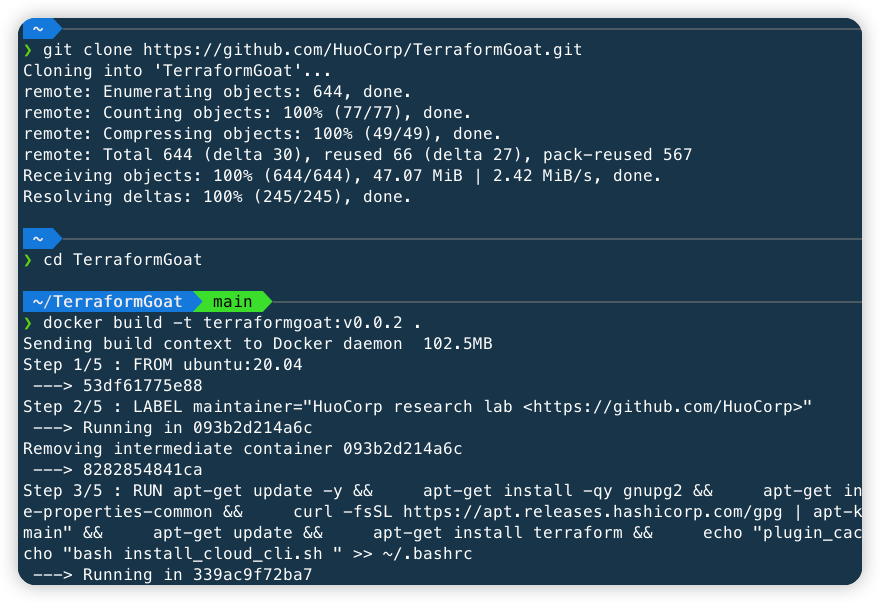
TerraformGoat is built using Dockerfile, so you need to install the Docker environment first. For the Docker installation method, please refer to: https://docs.docker.com/get-docker/
git clone https://github.com/HuoCorp/TerraformGoat.git
cd TerraformGoat
docker build -t terraformgoat:v0.0.3 .After docker build is complete, start and enter the container
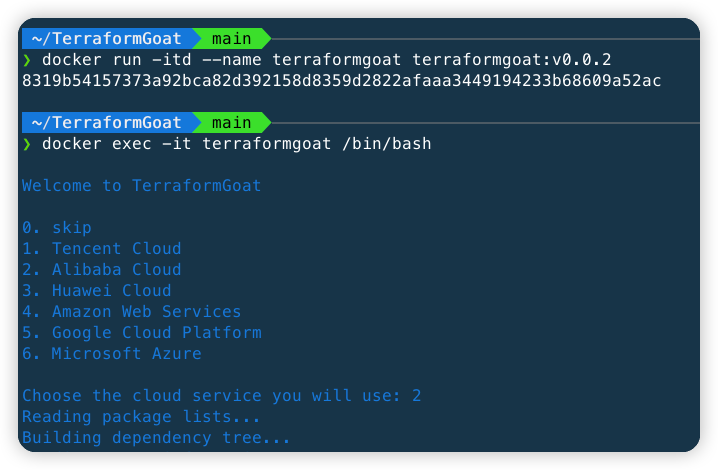
docker run -itd --name terraformgoat terraformgoat:v0.0.3
docker exec -it terraformgoat /bin/bashWhen entering the container, you need to select the cloud service to run
After selecting the cloud service you want to use, the relevant dependencies will be installed. After the relevant dependencies are installed, you can use TerraformGoat.
Using the build of the Alibaba Cloud ECS SSRF vulnerability scenario as a demo:
docker stop terraformgoat
docker rm terraformgoat
docker rmi terraformgoat:v0.0.3- The README of each vulnerable environment is executed within the TerraformGoat container environment, so the TerraformGoat container environment needs to be deployed first.
- Due to the horizontal risk of intranet horizontal on the cloud in some scenarios, it is strongly recommended that users use their own test accounts to configure the scenarios, avoid using the cloud account of the production environment, and install TerraformGoat using Dockerfile to isolate the user's local cloud vendor token and the test account token.
- TerraformGoat is used for educational purposes only, It is not allowed to use it for illegal and criminal purposes, any consequences arising from TerraformGoat are the responsibility of the person using it, and not the HuoCorp organization.
Contributions are welcomed and greatly appreciated. Further reading — CONTRIBUTING.md for details on contribution workflow.
TerraformGoat is under the Apache 2.0 license. See the LICENSE file for details.