This project is a reference implemenation of AWS ioT device SDK for Embedded C running on Azure Sphere MT3620 MCU. It integrates multiple official demos include MQTT, HTTP and AWS IoT Shadow service.
Azure Sphere MCU come with a hardware Root-of-Trust and device certificate lifecycle management service (AS3) to facilitate secure connection to any cloud. This project is also a complete demo of secure connection to a 3rd party IoT cloud.
More specifically, AWS IoT Core support device Just-in-time-registeration, aka JITR mechanism. User can have a zero-touch provisioning expereience with high security and trustworthy when connect Azure Sphere MT3620 MCU to AWS IoT core
- Azure Sphere RDB from SeeedStudio or Azure Sphere EVK from Avnet
- Minimum Azure Sphere SDK is 22.02.
- Visual Studio Code or Visual Studio 2019 installed on Windows 10 PC.
- Microsoft Account to be used with Azure Sphere Developer Utility
- AWS Account to host your services
- AWS CLI and boto3 are installed on your PC
-
Follow the guide of Get started with a development kit to setup your hardware and claim it your tenant.
-
Setup WiFi for Azure Sphere and ensure it get connected to internet.
-
Put your device into development mode by
azsphere device enable-development -
Retrieve your Azure Sphere tenant ID and record for later use
azsphere tenant show-selected
-
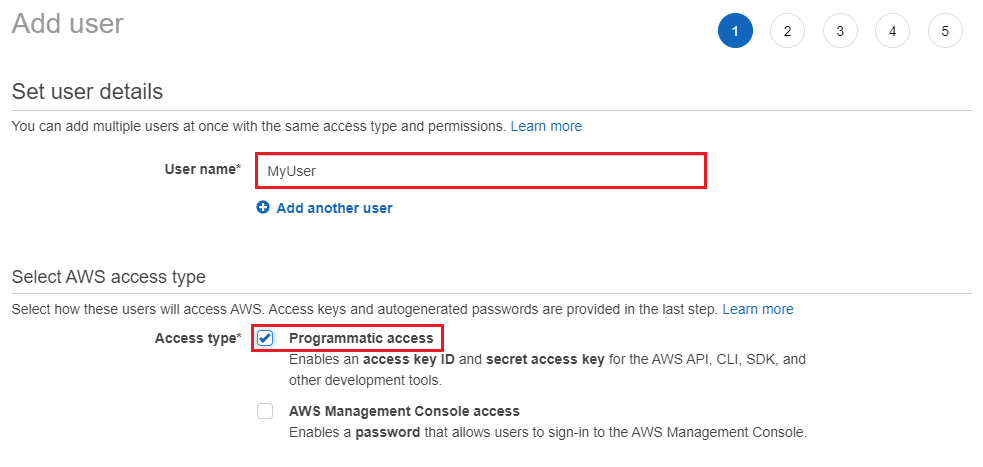
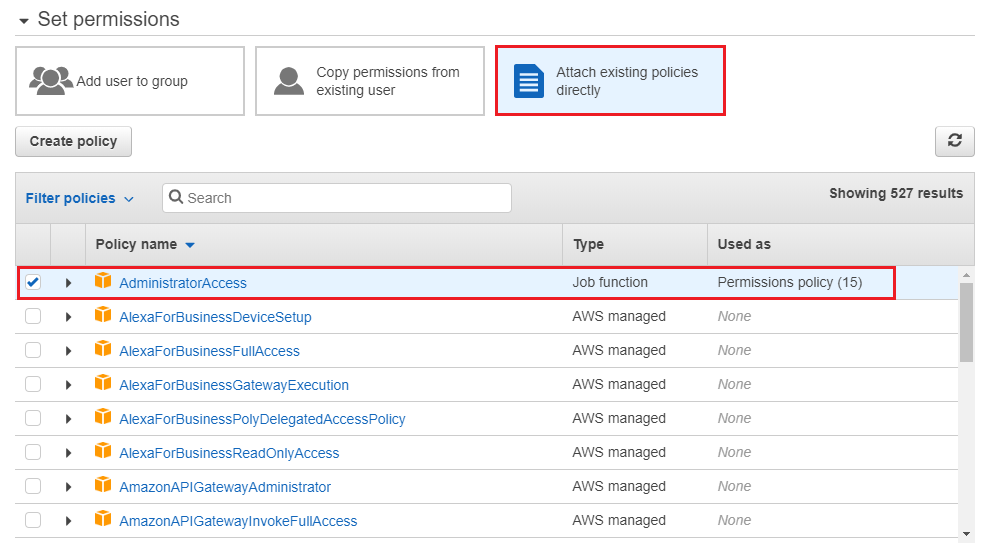
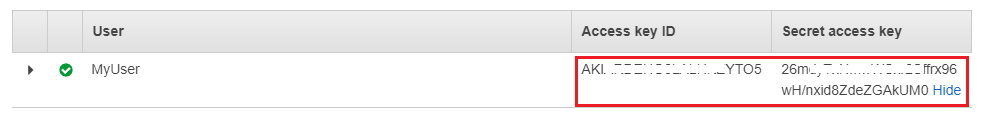
Login AWS and go to IAM service to add a Programmatic access user. Assign AdministratorAccess permission to this new user and record access id id and key
-
Open Windows command prompt, use AWS CLI to configure your credentials file by
aws configureYou will be asked to provide access id and access key created in the previous step, and you also provide the default region code, refer to this page to get the full list of supported region. E.g.
ap-northeast-1is for Asia Pacific (Tokyo).Please note all resources in this demo will be depolyed to this default region.
-
All resources required on AWS IoT will be created by the preconfigure.py script using boto3 SDK. Go to the root of this project and run the script by
python script/preconfigure.pyThe script need 30 seconds to finish. The resources configured on AWS are:
- Azure Sphere Tenant CA certificate
- AWS IoT Policy
- IAM role with built-in polices assuming by Lambda function
- JITR Lambda function with proper permission (function and its dependencies can be found here)
- AWS IoT Rule to monitor certificate register event and trigger lambda function
-
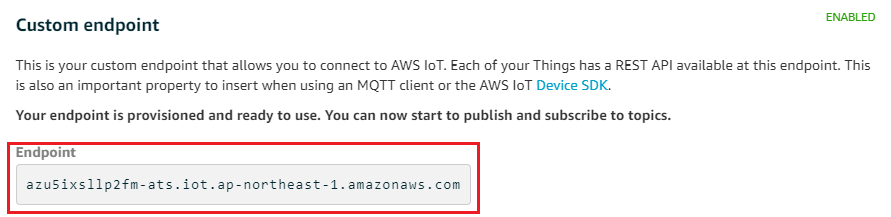
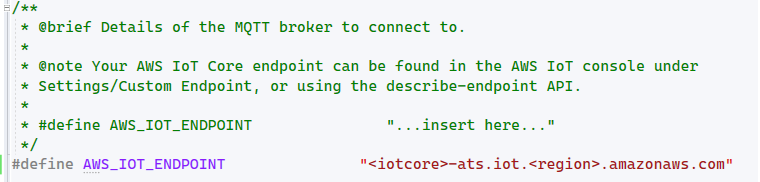
Go to AWS IoT console Setting page, record the custom endpoint URL
-
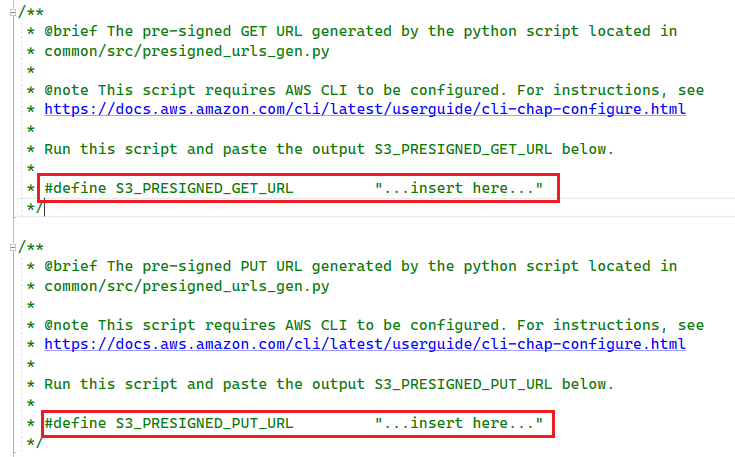
To test with HTTP upload and download use case, user must create your own bucket and generate presigned URL for authorized resource access.
-
Start Visual Studio 2019
-
From the File menu, select Open > CMake... and navigate to the folder that contains the sample.
-
Select the file CMakeLists.txt and then click Open to load the project.
-
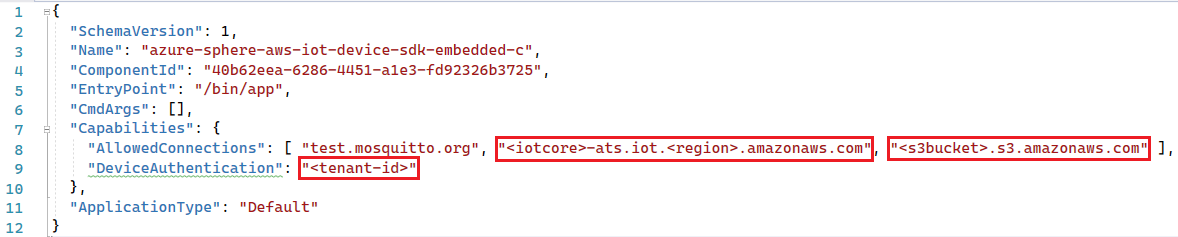
Go to app_manifest.json file, replace
<iotcore>-ats.iot.<region>.amazonaws.com,<s3bucket>.s3.amazonaws.comand<tenant-id>string with correct value record in previous steps -
Go to .\azure-sphere-aws-iot-device-sdk-embedded-c\aws-iot-device-sdk-embedded-C\demos\demo_config.h, modify following macros.
-
In Solution Explorer, right-click the CMakeLists.txt file, and select Generate Cache for azure-sphere-aws-iot-device-sdk-embedded-c. This step performs the cmake build process to generate the native ninja build files.
-
In Solution Explorer, right-click the CMakeLists.txt file, and select Build to build the project and generate .imagepackage target.
-
Double click CMakeLists.txt file and press F5 to start the application with debugging. The default code has enabled all 5 subroutines.
-
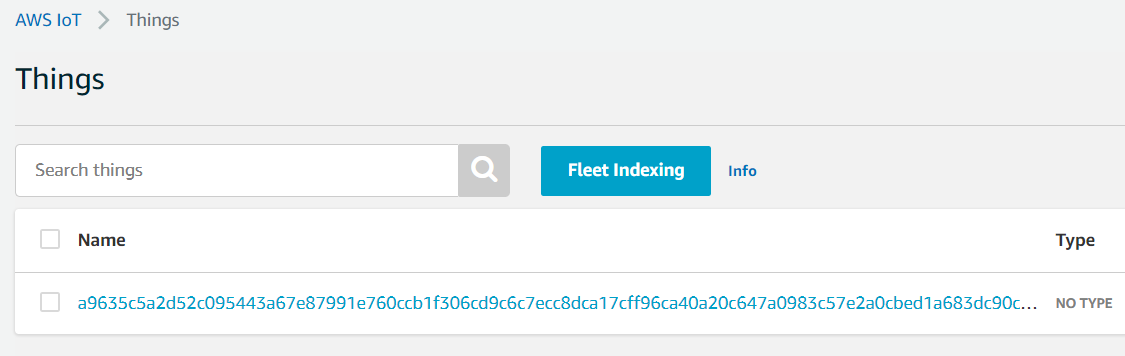
Go to AWS IoT console Manage/Things page, your Azure Sphere device will be listed, the display name is azure sphere device id.
-
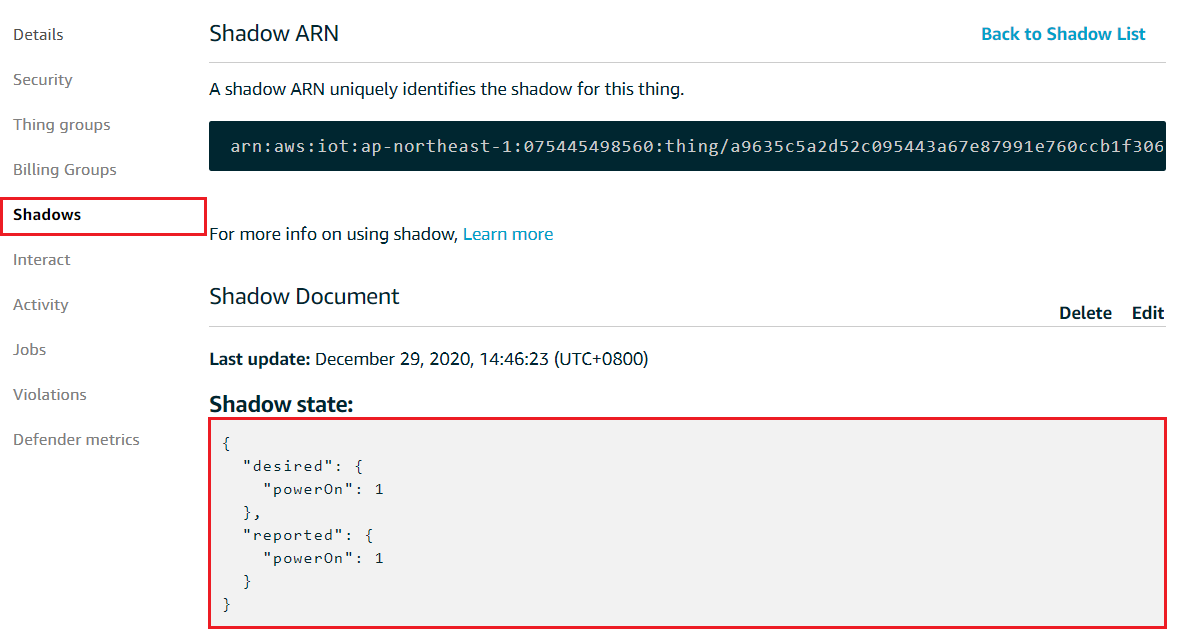
click the thing to check the details, you can see the device shadow is created with some properties.
-
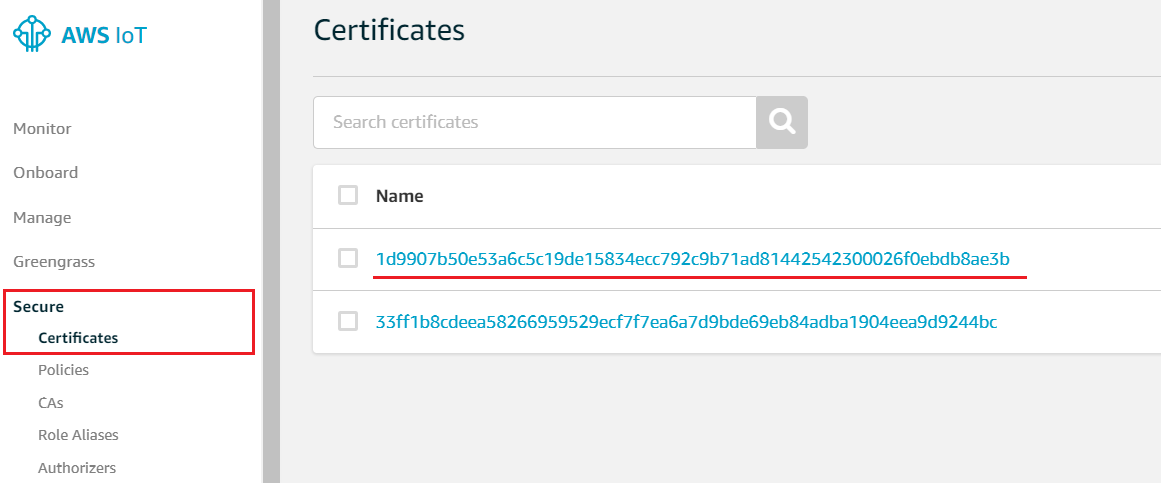
Go to AWS IoT console Secure/Certificates page, you will see the device certificate in use is registered. Try to reboot your device, afer a while you will observe the device certificate id is changed but still linking to your device in the thing registry.
-
Go to S3 console, open the right bucket and check the uploaded object content: Hello World!
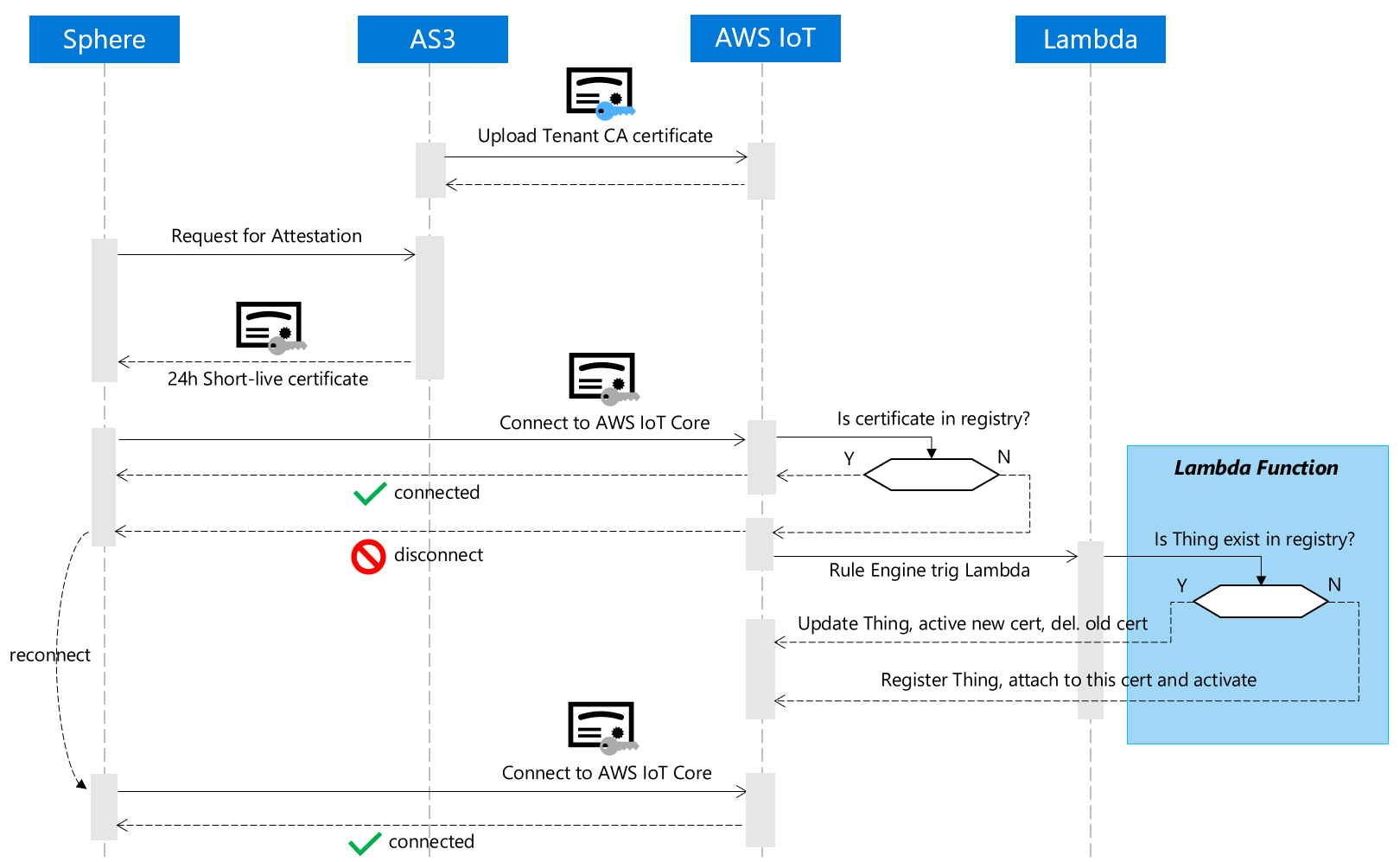
Here is a diagram dipict the overall workflow