| Build & Test | |
|---|---|
 macOS macOS |
|
 Linux Linux |
ChickenHook is a multi architecture hooking framework.
Supported architectures: x86, arm64, x86_64 (experimental) Supported platforms: Android, Linux
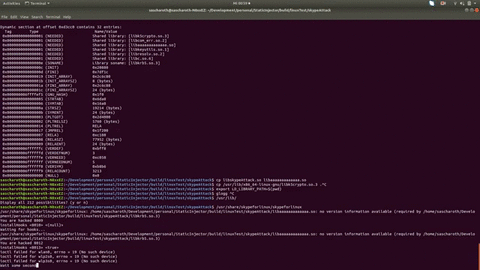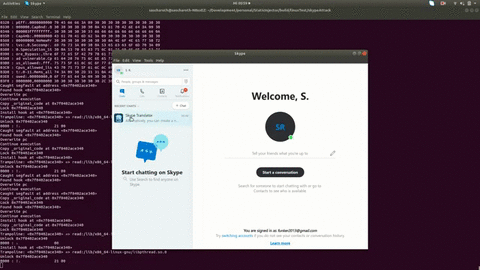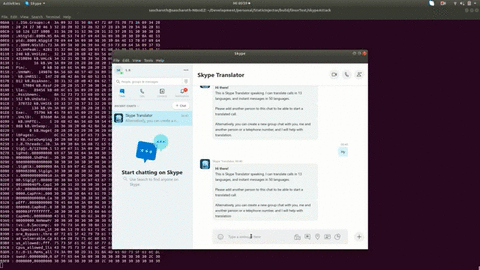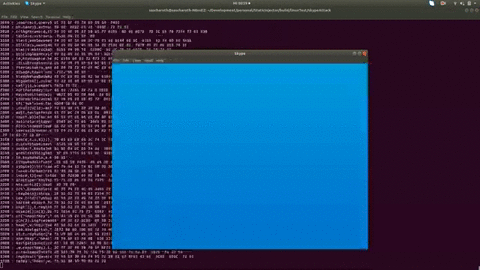
Hack some applications using ChickenHook + StaticInjector (Linux Wrapper)
See more at: StaticInjector
Here are some examples hacks using StaticInjector
Check this video (Please enable subtitles):
Check this video (Please enable subtitles):
http://img.youtube.com/vi/kbrenIx8OrI/0.jpg
Read more in our wiki: How to create a linux attack (skype example)
See more at: ChickenTime
- ant
- cmake
- make
- Android SDK
- Android NDK
- Android Studio (Optional)
- Create the hook function (the function that should be called instead of the original function)
example here shows a hook function for libc's open
ssize_t my_read(int __fd, void *__buf, size_t __count) {
__android_log_print(ANDROID_LOG_DEBUG, "my_read", "read called [-] %d", __fd);
// <== add your code before real call here
// yeah we're inside! But sometimes you want to call the original function also.
// For this purpose we try to retrieve the corresponding trampoline.
// So let's retrieve our trampoline in order to call the original function "read"
int res = -1;
ChickenHook::Trampoline trampoline;
if (ChickenHook::Hooking::getInstance().getTrampolineByAddr((void *) &read, trampoline)) {
__android_log_print(ANDROID_LOG_DEBUG, "my_read",
"hooked function call original function");
printLines(hexdump(static_cast<const uint8_t *>(__buf), __count, "read"));
// retrieve the real read call address
ssize_t (*_read)(int, void *, size_t) =(ssize_t (*)(int, void *,
size_t)) trampoline.getRealCallAddr();
// if read != nullptr we have a valid address and call it
// if read ==nullptr we have to copy the original code of read.
if (_read == nullptr) {
// !! WARNING !! This is a very risky workaround.
// * Race condition can lead to crashes
// * Multithreading and semaphores in target function or it's callee's can lead to deadlocks
trampoline.copyOriginal();
res = read(__fd, __buf, __count);
trampoline.reinstall();
} else {
// Very save method. Available for most of all functions
res = _read(__fd, __buf, __count);
}
} else {
__android_log_print(ANDROID_LOG_DEBUG, "my_read",
"hooked function cannot call original function");
}
// <== manipulate results here
return res;
}- Inject the trampoline (enable the hook)
ChickenHook::Hooking::getInstance().hook((void *) &read, (void *) &my_read);Currently ChickenHook can be build for Linux and Android and MacOs.
ant configure-linux compile-linux test-linux
artifacts will be in build/libs/
Use as an Android Studio project or:
ant configure-android compile-android test-android
ant configure-mac compile-mac test-mac install-mac
artifacts will be in ./artifactsOut
- Fetch artifacts via ANT
<target name="artifacts">
<mkdir dir="artifacts"/>
<get src="https://dev.azure.com/ChickenHook/ChickenHook/_apis/build/builds/101/artifacts?artifactName=ChickenHook&api-version=5.1&%24format=zip" dest="artifacts/ChickenHook.zip"/>
<unzip src="artifacts/ChickenHook.zip" dest="artifacts/"/>
<get src="https://dev.azure.com/ChickenHook/ChickenHook/_apis/build/builds/99/artifacts?artifactName=BeaEngine&api-version=5.1&%24format=zip" dest="artifacts/BeaEngine.zip"/>
<unzip src="artifacts/BeaEngine.zip" dest="artifacts/"/>
</target>- Include into your CMake project Includes
target_include_directories(${PROJECT_NAME} PUBLIC
${CMAKE_SOURCE_DIR}/artifacts/ChickenHook/${CMAKE_SYSTEM_NAME}-${CMAKE_SYSTEM_PROCESSOR}/include/
${CMAKE_SOURCE_DIR}/artifacts/BeaEngine/${CMAKE_SYSTEM_NAME}-${CMAKE_SYSTEM_PROCESSOR}/include/
)Static libraries
target_link_libraries(${PROJECT_NAME}
# add chickenhook here
${CMAKE_SOURCE_DIR}/artifacts/ChickenHook/${CMAKE_SYSTEM_NAME}-${CMAKE_SYSTEM_PROCESSOR}/lib/libChickenHook.a
${CMAKE_SOURCE_DIR}/artifacts/BeaEngine/${CMAKE_SYSTEM_NAME}-${CMAKE_SYSTEM_PROCESSOR}/lib/libBeaEngine_s_d_l.a
log
dl
)| Project | Description |
|---|---|
| ChickenHook | A linux / android / MacOS hooking framework |
| BinderHook | Library intended to hook Binder interface and manipulate events |
| RestrictionBypass | Android API restriction bypass for all Android Versions |
| AndroidManifestBypass | Android API restriction bypass for all Android Versions |
| .. |