Create a globally-distributed Amazon CloudFront Distribution (CDN) that will securely serve-up static files from an Amazon S3 Bucket using OpenID Connect. The purpose of this repository is to allow organizations or users to integrate with their preferred OpenID Connect compliant Identity Provider (IdP).
- AWS SAM CLI is Installed
- AWS Credentials are setup in your Environment
- An S3 Bucket is created in your AWS account in the Same Region you are deploying to
- Python3 is Installed in your Environment
- Pip3 is Installed in your Environment
The following set of steps should be followed to deploy this solution:
- Create a base AWS Secrets Manager Secret Configuration
- Deploy the AWS SAM Stack
- Set up Registered OIDC Application
- Generate OIDC Configuration
- Update AWS Secrets Manager
- Navigate to Amazon CloudFront URL / Troubleshoot
For more details about generating the configuration file for AWS Secrets Manager please refer to CLI Documentation
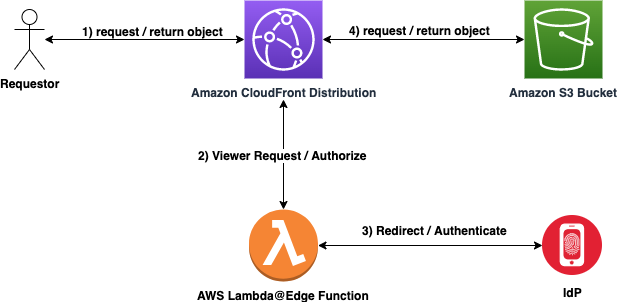
- User requests content from Amazon CloudFront Distribution
- AWS Lambda@Edge Viewer Request invoked
- If valid authentication cookie present in header, redirect to Amazon S3 Bucket.
- If no authentication cookie is present or expired/invalid cookie header is present, continue to step 3.
- AWS Lambda@Edge Function redirects request to IdP for Authentication request.
- If Authentication challenge fails - deny access and exit.
- If Authentication challenge succeeds - continue on.
- Retrieve object from Amazon S3 bucket and return content to requestor via Amazon CloudFront Distribution. User is happy :)
- S3 Data Bucket
- S3 Logging Bucket
- CloudFront Distribution
- Lambda@Edge Function for OIDC Auth
Please refer to this document for Troubleshooting common scenarios. Open a GitHub issue if this does not help!
- Amazon Cognito Application Registration
- Okta Application Registration
- Keycloak Client Creation and Registration
See CONTRIBUTING for more information.
This library is licensed under the MIT-0 License. See the LICENSE file.
- Viyoma Sachdeva
- Matt Noyce