((اللَّهُمَّ انْفَعْنِي بِمَا عَلَّمْتَنِي، وَعَلِّمْنِي مَا يَنْفَعُنِي، وَزِدْنِي عِلْمًا))
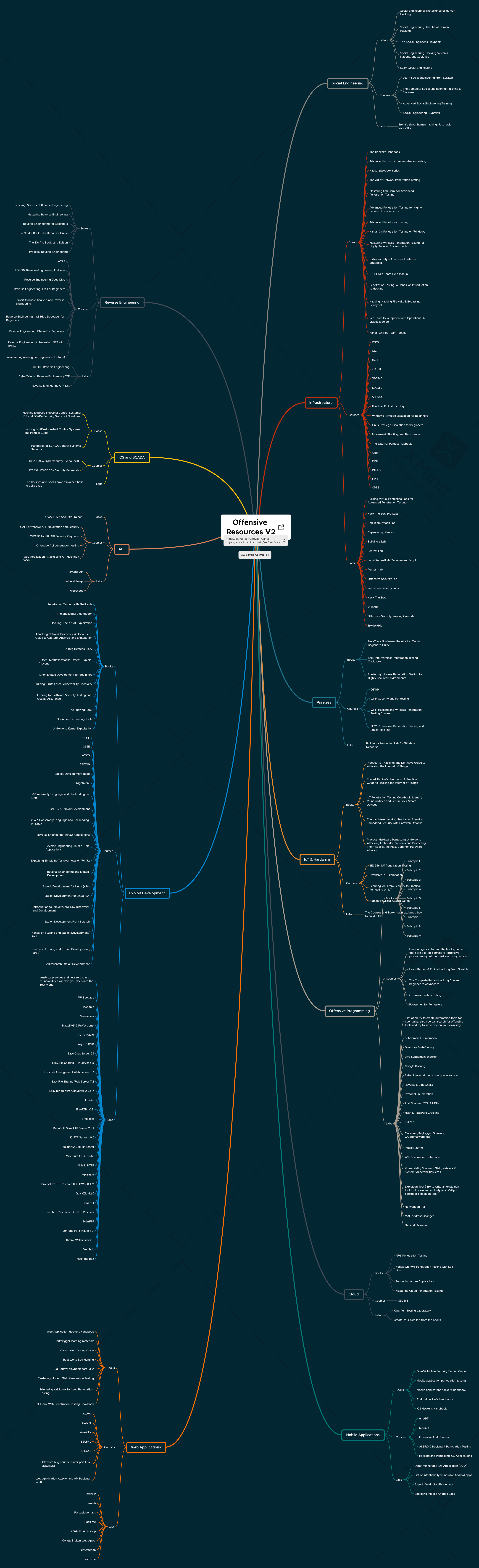
- New Labs, Courses & Books Have been added to whole old sections
- Added Reverse Engineering Section
- Added Wireless Penetration Testing Section
- Added IoT & Hardware Penetration Testing Section
- Added ICS & SCADA Penetration Testing Section
- Infrastructure
- Wireless
- IoT & Hardware
- ICS and SCADA
- Exploit Development
- Web Applications
- Mobile Applications
- API
- Cloud
- Reverse Engineering
- Social Engineering
- Offensive Programming
-
Books
- The Hacker's Handbook
- Advanced Infrastructure Penetration testing
- Hacker playbook series
- The Art of Network Penetration Testing
- Mastering Kali Linux for Advanced Penetration Testing
- Advanced Penetration Testing for Highly-Secured Environments
- Advanced Penetration Testing
- Hands-On Penetration Testing on Windows
- Mastering Wireless Penetration Testing for Highly Secured Environments
- Cybersecurity - Attack and Defense Strategies
- RTFM: Red Team Field Manual
- Penetration Testing: A Hands-on Introduction to Hacking
- Hacking: Hacking Firewalls & Bypassing Honeypot
- Red Team Development and Operations: A practical guide
- Hands-On Red Team Tactics
-
Courses
-
Labs
- Building Virtual Pentesting Labs for Advanced Penetration Testing>
- Hack The Box: Pro Labs
- Red Team Attack Lab
- Capsulecorp Pentest
- Building a Lab
- Pentest Lab
- Local PentestLab Management Script
- Pentest-lab
- Offensive Security Lab
- Pentesteracademy Labs
- Hack The Box
- Vulnhub
- Offensive Security Proving Grounds
- TryHackMe
-
Books
-
Courses
-
Labs
- Building a Pentesting Lab for Wireless Networks
- The Courses and Books have explained how to build a lab
-
Books
- Practical IoT Hacking: The Definitive Guide to Attacking the Internet of Things
- The IoT Hacker's Handbook: A Practical Guide to Hacking the Internet of Things
- IoT Penetration Testing Cookbook: Identify Vulnerabilities and Secure Your Smart Devices
- The Hardware Hacking Handbook: Breaking Embedded Security with Hardware Attacks
- Practical Hardware Pentesting: A Guide to Attacking Embedded Systems and Protecting Them Against the Most Common Hardware Attacks
-
Courses
-
Labs
- The Courses and Books have explained how to build a lab
-
Books
-
Courses
-
Labs
- The Courses and Books have explained how to build a lab
-
Books
- Penetration Testing with Shellcode
- The Shellcoder's Handbook
- Hacking: The Art of Exploitation
- Attacking Network Protocols: A Hacker's Guide to Capture, Analysis, and Exploitation
- A Bug Hunter's Diary
- Buffer Overflow Attacks: Detect, Exploit, Prevent
- Linux Exploit Development for Beginners
- Fuzzing: Brute Force Vulnerability Discovery
- Fuzzing for Software Security Testing and Quality Assurance
- The Fuzzing Book
- Open Source Fuzzing Tools
- A Guide to Kernel Exploitation
-
Courses
- OSCE
- OSEE
- eCXD
- SEC760
- Exploit-Development Repo
- Nightmare
- x86 Assembly Language and Shellcoding on Linux
- CNIT 127: Exploit Development
- x86_64 Assembly Language and Shellcoding on Linux
- Reverse Engineering Win32 Applications
- Reverse Engineering Linux 32-bit Applications
- Exploiting Simple Buffer Overflows on Win32
- Reverse Engineering and Exploit Development
- Exploit Development for Linux (x86)
- Exploit Development for Linux x64
- Introduction to Exploit/Zero-Day Discovery and Development
- Exploit Development From Scratch
- Hands-on Fuzzing and Exploit Development(Part 1)
- Hands-on Fuzzing and Exploit Development(Part 2)
- ZDResearch Exploit Development
-
Labs
- Analyize previous and new zero-days vulnerabilities will dive you deep into the real-world
- PWN collage
- Pwnable
- Vulnserver
- BlazeDVD 5 Professional
- DVDx Player
- Easy CD DVD
- Easy Chat Server 3.1
- Easy File Sharing FTP Server 3.5
- Easy File Management Web Server 5.3
- Easy File Sharing Web Server 7.2
- Easy RM to MP3 Converter 2.7.3.7
- Eureka
- FreeFTP 1.0.8
- FreeFloat
- KarjaSoft Sami FTP Server 2.0.1
- KnFTP Server 1.0.0
- Kolibri v2.0 HTTP Server
- Millenium MP3 Studio
- Minialic HTTP
- Minishare
- ProSysInfo TFTP Server TFTPDWIN 0.4.2
- QuickZip 4.60
- R v3.4.4
- Ricoh DC Software DL-10 FTP Server
- SolarFTP
- Soritong MP3 Player 1.0
- Xitami Webserver 2.5
- Vulnhub
- Hack the box
-
Books
-
Courses
-
Labs
-
Books
-
Courses
-
Labs
-
Books
-
Courses
-
Labs
-
Books
-
Courses
-
Labs
- AWS Pen-Testing Laboratory
- Create Your own lab from the books
-
Books
-
Courses
- eCRE
- FOR610: Reverse-Engineering Malware
- Reverse Engineering Deep Dive
- Reverse Engineering: IDA For Beginners
- Expert Malware Analysis and Reverse Engineering
- Reverse Engineering 1: x64dbg Debugger for Beginners
- Reverse Engineering: Ghidra For Beginners
- Reverse Engineering 6: Reversing .NET with dnSpy
- Reverse Engineering For Beginners (Youtube)
-
Labs
-
Books
-
Courses
-
Labs
-
Bro, it's about human hacking. Just hack yourself xD
-
Books
- Hands-On Penetration Testing with Python
- Python Penetration Testing Cookbook
- Python for Offensive PenTest
- Black Hat Python
- Gray Hat C#: A Hacker's Guide to Creating and Automating Security Tools
- Black Hat Go: Go Programming For Hackers and Pentesters
- Security with Go
- Penetration Testing with PerL
- Black Hat Ruby
-
Courses
- I encourage you to read the books, cause there are a lot of courses for offensive programming but the most are using python.
- Learn Python & Ethical Hacking From Scratch
- The Complete Python Hacking Course: Beginner to Advanced!
- Offensive Bash Scripting
- Powershell for Pentesters
-
Labs
- First of all try to create automation tools for your tasks. also you can search for offensive tools and try to write one on your own way.
- Tools:
- Subdomain Enumeration
- Directory Bruteforcing
- Live Subdomain checker
- Google Dorking
- Extract javascript urls using page source
- Reverse & Bind Shells
- Protocol Enumeration
- Port Scanner (TCP & UDP)
- Hash & Password Cracking
- Fuzzer
- Malware ( Keylogger, Spyware, CryptoMalware, etc)
- Packet Sniffer
- Wifi Scanner or Bruteforcer
- Vulnerability Scanner ( Web, Network & System Vulnerabilities, etc )
- Exploition Tool ( Try to write an exploition tool for known vulnerability [e.x: Vsftpd backdoor exploition tool] )
- Network Sniffer
- MAC address Changer
- Network Scanner