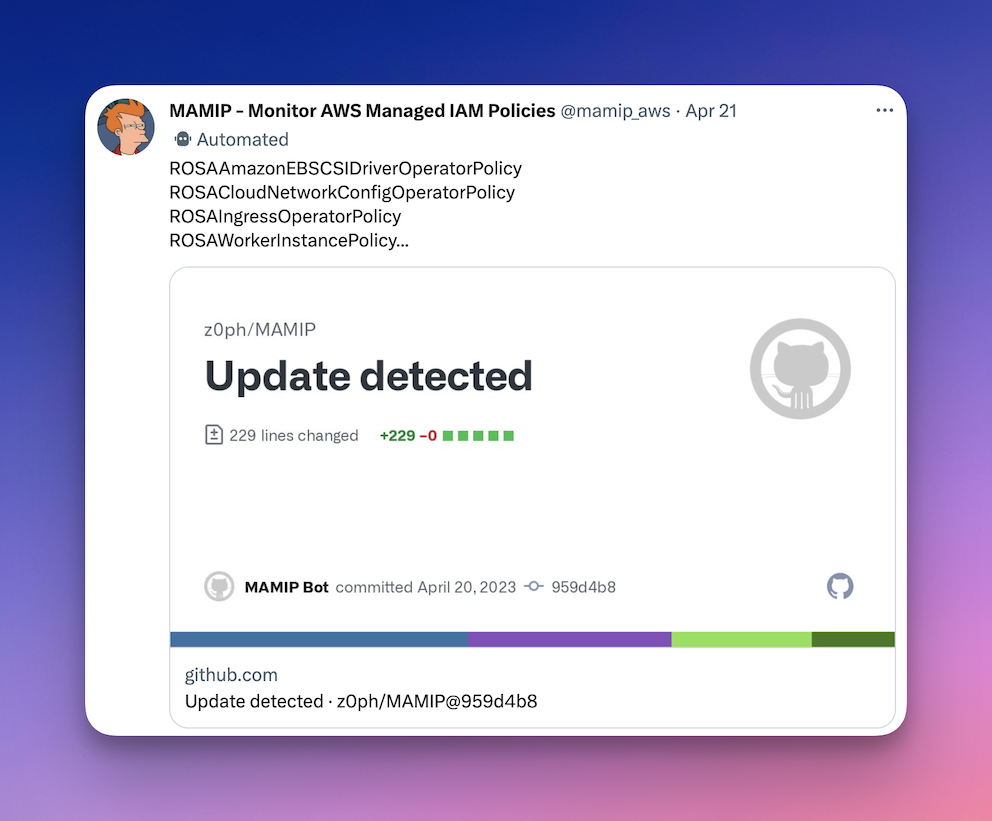
📢 [MAMIP] Monitor AWS Managed IAM Policies
Thanks to @0xdabbad00 for the original idea, this repo automates the retrieval of new AWS Managed IAM Policies making it easier to monitor and get alerted when changes occur.
✋ Usage
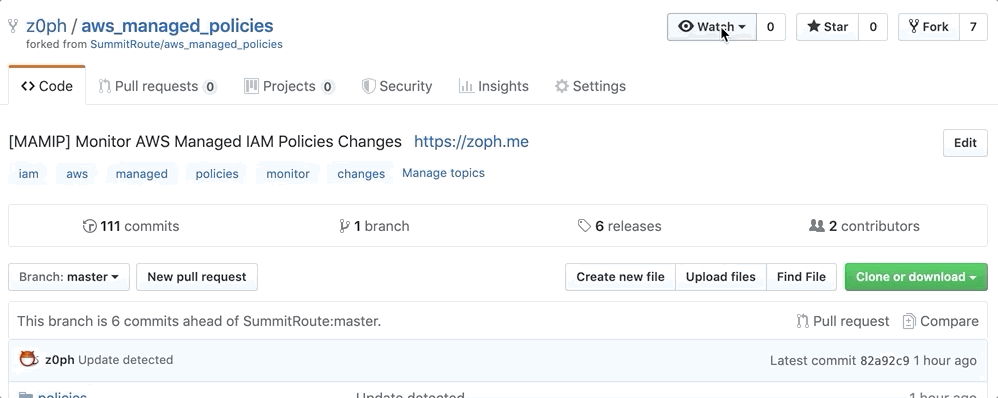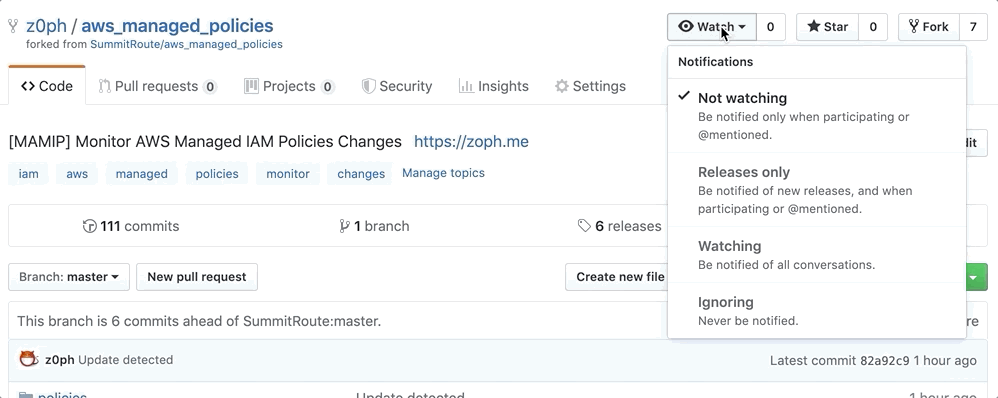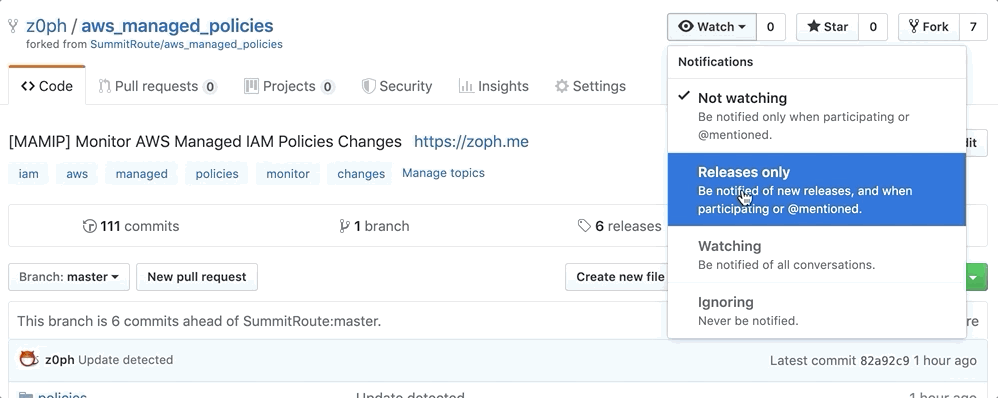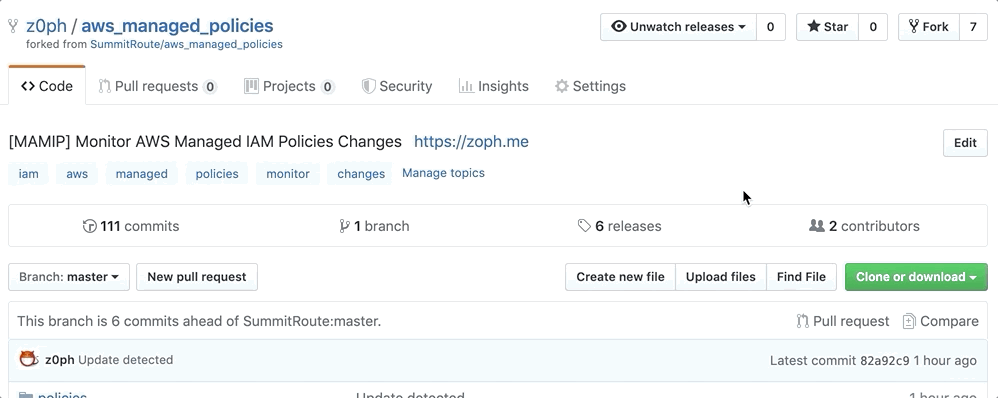
3️⃣ Three options to get notifications
- Follow the Twitter Account or on Mastodon.
- Activate
Releases OnlyNotification feature of Github
- Subscribe to the Github RSS Feed (
masterbranch)
✅ Policy Validation
I'm using AWS Access Analyzer Policy Validation. You can check findings in the findings folder.
👴 Deprecated Policies
Some AWS Managed Policies are now deprecated since they first appeared in this repository. Policy validation only takes place on actual AWS-managed policies.
🤍 How it works behind the scene
AWS Managed Policies are acquired as follows:
aws iam list-policies --scope AWS > list-policies.json
cat list-policies.json \
| jq -cr '.Policies[] | select(.Arn | contains("iam::aws"))|.Arn +" "+ .DefaultVersionId+" "+.PolicyName' \
| xargs -n3 sh -c 'aws iam get-policy-version --policy-arn $1 --version-id $2 > "policies/$3"' shThis command does the following:
- Gets the list of all IAM Policies in the AWS account
- Finds the ones with an ARN containing
iam::aws, so that only the AWS managed policies are grabbed. - Gets the
ARN, current version id, and policy name (needed so we don't have a slash as theARNdoes for writing a file) - Calls
aws iam get-policy-versionwith those values, and writes the output to a file using the policy name.
⚙️ Automation Details
- Infrastructure is deployed using Terraform:
- ECS + Fargate
- Clone this repository
- Run the magic (previously mentioned command)
- If changes are detected:
- Commit changes
- Push + Create Release
- Send SQS message to qTweet
🕐 Schedule
- ECS + Fargate (Spot): current setting