When analyzing malware or 3rd party software, it's challenging to identify statically linked libraries and to understand what a function from the library is doing.
idenLib.exe is a tool for generating library signatures from .lib files.
idenLib.dp32/idenLib.dp64 is a x32dbg/x64dbg plugin to identify library functions.
idenLib.py is an IDA Pro plugin to identify library functions.
Any feedback is greatly appreciated: @_qaz_qaz
- Parses input file(
.libfile) to get a list of function addresses and function names. - Gets the last opcode from each instruction
-
Compresses the signature with zstd
-
Saves the signature under the
SymExdirectory, if the input filename iszlib.lib, the output will bezlib.lib.sigorzlib.lib.sig64, ifzlib.lib.sig(64)already exists under theSymExdirectory from a previous execution or from the previous version of the library, the next execution will append different signatures. If you executeidenLib.exeseveral times with different version of the.libfile, the.sig/sig64file will include all unique function signatures.
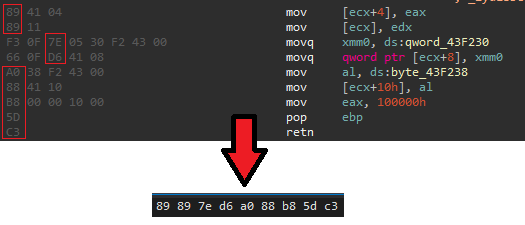
Inside of a signature (it's compressed):

x32dbg/x64dbg, IDA Pro plugin usage:
- Copy
SymExdirectory underx32dbg/x64dbg/IDA Pro's main directory - Apply signatures:
Supports x86 and AMD64/x86-64 architectures.
- Detailed information about
C Run-Time Libraries (CRT);