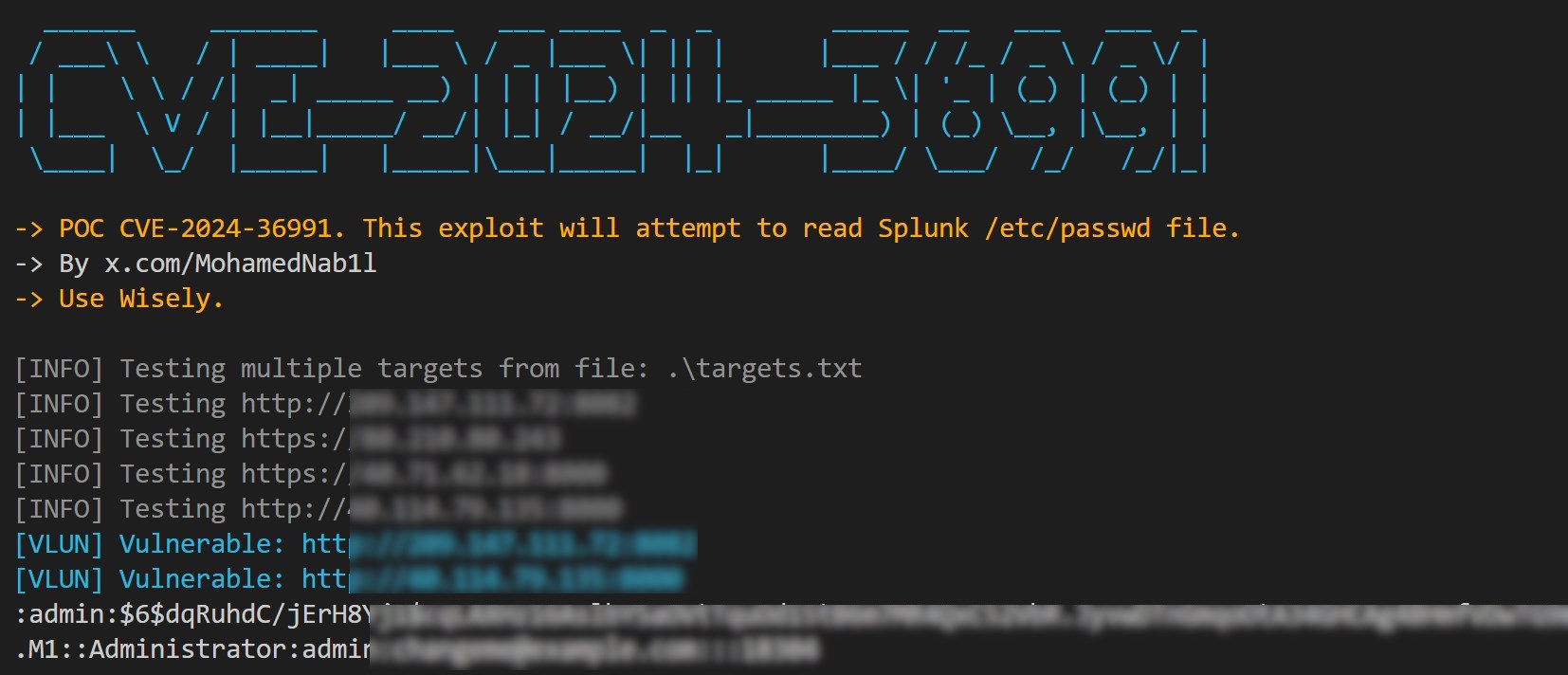
POC for CVE-2024-36991: This exploit will attempt to read Splunk /etc/passwd file.
This is a bulk scanning and exploitation tool for CVE-2024-36991: Path traversal that affects Splunk Enterprise on Windows versions below 9.2.2, 9.1.5, and 9.0.10
- Python 3.6 or higher
requestslibrary
python CVE-2024-36991.py -u https://target:9090python CVE-2024-36991.py -f targets.txtThe vulnerability affects instances with Splunk Web turned on. You could turn Splunk Web off as a possible workaround. See Disable unnecessary Splunk Enterprise components and the web.conf configuration specification file for more information on turning Splunk Web off.
For any suggestions or thoughts, please get in touch with me.
I like to create my own tools for fun, work and educational purposes only. I do not support or encourage hacking or unauthorized access to any system or network. Please use my tools responsibly and only on systems where you have clear permission to test.