An App intended for fuzzing the Binder interface and System Services of Android. You can use this Project in order to find bugs and exploits inside the Binder interface or System Services.
Watch this Youtube Video for a quick introduction
Or this youku video (for Chinese watchers): https://v.youku.com/v_show/id_XNDcwMjk1NzUwMA==.html
Binder fuzzy can be used via the python client or via the App itself. Choose one for your needs.
Read the full documentation here
- Python 3.0
- Ubuntu Linux 18.04
- Download tip here
- unzip release.zip
- cd bin/
python3 binderFuzzy.py --fuzzy-apk binderfuzzy-release.apk --script startActivity.bf{
"fields_ordered" : [
{
"clazz": "android.app.ActivityTaskManager",
"field": "IActivityTaskManagerSingleton"
},
{
"clazz": "android.util.Singleton",
"field": "mInstance"
}
],
"call" : {
"clazz": "android.app.IActivityTaskManager",
"method": "startActivity(",
"params":[
"auto",
"packageNames",
"launchIntents",
"packageNames",
"auto",
"packageNames",
"auto",
"auto",
"null",
"auto"
]
}
}- Android 6 or greater
- Download APK here
- Enable unknown source during installation
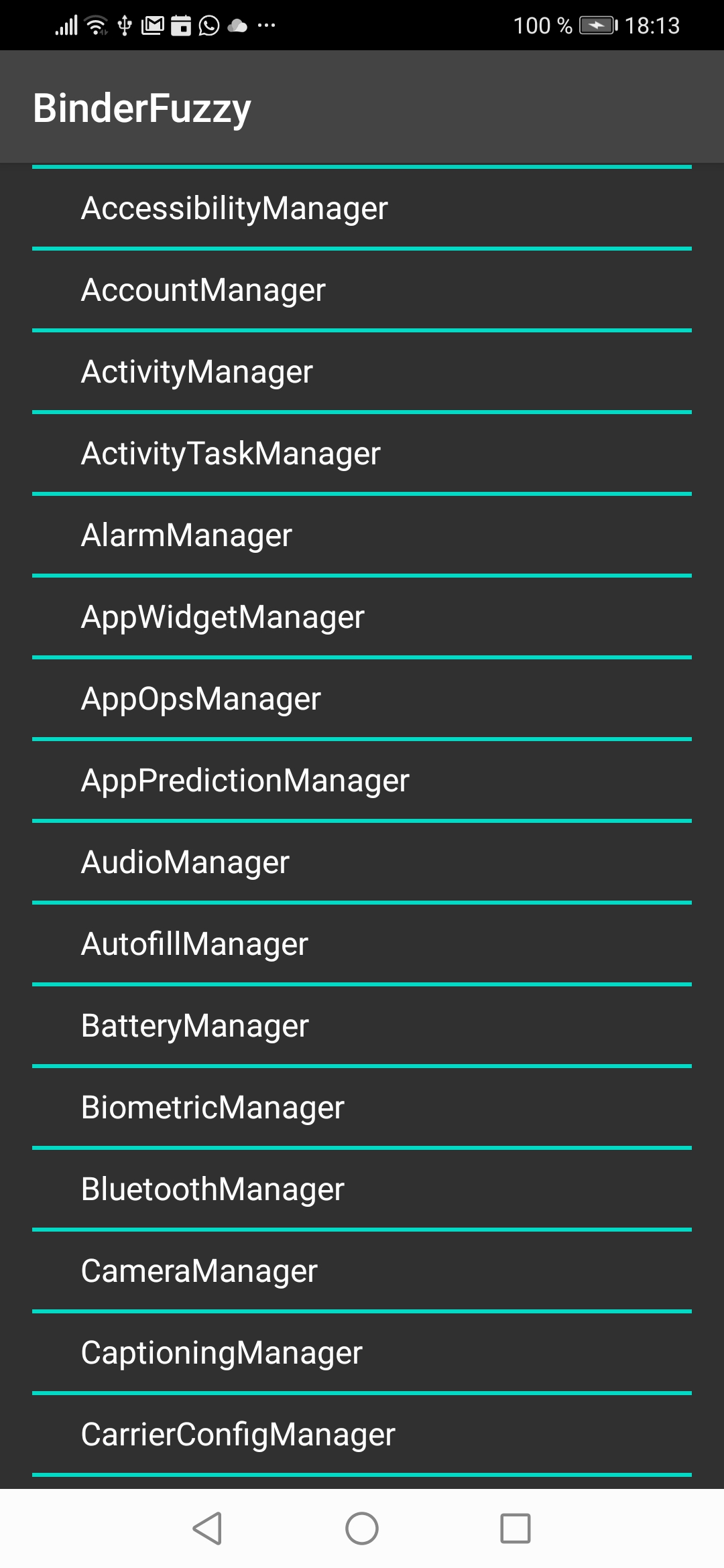
First step is to select a System Service we're going to fuzz. After a click on the "NEW" button the list of available Services appears and you can choose one.
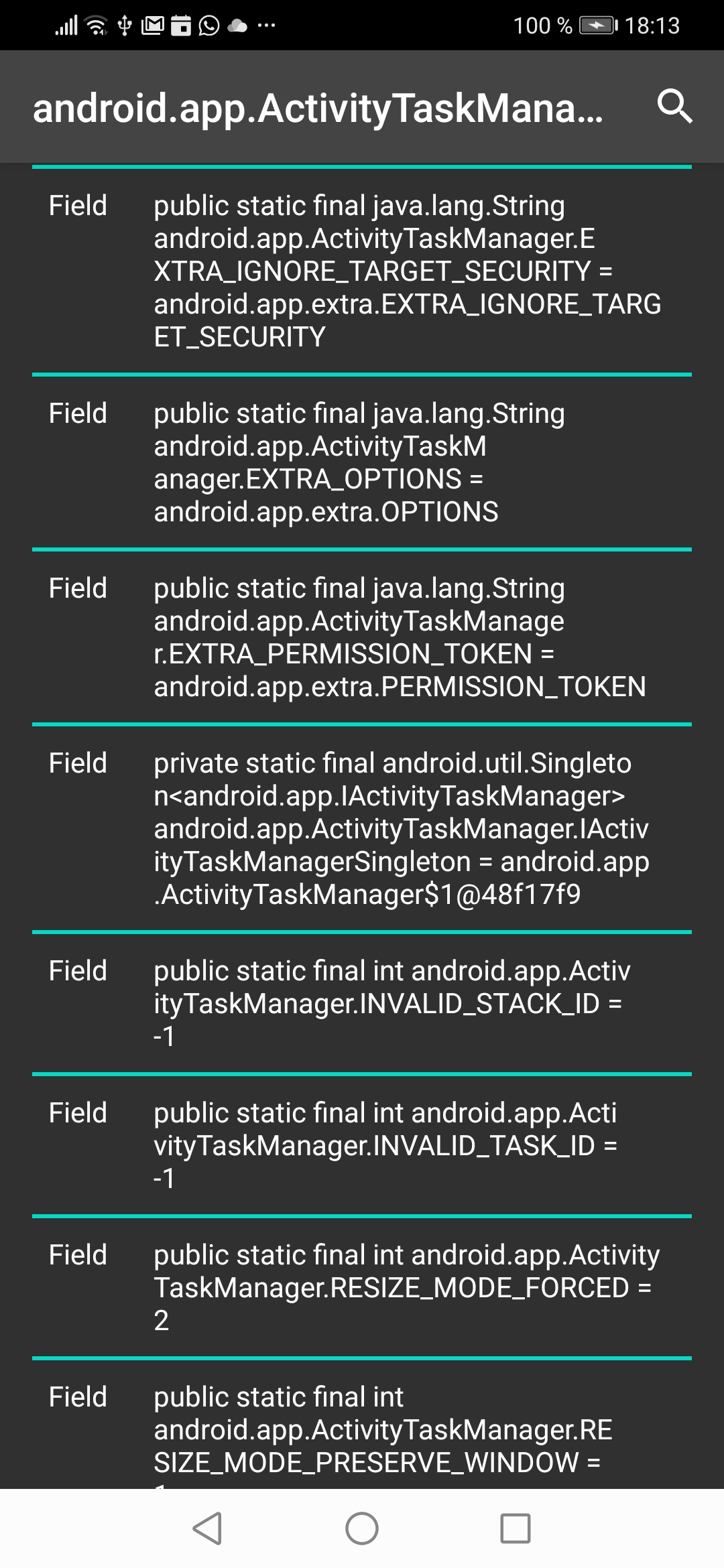
The next screen lists all members: functions and fields.
=> If you click on a field the browser will open the object in a new Window.
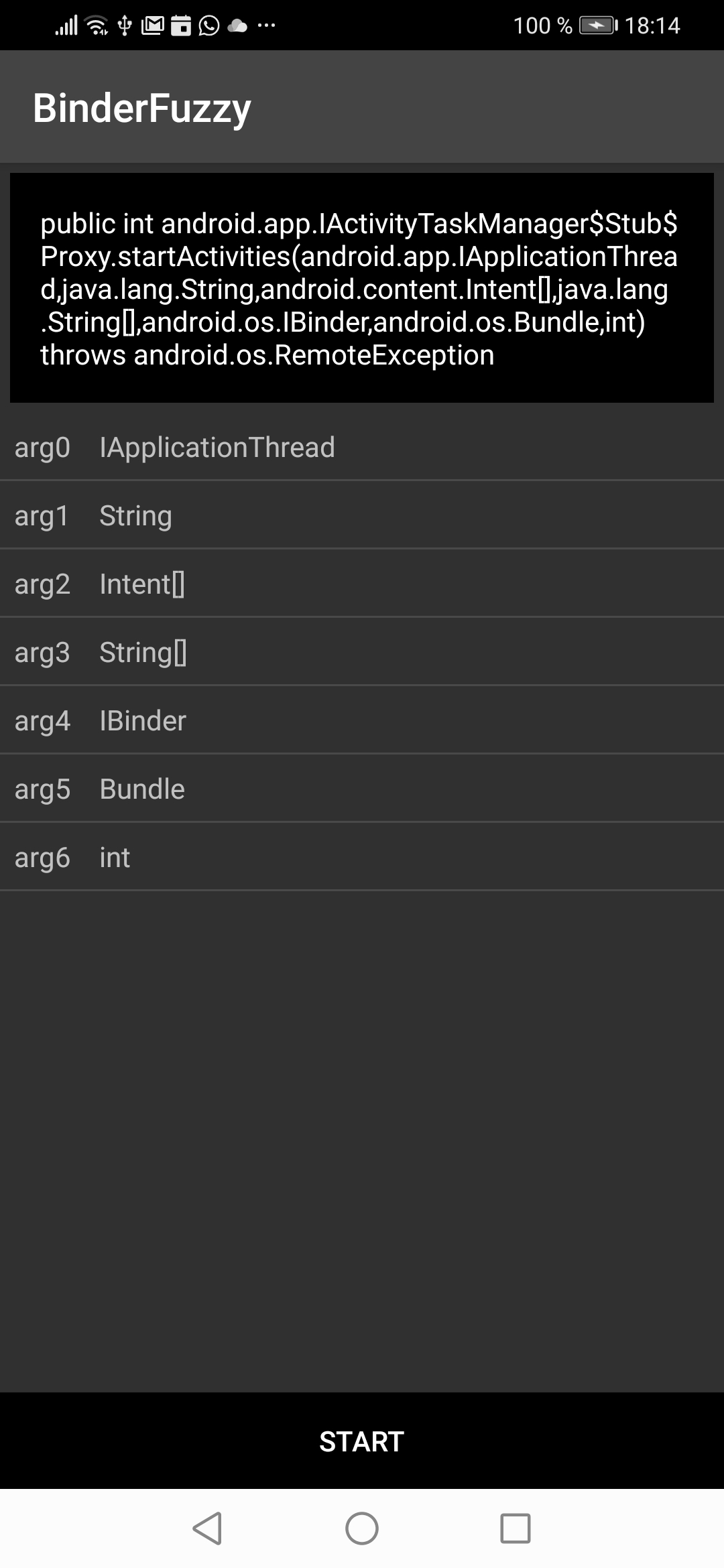
=> If you click on a method the browser forwards this to the FuzzCreator.
Now you have to configure the parameters of the call. Some parameters have special options like integers, strings and intents. You can open a feature request if you need more features here. However, you must click on each parameter and configure how the fuzzer shall gather the values for the call.
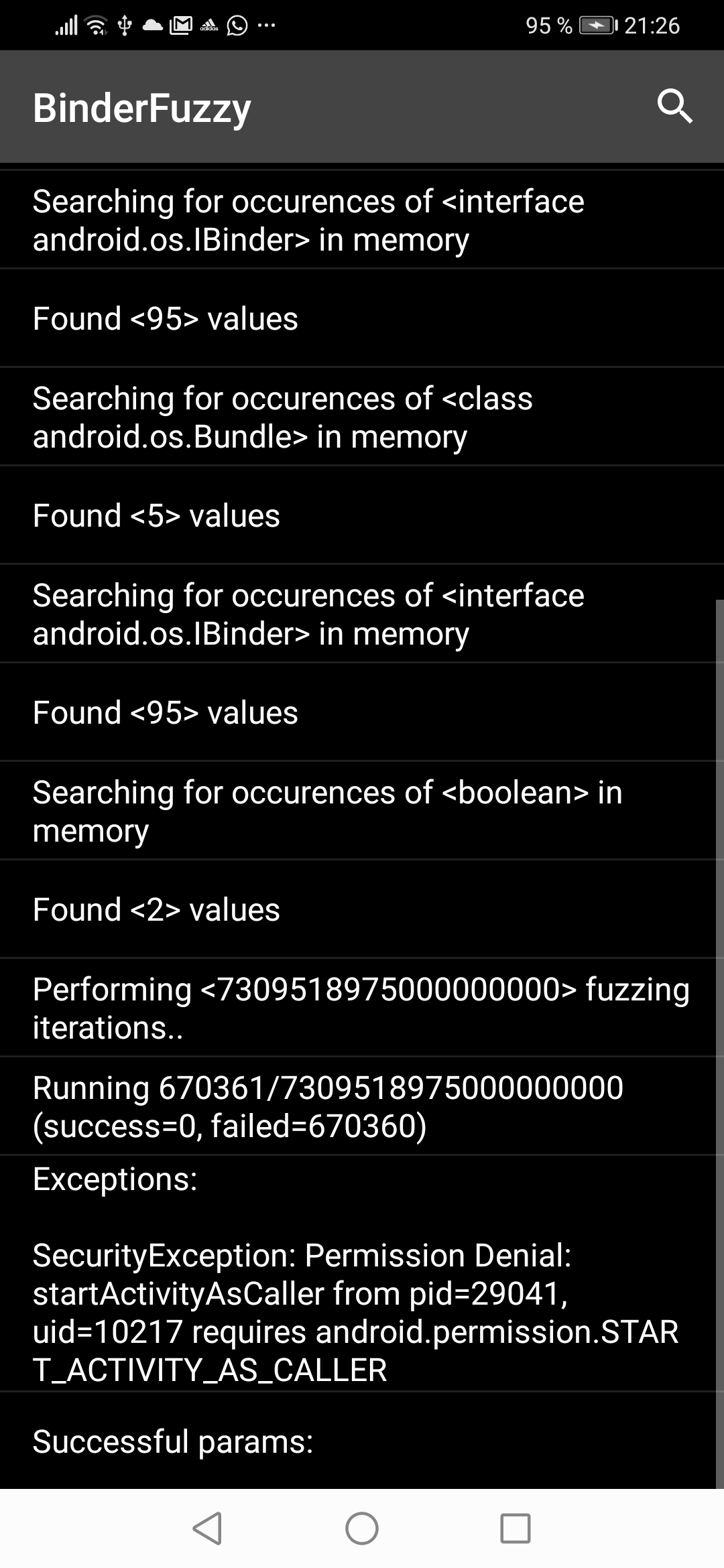
Once you're finished you can press the START button and the test begins.
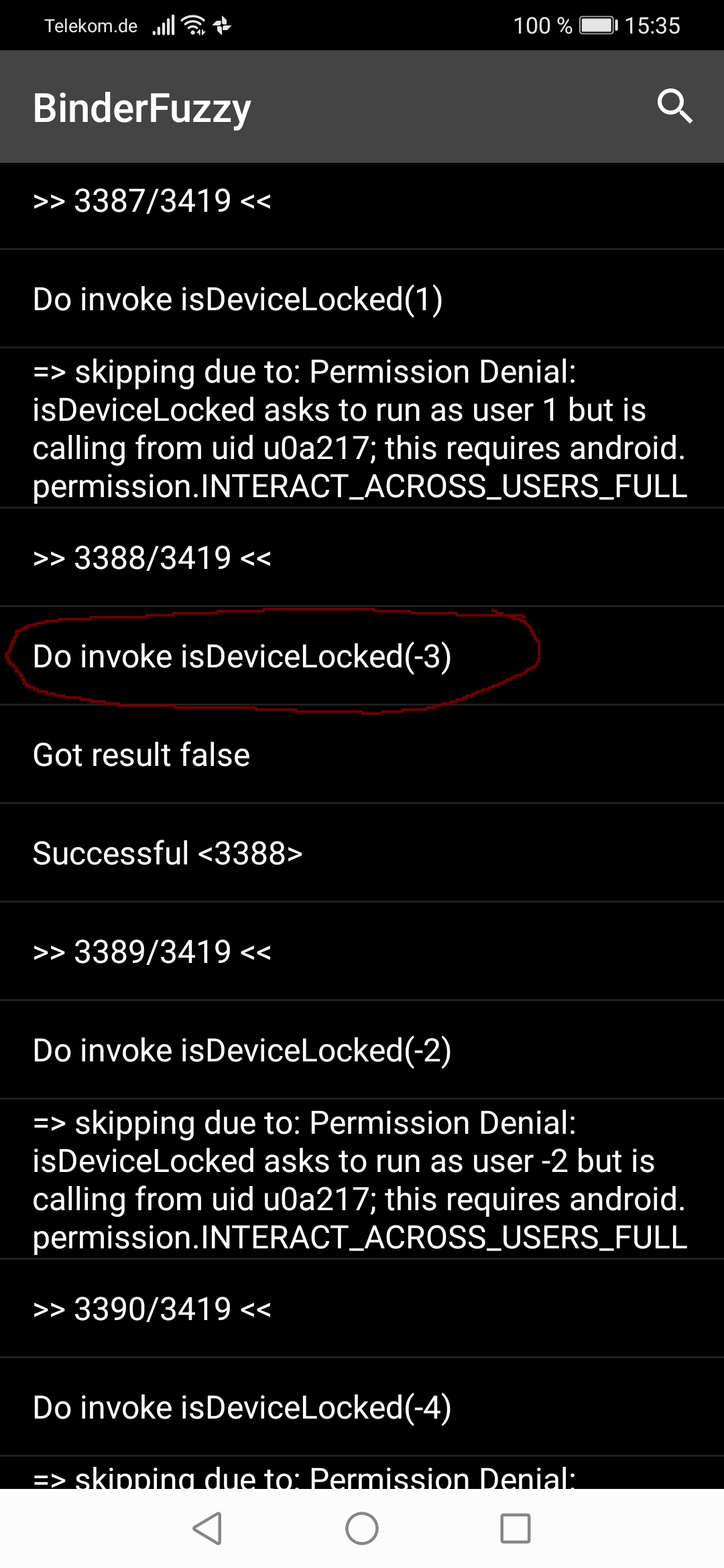
Passing user -3 as parameter will bypass the permission check.
| Project | Description |
|---|---|
| ChickenHook | A linux / android / MacOS hooking framework |
| BinderHook | Library intended to hook Binder interface and manipulate events |
| RestrictionBypass | Android API restriction bypass for all Android Versions |
| AndroidManifestBypass | Android API restriction bypass for all Android Versions |
| .. |